21+ SAMPLE Cyber Security Proposal in PDF
Cyber security proposal, 21+ sample cyber security proposal, a cyber security, benefits of cyber security proposal, how to develop a cyber security plan, what constitutes an effective cybersecurity strategy, is cyber security a source of stress, what is the definition of personal security.


Cyber Security Guard Proposal

PhD Cyber Security Area Project Proposal

Cyber Security PhD Research Recommendation Proposal

Joint Cyber Security Business Plan Proposal

Cyber Security Security Awareness Proposal

Cyber Security Business Proposal Letter

Cyber Security Data Center Modernization Proposal
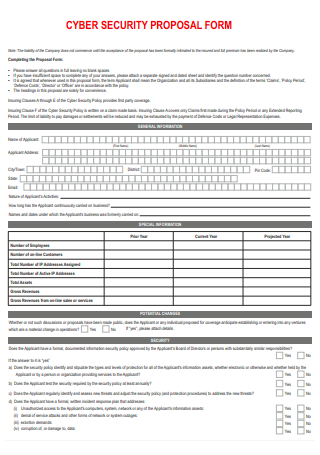
Cyber Security Proposal Form

Bachelor of Science Degree in Cyber Security Proposal
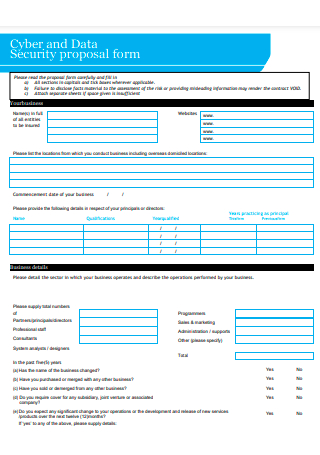
Cyber and Data Security Proposal Form

Cyber Risk and Security Proposal

Cyber Security Proposal in PDF

Cyber Security Products and Services Proposal

Cyber Security Insurance Proposal Form
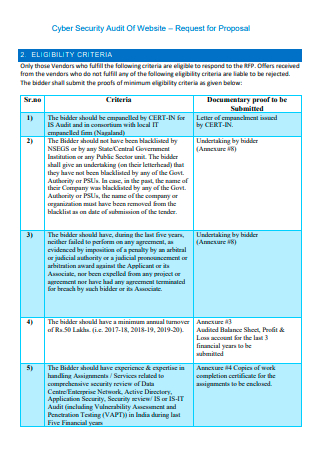
Cyber Security Audit of Website Proposal

Cyber Security Services Proposal
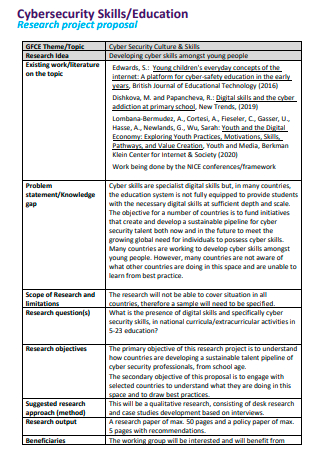
Cyber Security Skills Research Project Proposal

Cyber Security Proposal Example

Cyber Security Act Proposal

Cyber Security Legislative Proposal

Standard Cyber Security Proposal
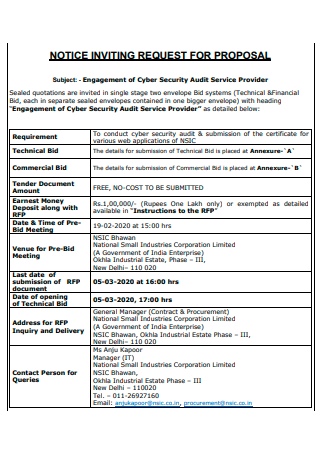
Cyber Security Audit Service Provider Proposal
What is a cyber security, share this post on your network, file formats, word templates, google docs templates, excel templates, powerpoint templates, google sheets templates, google slides templates, pdf templates, publisher templates, psd templates, indesign templates, illustrator templates, pages templates, keynote templates, numbers templates, outlook templates, you may also like these articles, 25+ sample construction company proposal in ms word.
Navigating the intricate world of construction demands a seasoned company with a proven track record. Our comprehensive guide on the Construction Company Proposal is your blueprint to understanding the…
8+ SAMPLE Drama Proposal in PDF

Julia Child said: “Drama is very important in life: You have to come on with a bang. You never want to go out with a whimper. Everything can have…
browse by categories
- Questionnaire
- Description
- Reconciliation
- Certificate
- Spreadsheet
Information
- privacy policy
- Terms & Conditions
- How it works

Undergraduate Cyber Security Proposal Sample
Here is a sample that showcases why we are one of the world’s leading academic writing firms. This assignment was created by one of our expert academic writers and demonstrated the highest academic quality. Place your order today to achieve academic greatness.
View a different grade
Introduction
Network intrusion detection systems (NIDS) have been quickly developed in industry and academics in response to the escalating cyber-attacks on states and business organisations worldwide. Insider threats, breach-of-system assaults, and web-based attacks are the most damaging types of cybercrime (Haq et al., 2015). And to protect computer systems from unauthorised access, businesses use a firewall, antivirus software, and an intrusion detection system (NIDS) (Liao et al., 2013).
The anomaly detection speed, precision, and reliability are essential success elements for NIDS. Machine learning (ML) approaches are used to develop NIDS to increase recognition performance and minimise false alarms (Halimaa & Sundarakantham, 2019). Deep learning (DL) methodologies have been used in NIDS as an enhanced version of ML (Alrowaily et al., 2019). Therefore, this research compares various crossovers of modern-day technologies, such as ML and DL, with NIDS to show how it can tackle cyber-attacks.
This research compares computational models such as ML and DL, making NIDS more efficient against cyber-attacks.
It has the following objectives:
- Evaluate existing literature in this area to draw insights into the research problem.
- To compare modern-day computational models such as ML and DL to optimise NIDS.
- To identify problems in the existing NIDS to make it more efficient.
- To recommend a suitable model to improve NIDS efficacy.
Product Overview
It will identify shortcomings in the conventional NIDS. Moreover, it will find modern-day approaches (ML, DL, etc.) to make NIDE more efficient in countering cyber-attacks. It will see how the incorporation of modern computational models can improve NIDS.
This research targets academics, large corporations, governments, and network security and ML practitioners.
Background Review
Existing approaches.
Currently, the following NIDS are used by large organisations:
- Signature-based intrusion detection systems detect probable threats by skimming network traffic for specified patterns, such as byte sequences or known harmful instruction sequences used by malware. The word “signature” comes from an antivirus program that alludes to these recognised patterns. Although signature-based intrusion detection systems may quickly detect known assaults, they cannot detect novel attempts that no way exists (Kumar & Sangwan, 2012).
- Anomaly-based intrusion detection systems are a relatively new development that perceives and adapts to unidentified threats, mainly due to the explosion of malware. This detection approach uses MLalgorithms to establish a specified prototype of reliable activity, which is then used to compare new behaviour. While this method allows for identifying previously undiscovered assaults, it is vulnerable to false positives, which occur when previously unknown permitted behaviour is erroneously categorised as harmful (Aldweesh et al., 2020).
Related Literature
According to Sultana et al. (2019), because of the advent of customisable capabilities, Software Defined Networking Technology (SDN) provides a chance to better perceive and monitor network sanctuary issues. SDN-based NIDS recently incorporated ML methods to secure computer networks and resolve network security concerns. In the context of SDN, a stream of sophisticated ML methodologies DL– is beginning to emerge. They examined current studies on ML approaches that utilise SDN to achieve NIDS in this survey. They primarily studied DL approaches in the development of SDN-based NIDS. In the interim, in this survey, they explored technologies used to construct NIDS models in an SDN context. This survey concludes with a debate on current issues in executing NIDS using ML/DL and forthcoming work.
Similarly, according to Jiang et al. (2020), Intrusion Detection Systems (IDS) plays a vital role in network security by detecting and stopping hostile activity. The network intrusion observations are drowned in many everyday observations due to the dynamic and time-varying network environment, resulting in inadequate data for model development and detecting results with a high false detection rate. They offer a network intrusion detection technique that combines blended sampling with a deep network model in response to the data imbalance. They use one-side selection to minimise noisy samples in the overwhelming group and then boost subsets of features using the Synthetic Minority Oversampling Technique. This method may create a balanced dataset, allowing the model to thoroughly understand the properties of minority samples while drastically reducing model training time. Second, they create a deep hierarchical network model using a convolutional neural network. Simulations on the NSL-KDD and UNSW-NB15 datasets tested the proposed network intrusion detection system, with classification results of 84.59per cent and 76.76 per cent, respectively.
Lastly, according to Ahmad et al. (2021), a thorough assessment of current NIDS-based publications discusses the merits and drawbacks of the proposed solutions. A discussion of recent trends and developments in ML and DL-based NIDS follows the suggested technique, review criteria, and dataset allocation. They emphasised numerous research obstacles and recommended future research scope in developing ML and DL-based NIDS by using the weaknesses of the presented approaches. According to the study, 61% of the recommended methods were evaluated using the KDD Cup’99 and NSL-KDD datasets, owing to the availability of comprehensive findings utilising these datasets. However, these datasets are too old to address recent network assaults, limiting the performance of the offered approaches in real-time scenarios. For AI-based NIDS approaches, the model should be evaluated using the most recent updated dataset, such as CSE-CIC-IDS2018, for improved detection accuracy for intrusions.
Hire an Expert Dissertation Proposal Writer
Orders completed by our expert writers are
- Formally drafted in the academic style
- 100% Plagiarism-free & 100% Confidential
- Never resold
- Include unlimited free revisions
- Completed to match exact client requirements
Methodology
It will be quantitative research based on the secondary data collected through the systematic literature review. Various NIDS approaches based on the literature will be tested through different ML and DL models, such as CNN. Ahmad et al. (2021)’s study will be used as a base to conduct the review.
The latest hardware with a sound graphics card, such as Nvidia GeForce RTX 3080, will be used to run ML and DL models to test balanced and unbalanced data sets such as KDD Cup’99 and NSL-KDD present for NIDS.
Version Management Plan
It will use git version control as a repository to help all connected users track the progress of the project. All affiliated users can check the source code and test and debug it.
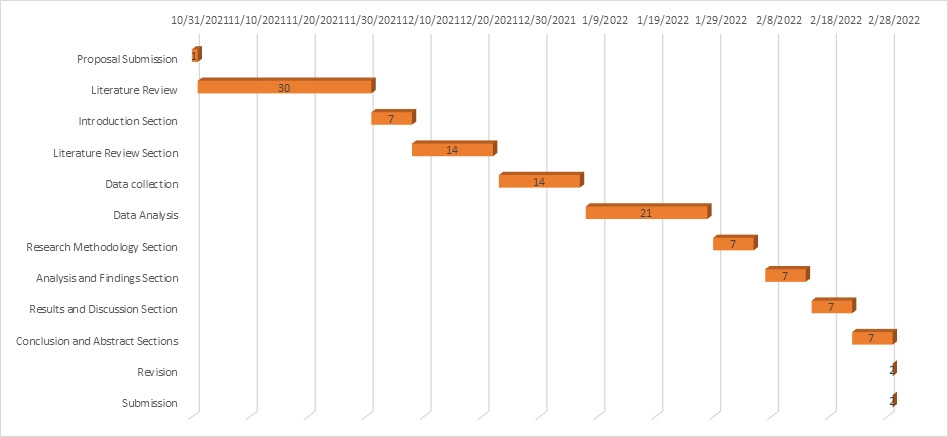
Project Management
The activities of the project are presented in the following Gantt chart:
Bibliography
Ahmad, Z. et al., 2021. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Transactions on Emerging Telecommunications Technologies, 32(1), p. e4150.
Aldweesh, A., Derhab, A. & Emam, A., 2020. Deep learning approaches for anomaly-based intrusion detection systems: A survey, taxonomy, and open issues. Knowledge-Based Systems, Volume 189, p. 105124.
Alrowaily, M., Alenezi, F. & Lu, Z., 2019. Effectiveness of machine learning-based intrusion detection systems. In. International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, July.pp. 277-288.
Halimaa, A. & Sundarakantham, K., 2019. Machine learning based intrusion detection system. In. 2019 3rd International conference on trends in electronics and informatics (ICOEI), April.pp. 916-920.
Haq, N. et al., 2015. Application of machine learning approaches in intrusion detection system: a survey. IJARAI-International Journal of Advanced Research in Artificial Intelligence, 4(3), pp. 9-18.
Jiang, K., Wang, W., Wang, A. & Wu, H., 2020. Network intrusion detection combined hybrid sampling with deep hierarchical network. IEEE Access, Volume 8, pp. 32464-32476.
Kumar, V. & Sangwan, O., 2012. Signature based intrusion detection system using SNORT. International Journal of Computer Applications & Information Technology, 1(3), pp. 35-41.
Liao, H., Lin, C., Lin, Y. & Tung, K., 2013. Intrusion detection system: A comprehensive review. Journal of Network and Computer Applications, 36(1), pp. 16-24.
Sultana, N., Chilamkurti, N., Peng, W. & Alhadad, R., 2019. Survey on SDN based network intrusion detection system using machine learning approaches. Peer-to-Peer Networking and Applications, 12(2), pp. 493-501.
Frequently Asked Questions
How to write an undergraduate dissertation proposal.
To write an undergraduate dissertation proposal:
- Choose a research topic.
- Outline objectives and research questions.
- Describe methodology and data sources.
- Provide a brief literature review.
- State significance and potential outcomes.
- Include a timeline and list of references.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
Research Topics & Ideas: Cybersecurity
50 Topic Ideas To Kickstart Your Research

