Administrivia
Lectures and assignments, second half.


An Introduction to Computer Networks - Second Edition
(6 reviews)
Peter Lars Dordal, Loyola University of Chicago
Copyright Year: 2014
Last Update: 2020
Publisher: Peter L Dordal
Language: English
Formats Available
Conditions of use.
Learn more about reviews.
Reviewed by Stuart Anderson, Adjunct Instructor, Norfolk State University on 11/13/23
The textbook is complete and thorough. The index correctly points to the material in the chapters. read more
Comprehensiveness rating: 5 see less
The textbook is complete and thorough. The index correctly points to the material in the chapters.
Content Accuracy rating: 5
The information in the book is accurate as it applies to networking concepts.
Relevance/Longevity rating: 5
The book's content is current.
Clarity rating: 4
The material is clear however, it does make assumptions about the reader's level of current knowledge about the material.
Consistency rating: 5
The material is consistent and flows in a good order.
Modularity rating: 4
The is very good in how the information is broken down into specific modules. Some modules need more information to make them more complete.
Organization/Structure/Flow rating: 5
The information is organized in a fashion that allows future topics to build on the previous topics.
Interface rating: 5
There were no interface issues.
Grammatical Errors rating: 5
There are no grammatical errors.
Cultural Relevance rating: 5
The test is inclusive of all cultures.
This is a good textbook for networking information. Some of the material could be explained in more detail to make it more of an introductory topic. A reader with networking experience would find this book a good reference, however, a reader new to the networks might find some of the material a bit light. As a network engineer, I found the information thorough and would work well with other networking material.
Reviewed by Terri Devlin, Instructor, Aims Community College on 7/23/19
Even though the title of the text is "An Introduction to Networking", the author seems to assume that the student or reader knows a lot about the subject matter and terminology. Topics and some definitions are presented, however the author does a... read more
Comprehensiveness rating: 3 see less
Even though the title of the text is "An Introduction to Networking", the author seems to assume that the student or reader knows a lot about the subject matter and terminology. Topics and some definitions are presented, however the author does a deep dive into the topic area quickly. This text would not be beneficial to students seeking CompTia Network + Certification because many of the terms and concepts tested in the certification exam are not covered in this text.
The author presents the material in an unbiased manner. Errors were not identified
Relevance/Longevity rating: 2
Out-of-date information was identified. The text is written in a manner that updates could be made in a straightforward manner.
Clarity rating: 2
The text was difficult to read because precise definitions and content were not provided. Other textbooks and internet sources were used to look up definitions and refresh understanding of technical terms and concepts
Consistency rating: 4
The terminology, framework, and chapter exercises followed a consistent approach.
The layout of the book is easy to understand and follow.
Organization/Structure/Flow rating: 3
The topics were organized in a logical fashion. It was a challenge to determine the network “big picture” and how the components fit into the picture. The topics make sense to people familiar with Networks. This text would be challenging to people new to Computer Network concepts.
Interface rating: 3
The text is free of navigation problems. The figures and tables were easily identified. An improvement could be made with providing better images or pictures.
Grammatical Errors rating: 4
The text was free of grammatical errors.
The text is appropriate for globally-based students.
Many computer concept textbooks have associated software that helps student learn topics and practice. Computer Networks is an area where practice helps students learn. This text did not have associated software available.
Reviewed by Audrey Styer, Instructor, CIS/CPS, Morton College on 12/21/18
This textbook provides a very comprehensive and in-depth introduction to computer networking. read more
This textbook provides a very comprehensive and in-depth introduction to computer networking.
All information presented is accurate.
This textbook is continually being updated to accommodate the ever-changing nature of computer networking.
Clarity rating: 5
Material is presented in a clear manner, but does require a prior basic understanding of computer networking.
Consistency of presentation and methodology is maintained throughout the text.
Modularity rating: 5
The chapters are well defined by topic
The material is presented in a logical manner that helps learners develop their understanding.
The PDF version is easy to read and navigate. The linked Table of Contents and Index make finding and moving to specific topics simple.
I found no grammatical errors.
This is not applicable to this topic.
The callout boxes provide a visual break for readers and increase learning with interesting facts and supporting information. Unfortunately, this textbook is too advanced for my undergraduate learners and does not map to CompTIA’s Network+ certification.
Reviewed by Sunho Lim, Assistant Professor, Texas Tech University on 3/27/18
The text covers all five layers (phy, link, net, trans, and app) and their associated algorithms and communication protocols in the network, and provides an effective index and/or golssary. read more
The text covers all five layers (phy, link, net, trans, and app) and their associated algorithms and communication protocols in the network, and provides an effective index and/or golssary.
The content is accurate and unbiased.
Relevance/Longevity rating: 3
The most content is up-to-date and the text is written in a way to easily be updated. Since network technology is time-sensitive, some sections in the text should be updated.
The text is easy to read but some advanced sections (e.g., network simulator ns-2 and ns-3) would be challenging to read and understand technical terminology used.
The text is consistent in using terminology and framework.
The text is well divided into a set of sections. It is easy to selectively choose a section depending on the level of class or students.
Organization/Structure/Flow rating: 4
The topics in the text are presented in a bottom-up way, but grouping sections in terms of layer would be great.
The text has an interface issue, such as some contents are displayed out of page or cut off.
The text contains no grammatical errors.
Cultural Relevance rating: 1
The text is not related to any culture.
The text is appropriate to both undergraduate to graduate students. A set of selective chapters can be used depending on the instructor. The text is good to use for a reference book.
Reviewed by Lisa Bain, Professor, Rhode Island College on 2/1/18
The book covers all the major topics required for a computer networking course. read more
The book covers all the major topics required for a computer networking course.
Yes, this book is accurate in the major areas that the reviewer read. The entire text was not reviewed.
Relevance/Longevity rating: 4
Yes, the book is up-to-date with the major concepts that do not change (e.g. TCP, IP, UDP) and also includes the latest standards for Wi-Fi. However, some networking technologies will need to be updated as advancements are made (e.g. newer Wi-Fi standards).
Yes, the text is clearly written. However, the content is very technical and would be challenging for a non-technical person to understand all aspects. It is very straight-forward and appropriate for a technical audience.
Yes, the book is consistent and uses the same technical terminology throughout.
Yes the book is very modular and provides many small sections within each chapter for specific topics.
The flow of the book is similar to other networking books in that is starts with an introduction then provides additional details in following chapters.
The interface in PDF is easy to navigate using the table of contents and embedded links.
Of the information read, no grammar errors were found.
This is not relative to this book.
This book would be appropriate for an instructor with a strong background in teaching networking and using a more technical approach.
Reviewed by Luke Osterritter, Adjunct Instructor, Penn State New Kensington on 2/1/18
This text does a great job of covering the basics of computer networks while also presenting in-depth information, as well as diving into some somewhat tangential, but important, areas (e.g. security). read more
This text does a great job of covering the basics of computer networks while also presenting in-depth information, as well as diving into some somewhat tangential, but important, areas (e.g. security).
There are some terms here that I have seen presented differently than I have learned them or encountered in industry, but nothing inaccurate.
It would seem that this book is kept rather up-to-date, though much of the content is so fundamental as to not have too much of an expiration date, even in this field.
I believe the text is clear in most cases. However, I do feel many of the topics become very in-depth, very fast. It would be nice to have some concepts factored out to their basics early in the chapters, then expounded upon later.
The text does not appear to have any major inconsistencies.
When viewing online, the table of contents makes the content very browsable. However, when viewing in PDF, the large amount of subheadings for any one chapter can be a bit tough to navigate.
As the author notes, there isn't much agreement in how to present this topic, and it can be very difficult to explain one portion without referencing another topic that may not have been presented. I think factoring out some basics and explaining them up front, as this book has done, is a clever way of handling this.
I did not encounter any issues with the text interface.
I did not see any obvious grammatical errors.
This book is very matter-of-fact, with little in the way of irreverence. Likewise, there isn't much to work with here to be proactively inclusive. I think it works to be somewhat inert in this manner.
Overall, I think that this book is a great resource to have given its open availability. It's not the simplest book, so using this in a first level class or in a more general IT, CS, or survey course will take some shepherding on the part of the instructor. The comprehensiveness does suggest to me that this might be able to fill two courses worth of content, as well. It would be nice to have some of the information factored out, with some of the highlights available as lecture materials. On its own though, I feel this would be a strong resource to use in a computer networking course.
Table of Contents
- 1 An Overview of Networks
- 3 Other LANs
- 6 Abstract Sliding Windows
- 7 IP version 4
- 8 IP version 6
- 9 Routing-Update Algorithms
- 10 Large-Scale IP Routing
- 11 UDP Transport
- 12 TCP Transport
- 13 TCP Reno and Congestion Management
- 14 Dynamics of TCP Reno
- 15 Newer TCP Implementations
- 16 Network Simulations: ns-2
- 17 The ns-3 Network Simulator
- 19 Queuing and Scheduling
- 20 Quality of Service
- 21 Network Management and SNMP
- 22 Security
- 23 Bibliography
- 24 Selected Solutions
Ancillary Material
- Peter L Dordal
About the Book
An Introduction to Computer Networks is a free and open general-purpose computer-networking textbook, complete with diagrams and exercises.It covers the LAN, internetworking and transport layers, focusing primarily on TCP/IP. Particular attention is paid to congestion; other special topics include queuing, real-time traffic, network management, security and the ns simulator.
The book is suitable as the primary text for an undergraduate or introductory graduate course in computer networking, as a supplemental text for a wide variety of network-related courses, and as a reference work.
About the Contributors
Peter Lars Dordal is an associate professor within the Department of Computer Science at Loyola University of Chicago. His research interests are in programming languages and computer networks.
Contribute to this Page
- Skip to content
- Skip to search
- Skip to footer
What is Computer Networking?