If you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
Research Proposal on Cyber Security
Defining Cyber Security?
Cybersecurity is made up of several security technologies and predefined policies to guarantee the safety measures for network, hardware, and software . These measures prevent data attacks and threats from unauthenticated users. And, it assures to provide data integrity, privacy, accessibility, and trust .
This article presents you with current topics of Research Proposal on Cyber Security with their key areas!!!
In an organization, two prime security types are embedded to protect their sensitive information. They are physical and cybersecurity . These two technologies create security creates a shield over the organization’s data to prevent illegal users . In this, cybersecurity deals with intelligent online cyber-attacks.

In fact, information/network security is recognized as part of cybersecurity. Overall, it is the best protective technology to detect and prevent cyber-attacks . Furthermore, it is also popularly known for security risk control. Now, we can see about the few major issues that are prolonged for the long-term to meet the best solving solutions.
What are some problems with cyber security?
- Unauthenticated database / port scan
- Installing malware through web penetration for data alteration
- Compromise the system from remote location
- Illegal access over the network records and perform forging operation
- Flooding attack to create numerous requests over a server
- Intentionally troublemaking a server rooms to get the resource freely
- Ransomware attacks on sensitive data to stop the access
- Denial of Service / Distributed DoS attack to create more traffic to block the access
- Man-in-the-middle / eavesdrop attack on data conversation
- Mount the malware / spyware on a network
- Breach the encrypted data
Important 3 Terms of Cyber Security
Now, we can see the significant terminologies used in cybersecurity. While performing any operations in cyber-attacks, these three terms need to focus more. Though these terms may look similar, it has different nature and computing processes. The three terms as follows,
- It is an ability of creating harm to the system while threat uses the vulnerability
- For more clarity, it is formulated as threat x vulnerability which is the launch point to the cybersecurity
- It is an activity to create harmful things to either individual or whole organization / company
- It is classified as intentional, unintentional and natural threats
- It includes several threat evaluation techniques for better interpretation
- From the background context of the cyber system, it is addressed as the applications errors or hardware defectiveness
- Now, it is popularly known as the susceptibility / defenselessness nature of the system
- Further, it may affect the CIA (Confidentiality, Integrity and Authentication) triad
As a matter of fact, our research team is comprised of a colossal collection of distinct research areas for Research Proposal on Cyber Security. We are ready to give you more unknown interesting facts on those areas. For your reference, here we have listed key enabling technologies in cybersecurity.
Key Technologies of Cyber Security
- Cloud Evidence Rescue System in Cyber Forensic
- Medical IoT in D2D Wireless Networks
- Vulnerability on Self-Organizing Social Networks
- Integrated Cyber Systems (cross-platform safety and firewalls)
- Autonomous Vehicles Cybersecurity
- Internet of Medical Things (IoMT)
- Potential Radicalization on Social Website Content
- Insider and Outsider Threat Detection
What are insider threats in cyber security?
Essentially, insider threat is one of the risks in cybersecurity caused by the node in the same network . For instance: data theft in the company is caused by the employee itself. The kind of threat can be originated from old/current employees or associated partners. Since these persons already have limited / whole rights to access company data but trying to perform illegal activities. Here, we have given you the process involved in detecting insider threats,
- Verify the integrity of the file to analyze whether the file is compromised or not. For instance: boot / system files
- Examine the content of the file to figure out the abnormal patterns hide inside the file. For instance: virus signatures
- Spot the files and directories to check they were place in placed in different locations
Insider Threat Indicators in Cyber Security
Based on certain indicators also, we can detect the insider threat. These indicators address the abnormal activities in the network. For instance, the employee has a grudge but pretends to normal; it may indicate the foul game. Here we have given three common indicators to track the inside threats:
- Traffic Size – Transmission of voluminous data in the network
- Events at Strange Timing – Identify the abnormal actions in the network (like mid-night timings)
- Nature of Events – Attempt to gain access to rare network resources / services
Next, we can see significant countermeasures to prevent insider threats . The below-specified countermeasures are just the sample for your information. Beyond this, our developers have come across numerous best solutions. Still, now, we are tirelessly working on up-to-date different security mechanisms to build research proposal on cyber security .
How to protect insider threats?
- Analyze the data at all the aspects (rest in servers, motion in network, storage in cloud and terminals)
- Screen the entire storage systems to auto-generate alerts on policy abuses. For instance: warehouses, data center, relational databases, and mainframes
- Inspect the user behavior through learning for identifying and warning security risks
- Complicate the private data by disguising / encoding so that even if the hackers trace the data, it will be not useful anymore
- Silently observes the legitimate user intent in accessing the data for detecting abnormal activities
- Rank the security events based on the their threat severity on using combined ML and AI technologies
- Disclose the data size, background, locality in the cloud
- Check and assess the known attacks / susceptibilities and while processing it prevent other threats and SQL injection
Furthermore, our research team has given you the latest cybersecurity research topics that we are currently ongoing. Based on the active scholars’ demand, we have recommended the following research Cybersecurity master project ideas .
Best Research Proposal Topics in Cyber Security
- Cyber Anti-forensic Technologies
- Biometrics based Cyber Physical System
- Security Information and Event Management (SIEM)
- Development of Automated Defense System
- Improvement Cyber Intelligence based Bio-inspired Models
- Analysis of Correlations in Objects Mobility
- Intruders Identification using Bio-inspired Algorithm
- Evaluation of Different Cyber-defense Models
- Design Bio-inspired Models for Network Security
- Behavioral Analysis for Bio-authentication
- Security Enrichment using ML and Blockchain Techniques
- Challenges in Network Forensics and Traffic Analysis
- Data Hiding and Logic-based Assets Theft (watermarking and steganography)
- Threat Detection and Classification
- Enhancement of Cybersecurity using Adaptation Approaches
- Cyber Threat Prediction using Multi Technologies (ANN, Genetic and Evolutionary)
As you know well, PhD is nothing but the original research contribution to the interesting research field. For instance: cybersecurity, WSN, Cloud computing , AI, and more. The most important factors that you have to hold till the end of the research are the contribution and originality of the contribution . Next, we can see the research proposal on Cyber Security in detail with its significance and major phases.
Outline of Research Proposal on Cyber Security
In general, research is the data-assisted scientific investigation of the specific problem , which is conducted in chronological order to critically solve the problem by perfect solution. Aresearch proposal is defined as the intelligent approach find particular unknown facts with acceptable evidence in a well-organized manner . In this, it includes a time-scheduled plan, objectives, and structured format to describe the handpicked research questions and their appropriate answer. Here, we have given you few primary key features of the best proposal
Major Parts of Research Proposal
- Mention the research need and importance with contribution
- Address the research hole by referring recent relevant papers
- Clearly denote the problem statement in two or three sentences
- Describe the effective measures against proposed problem through methodologies
Now, we can how our research writing service helps you to create quality excellence proposal writing . We have a special team of writers who are technically strong in converting the actual research plan into the systematized proposal. Below, we have specified what makes our best from others in all the aspects of the proposal writing.

How to write the best PhD proposal writing?
- Describe the problem in crystal clear way which is theoretical proven but practically not evidently proven
- Frame the objectives of research which need to experimentally accomplished
- If the objectives are clearly depicted to readers the it is easy for them to catch the flow of research
- Take a stand on problem and rise all applicable research questions to accomplish the objectives
- Perform statistics-based verification on premises
- Describe the research state to conduct further study
- Provide background information through relevant research papers
- Point out the other papers’ contribution, advantages and drawbacks
- Contribute detailed survey over recent methods
- Core part of the proposal
- Must to give sufficient information on proposed techniques / algorithms
- Ensure the flow of methodologies being used
- Evidently tackle the problem through best-fitting solutions
To sum up, if you need the best Research Proposal on Cyber Security , then contact our team. Certainly, we are pleased to lend our hands to give you the fullest support in the whole research journey. Our ultimate goal is to meet your research expectation in all aspects.
Why Work With Us ?
Senior research member, research experience, journal member, book publisher, research ethics, business ethics, valid references, explanations, paper publication, 9 big reasons to select us.
Our Editor-in-Chief has Website Ownership who control and deliver all aspects of PhD Direction to scholars and students and also keep the look to fully manage all our clients.
Our world-class certified experts have 18+years of experience in Research & Development programs (Industrial Research) who absolutely immersed as many scholars as possible in developing strong PhD research projects.
We associated with 200+reputed SCI and SCOPUS indexed journals (SJR ranking) for getting research work to be published in standard journals (Your first-choice journal).
PhDdirection.com is world’s largest book publishing platform that predominantly work subject-wise categories for scholars/students to assist their books writing and takes out into the University Library.
Our researchers provide required research ethics such as Confidentiality & Privacy, Novelty (valuable research), Plagiarism-Free, and Timely Delivery. Our customers have freedom to examine their current specific research activities.
Our organization take into consideration of customer satisfaction, online, offline support and professional works deliver since these are the actual inspiring business factors.
Solid works delivering by young qualified global research team. "References" is the key to evaluating works easier because we carefully assess scholars findings.
Detailed Videos, Readme files, Screenshots are provided for all research projects. We provide Teamviewer support and other online channels for project explanation.
Worthy journal publication is our main thing like IEEE, ACM, Springer, IET, Elsevier, etc. We substantially reduces scholars burden in publication side. We carry scholars from initial submission to final acceptance.
Related Pages
Our benefits, throughout reference, confidential agreement, research no way resale, plagiarism-free, publication guarantee, customize support, fair revisions, business professionalism, domains & tools, we generally use, wireless communication (4g lte, and 5g), ad hoc networks (vanet, manet, etc.), wireless sensor networks, software defined networks, network security, internet of things (mqtt, coap), internet of vehicles, cloud computing, fog computing, edge computing, mobile computing, mobile cloud computing, ubiquitous computing, digital image processing, medical image processing, pattern analysis and machine intelligence, geoscience and remote sensing, big data analytics, data mining, power electronics, web of things, digital forensics, natural language processing, automation systems, artificial intelligence, mininet 2.1.0, matlab (r2018b/r2019a), matlab and simulink, apache hadoop, apache spark mlib, apache mahout, apache flink, apache storm, apache cassandra, pig and hive, rapid miner, support 24/7, call us @ any time, +91 9444829042, [email protected].
Questions ?
Click here to chat with us