Computer networking refers to connected computing devices (such as laptops, desktops, servers, smartphones, and tablets) and an ever-expanding array of IoT devices (such as cameras, door locks, doorbells, refrigerators, audio/visual systems, thermostats, and various sensors) that communicate with one another.
- Basic networking (0:57)
- Learn about network basics
Contact Cisco
- Get a call from Sales
Call Sales:
- 1-800-553-6387
- US/CAN | 5am-5pm PT
- Product / Technical Support
- Training & Certification
How does a computer network work
Specialized devices such as switches, routers, and access points form the foundation of computer networks.
Switches connect and help to internally secure computers, printers, servers, and other devices to networks in homes or organizations. Access points are switches that connect devices to networks without the use of cables.
Routers connect networks to other networks and act as dispatchers. They analyze data to be sent across a network, choose the best routes for it, and send it on its way. Routers connect your home and business to the world and help protect information from outside security threats.
While switches and routers differ in several ways, one key difference is how they identify end devices. A Layer 2 switch uniquely identifies a device by its "burned-in" MAC address. A Layer 3 router uniquely identifies a device's network connection with a network-assigned IP address.
Today, most switches include some level of routing functionality.
MAC and IP addresses uniquely define devices and network connections, respectively, in a network. A MAC address is a number assigned to a network interface card (NIC) by a device's manufacturer. An IP address is a number assigned to a network connection.
How is computer networking evolving?
Modern-day networks deliver more than connectivity. Organizations are embarking on transforming themselves digitally. Their networks are critical to this transformation and to their success. The types of network architectures that are evolving to meet these needs are as follows:
- Software-defined (SDN) : In response to new requirements in the "digital" age, network architecture is becoming more programmable, automated, and open. In software-defined networks, routing of traffic is controlled centrally through software-based mechanisms. This helps the network to react quickly to changing conditions.
- Intent-based : Building on SDN principles, intent-based networking (IBN) not only introduces agility but also sets up a network to achieve desired objectives by automating operations extensively, analyzing its performance, pinpointing problematic areas, providing all-around security, and integrating with business processes.
- Virtualized : The underlying physical network infrastructure can be partitioned logically, to create multiple "overlay" networks. Each of these logical networks can be tuned to meet specific security, quality-of-service (QoS), and other requirements.
- Controller-based : Network controllers are crucial to scaling and securing networks. Controllers automate networking functions by translating business intent to device configurations, and they monitor devices continuously to help ensure performance and security. Controllers simplify operations and help organizations respond to changing business requirements.
- Multidomain integrations : Larger enterprises may construct separate networks, also called networking domains, for their offices, WANs, and data centers. These networks communicate with one another through their controllers. Such cross-network, or multidomain, integrations generally involve exchanging relevant operating parameters to help ensure that desired business outcomes that span network domains are achieved.
Only Cisco offers a complete portfolio of modern network architectures for access, WANs, data centers, and cloud.
Types of computer networks
While similar in their overall objectives, various types of networks fulfill different purposes. Networks today are classified in the broad categories below.
Local-area network (LAN)
A LAN is a collection of connected devices in one physical location, such as a home or an office. A LAN can be small or large, ranging from a home network with one user to a large enterprise network with thousands of users and devices. A LAN may include both wired and wireless devices.
Regardless of size, a LAN's particular characteristic is that it connects devices that are in a single, limited area.
Wide-area network (WAN)
A WAN extends over a large geographical area and connects individual users or multiple LANs. The Internet can be considered a WAN. Large organizations use WANs to connect their various sites, remote employees, suppliers, and data centers so they can run applications and access necessary data.
Physical connectivity in WANs can be achieved by leased lines, cellular connections, satellite links, and other means.
Enterprise network
A network built for a large organization, typically called an enterprise, needs to fulfill exacting requirements. Since networking is crucial for any modern enterprise to function, enterprise networks must be highly available, scalable, and robust. These networks have tools that enable network engineers and operators to design, deploy, debug, and remediate them.
An enterprise may use both LANs and WANs across its campus, branches, and data centers.
Service-provider network
Service providers operate WANs to provide connectivity to individual users or organizations. They may offer simple connectivity, in the form of leased lines, or more-advanced, managed services to enterprises. Service providers also supply Internet and cellular connectivity to their customers.
Related topics
- Intent-based networking
- Networking Basics: What You Need to Know
- Networking Basics: Cisco DevNet Learning Labs
- Software-defined networking
- What is a Network Controller?
You may also like…
- What Is an Edge Router?
- What Is an Enterprise Network?
- What Is Network Topology?
- What Is Network Monitoring?
- What Is Power over Ethernet?
- What Is IT Service Management - ITSM?
- Assignments
CPS 114 Introduction to Computer Networks: Labs
Lab 2: simple router, introduction.
In this lab assignment, you will write a simple router with a static routing table. We will pass to your code raw Ethernet frames and give you a function that can send a raw Ethernet frame. It is up to you to implement the forwarding logic between getting a frame and sending it out over another interface.

Figure 1: sample topology
Your router will route real packets from any machine to application servers sitting behind your router. The servers are running HTTP applications. When you have finished the forwarding path of your router, you should be able to access these servers using regular client software. In addition, you should be able to ping and traceroute to and through your functioning router. If the router is functioning correctly, all of the following operations should work:
This lab runs on top of Stanford's Virtual Network System . VNS allows you to build virtual network topologies consisting of nodes that operate on actual Ethernet frames. You don't have to know how VNS works to complete this assignment.
Getting started
First download and untar the assignment code .
You will also need to download your testing topology and auth_key file from class Forum ( DO use your own topology and auth_key file). Please
Here is one sample rtable file for topology in Figure 1. The base rtable file only has a default route to the firewall.
You can then build and run the assignment code (TOPOLOGY_ID and USER_NAME are in the topology file): xwy@linux21$ make xwy@linux21$ ./sr -s vns-2.stanford.edu -t <TOPOLOGY_ID> -u <USER_NAME>
From another terminal or another machine, try pinging one of the router's interfaces. Currently, all the assignment code does is print that it gets a packet to the command line.
Understanding the code
Data structure.
sr_router.[h|c] : The full context of the router is housed in the struct sr_instance (sr_router.h). sr_instance contains information about the topology the router is routing for as well as the routing table and the list of interfaces.
sr_if.[h|c] : After connecting, the server will send the client the hardware information for that host. The assignment code uses this to create a linked list of interfaces in the router instance at member if_list. Utility methods for handling the interface list can be found at sr_if.[h|c].
sr_rt.[h|c] : The routing table in the stub code is read on from a file (default filename "rtable", can be set with command line option -r ) and stored in a linked list of routing entries in the current routing instance.
sr_arpcache.[h|c] : You will need to add ARP requests and packets waiting on responses to those ARP requests to the ARP request queue. When an ARP response arrives, you will have to remove the ARP request from the queue and place it onto the ARP cache, forwarding any packets that were waiting on that ARP request. Pseudocode for these operations is provided in sr_arpcache.h. The base code already creates a thread that times out ARP cache entries 15 seconds after they are added for you. You must fill out the sr_arpcache_sweepreqs function in sr_arpcache.c that gets called every second to iterate through the ARP request queue and re-send ARP requests if necessary. Psuedocode for this is provided in sr_arpcache.h.
Important Functions
void sr_handlepacket(struct sr_instance* sr, uint8_t * packet, unsigned int len, char* interface)
This function receives a raw Ethernet frame and sends raw Ethernet frames when sending a reply to the sending host or forwarding the frame to the next hop. This method, located in sr_router.c, is called by the router each time a packet is received. The "packet" argument points to the packet buffer which contains the full packet including the ethernet header. The name of the receiving interface is passed into the method as well.
int sr_send_packet(struct sr_instance* sr, uint8_t* buf, unsigned int len, const char* iface)
This method, located in sr_vns_comm.c, will send an arbitrary packet of length, len, to the network out of the interface specified by iface.
void sr_arpcache_sweepreqs(struct sr_instance *sr)
The assignment requires you to send an ARP request about once a second until a reply comes back or we have sent five requests. This function is defined in sr_arpcache.c and called every second, and you should add code that iterates through the ARP request queue and re-sends any outstanding ARP requests that haven't been sent in the past second. If an ARP request has been sent 5 times with no response, a destination host unreachable should go back to all the sender of packets that were waiting on a reply to this ARP request.
Requirements
- The router enforces guarantees on timeouts--that is, if an ARP request is not responded to within a fixed period of time, the ICMP host unreachable message is generated even if no more packets arrive at the router.
Functions and data structures you need to implement
There is no specific requirement which function you can/cannot modify. To make the simple router work, you need to handle 4 kinds of packets correctly: Ethernet , IP , ICMP and ARP . For the actual specifications, there are also the RFC's for ARP (RFC826) , IP (RFC791) , and ICMP (RFC792) .
In our reference implementation, we developed sr_ip.[h|c], sr_icmp.[h|c] (you need to add these source files to the Makefile). We also modified sr_router.[h|c], protocol.h and sr_arpcache.[h|c]. Total work load is around 550 lines of c code.
Understanding Protocols
You are given a raw Ethernet frame and have to send raw Ethernet frames. You should understand source and destination MAC addresses and the idea that we forward a packet one hop by changing the destination MAC address of the forwarded packet to the MAC address of the next hop's incoming interface.
Internet Protocol
You should understand how to find the longest prefix match of a destination IP address in the routing table. If you determine that a datagram should be forwarded, you should correctly decrement the TTL field of the header and recompute the checksum over the changed header before forwarding it to the next hop.
Internet Control Message Protocol
ICMP is used to send control information back to the sending host. You will need to properly generate the following ICMP messages (including the ICMP header checksum) in response to the sending host under the following conditions:
Address Resolution Protocol
ARP is needed to determine the next-hop MAC address that corresponds to the next-hop IP address stored in the routing table. Without the ability to generate an ARP request and process ARP replies, your router would not be able to fill out the destination MAC address field of the raw Ethernet frame you are sending over the outgoing interface. Analogously, without the ability to process ARP requests and generate ARP replies, no other router could send your router Ethernet frames. Therefore, your router must generate and process ARP requests and replies. To lessen the number of ARP requests sent out, you are required to cache ARP replies. Cache entries should time out after 15 seconds to minimize staleness. The provided ARP cache class already times the entries out for you.
When forwarding a packet to a next-hop IP address, the router should first check the ARP cache for the corresponding MAC address before sending an ARP request. In the case of a cache miss, an ARP request should be sent to a target IP address about once every second until a reply comes in. If the ARP request is sent five times with no reply, an ICMP destination host unreachable is sent back to the source IP as stated above. The provided ARP request queue will help you manage the request queue.
In the case of an ARP request, you should only send an ARP reply if the target IP address is one of your router's IP addresses. In the case of an ARP reply, you should only cache the entry if the target IP address is one of your router's IP addresses. Note that ARP requests are sent to the broadcast MAC address (ff-ff-ff-ff-ff-ff). ARP replies are sent directly to the requester's MAC address.
Testing and Debugging
The above test case does not include Destination Host Unreachable , Destination Unreachable and Protocol Unreachable tests. To do these three tests, you may use test4 at cps114.cod.cs.duke.edu . Before you start these tests, you need to reconfigure your router/rtable. Let's take Figure 1 as an example.
Suppose your topology is shown in Figure 1, the allocated IP block is 171.67.243.176/29 (8 IP addresses). Packets heading to this IP block will be routed to your router. This IP block consists of 4 /31 blocks. They are 171.67.243.176/31 (connected to eth0), 171.67.243.178/31, 171.67.243.180/31 (connected to eth1) and 171.67.243.182/31 (connected to eth2). 171.67.243.178/31 is not connected to any interface.
171.67.243.179 171.67.243.178 255.255.255.254 eth1
to your routing table, once your router receives a packet heading to 171.67.243.179, it will send ARP request for 171.67.243.178 through eth1. There will be no reply since 171.67.243.178 does not exist at all. After 5 ARP requests without any reply, a Destination Host Unreachable ICMP packet will be generated by your router. At this point, your route/rtable should look like
0.0.0.0 172.24.74.17 0.0.0.0 eth0 171.67.243.181 171.67.243.181 255.255.255.255 eth1 171.67.243.183 171.67.243.183 255.255.255.255 eth2 171.67.243.179 171.67.243.178 255.255.255.254 eth1
For the Destination Unreachable test, We do following changes to the above routing table. First, we remove the default route. Second we remove the routing table entry for 171.67.243.179. Third, we add a entry for any PC in Figure 1. For example, if any PC is cps114.cod.cs.duke.edu , we add a entry for its IP address (152.3.145.121) to the routing table. After these three changes, your routing table should look like.
152.3.145.121 172.24.74.17 255.255.255.0 eth0 171.67.243.181 171.67.243.181 255.255.255.255 eth1 171.67.243.183 171.67.243.183 255.255.255.255 eth2
Right now, your router/rtable is ready for the Destination Unreachable test. You may simply send a UDP packet heading for 171.67.243.179 from cps114.cod.cs.duke.edu (152.3.145.121). Your router should be able to generate a Destination Unreachable ICMP packet and send it to cps114.cod.cs.duke.edu . At this point, you may think about why do we do the above three modifications. Try not to delete the default route, what do you find?
For the Protocol Unreachable test, you may simply send one UDP packet to any of your router interfaces. Your router should be able to generate a protocol unreachable packt and send it to you.
For the Destination Host Unreachable test, Destination Unreachable test and Protocol Unreachable tests, you can log on to cps114.cod.cs.duke.edu with your cs appartment account and use test4 to send UDP packets and receive ICMP feedbacks. You need to create and modify config.xml . <dst> stands for your UDP packet's destination address, <intf> is the interface IP addresses of your router. Then run the test case as following. xwy@cps114:~$ test4 config.xml This test4 sends 3 UDP packets to your specified IP address, grabs received ICMP packets and check these packets' source addresses, ICMP type and code fields.
- Run the command make submit , this should create a file called router.tar.gz.
- Upload router.tar.gz to the lab2 assignment on Blackboard .
Collaboration policy
You can discuss with anyone, but you must not look at each other's code, or copy code from others.
Acknowledgement
CSEE 4119: An Introduction to Computer Networks (Spring 2022)
Description.
The course will cover the core elements of modern Internet technology and protocols, including the application, transport, network, link layers and physical layers, for both wired and wireless networks. Coverage roughly corresponds to Chapters 1-8 of the textbook and additional instructor-provided resources.
MW, 5.40 - 6.55 pm ET online and in person
Instructional Staff
James Kurose and Keith Ross, Computer Networking - A Top-Down Approach , 8th edition (new!); Book web site
Class Mailing Lists and Other Resources
- Homework assignments are submitted via Courseworks (Canvas) .
- The Courseworks list will be used for announcements. Slack and Ed will be used for discussion.
- How to Email Your Professor (without being annoying AF)
Grading and Late Policies
(Percentages may be adjusted.)
All homeworks are due by the date and time specified in the assignment (usually one or two weeks after they are issued). Homework submissions will be electronic, through CourseWorks. Complete instructions will be given with each homework.
All submissions must be in PDF format, e.g., using Word or LaTeX. Scanned handwritten assignments are strongly discouraged, and scanned solutions written in pencil are not acceptable at all. Any hand-drawn figures must be clearly legible. Camera screen shots are not permitted; please use screen capture programs such as MacOS "Grab".
You can submit your assignment multiple times, but the last submission is what counts. Each submission will be time stamped. Proper submission is your responsibility; we strongly urge you to make sure you understand the submission process and submit early. You can always submit again up until the deadline, so we strongly urge you to submit well before the deadline and then submit again if you have a more updated assignment to submit later.
You are allowed a total of 7 late days , to be used as you wish throughout the semester, except that you can use only at most two (2) late days for each assignment. That means you can be five days (24 hour periods) late for Homework 2 (for example), or one day late for each of the first five homework assignments, with no point penalty. Each late day entitles you to 24 hours beyond the submission deadline. Once you have exhausted your five late days, each day (24-hour period) or partial day late incurs a 20% penalty. There are no partial late days, either for partial submission or for partial days. Late days are counted based on the last submission. In other words, if you hand in a partial assignment before the due date and a full assignment two days after the due date, you will be assessed two late days. If you do not hand in your assignment at all, you will get zero points, but lose no late days.
Solutions will be posted approximately five days after the submission deadline. No assignments will be accepted after the solution has been posted.
No other extensions will be given, except for medical emergencies certified by University Health Services or a family emergency.
Naturally, you may hand in incomplete assignments for partial credit by the deadline.
Also see the Columbia Policies and Procedures Regarding Academic Honesty .
All students or groups whose assignments are determined to be obviously very similar will receive a zero on the respective homework assignment for the first offense, and will receive an F for the course for the second offense ("all" means both the copy-er and copy-ee). More serious cases of cheating, such as copying someone's work without their knowledge or cheating on exams, will result in the person cheating receiving an F. In addition, offenses will be reported to the Dean's office, which may result in further disciplinary action, including suspension or expulsion from the program. Penalties will be given without discussion or warning; the first notice you receive may be a letter from the Dean. Note that you are responsible for not leaving copies of your assignments lying around and for protecting your files accordingly.
We would like the course to run smoothly and we'd like you to enjoy the course. Feel free to let us know what you find good and interesting about the course. Let us know sooner about the reverse. See us during office hours, leave us a note, or send us email. We appreciate that video courses can be more challenging (and less fun), so your feedback and suggestions are particularly valuable this semester.
- The Urban, Infrastructural Geography Of The Cloud
- Submarine cable map
- Undersea cables
- 9 things you didn't know about Google's undersea cable
- Feature SemiconductorsOptoelectronics Is Keck's Law Coming to an End?
- cgi-bin tutorial
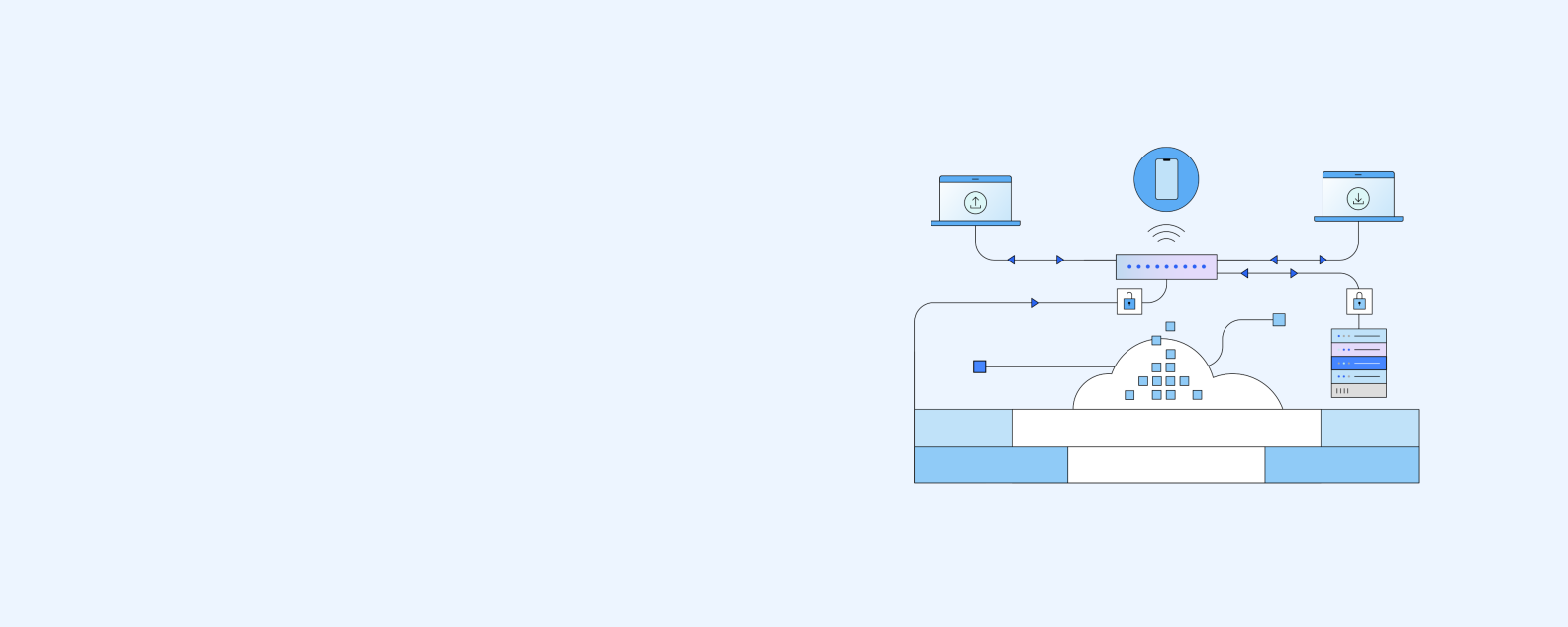
A computer network comprises two or more computers that are connected—either by cables (wired) or wifi (wireless)—with the purpose of transmitting, exchanging, or sharing data and resources.
You build a computer network by using hardware (for example, routers, switches, access points, and cables) and software (for example, operating systems or business applications).
Geographic location often defines a computer network. For example, a LAN (local area network) connects computers in a defined physical space, like an office building, whereas a WAN (wide area network) can connect computers across continents. The internet is the largest example of a WAN, connecting billions of computers worldwide.