Researched by Consultants from Top-Tier Management Companies

Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories
How To Draft Best-in-Class Cyber Security Proposals (With Templates)

Naveen Kumar
Incidents of data breaches and cybercrime have seen a spurt during and post-pandemic periods. As organizations pushed their wares to the digital realm, cyber predators found it an opportunity to target these newcomers. This led to small and medium-sized enterprises (SMEs) losing $3.9 million to cybercrime in 2020-21. To control this humungous loss, cyber security systems emerged as the new buzzword, with investment pouring into this area as a business opportunity to capitalize on. As a result, the world information security market touched $170.4 billion by the end of 2022, and it is a thriving and competitive business today.
Winning clients in this cut-throat industry are not easy. With organizations like CyberArk, McAfee, Fortnite and Zscaler enforcing and monitoring standards related to cyber security, winning a client for a firm can be a challenge. However, SlideTeam’s Cyber Security PPT Presentation Templates can help you make a mark and win clients.
Pre-Designed Cyber Security Proposal Templates
The problems which SMEs face in nailing clients are with the skillset, technology, and approach. While the first two depend on the organization and its employees, we can help you with the third. You must approach a potential client with a well-developed cyber security proposal that helps them understand the value of data protection and how exactly your firm will help.
These editable and 100% customizable cyber security proposal templates will make the process of drafting your pitch effortless and less time-consuming. Let’s understand the structure of a cyber security proposal with the help of these sample templates.
Cyber Security For Organization Proposal PowerPoint Presentation
This PowerPoint image is the cover slide of the presentation deck. You can change the pictures, color, text, style, and layout of this slide to match your presentation. Use this sample design to introduce your audience to the meeting agenda. Click here to download the complete cyber security proposal presentation.

Download the presentation deck
1. Cover Letter Template For Cyber Security Proposal
Cover letters are like golden covers wrapped around the (metaphorical) meat of the proposal. They add value to the proposition and are the first thing a client looks at. It must be drafted in an intelligent manner to highlight critical points of your cyber security proposal and offerings. This sample PPT design will help you prepare a cover letter that compels the reader to go on. Get it now!

Download the Cover Letter Template
2. Project Context And Objectives For Cyber Security Proposal
The best way to hook your audience in a proposal presentation is to start on your main value proposition within the first three minutes. Describing your project context and objectives will help the prospect evaluate whether you have the solution they are looking for. Use this cyber security sample template to define the proposal context — problem & solution — and the objectives — skills, training, and security enhancements — your firms will achieve by entering into a deal with you.
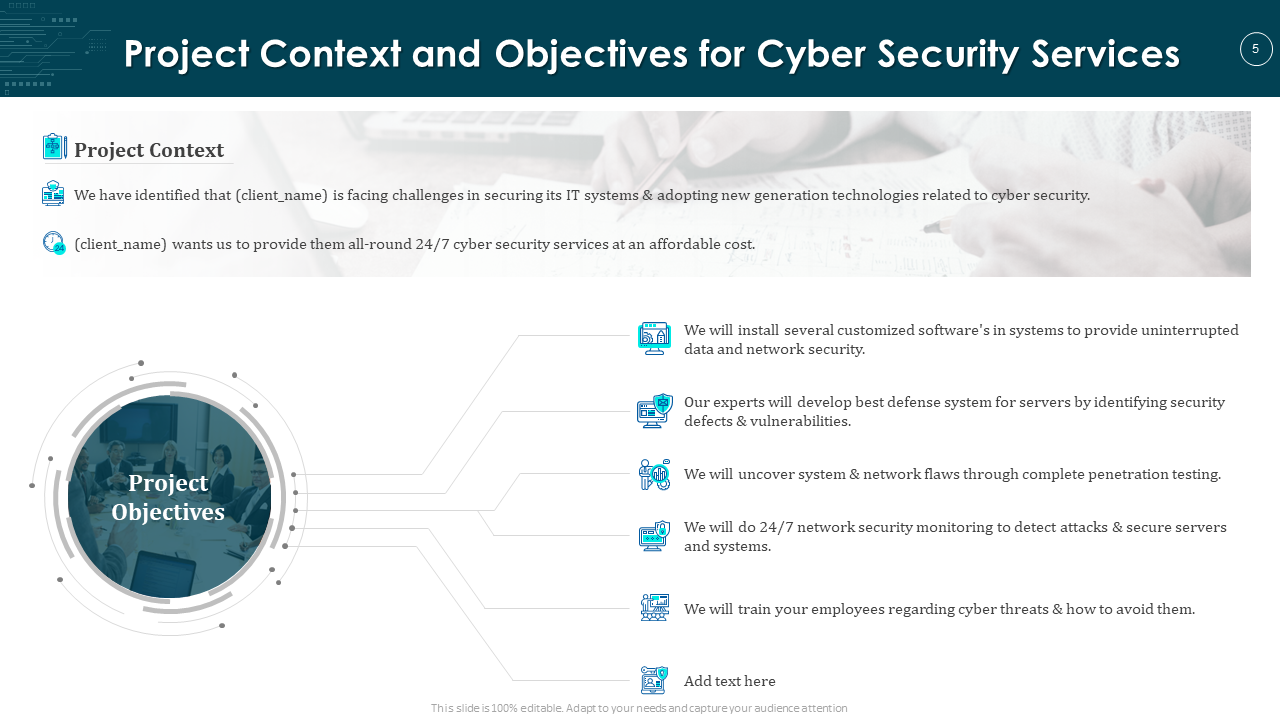
Download the Project Context And Objective Template
3. Process Flow of Cyber Security Presentation Template
The process flow will give the potential client a detailed outline of the cyber security plan. It helps you convey details of the big picture and ‘how’ of your cyber security plan within a deadline. This sample template will help you share week-wise information about the cyber security plan. Use it to mention key activities from project kick-off to planning, development & implementation to maintaining & training employees for security protocols. Grab this design today!
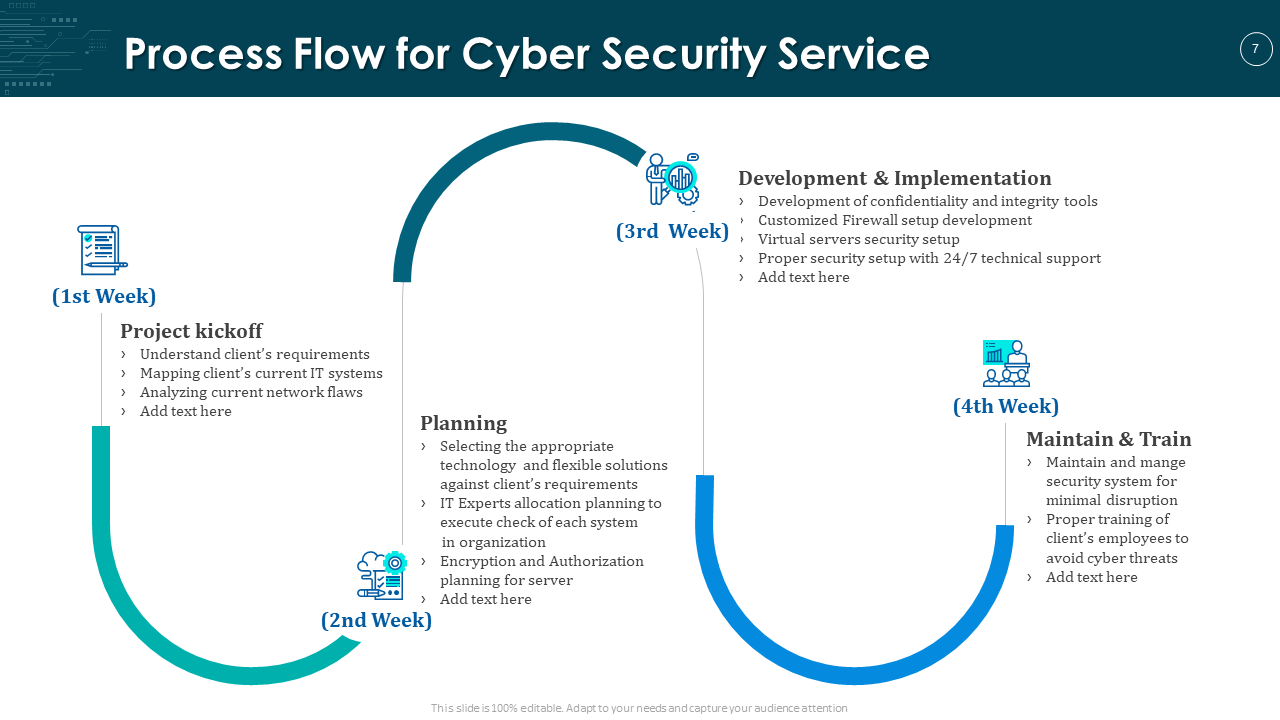
Download the Process Flow Template
Streamlining operations and business processes are essential to enhance productivity & discipline in employees and boost organizational growth exponentially. Use these process mapping templates to optimize business processes.
4. Cyber Security Plan Timeline Presentation Template
Defining a timeline for cyber security plan implementation is necessary to help investors understand how soon they will be immune to cyber-attacks. It will prepare the client’s organization and ease going through the gradual and necessary periodic changes for all stakeholders. This sample timeline design for the cyber security proposal will help you share the timeframe in the number of days for each phase. Download it now!
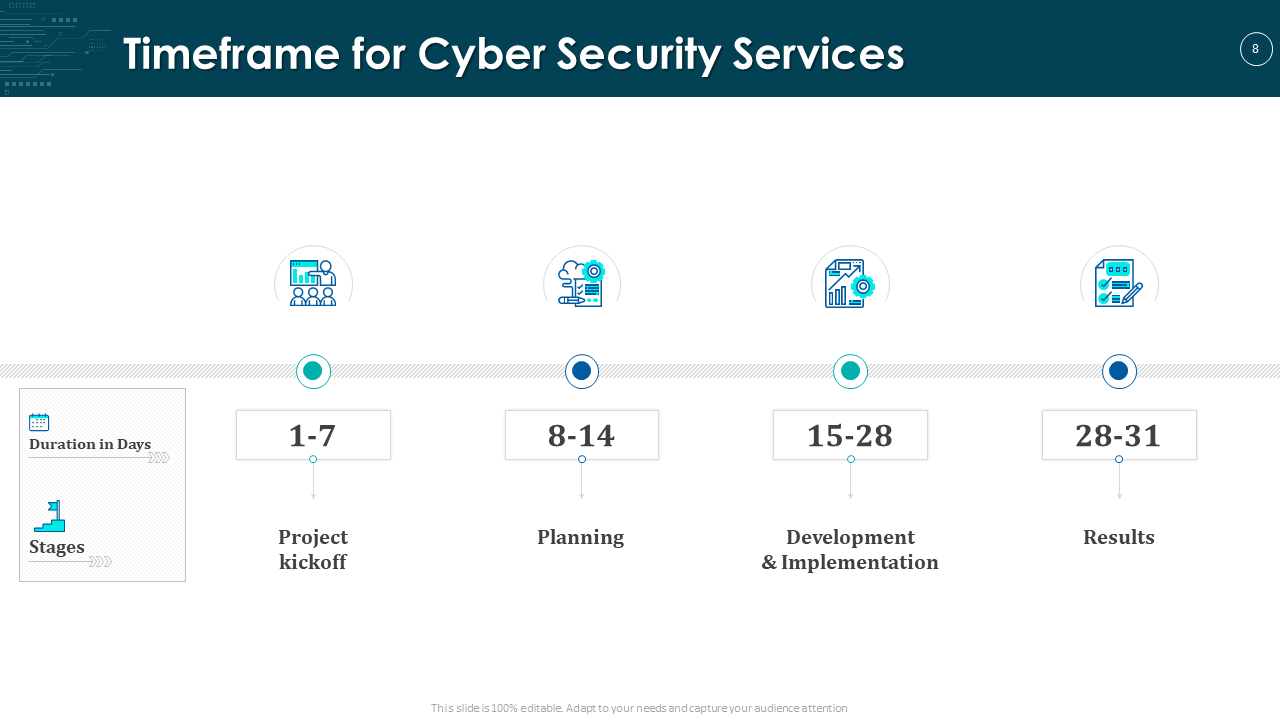
Download the Cyber Security Timeline Template
5. Investment and Duration Template For Cyber Security Proposal
After understanding your solution, implementation process, and duration for cyber security, clients will now be interested in how much it will cost them. Service costing is the game-changer in proposal presentation. If defined right, it will serve as a competitive advantage in your cyber security proposal and help you bag a client. This PPT Template enables you to provide each phase’s investment requirements in a comprehensive manner. Get it now!
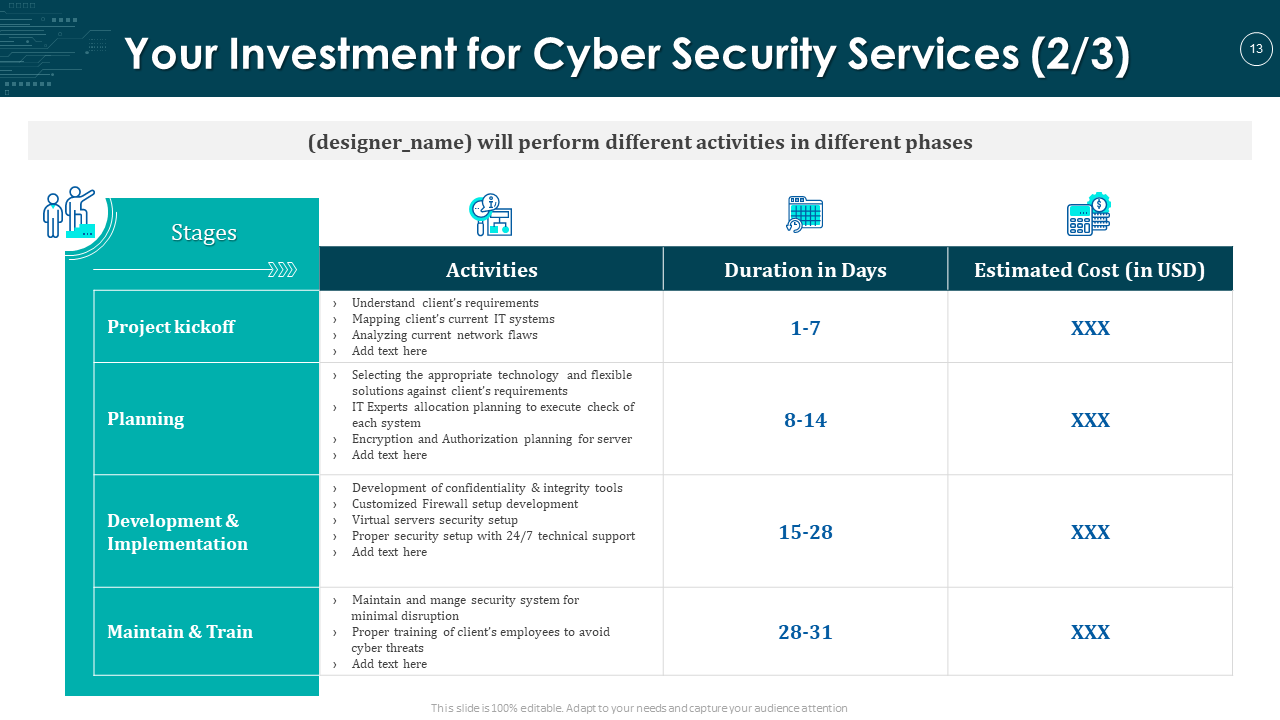
Download the Investment and Duration Template
6. Additional Services In Cyber Security Proposal Presentation Template
Services you offer, in addition to the main piece of cyber security, can be your USP if offered well. This will be your winning stroke if competitors are not offering these services and clients need them. These services can vary from cloud storage and assistance in software development, depending on what you have in your arsenal. This presentation template will help you win clients as it offers additional services. Download this cyber security presentation proposal template now!
Tip: You can also add a separate template in the investment section to show the original value of these additional services to the client.
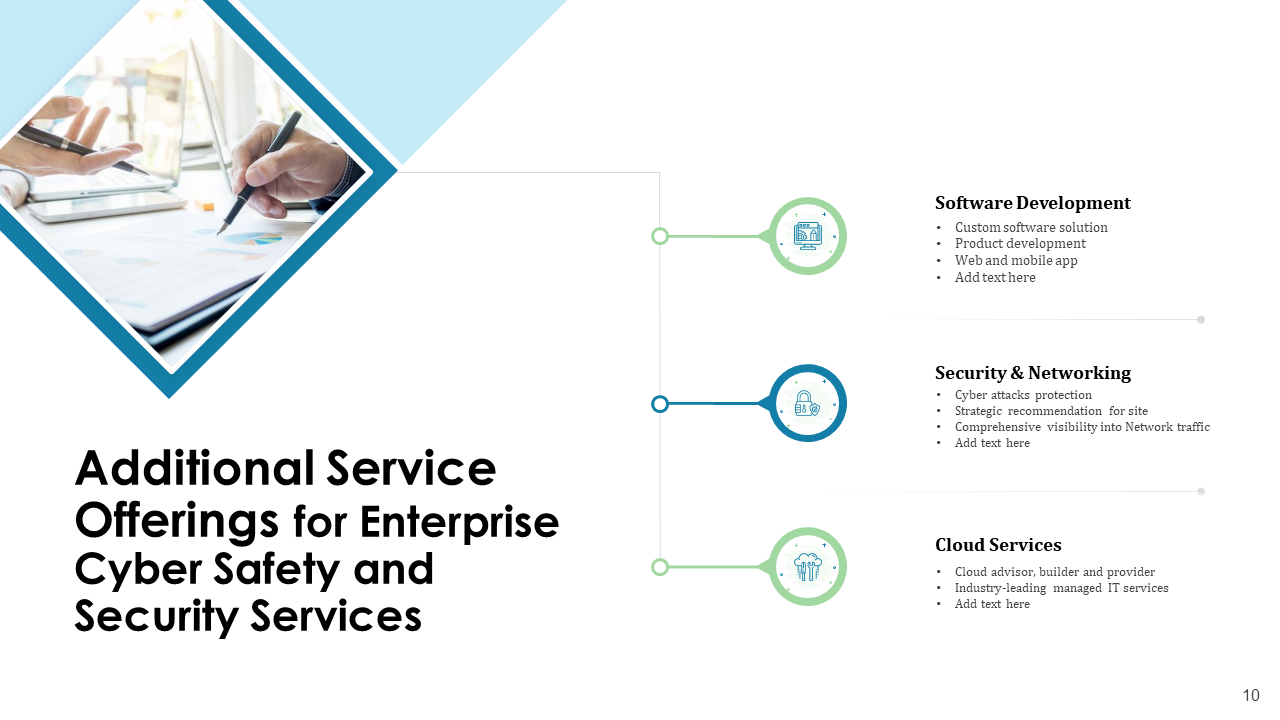
Download the Additional Service Offerings Template
Cloud computing is part of the basic build and storage of every digital platform and business, whether it’s social media like WhatsApp, Instagram, or Twitter or e-commerce platforms like Amazon, eBay, and Walmart. What’s next? The next big thing in line to revolutionize the digital world is Machine Learning (ML). Use these machine learning templates to devise and present your mindful strategy about this game-changing technology.
7. Why Us For Cyber Security of Organization Presentation Template
Showcase your strengths and competitive advantage to the clients to win their trust. Use this PPT Template to highlight your organization’s experience, company overview, and things that make you a worthy partner to meet client’s security requirements. Adding details like 24/7 service availability, team composition, and statistics will ensure the client will not see anyone beyond you. This sample PowerPoint Graphic will help you highlight your cyber security firm’s strengths in an eye-catching manner and win clients. Combined with templates like about us, rewards and recognition, and our expertise, it will give a perfect company overview. Download now!