You can further define a computer network by the protocols it uses to communicate, the physical arrangement of its components, how it controls traffic, and its purpose.
Computer networks enable communication for every business, entertainment, and research purpose. The internet, online search, email, audio and video sharing, online commerce, live-streaming, and social networks all exist because of computer networks.
Read how desktop as a service (DaaS) enables enterprises to achieve the same level of performance and security as deploying the applications on premises.
Register for the guide on app modernization
As networking needs evolved, so did the computer network types that serve those needs. Here are the most common and widely used computer network types:
LAN (local area network): A LAN connects computers over a relatively short distance, allowing them to share data, files, and resources. For example, a LAN may connect all the computers in an office building, school, or hospital. Typically, LANs are privately owned and managed.
WLAN (wireless local area network): A WLAN is just like a LAN but connections between devices on the network are made wirelessly.
WAN (wide area network): As the name implies, a WAN connects computers over a wide area, such as from region to region or even continent to continent. The internet is the largest WAN, connecting billions of computers worldwide. You will typically see collective or distributed ownership models for WAN management.
MAN (metropolitan area network): MANs are typically larger than LANs but smaller than WANs. Cities and government entities typically own and manage MANs.
PAN (personal area network): A PAN serves one person. For example, if you have an iPhone and a Mac, it’s likely you’ve set up a PAN that shares and syncs content—text messages, emails, photos, and more—across both devices.
SAN (storage area network): A SAN is a specialized network that provides access to block-level storage—shared network or cloud storage. To the user, it looks, and works like a storage drive that’s physically attached to a computer. (For more information on how a SAN works with block storage, see Block Storage: A Complete Guide ).
CAN (campus area network): A CAN is also known as a corporate area network. A CAN is larger than a LAN but smaller than a WAN. CANs serve sites such as colleges, universities, and business campuses.
VPN (virtual private network): A VPN is a secure, point-to-point connection between two network end points (see ‘nodes’ below). A VPN establishes an encrypted channel that keeps a user’s identity and access credentials, as well as any data transferred, inaccessible to hackers.
The following are some common terms to know when discussing computer networking:
IP address : An IP address is a unique number assigned to every device connected to a network that uses the Internet Protocol for communication. Each IP address identifies the device’s host network and the location of the device on the host network. When one device sends data to another, the data includes a ‘header’ that includes the IP address of the sending device and the IP address of the destination device.
Nodes : A node is a connection point inside a network that can receive, send, create, or store data. Each node requires you to provide some form of identification to receive access, like an IP address. A few examples of nodes include computers, printers, modems, bridges, and switches. A node is essentially any network device that can recognize, process, and transmit information to any other network node.
Routers : A router is a physical or virtual device that sends information that is contained in data packets between networks. Routers analyze data within the packets to determine the best way for the information to reach its ultimate destination. Routers forward data packets until they reach their destination node.
Switches : A switch is a device that connects other devices and manages node-to-node communication within a network, ensuring that data packets reach their ultimate destination. While a router sends information between networks, a switch sends information between nodes in a single network. When discussing computer networks, ‘switching’ refers to how data is transferred between devices in a network. The three main types of switching are as follows:
Circuit switching , which establishes a dedicated communication path between nodes in a network. This dedicated path assures the full bandwidth is available during the transmission, meaning that no other traffic can travel along that path.
Packet switching involves breaking down data into independent components that are called packets, which because of their small size, make fewer demands on the network. The packets travel through the network to their end destination.
Message switching sends a message in its entirety from the source node, traveling from switch to switch until it reaches its destination node.
Ports : A port identifies a specific connection between network devices. Each port is identified by a number. If you think of an IP address as comparable to the address of a hotel, then ports are the suites or room numbers within that hotel. Computers use port numbers to determine which application, service, or process should receive specific messages.
Network cable types : The most common network cable types are Ethernet twisted pair, coaxial, and fiber optic. The choice of cable type depends on the size of the network, the arrangement of network elements, and the physical distance between devices.
The wired or wireless connection of two or more computers for the purpose of sharing data and resources form a computer network. Today, nearly every digital device belongs to a computer network.
In an office setting, you and your colleagues may share access to a printer or to a group messaging system. The computing network that allows this is likely a LAN or local area network that permits your department to share resources.
A city government might manage a city-wide network of surveillance cameras that monitor traffic flow and incidents. This network would be part of a MAN or metropolitan area network that allows city emergency personnel to respond to traffic accidents, advise drivers of alternate travel routes. And even send traffic tickets to drivers who run red lights.
The Weather Company worked to create a peer-to-peer mesh network that allows mobile devices to communicate directly with other mobile devices without requiring wifi or cellular connectivity. The Mesh Network Alerts project allows the delivery of life-saving weather information to billions of people, even without an internet connection.
The internet is actually a network of networks that connects billions of digital devices worldwide. Standard protocols allow communication between these devices. Those protocols include the hypertext transfer protocol (the ‘http’ in front of all website addresses). Internet protocols (or IP addresses) are the unique identifying numbers that are required of every device that accesses the internet. IP addresses are comparable to your mailing address, providing unique location information so that information can be delivered correctly.
Internet Service Providers (ISPs) and Network Service Providers (NSPs) provide the infrastructure that allows the transmission of packets of data or information over the internet. Every bit of information that is sent over the internet doesn’t go to every device connected to the internet. It’s the combination of protocols and infrastructure that tells information exactly where to go.
Computer networks connect nodes like computers, routers, and switches by using cables, fiber optics, or wireless signals. These connections allow devices in a network to communicate and share information and resources.
Networks follow protocols, which define how communications are sent and received. These protocols allow devices to communicate. Each device on a network uses an Internet Protocol or IP address, a string of numbers that uniquely identifies a device and allows other devices to recognize it.
Routers are virtual or physical devices that facilitate communications between different networks. Routers analyze information to determine the best way for data to reach its ultimate destination. Switches connect devices and manage node-to-node communication inside a network, ensuring that bundles of information traveling across the network reach their ultimate destination.
Computer network architecture defines the physical and logical framework of a computer network. It outlines how computers are organized in the network and what tasks are assigned to those computers. Network architecture components include hardware, software, transmission media (wired or wireless), network topology, and communications protocols.
Main types of network architecture
There are two types of network architecture: peer-to-peer (P2P) and client/server . In P2P architecture, two or more computers are connected as “peers,” meaning that they have equal power and privileges on the network. A P2P network does not require a central server for coordination. Instead, each computer on the network acts as both a client (a computer that needs to access a service) and a server (a computer that serves the needs of the client accessing a service). Each peer makes some of its resources available to the network, sharing storage, memory, bandwidth, and processing power.
In a client/server network, a central server or group of servers manage resources and deliver services to client devices in the network. The clients in the network communicate with other clients through the server. Unlike the P2P model, clients in a client/server architecture don’t share their resources. This architecture type is sometimes called a tiered model because it's designed with multiple levels or tiers.
Network topology
Network topology refers to how the nodes and links in a network are arranged. A network node is a device that can send, receive, store, or forward data. A network link connects nodes and may be either cabled or wireless links.
Understanding topology types provides the basis for building a successful network. There are several topologies but the most common are bus, ring, star, and mesh:
A bus network topology is when every network node is directly connected to a main cable.
In a ring topology , nodes are connected in a loop, so each device has exactly two neighbors. Adjacent pairs are connected directly; nonadjacent pairs are connected indirectly through multiple nodes.
In a star network topology , all nodes are connected to a single, central hub and each node is indirectly connected through that hub.
A mesh topology is defined by overlapping connections between nodes. You can create a full mesh topology, where every node in the network is connected to every other node. You can also create partial mesh topology in which only some nodes are connected to each other and some are connected to the nodes with which they exchange the most data. Full mesh topology can be expensive and time-consuming to run, which is why it's often reserved for networks that require high redundancy. Partial mesh provides less redundancy but is more cost-effective and simpler to run.
Computer network security protects the integrity of information that is contained by a network and controls who access that information. Network security policies balance the need to provide service to users with the need to control access to information.
There are many entry points to a network. These entry points include the hardware and software that comprise the network itself as well as the devices used to access the network, like computers, smartphones, and tablets. Because of these entry points, network security requires using several defense methods. Defenses may include firewalls—devices that monitor network traffic and prevent access to parts of the network based on security rules.
Processes for authenticating users with user IDs and passwords provide another layer of security. Security includes isolating network data so that proprietary or personal information is harder to access than less critical information. Other network security measures include ensuring hardware and software updates and patches are performed regularly. This educates network users about their role in security processes, and staying aware of external threats executed by hackers and other malicious actors. Network threats constantly evolve, which makes network security a never-ending process.
The use of public cloud also requires updates to security procedures to ensure continued safety and access. A secure cloud demands a secure underlying network.
Read about the top five considerations for securing the public cloud.
As noted above, a mesh network is a topology type in which the nodes of a computer network connect to as many other nodes as possible. In this topology, nodes cooperate to efficiently route data to its destination. This topology provides greater fault tolerance because if one node fails, there are many other nodes that can transmit data. Mesh networks self-configure and self-organize, searching for the fastest, most reliable path on which to send information.
Type of mesh networks:
There are two types of mesh networks—full mesh and partial mesh.
- In a full mesh topology , every network node connects to every other network node, providing the highest level of fault tolerance. However, it costs more to run. In a partial mesh topology, only some nodes connect, typically those that exchange data most frequently.
- A wireless mesh network may consist of tens to hundreds of nodes. This type of network connects to users over access points spread across a large area.
Load balancers efficiently distribute tasks, workloads, and network traffic across available servers. Think of load balancers like air traffic control at an airport. The load balancer observes all traffic coming into a network and directs it toward the router or server that is best equipped to manage it. The objectives of load balancing are to avoid resource overload, optimize available resources, improve response times, and maximize throughput.
For a complete overview of load balancers, see Load Balancing: A Complete Guide .
A content delivery network (CDN) is a distributed server network that delivers temporarily stored, or cached, copies of website content to users based on the user’s geographic location. A CDN stores this content in distributed locations and serves it to users as a way to reduce the distance between your website visitors and your website server. Having cached content closer to your end users allows you to serve content faster and helps websites better reach a global audience. CDNs protect against traffic surges, reduce latency, decrease bandwidth consumption, accelerate load times. And lessen the impact of hacks and attacks by introducing a layer between the end user and your website infrastructure.
Live-streaming media, on-demand media, gaming companies, application creators, e-commerce sites—as digital consumption increases, more content owners turn to CDNs to better serve content consumers.
Avoid network traffic jams and decrease latency by keeping your data closer to your users with Akamai’s content delivery network on IBM Cloud®.
IBM Cloud® Load Balancers enable you to balance traffic among servers to improve uptime and performance.
Gain more control of your cloud infrastructure and protect your servers and network.
IBM Hybrid Cloud Mesh offers simple, secure, and predictable application-centric connectivity.
Learn how load balancing optimizes website and application performance.
An introduction to content delivery networks and how they improve customer satisfaction by optimizing website and mobile app performance.
Answers to pressing questions from IT architects on public cloud security.
IBM NS1 Connect provides fast, secure connections to users anywhere in the world with premium DNS and advanced, customizable traffic steering. NS1 Connect’s always-on, API-first architecture enables your IT teams to more efficiently monitor networks, deploy changes and conduct routine maintenance.
What computer networks are and how to actually understand them

by Sumedh Nimkarde
Whether you are new to the world of development, or have been building things for a long time — or even if you’re a person who just likes computers and uses the internet daily — you’ve got to know the basics of networking and specifically Computer Networks.
If you like digging more into servers, their security, and how you connect to your servers from a remote client, all of this requires some knowledge of computer networks and their components. I have tried to cover most of the topics concerning computer networks in this article.
Also, from here, I will refer to “computer networks” simply as “networks”.
Let us first look at my working definition of computer networks:
Computer networks can be defined as the exchange of network packets between computing machines across the world with the help of data lines like wire cables, optical fibers, etc.
The Internet is a kind of computer network. Sorta.
We will take a look at some commonly used terms and components and how they function in a computer network, some of which are in the above diagram.
Commonly used terms in Computer Networks
Nodes in computer networks mean any computing device such as computers, mobile phones, tablets, etc which try to send and receive network packets across the network to another similar device.
Network Packets
Network packets are nothing but the information or units of data that a source node wants to send/receive to/from the destination node. In this article, network packets/data packets all convey the same meaning.
Internet Protocol (IPs)
Consider you want to send a birthday gift to your friend on their birthday, where will you send it? To their street address right?
Same is the case here. The early computer scientists wanted to identify computers on the internet with a unique number, something like a telephone numbers today. So, they came up with the concept of TCP/IP.
An IP of a computer device is the address of that device in a computer network. Technically, it is a 32-bit number used which identifies devices in a network. All the communication to and fro from the device in that network will be done in terms of its IP address.
Consider that you are uploading a file to any site or say to Google drive.
Talking at the lowest level of network communication, your file is converted to packets and each packet has the destination node address with it which is nothing but the IP address.
On a higher level, IP addresses are classified into two types:
- IPv4 : IPv4 addresses are 32 bits (four bytes) as explained in the definition. An example of the IPv4 address would be 104.244.42.129 which is the IPv4 address of twitter.com . They are stable to use and hence are used today to identify machines in the world.
- IPv6 : IPv6 addresses are pretty new to the world and are basically eight hexadecimal numbers separated by “:”. An example of IPv6 address would be 2001:0cb8:85a3:0000:0000:8a2e:0370:7334 . They are unstable and hence not used widely yet. The web is still using IPv4 due to its stability and there is no estimate when we will start to use IPv6 since it is not stable for now.
IPv4 is classified into five classes named Class A, B, C, D, E.
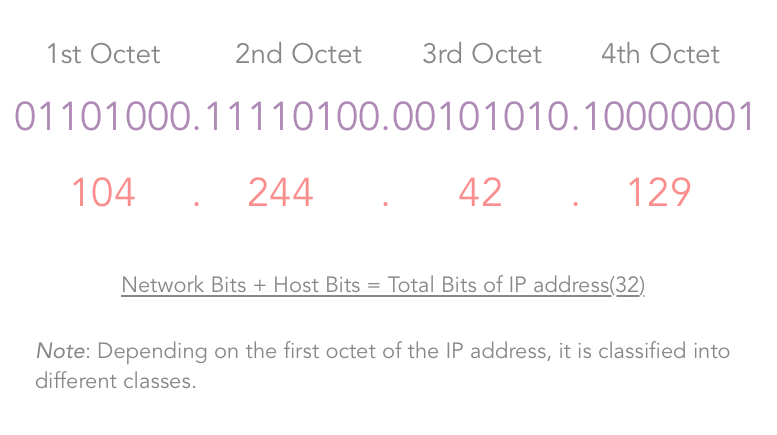
Class A : As shown in the third column of the above image, for a Class A IP addresses, the first bit of the first octet of the IP address is constant and is “0”.
The Second column indicates the Network bits and the host bits of the corresponding class of IP address. Consider in case of a Class A IP address, we have the following formula:
Number of networks/subnets = 2^(# of network bits) .
Number of valid hosts in each subnet = 2^(# of host bits) — 2 .
The number of network bits and host bits are decided by the default subnet mask of the class of IP address.
The default subnet mask for a class A IP addresses is 255.0.0.0, that is 11111111.00000000.0000000.00000000 . Thus, for class A:
Network bits = 8, and Host bits = 24.
Since Network bits = 8 , Host bits = 24 , their sum has to be 32, since IPv4 addresses are of 32 bits. But, since we are using the one bit (first bit in the first octet) to identify the class:
Number of usable network bits = Number of network bits — Number of constant bits = 8–1 = 7
Thus, the Number of possible networks in Class A = 2^7 — 2 = 126 and,
Number of possible hosts (that is devices that can be connected to the network) per network in Class A = 2^24-2 = 16277214 .
Now, here, for class A, you may wonder why I subtracted an extra 2 from the number of possible networks. It is because, for class A, 127.x.y.z was kept reserved. For other classes, the usual formula is used.
Thus, IP addresses in class A range from 1.x.x.x to 126.x.x.x .
Class B: the case is similar with Class B. The only difference is 2 bits of the first octet are constant (10) and they identify the class of IP address that is class B. All other calculations are same, and I am not mentioning them here since they are easy to grab from the table above. They range from 128.0.x.x to 191.255.x.x .
Class C : 3 bits of the first octet are constant (110) and they identify the class as class C. They range from 192.0.0.x to 223.255.255.x .
Class D and Class E : Class D and Class E are used for experimental purposes.
IPv4 addresses are mainly of two types:
- Static : These IP addresses are the ones which remain constant for a device over time. Examples of these are the remote servers that we use to host our apps, websites, etc. where we use the ssh client to ssh to our server.
- Dynamic : Generally, these are the IP addresses that a common computer in an Internet network is assigned. Try switching your router off and you will see a change in the IP address of your computer! (But only after reading this article ?). Now, you may be thinking who allocates these IP addresses? It is the DHCP (Dynamic Host Configuration Protocol) server which is explained briefly further in this article.
Note : A device can have multiple IP addresses at the same time. Consider a device connected to two networks, wifi as well as any LAN network — it will have two IP addresses. This implies that the IP addresses are assigned to the interfaces and not directly to the computer.
Okay, so far so good. Let’s continue.
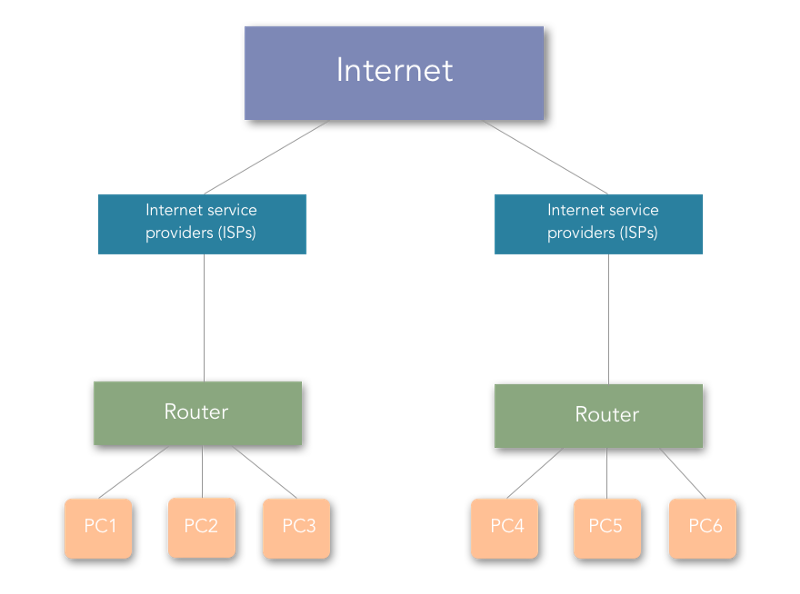
As its name suggests, a Router is a hardware component that takes care of routing packets. It determines which node the packet came from and which destination node the sender node want to send it to. No computer knows where other computers are located, and packets are not sent to every computer. A Router identifies the destination node address to which a network packet has to be sent and it forwards it to the desired address.
Routers have a specific “Routing Protocol” which defines the format in which they exchange data with another router or networking nodes. In other words, routing protocol defines how routers communicate with each other.
Routers build up a “Routing Table” which identifies the most optimized paths to be taken in the network while sending packets.
Technically, a routing table is just a table with the list of “routes” from one router to other. Each route consists of the address of the other routers/nodes in the network and how to reach them.
Above is an example of a routing table. The key points to take a note of here are:
- Destination: This is the IP address of the destination node. It indicates where the network data packet should end up.
- Gateway: Gateway is the component which connects two networks. Consider that you have a router connected to another router. Each of the routers has devices connected to it. So, the address of the last router (say R1 here) after which the network packet enters the other network (say R2’s network) is called the gateway. Usually, the gateways are nothing but the routers. Let me give one more example: say that your room is one network and your sibling’s room next to yours is another network, then the “door” between the two rooms can be considered the gateway. People sometimes refer to the “ routers ” as the gateway, because, that’s what they are, “ a gateway to another network ”.
- Genmask/Subnet mask: It is nothing but the net/subnet mask. A subnet mask is a number which when combined with an IP address allows you to divide the IP space into smaller and smaller chunks for use in both physical and logical networks. The explanation of how subnet mask calculations happen is beyond the scope of this article.
- Flags: Different flags have a different meaning. For example, in the first route, “U” in “UG” means the route is UP, whereas “G” in “UG” means GATEWAY. Since the route signifies a GATEWAY, it is a door to the other network. Whenever we send any data through this route, it gets sent to another network.
- Iface (Network interface): Network interface refers to the network that the route defined in the routing table is having the destination computer in. That is if you are connected to Wifi, then it would be “wlan” and when you are connected to a LAN, then it would be “eth”.
So this is the way a router works, with the help of Routing Protocol and Routing Table .
All good up to now. But, you must be thinking —
“Okay! But hey, we are learning about components here. I need to stitch them together and get to know how the internet works.”
Cool! Some more terms and you will have a proper understanding of how everything goes.
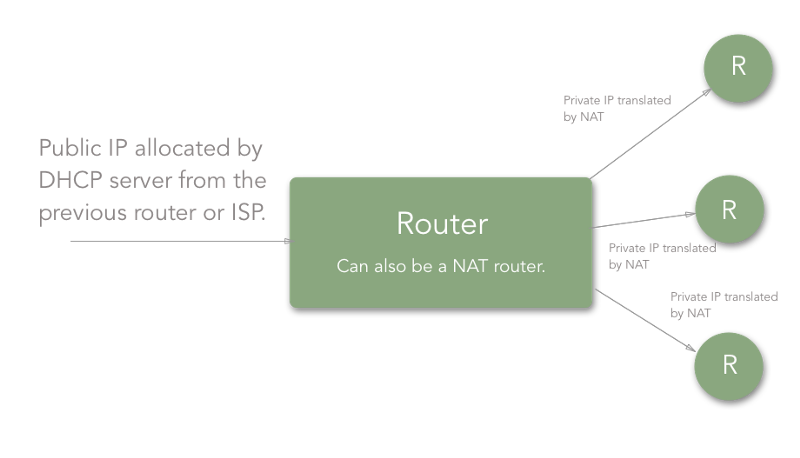
Network Address Translation (NAT)
Network address translation is a technique used by routers to provide internet service to more devices with less usage of public IPs. Thus, a router is assigned a single IP address by the ISP and it assigns the private IPs to all the devices connected to it. NAT helps the ISPs provide internet access to more consumers.
Thus, if you are connected to the router of your house, your public IP will be visible to the world, but the private one will not. Whatever network packets are communicated will be addressed by your public IP (that is the public IP assigned to the router).
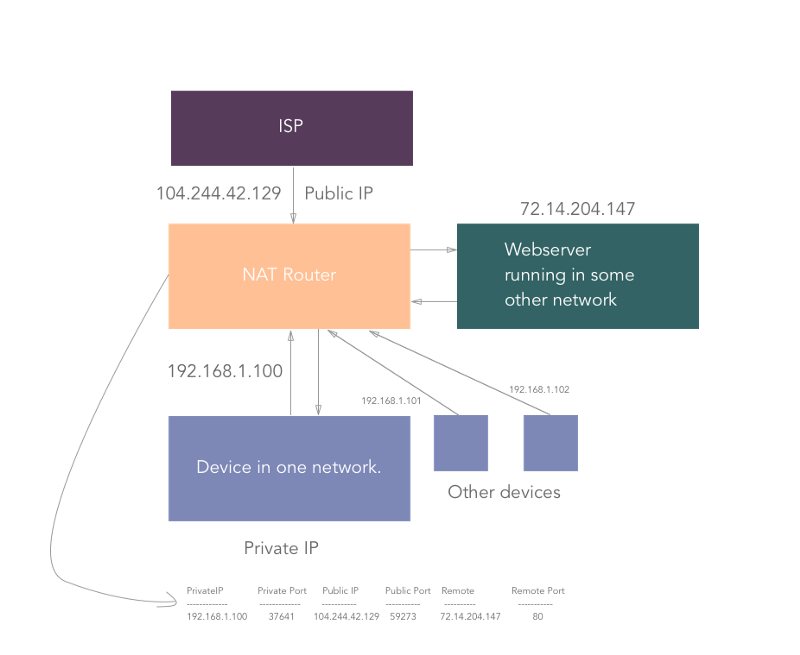
Consider the above figure. Let’s say that in your home network, you are trying to access medium.com (remote static IP: 72.14.204.147 ) , from your computer (private IP: 192.168.1.100 ).
So, for your computer, the connection looks like:
192.168.1.100:37641 → 72.14.204.147:80 .
“37641” is the random port number assigned by NAT router to your device/computer. (When there is network communication between daemons running on different ports on a computer, the respective port is used by NAT). Each outbound connection gets an assigned port by the NAT router.
The connection is established in NAT like:
But, since the outside world of the network doesn’t know about your private address, the connection looks like the following to medium.com :
104.244.42.129:59273 → 72.14.204.147:80 .
That way, we achieve assigning a higher number of IP addresses without wasting many public IPs.
Now, when medium.com sends the response back to 104.244.42.129:59273 , it travels all the way to your home router which then looks up for the respective private IP and private port and redirects the packet to your device/computer.
Note : NAT is a generalized concept. NAT can be achieved as 1:1, 1:N where 1, N are the number of IP addresses in the network. A technique called as “IP Masquerading” is a 1:N NAT.
Dynamic Host Configuration Protocol (DHCP)
Dynamic Host Configuration Protocol or DHCP is responsible for assigning dynamic IP addresses to the hosts. The DHCP server is maintained by the ISP or previous router if there is a chain of routers to reach the host.
Thus, allocation of IP addresses is carried out by the DHCP server. Generally, ISP maintains a DHCP server and the routers in our houses get assigned a public IP from the DHCP server.
Note : Whenever a router or say a DHCP server maintained by an ISP or router restarts, the IP address allocation starts again and devices are allocated IPs which are different than the previous ones.