Download the Why Us Template
8. Case Study And Client Testimonials For Cyber Security Proposal
Case studies and client testimonials prove your expertise and the value-added services your cyber security organization provides to its clients. These will also serve as background checks. Suppose you worked with industry giants or even with startups having a good reputation in the market. In that case, it is highly recommended that you add their case studies and testimonials as the ‘push factor in your favor. Download now!

Download the Case Study And Client Testimonials Template
9. Statement of Work & Contract Template For Cyber Security Proposal
A statement of work (SOW) describes project requirements, including the scope of work, deliverables, timelines, work location, and payment terms and conditions. It will allow discussion of the project in brief and keep both parties on the same page. This sample template will help you outline an SOW & contract for your cyber security proposition and discuss project variables with clients. You can key in service rendered, mutual cooperation, terms of payments, cancellation policy, confidentiality agreement, and termination policy. Get it now!

Download the Statement of Work & Contract Template
10. Next Steps Template For Cyber Security Proposal
You proposed your cyber security strategy, and the client agreed to it. What’s next? Even if you know what to do next, maybe clients don’t. Don’t let the boat sink in shallow water after taking it out from storms. Guide the clients towards the following steps, like reading and signing the contract and sealing the deal using this template. This PPT Template will help you illustrate and pilot the audience toward forming a strong strategic partnership. Download it now!

Download the Next Steps Template
Over To You
With the help of a cyber security proposal, you can show clients how much you care about solving their problems and how your IT protection firm is perfect to meet their needs. It is an ideal tool to win a client with an intelligent presentation of your services and expertise in the digital world.
We shared these plug-and-play cyber security proposal templates and decks to help you develop this client-grabbing tool with more precision. You can download these all-inclusive complete decks with a single click. Our presentation service team is also here to help you customize your cyber security proposal to meet your specific needs.
Hurry! Don’t miss your chance to impress a client and be a digital hero by protecting one more organization from cyber-attacks and crimes.
P.S. That’s not it! We have more to offer to up your technology game. Grab these high-quality cyber security templates to present your strategies, options, tips, analysis, and more.
FAQs on Cyber Security
1. how do you write a cyber security proposal.
You can draft a comprehensive cyber security proposal by following the steps below:
1. Understand security threats and vulnerabilities with security risk analysis.
2. Evaluate the existing security technologies and improve, if required.
3. Review cyber security protocols.
4. Set/re-design goals and objectives for organization security.
5. Select a security framework/technology/tools.
6. Start writing the proposal with the first step of drafting a cover letter.
7. Devise a roadmap for implementing the strategy.
8. Set a budget, and add requirements and service offerings for a complete cyber security plan.
9. Include your organization’s expertise, team skills, and previous experience.
10. Check your proposal thoroughly before presenting it to the clients.
2. What are the three objectives of cyber security?
Cyber security protects the organization’s and customers’ data from unauthorized access or hacks. Cyber security objectives can be achieved by taking care of these three: confidentiality, integrity, and availability. These are also known as the three-pillar approach to cybersecurity. Each of these is a separate topic of study for experts. It is, however, clear that if these objectives are not met, the cyber security effort remains incomplete.
3. What are the five types of cyber security?
Cyber security can be classified into five broad types based on the elements it protects:
1. Critical Infrastructure Protection (CIP).
2. Application security, also known as web application security or Web AppSec.
3. Network security is also called Endpoint Security.
4. Cloud Security or cloud computing security.
5. Internet of things (IoT) security.
4. What are the three elements of cyber security strategies?
The three main things that should be taken into consideration while developing a cyber security strategy are:
1. Governance: How an organization controls and directs its IT security. It includes a specific and clear action plan and entails who is authorized to make decisions. Best security practices, policies, and procedures also fall under governance.
2. Technology: This refers to an organization’s infrastructure to withstand cyber security threats after user interaction. This includes but is not limited to the organization’s network and logical & physical environment that protects data and its valuable assets. Technological elements include regular network penetration testing, access control analysis, and physical security assessments.
3. Operations: This includes the implementation of governance and technological elements to exercise security. It includes designing and running security programs such as vulnerability management and risk monitoring and ensuring they are suitable to address existing and new cyber threats.
When writing a cyber security management plan, taking care of these elements will help maximize the impact and reduce the threat damage.
Related posts:
- Top 11 Templates to Create a Concise One-Page Stock Pitch [Free PDF Attached]
- 10 Elements of A Successful Corporate Sponsorship Proposal (With Presentation Templates)
- Top 10 Floor Plan Templates To Share the Essence of Your Property
- Top 10 Templates To Control Revenue Expenditure; Earn More With Less
Liked this blog? Please recommend us

How to Draft a Proactive Security Management Plan (With Editable Templates)?

Top 11 Cloud Security Templates to Design an Impregnable Database

Top 10 PPT Templates on Data Security to Ace That Presentation

10 Best Templates to Explain Principles of Information Security


Top 10 Templates to Conduct Security Incident Management; Prevent, Avert Crisis

Why Does the Enterprise Security Management Concern You! 17 Best Layouts for Your Organization

Top 10 Data Security Management Templates to Safeguard Your Business (Free PDF Attached)

Top 20 Cybersecurity Templates to Raise Your Guard Against Online Attacks
![cyber security research proposal example [Updated 2023] Top 25 Cybersecurity PowerPoint Templates To Safeguard Technology](https://www.slideteam.net/wp/wp-content/uploads/2020/04/Banner-11-335x146.png)
[Updated 2023] Top 25 Cybersecurity PowerPoint Templates To Safeguard Technology
10 Cybersecurity Risks That Plague Companies Worldwide (and PPT Templates That Can Help Thwart Them)

Top 10 Templates To Build A Cybersecurity Training Module
![cyber security research proposal example Top 10 Templates to Fabricate a Powerful Cyber Security Roadmap [Free PDF Attached]](https://www.slideteam.net/wp/wp-content/uploads/2022/05/Cyber-Security-Roadmap-Templates_1-1013x441.png)
Top 10 Templates to Fabricate a Powerful Cyber Security Roadmap [Free PDF Attached]
This form is protected by reCAPTCHA - the Google Privacy Policy and Terms of Service apply.

Digital revolution powerpoint presentation slides

Sales funnel results presentation layouts
3d men joinning circular jigsaw puzzles ppt graphics icons

Business Strategic Planning Template For Organizations Powerpoint Presentation Slides

Future plan powerpoint template slide

Project Management Team Powerpoint Presentation Slides

Brand marketing powerpoint presentation slides

Launching a new service powerpoint presentation with slides go to market

Agenda powerpoint slide show

Four key metrics donut chart with percentage

Engineering and technology ppt inspiration example introduction continuous process improvement

Meet our team representing in circular format

Cyber Security Project Proposal Template
- Great for beginners
- Ready-to-use, fully customizable Subcategory
- Get started in seconds