Domain Name System/Server
We have already discussed that any machine is identified by the IP address.
Okay, so you are running a web server on your localhost on your machine. If you have dug around in the hosts on any Linux machine, you would have encountered something like this:
which means that even if you type 127.0.0.1 in your browser’s URL bar, it would mean the same as localhost .
Similar to the above, the websites you use daily are web servers running on some remote instance/node having a static IP address. So, typing that IP address in your browser’s URL bar will take you to the website?
Yes, surely it will. But, are you a superhuman to remember the IP addresses of thousands of sites?
Thus, there come the domains that we use, say medium.com, twitter.com, behance.net, codementor.io, etc.
A Domain Name Server is a server having huge records of domain name mapping IP addresses which searches for the domain input and returns the respective IP address of the machine on which the website you want to access is hosted.
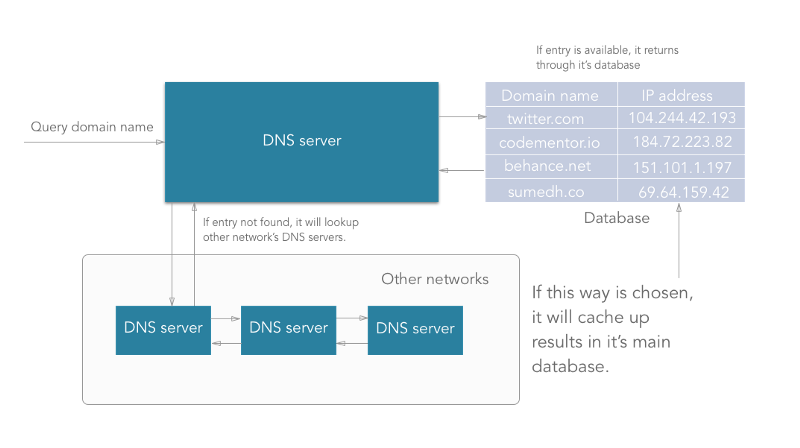
How does DNS work actually?
- DNS is managed by your ISP (internet service provider).
- When we type an URL in the address bar, the data packets travel through your router, maybe multiple routers to your ISP where your DNS server is present.
- DNS server present at the ISP looks up for the domain in its database. If an entry is found, then it returns it.
- If any entry is not found in its primary database that it maintains, the DNS server will travel through the internet to another DNS server maintained by another ISP and check if the entry is available in that another DNS server’s database. Along with returning the IP address taken from another DNS, it will update the primary database with this new entry also.
- Thus, sometimes (very rarely) a DNS server may have to traverse to multiple DNS servers to get a matching entry.
- If after traversing a lot of DNS servers across the internet, it doesn’t get a matching entry, then the DNS server throws an error indicating that the “domain name is invalid or doesn’t exist”.
The Internet Corporation for Assigned Names and Numbers (ICANN) is a consortium (a non-profit corporation) that manages the assignment of domain names and IP address ranges on behalf of the community.
A domain is divided into three parts as shown in the following figure.
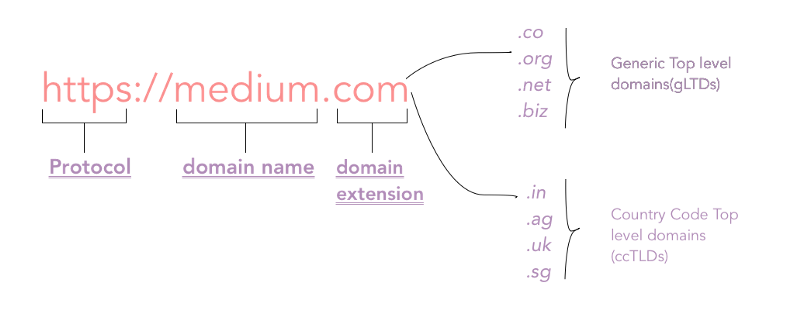
- Protocol : The protocol used to access the website, for example, HTTP, HTTPS, etc.
- Domain name : The main domain name in our domain. This can be anything that is available as per the ICANN registry.
- Domain extension : This is one which is considered important while buying a domain. Generally, it is classified into two types:
- Generic Top-level Domains (gTLDs) : This includes most popular domain extensions like .com, .org, .net, .edu, .co, etc.
- Country Code Top-level Domains(ccTLDs) : These indicate that the domain is related to the country code specified in the domain extension. For example, “.in” indicates that the website is originated from India. Also, some of the ccTLDs require that the person purchasing the domain should be from the same country. Most of the small country code extensions are not searchable from outside that country.
Internet Service Providers (ISPs)
Internet Service Providers are the companies that provide everyone Internet. The article you are reading now is because of the internet that your ISP provides you.
ISPs provide internet, handle routing your requests to the correct destination, resolve domain names with the help of DNS cache that they maintain, and handle all this network infrastructure which enables us to use the internet.
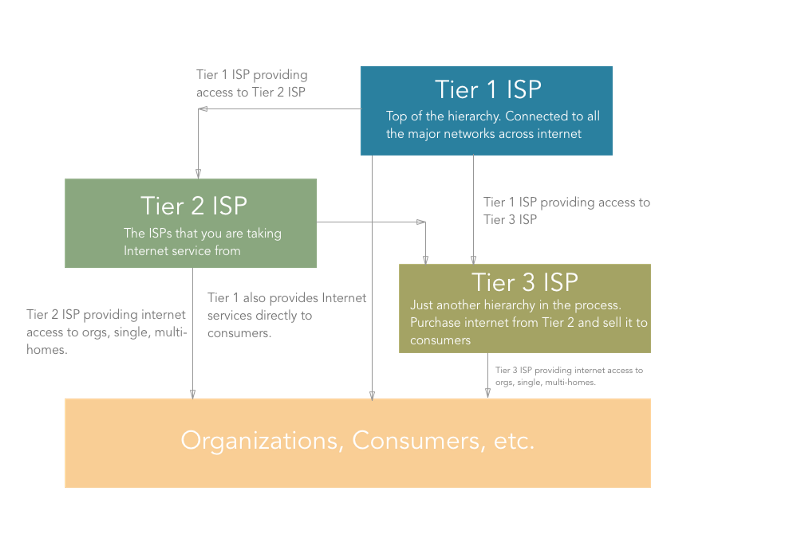
ISP is a hierarchical thing working across the internet. There are certain types of ISPs namely Tier 1, Tier 2, Tier 3 ISPs.
- Tier 1 ISPs are the ones which connect major networks on the internet. Consider them as the major highways of the internet. They are connected to almost every network on the internet. Also, they provide internet access to the Tier 2 ISPs. ex. CERFNet, UUNet, PSINet. They are also called Network Service Providers. These ISPs are connected to each other by means of large cables going beneath the sea.
- The Tier 2 (Regional) ISPs are the ones who primarily provide Internet services to organizations, consumers (that is “us”) or the Tier 3 ISPs. The internet connection you are using is from a Tier 2 ISP. However, organizations can also get Internet access from Tier 1 ISPs.
- Tier 3 (Local) ISPs are just like Tier 2. It’s just one more level of hierarchy out there that purchases bandwidth from Tier 2 ISP and sells it to consumers.
The traffic that goes through your router also goes through Tier 3 (if present), Tier 2, and ultimately through Tier 1 ISPs all the way to another network.
Woot Woot! I am happy that you are still with me. We will put all the things together now.
Putting all of the above things together
Up until now, we have learned about all the components needed to make everything work. Now, we will glue them together.
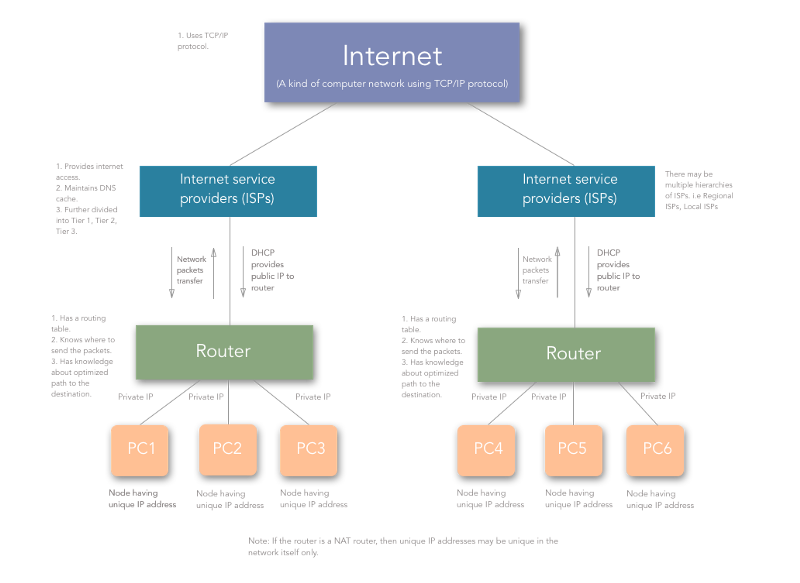
Let’s summarize all the things we’ve learned:
- When a computer/device comes online, it gets a private IP assigned by the router. The router gets a public IP from the ISP.
- Other devices in the network are allocated unique private IPs.
- ISPs are the ones who are present across the world and are connected to each other. They sell Internet services to the regional and local ISPs, from whom we, the consumers, purchase Internet.
- Thus, when a device tries to establish a network connection with some other device on some other network, it does it with the identity of its gateway (the router). The router then maps the private IP and private port number with the public IP and random high integer public port number.
- The router then sends the packets to the desired destination where some other router or gateway does the same thing as the previous router and analyses which computer/device that packet came from.
- The remote computer/device responds by sending the destination as the public IP and public port of the router.
- The router then again checks for the private IP and private port and forwards the network packets.
So, this is how the Internet aka A kind of Computer Network using TCP/IP protocol works .
Thanks for reading the article. If you have any questions, please feel free to ask them in the comments below.
If you liked this article, please give me some ? and share it with others. See you in the next one. You are awesome!
Also, if you’d like to support me ?
Buy Sumedh Nimkarde a Coffee - BuyMeACoffee.com Hello, I am Sumedh and my work is to build, break and rebuild things. www.buymeacoffee.com
Thanks a lot again for reading! Feel free to connect with me on Twitter , GitHub .
If this article was helpful, share it .
Learn to code for free. freeCodeCamp's open source curriculum has helped more than 40,000 people get jobs as developers. Get started