In today's digital landscape, protecting your organization from cyber threats is more important than ever. But where do you start? ClickUp's Cyber Security Project Proposal Template is here to help you outline and present a comprehensive plan to safeguard your business from potential risks.
With this template, you can:
- Identify and assess vulnerabilities in your current systems
- Propose effective security measures and strategies to mitigate risks
- Create a roadmap for implementing security controls and protocols
- Estimate project timelines, budgets, and resource requirements
Don't leave your organization's security to chance. Use ClickUp's Cyber Security Project Proposal Template to ensure you have a solid plan in place to protect your valuable assets. Get started today and stay one step ahead of cyber threats!
Benefits of Cyber Security Project Proposal Template
When it comes to cybersecurity, having a solid project proposal is crucial. With the Cyber Security Project Proposal Template, you can:
- Clearly outline the scope, objectives, and deliverables of your cybersecurity project
- Identify potential risks and vulnerabilities, and propose effective solutions to mitigate them
- Provide a detailed timeline and budget for your project, ensuring efficient resource allocation
- Demonstrate your expertise and professionalism to stakeholders, increasing their confidence in your project
- Streamline the approval process by presenting a comprehensive and well-structured proposal
Main Elements of Cyber Security Project Proposal Template
ClickUp's Cyber Security Project Proposal template is designed to help you create and manage your cyber security projects with ease. Here are the main elements of this Whiteboard template:
- Custom Statuses: Keep track of the progress of your project proposal with two statuses - Open and Complete, allowing you to easily visualize the current status of each task.
- Custom Fields: Utilize custom fields to add important information to your project proposal, such as project budget, timeline, and key stakeholders, ensuring all necessary details are captured and easily accessible.
- Custom Views: Access two different views - Project Proposal and Getting Started Guide - to effectively plan and execute your cyber security projects. The Project Proposal view allows you to outline project goals, deliverables, and milestones, while the Getting Started Guide view provides a step-by-step guide to kickstart your project.
- Collaboration Tools: Collaborate seamlessly with your team using ClickUp's built-in collaboration features, including task comments, file attachments, and real-time editing, ensuring everyone is on the same page throughout the project lifecycle.
How to Use Project Proposal for Cyber Security
If you're working on a cyber security project proposal, follow these steps to effectively use the Cyber Security Project Proposal Template in ClickUp:
1. Define the project scope and objectives
Start by clearly defining the scope and objectives of your cyber security project. What specific goals do you want to achieve, and what areas of your organization's security do you want to address? This will help you set a clear direction for your proposal.
Use the Goals feature in ClickUp to outline the project scope and objectives in a structured and organized manner.
2. Identify potential risks and vulnerabilities
Conduct a thorough assessment of your organization's current cyber security landscape. Identify potential risks and vulnerabilities that need to be addressed in your project. This could include areas such as network security, data protection, access controls, and employee training.
Utilize the Table view in ClickUp to create a comprehensive list of risks and vulnerabilities, and assign tasks to team members responsible for addressing each one.
3. Develop a detailed project plan
Once you have identified the risks and vulnerabilities, it's time to develop a detailed project plan. Break the project down into specific tasks and milestones, and assign responsibilities to team members. Outline the timeline, budget, and resources required for each phase of the project.
Use the Gantt chart feature in ClickUp to create a visual representation of your project plan, allowing you to easily track progress and make adjustments as needed.
4. Outline the proposed solution
In your project proposal, clearly outline the proposed solution to address the identified risks and vulnerabilities. Explain how your project will enhance the organization's cyber security measures and protect sensitive data. Provide details on the technologies, tools, and methodologies that will be utilized.
Create a Doc in ClickUp to write a detailed description of the proposed solution, including any relevant diagrams or visuals.
5. Present the project proposal
Once your project proposal is complete, it's time to present it to the relevant stakeholders for approval. Prepare a compelling presentation that highlights the importance of the project, the potential risks it addresses, and the benefits it will bring to the organization. Be prepared to answer any questions or concerns raised during the presentation.
Use the Dashboards feature in ClickUp to create a visually appealing and informative presentation, incorporating key project details and metrics.
By following these steps and utilizing the Cyber Security Project Proposal Template in ClickUp, you can effectively communicate your project plan and secure the necessary support and resources to enhance your organization's cyber security measures.
Get Started with ClickUp's Cyber Security Project Proposal Template
IT professionals and cybersecurity teams can use this Cyber Security Project Proposal Template to streamline the process of pitching and implementing cybersecurity projects.
First, hit “Get Free Solution” to sign up for ClickUp and add the template to your Workspace. Make sure you designate which Space or location in your Workspace you’d like this template applied.
Next, invite relevant members or guests to your Workspace to start collaborating.
Now you can take advantage of the full potential of this template to secure your organization's data:
- Use the Project Proposal View to create a detailed project proposal, outlining objectives, scope, and resources required
- The Getting Started Guide View will guide you through the steps to initiate the cybersecurity project and ensure a smooth implementation
- Customize the Project Proposal status to Open when you start working on the project proposal
- Update tasks to the Complete status as you progress through each stage of the project
- Assign tasks to team members and set due dates to ensure accountability and timely completion
- Collaborate with stakeholders to gather necessary information and align goals
- Utilize comments and @mentions to communicate effectively and gather feedback
- Monitor and analyze tasks to track progress and make data-driven decisions
Related Templates
- Seed Processing Unit Project Proposal Template
- UX Project Proposal Template
- Basketball Court Project Proposal Template
- R&D Project Proposal Template
- Dairy Plant Project Proposal Template
Template details
Free forever with 100mb storage.
Free training & 24-hours support
Serious about security & privacy
Highest levels of uptime the last 12 months
- Product Roadmap
- Affiliate & Referrals
- On-Demand Demo
- Integrations
- Consultants
- Gantt Chart
- Native Time Tracking
- Automations
- Kanban Board
- vs Airtable
- vs Basecamp
- vs MS Project
- vs Smartsheet
- Software Team Hub
- PM Software Guide
Departments
Planning and strategy
- Strategy: Kent 2025
- UK's European university
- Annual review and reports
How we operate
- Constitution
- Regulations
- Charity information
- Modern Slavery Act Transparency Statement
- Vice-Chancellor
- Executive Group
- Principal officers
- Honorary graduates
- Schools and faculties
- Professional services
- External services
- Complete A-Z
More about Kent
- Career Opportunities
- Essential Kent
- Eastern ARC
- Regional impact
- Community relations
Events and what's on
- Full calendar
- Undergraduate term dates
Excellence at Kent
- Latest research news
- Research impact
- Publications
- Public engagement
Departments/people
- Find a Kent expert
- Research Services
- Innovation & Enterprise
- Graduate School
- Academic/research jobs
- Research degrees
- Search courses
- How to apply
- Postgraduate funding
- Graduate school
Undergraduate courses
- Fees and funding
Undergraduate courses 2023
Study abroad
Postgraduate courses
- Taught courses
Part-time and short courses
- Online prospectus
- Summer schools
International
- Foundation (IFP)
- Pre-sessional English
- Short-term programmes
- Applicant Days
- Informal visits
- Kent around the world
Useful links
- Accommodation
- Scholarships
Information for...
International students
- Parents and family
- New students
UK locations
- Validated institutions
European centres
Other locations
- Exchanges with over 100 overseas universities
- Study and work abroad
- Double-degrees
- Short-term study options
- 'International' courses
- Erasmus exchanges
- Study at Kent
- Application process
- When you arrive
- International Partnerships
- Worldwide partnerships
- International exchanges
- Alumni groups/networks
- International Recruitment
- English & world languages
Strategy & reputation
- International impact
- World-leading research
- International Research Impact
- Campus locations
International expertise
- Business services
- Collaborative projects
- Consultancy
- Employability points
- Undergraduate
- Postgraduate
- Part-time (undergraduate)
- Executive education
- Careers & Employability Service
- Kent Business School
- Conferences and functions
- Sports centre and facilities
News Centre
- Latest stories
- Expert comment
- Press office
- Social media
Students and staff
- Student news
- Campus transport news
- IT service alerts
- Submit a story
Lasting connections...
- Alumni and friends
- Alumni groups
- Former staff
- Telephone Campaign
- Congregations
- Discount on fees
- Alumni scholarships
- Online giftshop
Major projects
- Kent Law Campaign
- Kent Opportunity Fund
- Hong Kong & China Portal
Ways to give
- By post or phone
- Other options..
- School of Computing home
- Undergraduate degrees
- Master's degrees
- PhD and research degrees
- Computational Intelligence
- Data Science
- Programming Languages and Systems
- Research interests
- Suggested PhD projects
- Kent IT Consultancy
- Working with us
For current students & staff
- Information for students
- Systems support
- Information for staff
- School of Computing
- University of Kent
Example PhD project topics
Below please find a list of some example topics for PhD studies, proposed by selected academics of the Group. The list does not reflect all possible topics supervisors are interested, so you are recommended to study individual supervisors' research interests and publications and approach them for more advice. You are welcome to propose your own topics that match interests of supervisors of the Group. If you are interested in studying at our Group but need help to determine your supervisor and topic, please feel free to contact Professor Shujun Li [email protected] >, the Group Head, for advice. From time to time, we will offer funded PhD studentships .
Comprehensive understanding of cybercrime
Supervisor: budi arief.
- Mapping threats against cybercrime incidents, and looking at how these threats materialise, in order to understand the factors abetting or preventing them
- Conducting qualitative and quantitative study to gather data on various losses experienced by victims, as well as their circumstances, leading to the creation of victim profiles, which can help minimise the risk of victimisation
- Cataloguing existing measures and/or initiatives for combating cybercrime and evaluate their effectiveness
- Delving deeper into policing cybercrime and its associated metrics, such as the cost of policing tasks and statistics of cybercrime in the public sector
- Exploring other issues in human behavior and legal framework
Security and Privacy of the Internet of Things (IoT)
IoT has the potential to make our live more comfortable and effortless, but IoT devices could also pose new large-scale privacy and security risks that are not fully understood yet. For example, data collected from these devices (with or without authorisation from its owner) could reveal too much information about someone, and criminals might try to exploit this wealth of information in mounting more successful attacks, for example credit card fraud or social engineering attacks leading to identity theft. Furthermore, the abundance of connected, unsecured IoT devices makes it possible to launch a large scale DDoS attack. Therefore, new approaches and techniques for securing IoT devices are needed, which will be the focus of this research.
Dealing with insider threat
Insider threat is a significant and ever-present risk faced by any organisation. While security mechanisms can be put in place to reduce the chances of external attackers gaining access to a system, the issue is more complex when dealing with insider threat. If an employee already has legitimate access rights to a system, it is much more difficult to prevent them from carrying out inappropriate acts, because it is hard to determine whether the acts are part of their official work or indeed malicious. This research will look into a more comprehensive integration of human factors, as well as better machine learning techniques to obtain more accurate results, and more advanced decision making tools to help organisations to detect and respond to insider threats early.
Behavioural APIs for secure communicating systems
Supervisors: laura bocchi and andy king.
In this project you will develop a theory and tool for design and implementation of secure communicating systems. The project will centre on Behavioural APIs. Behavioural APIs are abstract specifications of application-level protocols; they go beyond traditional APIs in that they specify conversation patterns among components/services (and not just sets of supported operations). Behavioural API have been successfully applied to guarantee safety (eg., absence of deadlocks) via code generation, verification and monitoring. Security has been explored only to a limited extent in this context. The project will focus on data-centric security and provenance, but possibly involve other security aspects.
Minimal Cost Quantum Security Infrastructures
Supervisor: carlos perez delgado.
The existence of quantum algorithms, such as Shor's Integer Factorisation Algorithm, implies that quantum computers pose an existential threat to a sizeable portion of our current security infrastructures. Many digital services, from privacy, to authentication, rely on protocols like RSA, or Diffie-Hellman that in turn rely on the hardness of factorisation. At the same time, quantum information provides some ways to implement cryptographic primitives like privacy (e.g. quantum key distribution). Some of these, however, incur heavy overhead costs that may be infeasible for widespread adoption (e.g. heavy use of quantum communication).
The purpose of this research project is to propose new complete cryptographic infrastructures that are provably secure to both classical and quantum attacks, and have provably optimal overhead costs.
Reverse Engineering for Security
Supervisor: andy king.
Reverse Engineering is the process of taking a software artifact, such as a binary, and figuring out what it does. Reversing is important in the security industry where security engineers frequently have to inspect binaries when searching for security holes. This project will develop tooling not for reversing a binary to, say, a C program or even an intermediate language. Rather the project will develop tools that explain what a binary does by annotating it with information that details the values register might store. This will be achieved, not by directly executing the binary (since the binary may be malicious) but rather by following all paths through the binary. In this way, it is potentially possible to work out the values that registers will possibly store at each point in the binary. The studentship will develop this idea and apply it to develop tools for supporting security engineers.
Synthesizing Security and Privacy Requirements in Socio-technical Systems
Supervisors: özgür kafalı , tbd: kent law school.
Goal: To provide a formal process for developing comprehensive and consistent security and privacy requirements by taking into account both technical and social considerations. Motivation: Regulations and functional requirements help developers understand how software and its users should behave in specific situations. Breach reports help developers and security analysts identify cases where a deployed system fails, or is misused, whether maliciously or accidentally. While such artifacts are helpful, they are often ambiguous, inconsistent, and incomplete. Moreover, practical systems often need to comply with regulations that may overlap or conflict in subtle ways, thereby exacerbating the complexity of navigating through such artifacts. Plan: Formally analyze textual software artifacts via a collection of knowledge representation techniques and reasoning methodologies such as normative reasoning, ontologies, and automated information extraction, with exemplars on healthcare laws and regulations, social network privacy, and IoT and mobile applications. Contributions: A systematic and repeatable security requirements engineering process that includes socio-technical system design, and verification of stakeholder needs and user expectations against software implementation.
Digital Forensics by Design
Supervisors: özgür kafalı , tbd: school of psychology.
Goal: To build forensics capabilities into software and enhance all three core phases of the digital forensics process, i.e. collection of digital evidence; examination of evidence via monitoring and diagnosis; and reporting and validation of forensics hypotheses in support of a breach. Motivation: Data breaches are inevitable, no matter how well organisations fortify their software systems or train their users. Breaches may take months to detect and contain costing organisations valuable resources. As the variety of breaches increases, such as those caused by a malicious or criminal attack, a system glitch, or human error, and the generated amount of system logs to detect such breaches increases in parallel, the job of a forensics analyst is becoming increasingly difficult to sort through the logs and come up with a diagnosis. Plan: Explore formal AI-based methods such as intention recognition, temporal reasoning, and argumentation, as well as gamification techniques. Contributions: A comprehensive misuse profile customisable for specific software products based on understanding of human decision making and insider threats; an adaptive logging mechanism that can be embedded in a software implementation.
Detecting Filthy Tampers
Supervisors: andy king and laura bocchi.
Even if a compiler is verified so that one is assured that the executed code confirms to the behaviour of a high-level program, there is no reason to believe that the low-level code has not been tampered with post-compilation to insert a back-door or some other malicious behaviour through binary rewriting.So even if the source code has been published for public scrutiny, one has to check that the low-level conforms intended behaviour of the source. This is problematic if the compiler is a black-box and one has no control over the compilation process.A compiler will typically apply loop optimisations, such as loop inversion, which means that control structures of low-level code are not in a one-to-one relationship with the high-level code.The project will therefore aim to build model checking techniques which are tolerant of syntactic differences between high-level and low-level code, in order to search for paths (behaviours) which occur in the low-level code which were never intended in the source.
Self-adaptation applied to Security and Privacy
Supervisor: rogério de lemos.
A future challenge in any system from critical infrastructures to internet of things is ability of systems to look after themselves regarding security and privacy. The notion of self-protection would be a fundamental requirement in future systems considering their complexity and connectivity. At Kent we have worked on self-adaptive authorisation infrastructures, and have built prototypes that enable to handling insider threats using self-adaptive principles ( https://saaf-resource.kent.ac.uk/ ). The goal is to continue this work in other directions, but mainly, in the area of provision of assurances. If guarantees need to be provided about the security and privacy of a system, then these systems need to be perpetually evaluated during run-time, and this is a huge challenge.
Human-based Decision Making in Resilient Cyber Security Systems
Systems are becoming more complex and interconnected, and the access to system resources need to be controlled in an efficient and trusted way. Humans alone are not able to manage the complexity of these emerging systems, hence the need of automating the decision making regarding the protection of resources. However, full automation is undesirable because there are limits in what can be achieved with self-adaptation considering the unpredicted nature of attacks. This requires humans to be involved in some of the non-mundane decisions regarding the protection of the system. The challenge now is how to involve humans in the process of decision making considering that systems, their goals and context may evolve in a way that humans are not able to follow in order to have an accurate interpretation of its state, which might have an impact on insightful/informative decisions.
Self-adaptive Privacy Guardian
Supervisors: rogério de lemos and budi arief, perpetually evolving mechanisms for detecting and handling insider threats, various topics in cyber security (see below), supervisors: shujun li.
He offers a number of topics for potential PhD applicants. Click here to see a list of such topics maintained on his personal website.
Cyber security awareness campaigns: What works and what doesn't?
Supervisor: jason r.c. nurse.
While technology is a key component of cyber security approaches, human users also play a critical role to maintaining corporate security. There are a number of ways to get users involved, but one of the most attractive for organisations is that of security awareness campaigns. In these campaigns, companies adopt a range of training sessions (general and targeted), produce awareness material (e.g., posters, leaflets), and engage in simulated sessions (e.g., phishing employees directly, and security gamification). The aim of this project is to investigate what really works and doesn’t work, out of the range of awareness techniques proposed. This project will build on my previous work, engage with several stakeholders across industry and academia, and contribute to the knowledge present in current research.
Cyber security and psychology: where do we go from here?
Supervisor: jason r.c. nurse , tbd: school of psychology.
The human aspect of cyber security has become increasingly prominent in research and practice, a reality undoubtedly motivated by the range of cyberattacks that exploit individuals (e.g., phishing, social engineering), and the broader challenge of building secure and usable systems. This project seeks to combine the fields of computing, HCI and psychology to investigate the range of challenges faced by users, designers and implementors in creating systems and environments that are supportive of users. The goal will be to understand these challenges and seek to develop novel approaches, methods and techniques to address them. These will encompass technical as well as socio-technical solutions. As there are several different areas in which this project could focus, there background and research interests of the student will shape the research.
Network Intrusion Detection using Data Analytics
Supervisors: peter rodgers and budi arief.
This project is an intersection of Data Mining, Information Visualization and Security research. Whilst there are number of different techniques currently in use for network intrusion detection, they typically focus on examining single nodes or the traffic on a single edge. However, some attacks may be best detected by looking at a sub-networks level, or groups of nodes/edges as they change over time. The novel concept is to define patterns of sub-networks, which can then be compared to detect any anomalies in the network and so flagged as potential malicious behaviour. We will provide a visual analytics demonstrator where users can monitor and explore a visual representation of a network. This graph pattern matching has the additional benefit of being easily integrated into visual tools. Users have the ability to both see the patterns identified in the network, as well as define and tune the patterns to be found. The data to be evaluated in the proposed research will be temporal network data. Time slices will be defined, with edges connecting nodes between time slices that are unchanged over the time interval. Initial data will come from standard open access data sources. We will divide the data into that used for development and that reserved later for testing the effectiveness of the system. Evaluation will have three strands: (1) usability of the software by analysts; (2) effectiveness of the intrusion detection against other state-of-the-art intrusion detection tools (to see if our method can detect intrusion that is undetected by others); and (3) application in the field to see if the system is real-world ready.
School of Computing, University of Kent, Canterbury, Kent, CT2 7NF
Enquiries: +44 (0)1227 824180 or contact us .
Last Updated: 18/03/2019
- Kent on facebook
- Kent on twitter
- Kent on linkedin
- Kent on youtube
- Kent on flickr
- Kent on rss
Social media at Kent
© University of Kent - Contact | Feedback | Legal | FOI | Cookies
- SGroup: European Universities Network
- Eastern Academic Research Consortium
- Universities UK
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics in 2024
Home Blog Security 60+ Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
- Cyber security and the law
- The future of cyber security
5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorisation Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
KPMG Personalization

- Quantum is coming — and bringing new cybersecurity threats with it
Quantum computing changing the security infrastructure of the digital economy
- Share Share close
- 1000 Save this article to my library
- View Print friendly version of this article Opens in a new window
- Go to bottom of page
- Home ›
- Insights ›
The quantum-computing revolution is upon us — a paradigm shift in computing power that harnesses the laws of quantum mechanics to solve problems far too complex for today’s classical digital computers.
Quantum computers apply the unique behavior of quantum physics to computing, introducing unprecedented capabilities to traditional programming methods. From transforming drug research, energy use, manufacturing, cybersecurity and communications to enhancing AI applications, autonomous-vehicle navigation, financial modelling and more — quantum is poised to unlock a new reality.
The emerging quantum-computing industry is already making enormous advances — as more organisations discover its potential, the global market is expected to hit US$50 billion by the end of this decade. 1 Major technology companies are rapidly developing their quantum capabilities — Amazon, IBM, Google and Microsoft, for example, have already launched commercial quantum-computing cloud services, and there are significant investments in new players such as Quantinuum and PsiQuantum.
KPMG in Canada surveyed 250 large corporations and found that about 60 percent of organisations in Canada and 78 percent in the US expect quantum computers to become mainstream by 2030. 2 But as quantum proliferates, so do concerns about its potential impact on cybersecurity.
Most businesses surveyed are “extremely concerned” about quantum computing’s potential to break through their data encryption. Sixty percent in Canada and 73 percent in the US believe “it’s only a matter of time” before cybercriminals are using the power of quantum to decrypt and disrupt today’s cybersecurity protocols. At the same time, however, 62 percent in Canada and 81 percent in the US admit that they need to do a better job of evaluating their current capabilities to ensure their data remains secure. 3
KPMG Australia research shows that protecting data and dealing with cyber risks is viewed by C-suite executives and board members from private sector enterprises as a top challenge in 2024 — and for the next 3 to 5 years. 4
KPMG in Germany conducted research in collaboration with Germany’s Federal Office for Information Security (BSI), 95 percent of respondents believe quantum computing’s relevance and potential impact on today’s cryptographic security systems is “very high or high,” and 65 percent also say the average risk to their own data security is “very high or high.” Yet only 25 percent of firms say the threat posed is currently being addressed in their risk management strategy. 5
Quantum’s emerging threats demand solutions
The level of preparation that organisations do today is expected to be critical to limiting their exposure and vulnerability to emerging threats — making quantum risk planning a priority. Quantum computers can break encryption methods at an alarming speed, rendering ineffective encryption tools that are widely used today to protect everything from banking and retail transactions to business data, documents, email and more.
“Harvest-now, decrypt-later” attacks could enable adversaries to steal encrypted files and store them until more advanced quantum computers emerge.
KPMG firms are helping clients take action to understand and respond to the broad and unprecedented quantum-risk environment, as asymmetric encryption is used in multiple applications, from storage to communication. The risk landscape includes the following critical areas:
- Web browsing
- Remote access
- Digital signatures
- Communication
- Crypto currencies
The quantum-risk landscape at a glance
There is little time to lose for organisations to gain a deeper understanding of the risks quantum may pose to their operations and security. For every organisation that holds and processes data, they should consider the lifetime value of the data that they use, and the impact of that data being used or misrepresented by bad actors. For example:
Sensitive organisational data: Highly confidential data held by military services, national intelligence, finance and government organisations.
Critical infrastructure providers: Organisations whose complex systems are critical to the functioning of communities, cities, provinces and countries, including healthcare, transportation, utilities and telecommunications. Imagine, for example, the potentially disastrous impact of quantum disrupting the operation of a city’s sprawling power grid.
Long-life infrastructure providers: Organisations providing systems that are built to have a long life span for profitability, including satellite communications, payment terminals, Internet of Things (IoT) sensor networks and transportation. Whether data consists of customer information, medical records or government classified data, a breach can have catastrophic financial, reputational and legal consequences. And some organisations are currently unaware of cyber attackers already accessing and storing encrypted company data with the aim of decrypting it in the future using a quantum computer.
Personal data handlers: Organisations managing personal data with a long confidentiality span are required by law to protect such data, including government, healthcare, financial firms and insurance organisations. They need to ensure protection over an extended period of 5, 10, 20 years or more.
Quantum computing will upend the security infrastructure of the digital economy. Quantum technology in general promises to disrupt several areas of advanced technology and bring unprecedented capabilities that can be harnessed to improve the lives of people worldwide. At first glance it appears to be a curse to security, as cryptographic algorithms that proved to be secure for decades may be breached by quantum computers. This is in fact a blessing in disguise since this challenge gives us a much-needed impetus to build stronger and more-resilient foundations for the digital economy.
Dr. Michele Mosca Institute for Quantum Computing The University of Waterloo
“Mosca’s Theorem”, illustrated below, suggests the timeframe required to protect data. Dr. Michele Mosca’s theorem stresses the need for organisations to begin applying diligence in the post-quantum space right away. It states that the amount of time that data must remain secure (X), plus the time it takes to upgrade cryptographic systems (Y), is greater than the time at which quantum computers have enough power to break cryptography (Z).
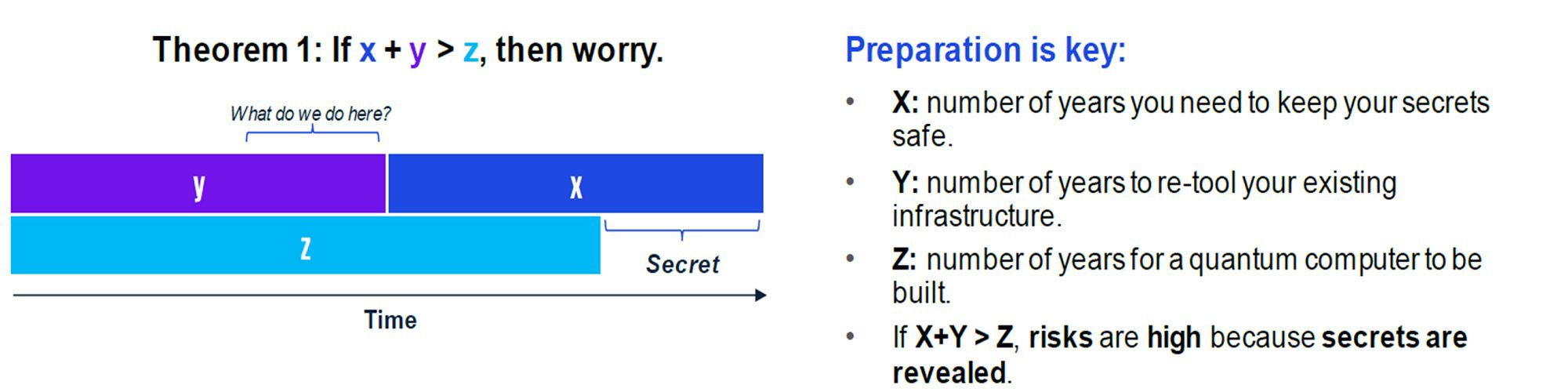
Once organisations are aware of their risk environment, they should be in a position to prioritise activity and mitigate or eliminate risks. However, this may not be a quick or simple process and may take years for each organisation.
Managing technical debt, for example, can be a significant challenge for organisations relying on systems that will be incapable of running modern cryptographic profiles. There is now an opportunity to evaluate migration timelines and understand how long it will take to make infrastructure quantum resistant. To do this, organisations should understand the challenge and allocate budgets for both the mitigation and ongoing monitoring that the post-quantum world will require.
It’s critical that organisations not only prepare for the quantum threat in their long-term risk planning, but also strengthen data protection now to help minimise quantum’s potentially disruptive and costly impacts.
The rules of the game are changing to meet the new risk reality
As quantum emerges and organisations continue to explore and discover both its game-changing advantages and threats, new legislation and regulations are in the works. In 2022, a U.S. law was passed that requires government agencies to take action in using post-quantum cryptography — and encourages the private sector to follow suit 7 .
The National Institute of Standards and Technology (NIST) in December 2023 released two draft publications to guide organisations aiming to redefine their capabilities and combat potential quantum-based attacks. The documents — “Quantum Readiness: Cryptographic Discovery” and “Quantum Readiness: Testing Draft Standards for Interoperability and Performance” — outline concrete issues and potential solutions when migrating to a new post-quantum cryptographic standard. 8
The growing list of initiatives also includes:
- The Quantum Computing Cybersecurity Preparedness Act 2022 , advising US federal organisations to prepare now for a post-quantum cybersecurity (PQC) world;
- National Security Memorandum on “Promoting US Leadership in Quantum Computing While Mitigating Risk to Vulnerable Cryptographic Systems”;
- White House Memorandum on “Migration to Post-Quantum Cryptography”;
- Monetary Authority of Singapore MAS/TCRS/2024/01 : Advisory on Addressing the Cybersecurity Risks Associated with Quantum 9 ;
- Quantum Security for the Financial Sector: Informing Global Regulatory Approaches, World Economic Forum in collaboration with the Financial Conduct Authority 10 .
This growing trend is likely to be investigated by other countries as we see a global movement towards identifying the risks and requirements of secure quantum technology.
Act now to help combat quantum’s risks
While quantum computing may seem like a futuristic science fiction concept, the technology is indeed poised to exert major consequences across today’s cybersecurity capabilities. We believe innovation is needed without delay.
The National Institute of Standards and Technology (NIST) has released a draft of the NIST Cybersecurity Framework 2.0 (CSF 2.0) — a major update to the Cyber Security Framework (CSF) it released in 2014 to help organisations reduce cybersecurity risk. To be finalised and published in early 2024, CSF 2.0 reflects changes in the cybersecurity landscape and will offer additional guidance on implementing the CSF. 11
The NIST has also chosen four encryption tools that it says are designed “to withstand the assault of a future quantum computer, which could potentially crack the security used to protect privacy in the digital systems we rely on every day.” 12 The four encryption algorithms will become part of NIST’s post-quantum cryptographic standard and all are expected to be finalised and ready for use in 2024. 13
Meanwhile, improvements and standards in Quantum Random Number Generators 14 (QRNGs), for entropy enhancement and randomisation, and Quantum Key Distribution, 15 a secure communication method for exchanging encryption keys only known between shared parties, also aim to harness the power of quantum technology and protect data.
It’s important to note that today’s quantum solutions are creating a false sense of security — as we do not know if the quantum algorithms considered resistant will remain that way as quantum computers become larger and more mainstream. The danger is illustrated by the discovery of vulnerabilities in the NIST-selected encryption algorithm CRYSTALS-Kyber. 16
Where to start as the power of quantum advances
Organisations can start to prepare by gaining a precise understanding of potential risks across their value chain. They should also identify methods to become more cryptographically agile in updating and deploying new cryptographic techniques as they become available. It’s also crucial to create end-of-life strategies for the data, products and systems that will become obsolete or unable to support new cybersecurity requirements in a quantum-computing world.
Here are key questions to ask going forward as quantum evolves:
- How long does your data need to be secure and are you liable for its management?
- What is the actual and reputational damage in case of a compromise?
- How long does it take for your system to migrate to quantum secure?
- Do you have an inventory of cybersecurity measures?
- Are you liable for a third-party service or cloud provider and are they are moving to a quantum-safe environment?
Key actions to help mitigate quantum risks:
- Provide insightful awareness training, education and roadmaps to senior leadership;
- Implement roadmaps and solutions to modernise cryptographic environments;
- Provide guidance on investing in quantum-resistant technologies;
- Develop contingency and mitigation plans to prevent a quantum attack; and
- Continuously monitor the fast-evolving quantum and security environment.
How KPMG can help
KPMG firms are helping organisations mitigate quantum risks. Our technology consulting specialists have extensive experience in cybersecurity and quantum technologies to support your quantum journey. Our quantum risk assessment can provide a deeper understanding of the specific threats posed by quantum technology.
With the help of KPMG firms, you can apply the outcomes of this assessment to build a customised cybersecurity strategy that fully encapsulates preparation for the quantum threat into your long-term risk planning — helping to prioritise your data and systems that are at risk. Steps to quantum-secure encryption include:
Discover: Identify cryptographic algorithms and protocols used to protect data and assets.
Assess: Perform a risk assessment to identify quantum-vulnerable systems and assets.
Manage: Prioritise remediation efforts and develop a remediation roadmap.
Remediate: Implement mechanisms that enable crypto agility, and transition vulnerable cryptographic systems to post-quantum cryptography based on priority.
Monitor : Perform ongoing monitoring of remediation efforts and changes to the threat and regulatory landscape.
KPMG specialists are using our quantum readiness assessment methodology and innovative collaborations to help make a difference for clients. KPMG firms’ collaboration with IBM Quantum (Quantum Safe) and InfoSec Global allow us to begin understanding the cryptographic footprint/baseline and work towards remediation and potential digital solutions. KPMG specialists are here to help.
Get in touch
Connect with us.
- Find office locations kpmg.findOfficeLocations
- Email us kpmg.emailUs
- Social media @ KPMG kpmg.socialMedia
- Request for proposal
Related content