Computer Networks and Internet Protocol
Note: This exam date is subjected to change based on seat availability. You can check final exam date on your hall ticket.
Page Visits
Course layout, books and references, instructor bio.

Prof. Soumya Kanti Ghosh

Prof. Sandip Chakraborty
Course certificate.

DOWNLOAD APP

SWAYAM SUPPORT
Please choose the SWAYAM National Coordinator for support. * :
Browse Course Material
Course info.
- Prof. Hari Balakrishnan
Departments
- Electrical Engineering and Computer Science
As Taught In
- Computer Networks
Learning Resource Types
Assignments.

You are leaving MIT OpenCourseWare

Computer Networking: Referencing and Citing
- e-Resources
- Talks & Lectures
- Associations, Tools & Standards
- Connect from Off-Campus
- Referencing and Citing
Referencing and citation

- It is important (morally & legally) to acknowledge someone else’s ideas or words you have used. Academic writing encourages paraphrasing information you have researched and read.
- Paraphrasing means re-wording something you have read in to your own words. If you use someone else’s words or work and fail to acknowledge them – you may be accused of plagiarism and infringing copyright.
- Referencing correctly enables the marker or reader of your assignment to locate the source of the information. They can verify the information or read further on the topic.
- Referencing also allows for you to retrace your steps and locate information you have used for assignments and discover further views or ideas discussed by the author.By referencing clearly and correctly, it demonstrates you have undertaken research on the assignment topic and located relevant information.
Learn important tips for reference and how to reference from our referencing guide, here .
- << Previous: Connect from Off-Campus
- Last Updated: Apr 2, 2024 4:43 PM
- URL: https://usiu-ke.libguides.com/ComputerNetworking
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- Computer Network Tutorial
Basics of Computer Network
- Basics of Computer Networking
- Introduction to basic Networking Terminology
- Goals of Networks
- Basic characteristics of Computer Networks
- Challenges of Computer Network
- Physical Components of Computer Network
Network Hardware and Software
Types of Computer Networks
- LAN Full Form
- How to Set Up a LAN Network?
- MAN Full Form in Computer Networking
- MAN Full Form
- WAN Full Form
- Introduction of Internetworking
- Difference between Internet, Intranet and Extranet
- Protocol Hierarchies in Computer Network
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Introduction of a Router
- Introduction of Gateways
- What is a network switch, and how does it work?
Network Topology
- Types of Network Topology
- Difference between Physical and Logical Topology
- What is OSI Model? - Layers of OSI Model
- Physical Layer in OSI Model
- Data Link Layer
- Session Layer in OSI model
- Presentation Layer in OSI model
- Application Layer in OSI Model
- Protocol and Standard in Computer Networks
- Examples of Data Link Layer Protocols
- TCP/IP Model
- TCP/IP Ports and Its Applications
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- Services and Segment structure in TCP
- TCP Connection Establishment
- TCP Connection Termination
- Fast Recovery Technique For Loss Recovery in TCP
- Difference Between OSI Model and TCP/IP Model
Medium Access Control
- MAC Full Form
- Channel Allocation Problem in Computer Network
- Multiple Access Protocols in Computer Network
- Carrier Sense Multiple Access (CSMA)
- Collision Detection in CSMA/CD
- Controlled Access Protocols in Computer Network
SLIDING WINDOW PROTOCOLS
- Stop and Wait ARQ
- Sliding Window Protocol | Set 3 (Selective Repeat)
- Piggybacking in Computer Networks
IP Addressing
- What is IPv4?
- What is IPv6?
- Introduction of Classful IP Addressing
- Classless Addressing in IP Addressing
- Classful Vs Classless Addressing
- Classless Inter Domain Routing (CIDR)
- Supernetting in Network Layer
- Introduction To Subnetting
- Difference between Subnetting and Supernetting
- Types of Routing
- Difference between Static and Dynamic Routing
- Unicast Routing - Link State Routing
- Distance Vector Routing (DVR) Protocol
- Fixed and Flooding Routing algorithms
- Introduction of Firewall in Computer Network
Congestion Control Algorithms
- Congestion Control in Computer Networks
- Congestion Control techniques in Computer Networks
- Computer Network | Leaky bucket algorithm
- TCP Congestion Control
Network Switching
- Circuit Switching in Computer Network
- Message switching techniques
- Packet Switching and Delays in Computer Network
- Differences Between Virtual Circuits and Datagram Networks
Application Layer:DNS
- Domain Name System (DNS) in Application Layer
- Details on DNS
- Introduction to Electronic Mail
- E-Mail Format
- World Wide Web (WWW)
- HTTP Full Form
- Streaming Stored Video
- What is a Content Distribution Network and how does it work?
CN Interview Quetions
- Top 50 Networking Interview Questions (2024)
- Top 50 TCP/IP interview questions and answers
- Top 50 IP addressing interview questions and answers
- Last Minute Notes - Computer Networks
- Computer Network - Cheat Sheet
- Network Layer
- Transport Layer
- Application Layer
Pre-Requisite: Computer Networking
A computer network is a cluster of computers over a shared communication path that works to share resources from one computer to another, provided by or located on the network nodes.
Uses of Computer Networks
- Communicating using email, video, instant messaging, etc.
- Sharing devices such as printers, scanners, etc.
- Sharing files.
- Sharing software and operating programs on remote systems.
- Allowing network users to easily access and maintain information.
There are mainly five types of Computer Networks
Personal Area Network (PAN)
Local Area Network (LAN)
Campus Area Network (CAN)
Metropolitan Area Network (MAN)
Wide Area Network (WAN)
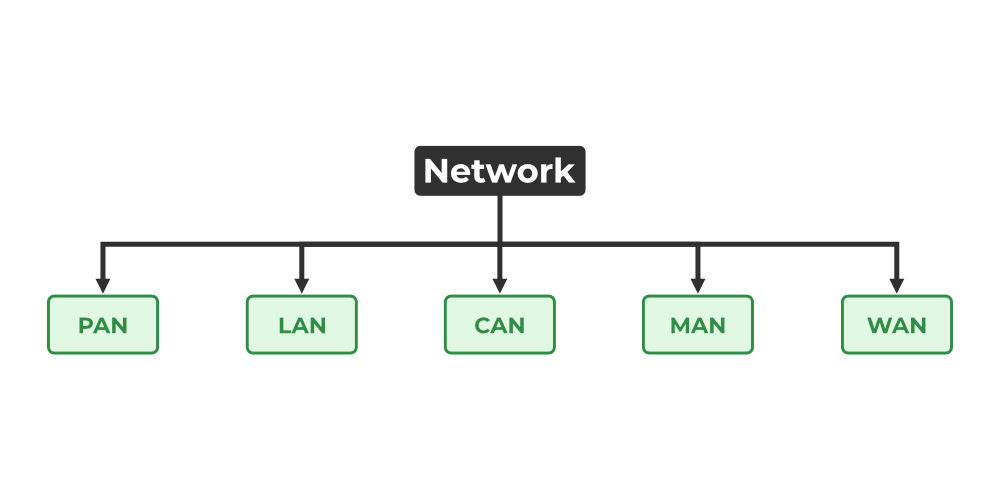
These are explained below.
1. Personal Area Network (PAN)
PAN is the most basic type of computer network. This network is restrained to a single person, that is, communication between the computer devices is centered only on an individual’s workspace. PAN offers a network range of 1 to 100 meters from person to device providing communication. Its transmission speed is very high with very easy maintenance and very low cost.
This uses Bluetooth , IrDA , and Zigbee as technology.
Examples of PAN are USB, computer, phone, tablet, printer, PDA, etc.
2. Local Area Network (LAN)
LAN is the most frequently used network. A LAN is a computer network that connects computers through a common communication path, contained within a limited area, that is, locally. A LAN encompasses two or more computers connected over a server. The two important technologies involved in this network are Ethernet and Wi-fi . It ranges up to 2km & transmission speed is very high with easy maintenance and low cost.
Examples of LAN are networking in a home, school, library, laboratory, college, office, etc.

3. Campus Area Network (CAN)
CAN is bigger than a LAN but smaller than a MAN. This is a type of computer network that is usually used in places like a school or colleges. This network covers a limited geographical area that is, it spreads across several buildings within the campus. CAN mainly use Ethernet technology with a range from 1km to 5km.
Its transmission speed is very high with a moderate maintenance cost and moderate cost.
Examples of CAN are networks that cover schools, colleges, buildings, etc.

4. Metropolitan Area Network (MAN)
A MAN is larger than a LAN but smaller than a WAN. This is the type of computer network that connects computers over a geographical distance through a shared communication path over a city, town, or metropolitan area. This network mainly uses FDDI, CDDI, and ATM as the technology with a range from 5km to 50km. Its transmission speed is average. It is difficult to maintain and it comes with a high cost.
Examples of MAN are networking in towns, cities, a single large city, a large area within multiple buildings, etc.
5. Wide Area Network (WAN)
WAN is a type of computer network that connects computers over a large geographical distance through a shared communication path. It is not restrained to a single location but extends over many locations. WAN can also be defined as a group of local area networks that communicate with each other with a range above 50km.
Here we use Leased-Line & Dial-up technology. Its transmission speed is very low and it comes with very high maintenance and very high cost.
The most common example of WAN is the Internet.
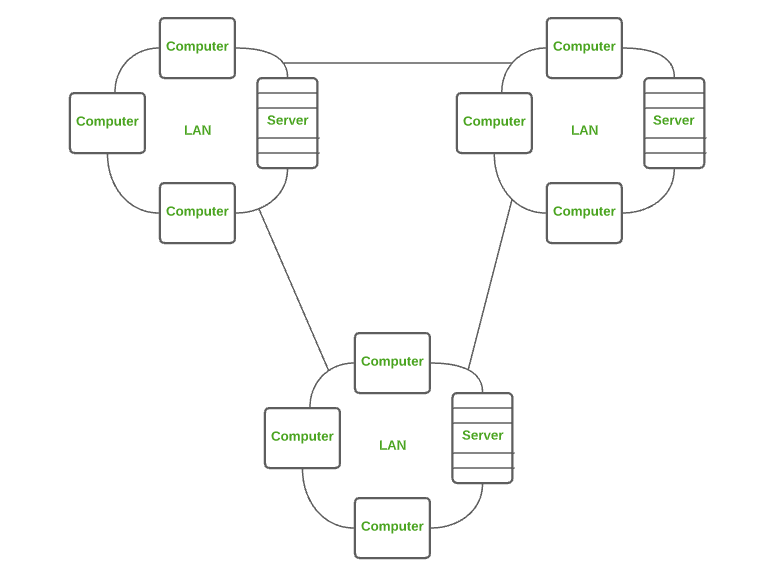
Comparison between Different Computer Networks
Other types of computer networks.
Wireless Local Area Network (WLAN)
Storage Area Network (SAN)
- System-Area Network (SAN)
Passive Optical Local Area Network (POLAN)
Enterprise Private Network (EPN)
Virtual Private Network (VPN)
Home Area Network (HAN)
1. Wireless Local Area Network (WLAN)
WLAN is a type of computer network that acts as a local area network but makes use of wireless network technology like Wi-Fi. This network doesn’t allow devices to communicate over physical cables like in LAN but allows devices to communicate wirelessly.
The most common example of WLAN is Wi-Fi.

There are several computer networks available; more information is provided below.
2. Storage Area Network (SAN)
SAN is a type of computer network that is high-speed and connects groups of storage devices to several servers. This network does not depend on LAN or WAN. Instead, a SAN moves the storage resources from the network to its high-powered network. A SAN provides access to block-level data storage.
Examples of SAN are a network of disks accessed by a network of servers.
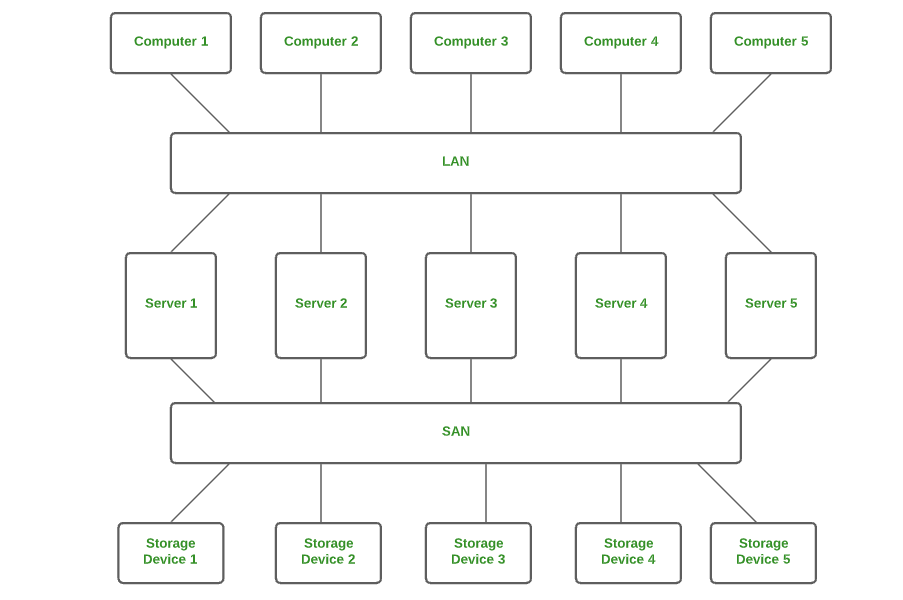
3. System Area Network (SAN)
A SAN is a type of computer network that connects a cluster of high-performance computers. It is a connection-oriented and high-bandwidth network. A SAN is a type of LAN that handles high amounts of information in large requests. This network is useful for processing applications that require high network performance.
Microsoft SQL Server 2005 uses SAN through a virtual interface adapter.

System Area Network (SAN)
4. Passive Optical Local Area Network (POLAN)
A POLAN is a type of computer network that is an alternative to a LAN. POLAN uses optical splitters to split an optical signal from a single strand of single-mode optical fiber to multiple signals to distribute users and devices. In short, POLAN is a point to multipoint LAN architecture.

5. Enterprise Private Network (EPN)
EPN is a type of computer network mostly used by businesses that want a secure connection over various locations to share computer resources.

6. Virtual Private Network (VPN)
A VPN is a type of computer network that extends a private network across the internet and lets the user send and receive data as if they were connected to a private network even though they are not. Through a virtual point-to-point connection users can access a private network remotely. VPN protects you from malicious sources by operating as a medium that gives you a protected network connection.

7. Home Area Network (HAN)
Many of the houses might have more than a computer. To interconnect those computers and with other peripheral devices, a network should be established similar to the local area network (LAN) within that home. Such a type of network that allows a user to interconnect multiple computers and other digital devices within the home is referred to as Home Area Network (HAN). HAN encourages sharing of resources, files, and programs within the network. It supports both wired and wireless communication.

Advantages of Computer Network
Some of the main advantages of Computer Networks are:
- Central Storage of Data: Files are stored on a central storage database which helps to easily access and available to everyone.
- Connectivity: A single connection can be routed to connect multiple computing devices.
- Sharing of Files: Files and data can be easily shared among multiple devices which helps in easily communicating among the organization.
- Security through Authorization: Computer Networking provides additional security and protection of information in the system.
Disadvantages of Computer Network
Some of the main disadvantages of Computer Networks are:
- Virus and Malware: A virus is a program that can infect other programs by modifying them. Viruses and Malware can corrupt the whole network.
- High Cost of Setup: The initial setup of Computer Networking is expensive because it consists of a lot of wires and cables along with the device.
- loss of Information: In case of a System Failure, might lead to some loss of data.
- Management of Network: Management of a Network is somehow complex for a person, it requires training for its proper use.
Please Login to comment...
Similar reads, improve your coding skills with practice.
What kind of Experience do you want to share?

IMAGES
VIDEO
COMMENTS
All assignments are on the web page Text: Kurose & Ross, Computer Networking: A Top-Down Approach, 4th or 5th edition-Instructors working from 4th edition, either OK-Don't need lab manual or Ethereal (used book OK) Syllabus on web page-Gives which textbook chapters correspond to lectures (Lectures and book topics will mostly overlap)
A computer network is a collection of two or more computer systems that are linked together. A network connection can be established using either cable or wireless media. Hardware and software are used to connect computers and tools in any network. A computer network consists of various kinds of nodes.
Module 1 • 5 hours to complete. Welcome to the Networking course of the IT Support Professional Certificate! In the first module of this course, we will cover the basics of computer networking. We will learn about the TCP/IP and OSI networking models and how the network layers work together. We'll also cover the basics of networking devices ...
Most of the assignments will involve some programming (in Java), but none of the programs is very long. Most of the assignments will be done in the context of the Open Network Lab a network testbed that allows you to define your own private network configuration and run applications within it. You will be working with multiple computers at the ...
A computer network is a collection of computers or devices connected to share resources. Any device which can share or receive the data is called a Node. Through which the information or data propagate is known as channels, It can be guided or unguided. In this Computer network tutorial, you'll learn basic to advanced concepts like the Basics ...
An Introduction to Computer Networksis a free and open general-purpose computer-networking textbook, complete with diagrams and exercises.It covers the LAN, internetworking and transport layers, focusing primarily on TCP/IP. Particular attention is paid to congestion; other special topics include queuing, real-time traffic, network management, security and the ns simulator.
A computer network is a set of computers sharing resources located on or provided by network nodes.Computers use common communication protocols over digital interconnections to communicate with each other. These interconnections are made up of telecommunication network technologies based on physically wired, optical, and wireless radio-frequency methods that may be arranged in a variety of ...
MAC and IP addresses uniquely define devices and network connections, respectively, in a network. A MAC address is a number assigned to a network interface card (NIC) by a device's manufacturer. An IP address is a number assigned to a network connection. How is computer networking evolving? Modern-day networks deliver more than connectivity.
Introduction. In this lab assignment, you will write a simple router with a static routing table. We will pass to your code raw Ethernet frames and give you a function that can send a raw Ethernet frame. It is up to you to implement the forwarding logic between getting a frame and sending it out over another interface. Figure 1: sample topology.
The course will cover the core elements of modern Internet technology and protocols, including the application, transport, network, link layers and physical layers, for both wired and wireless networks. Coverage roughly corresponds to Chapters 1-8 of the textbook and additional instructor-provided resources. Computer networks and the Internet.
Protocol Layering and Layering Models. Protocol Layering d Needed because communication is complex d Intended primarily for protocol designers
Open system: A system that is connected to the network and is ready for communication. Closed system: A system that is not connected to the network and can't be communicated with. Types of Computer Network Architecture. Computer Network falls under these broad Categories: Client-Server Architecture: Client-Server Architecture is a type of Computer Network Architecture in which Nodes can be ...
computer network, two or more computers that are connected with one another for the purpose of communicating data electronically. Besides physically connecting computer and communication devices, a network system serves the important function of establishing a cohesive architecture that allows a variety of equipment types to transfer information in a near-seamless fashion.
What is networking? A computer network comprises two or more computers that are connected—either by cables (wired) or wifi (wireless)—with the purpose of transmitting, exchanging, or sharing data and resources. You build a computer network by using hardware (for example, routers, switches, access points, and cables) and software (for ...
Computer networks can be defined as the exchange of network packets between computing machines across the world with the help of data lines like wire cables, optical fibers, etc. ... (a non-profit corporation) that manages the assignment of domain names and IP address ranges on behalf of the community. A domain is divided into three parts as ...
assignment_turned_in Problem Sets with Solutions. Simulation of a computer network, in 10 iterations, with 2.0 ms steps. The red represents the new recalculated step, and the green is the trace from the previous step. ...
Computer Mobile Phone Tablet Headset Network Topologies A computer physical network topology is the actual layout or physical design and intercon-nection of a computer network. A topology includes the cabling and devices that are part of the network. In the following sections you will learn about several different types of network topologies: B u s
The broad objective of the course is to understand - (i) the architecture and principles of today's computer networks, (ii) the protocols and their functionalities, (iii) the requirements for the future Internet and its impact on the computer network architecture. ... Average assignment score = 25% of average of best 8 assignments out of the ...
Assignments. This section contains the problem set, useful files, FAQ and solution for each assignment.
COMPUTER NETWORK ASSIGNMENTS Assignments based on CS-333 (Computer Networks -I) and CS-343 (Computer Networks -II ) PREPARED BY: PROF. MS. POONAM PONDE (NOWROSJEE WADIA COLLEGE) PROF. JEEVAN LIMAYE (FERGUSSON COLLEGE) OBJECTIVES The objectives of these assignments are : a. To cover basic concepts of networking b.
Referencing and citation. W hen you reference you use the standardized style to acknowledge the source of information used in your assignment. It is important (morally & legally) to acknowledge someone else's ideas or words you have used. Academic writing encourages paraphrasing information you have researched and read. Paraphrasing means re ...
Establishing the local area network is the first thing that must be done (LAN). Setting up the local area network initially and then adding support for the wide area network later on would be a far more effective use of time and resources. I began by configuring the router and giving it the IP address 192.168.1.
2. Local Area Network (LAN) LAN is the most frequently used network. A LAN is a computer network that connects computers through a common communication path, contained within a limited area, that is, locally. A LAN encompasses two or more computers connected over a server. The two important technologies involved in this network are Ethernet and Wi-fi.
Computer-science document from University of the People, 5 pages, University of the People CS 2204 - Communication and Networking Written Assignment Unit 3 What do you understand by The Hidden Node Problem? Describe 2 different spatial configurations which exemplify this issue Dordal (2009) emphasized a distinctive cha
Join us at 6 PM (WAT) this Thursday May 9, 2024, as our distinguish guest will be discussing the topic: GEN-Z ACCOUNTANTS: Redefining Traditional...
Unit: Computer Networks Assignment title: WeBuyAnyVehicle Spring 2024 - Winter 2024 Important notes • Please refer to the Assignment Presentation Requirements for advice on how to set out your assignment. These can be found on the NCC Education website. Hover over 'About Us' on the main menu and then navigate to 'Policies and Procedures' then scroll to the 'Student Support' area.