Capabilities of AI continue to garner interest and high expectations for the financial reporting function
Capabilities of AI continue to garner interest and high expectations for the function
AI and IoT are fundamentally altering business - 2023 AI + IoT year in review
Article by Lyon Poh, Partner, Technology Consulting and Edmund Heng, Partner, Technology Risk, KPMG in Singapore
Article by Lyon Poh and Edmund Heng
1 https://home.kpmg/ca/en/home/market-insights/predictions/technology/quantum-computing-will-help-us-solve-our-most-difficult-problems.html
2 https://kpmg.com/ca/en/home/media/press-releases/2023/05/quantum-computing-is-coming-but-few-are-ready-for-it.html
3 Ibid.
4 https://assets.kpmg.com/content/dam/kpmg/au/pdf/2024/keeping-us-up-at-night-australian-business-leader-challenges-2024.pdf
5 https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Crypto/Marktumfrage_EN_Kryptografie_Quantencomputing.pdf?__blob=publicationFile&v=3
6 Mosca’s Theorem, Michele Mosca
7 Quantum Computing Cybersecurity Preparedness Act - This act addresses the migration of executive agencies' information technology systems to post-quantum cryptography.
8 https://www.nextgov.com/cybersecurity/2023/12/nist-releases-2-draft-guides-prepare-post-quantum-migration/392934/
9 https://www.mas.gov.sg/regulation/circulars/advisory-on-addressing-the-cybersecurity-risks-associated-with-quantum
10 https://www.weforum.org/publications/quantum-security-for-the-financial-sector-informing-global-regulatory-approaches/
11 https://csrc.nist.gov/projects/post-quantum-cryptography
12 https://www.nist.gov/news-events/news/2023/08/nist-standardize-encryption-algorithms-can-resist-attack-quantum-computers
13 Ibid.
14 https://phys.org/news/2023-05-quantum-random-generator-independently-source.html
15 https://quside.com/how-does-quantum-key-distribution-qkd-work/
16 https://eprint.iacr.org/2023/1084
Comment: Why the SBTi’s proposal to include carbon credits is on the right side of climate history
- Medium Text

María Mendiluce is CEO of the We Mean Business Coalition, which brings together seven leading non-profit organizations in sustainability. She has 25 years of experience in corporate climate action and sits on the executive board of the Science Based Targets initiative. María took an active role in the founding of the Mission Possible Partnership, a multi-sector decarbonization initiative, and co-founded the SME Climate Hub, an SME-focused net-zero initiative.

Mandy Rambharos is Vice President, Global Climate Cooperation, ad leads EDF's work to promote more ambitious and effective global climate action under the Paris Agreement by directing multilateral engagement, including at the U.N., G20 and G7. She also leads EDF’s strategy to promote well-designed carbon pricing and markets that support the transformation toward a low-emissions future, while improving the well-being of marginalized communities.

Sustainability Chevron
Biden team sets out path for ethanol aviation fuel subsidies.
President Joe Biden's administration on Tuesday released guidance on its sustainable aviation fuel (SAF) subsidy program that allows corn-based ethanol to qualify for the program if it is sourced from farms using climate-friendly growing techniques.


IMAGES
VIDEO
COMMENTS
Cyber security is the practice of defending against malicious attacks on computers, computerized systems, networks, and data. The term "cloud computing" is used in various contexts, from business to mobile computing, and can be classified into a few broad categories. Cyber security is centered on the industry standard of confidentiality ...
making security risk assessment a wicked problem: 1.3.1 Security Analysts Knowledge and Expertise Experts rely on tacit knowledge to conduct the analysis. Security experts are not all equal in their knowledge and skillset. For example, security knowledge can be acquired from specialized courses, on-the-job training, or self-study.
Please find attached our cybersecurity proposal, including the associated services and activities. We have a proven track record of providing concrete advice, feasible solutions, and peace of mind over your secure systems and servers. Our team of experts combines innovation, communication, and knowledge of the latest technology and techniques ...
The primary objec ve of this project is to develop a comprehensive framework for cybersecurity and. resilience that can be used by organiza ons and individuals. The framework will include a set of ...
One-Step Academic Program Proposal 2.22.2018 Page 4 of 44 The Computer Science Department at UGA has 5 faculty whose research areas are in cybersecurity and privacy and is authorized to hire a new tenure-track faculty in cybersecurity
Moreover, it will find modern-day approaches (ML, DL, etc.) to make NIDE more efficient in countering cyber-attacks. It will see how the incorporation of modern computational models can improve NIDS. Audience. This research targets academics, large corporations, governments, and network security and ML practitioners. Background Review Existing ...
If you're still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic. A comprehensive list of cybersecurity-related research topics. Includes 100% free access to a webinar and research topic evaluator.
Research proposal examples. Writing a research proposal can be quite challenging, but a good starting point could be to look at some examples. We've included a few for you below. Example research proposal #1: "A Conceptual Framework for Scheduling Constraint Management".
Proposal Example 1. Information and Communications Technology (ICT) has taken a central role in modern society. Unfortunately, malicious hackers and cybercrime have become a stubborn and expensive part of the ICT landscape. This has made providing cybersecurity a defining challenge for our era. Many strategic plans and National Academies of ...
Cyber Security Resilience Team, Tesco bank and Morgan Stanley. Student numbers will be 10 in the first year, then increasing to 25 or more thereafter. There is a strong push from central government for research and teaching in cyber security, as part of the national UK Cyber Security Strategy.
Table 1. Descriptions and summaries of proposed categories of cyber security research.....15 Table 2. Examples of topics from each of the four cyber security subdisciplines.....30 Table 3. Compact description & list of classes proposed for an interdisciplinary cyber security minor.....31 Table 4.
These two technologies create security creates a shield over the organization's data to prevent illegal users. In this, cybersecurity deals with intelligent online cyber-attacks. In fact, information/network security is recognized as part of cybersecurity. Overall, it is the best protective technology to detect and prevent cyber-attacks.
A Systematic Literature Review on the Cyber Security. 1 Dr.Yusuf Perwej, 2 Prof. (Dr.) Syed Qamar Abbas, 3 Jai Pratap Dixit, 4 Dr. Nikhat Akhtar, 5Anurag. Kumar Jaiswal. 1 Professor, Department of ...
Use this cyber security sample template to define the proposal context — problem & solution — and the objectives — skills, training, and security enhancements — your firms will achieve by entering into a deal with you. Download the Project Context And Objective Template. 3.
ClickUp's Cyber Security Project Proposal Template is here to help you outline and present a comprehensive plan to safeguard your business from potential risks. With this template, you can: Identify and assess vulnerabilities in your current systems. Propose effective security measures and strategies to mitigate risks.
The human aspect of cyber security has become increasingly prominent in research and practice, a reality undoubtedly motivated by the range of cyberattacks that exploit individuals (e.g., phishing, social engineering), and the broader challenge of building secure and usable systems.
Executive Summary of Proposal. We request the creation of a Bridge Professorship to strengthen expertise at Tufts in Cyber Security and Policy and to provide leadership for the creation of a variety of degree programs in Cyber Security and Policy. Cyber Security and Policy is an emerging cross-disciplinary field that impacts many aspects of our ...
our national security depends on a strong cyber culture. To stay ahead of the threat, cybersecurity needs to be steeped into the national consciousness through education, sustained messaging and increased cooperation among businesses and government. My research examines the vulnerabilities, and cites case studies, national policy and expert ...
invites research and development project proposals in the area of Cybersecurity. Cybersecurity Research Development Programme (RDP) initiative of CySecK is aimed at achieving the following objectives: • Provide financial and academic support to active researchers to foster and promote R&D in the emerging field of cybersecurity. • Utilise ...
Criminal Law. Cyber Security Future Research Topics. Developing more effective methods for detecting and responding to cyber attacks. Investigating the role of social media in cyber security. Examining the impact of cloud computing on cyber security. Investigating the security implications of the Internet of Things.
I.C.S. College, Khed, Ratnagri. Abstract: In the current world that is run by technology and network connections, it is crucial to know what cyber security is. and to be able to use it effectively ...
world-wide leading cyber security researchers. With these goals at hand, the Ariel Cyber Innovation Center is soliciting proposals for funding research projects in cyber security. The emphasis will be on innovative and forward-looking research that may assist in establishing the Ariel Cyber Innovation Center as a world leader in cyber security ...
High Representative of the Union for Foreign Affairs and Security Policy on a European Cybersecurity Strategy. The objective of the Strategy is to ensure a secure and trustworthy digital environment, while promoting and protecting fundamental rights and other EU core values. This proposal is the main action of the Strategy.
From transforming drug research, energy use, manufacturing, cybersecurity and communications to enhancing AI applications, autonomous-vehicle navigation, financial modelling and more — quantum is poised to unlock a new reality. ... Imagine, for example, the potentially disastrous impact of quantum disrupting the operation of a city's ...
Unfortunately, the President's FY 2025 budget recommends new penalties for hospitals and health systems for not meeting what the Administration refers to as "essential cybersecurity practices," which we understand would be based on the consensus-based cybersecurity practices previously referenced.
The recent statement from the board of the Science Based Targets initiative (SBTi) that it will consider recognizing environmental attribute certificates, including carbon credits, for abatement ...