
151+ Computer Presentation Topics [Updated 2024]

For both professionals and fans, keeping up with the most recent developments and trends in the rapidly evolving field of technology is essential. One effective way to share and acquire knowledge is through computer presentations.
Whether you are a seasoned presenter or someone looking to enhance your tech presentation skills, choosing the right topics is key to delivering a compelling and informative session.
In this blog, we’ll explore various computer presentation topics, their relevance, and provide insights into tailoring presentations for different audiences and occasions.
How do you Tailor Topics According to Audience and Occasion?
Table of Contents
Tailoring topics according to the audience and occasion is a crucial aspect of delivering an effective and engaging presentation. Here are some strategies and considerations to help you customize your computer presentation topics based on your audience and the specific occasion:
- Know Your Audience
- Assess Knowledge Levels: Understand the expertise of your audience. Are they beginners, intermediate users, or experts in the field? This assessment will guide you in selecting the appropriate depth and complexity of your topics.
- Consider Backgrounds: Take into account the professional backgrounds, interests, and industries of your audience. Tailor your examples and case studies to resonate with their experiences.
- Identify Audience Needs and Goals:
- Address Pain Points: If possible, research or survey your audience to identify their challenges and pain points. Tailor your presentation to address these concerns, providing practical solutions and insights.
- Align with Goals: Understand the goals and objectives of your audience. Tailor your topics to align with their aspirations, whether it’s professional development, problem-solving, or staying updated on industry trends.
- Adapt to the Occasion:
- Event Type: Consider the type of event you are presenting at. Is it a conference, workshop, seminar, or a more informal gathering? The format and expectations of the event will influence your choice of topics.
- Time Constraints: Be mindful of the time allotted for your presentation. Tailor the scope and depth of your topics to fit within the designated time frame.
- Customize Content:
- Relevance to Industry: If your audience belongs to a specific industry, tailor your topics to address challenges and innovations relevant to that industry. Provide concrete examples and case studies that resonate with their professional experiences.
- Localize Examples: Consider the cultural context and geographic location of your audience. If possible, use examples and references that are familiar to them, making the content more relatable.
- Engage in Interactivity:
- Q&A Sessions: Plan for interactive sessions, allowing the audience to ask questions. This helps you gauge their interests and tailor your responses to address specific concerns.
- Polls and Surveys: Incorporate interactive elements such as polls or surveys to gather real-time feedback. Use the results to adjust your presentation on the fly if necessary.
- Provide Actionable Takeaways:
- Practical Applications: Tailor your topics to include practical applications and actionable takeaways. Ensure that your audience can apply the knowledge gained from your presentation in their professional or personal endeavors.
- Workshops and Demos: For hands-on sessions, tailor your topics to include workshops or live demonstrations. This enhances the learning experience and allows the audience to see practical implementations.
- Be Adaptable:
- Read the Room: Pay attention to the audience’s reactions during the presentation. Be adaptable and ready to adjust your approach based on their engagement levels and feedback.
- Flexibility in Content: Have backup content or supplementary materials that can be introduced based on audience interest or questions.
Software Development and Programming
- Trends in Programming Languages: A Comprehensive Overview
- Introduction to Python: Basics and Beyond
- Exploring the World of JavaScript Frameworks
- Best Practices in Software Development Methodologies
- The Evolution of Mobile App Development
- Low-Code Platforms: Revolutionizing Software Development
- The Impact of Microservices Architecture on Modern Applications
- DevOps Practices: Streamlining Development and Operations
- Code Review Techniques for Quality Assurance
- GUI vs. Command Line Interfaces: Pros and Cons
Emerging Technologies
- Artificial Intelligence (AI): An Introduction and Applications
- Machine Learning Algorithms: A Deep Dive
- The Role of Natural Language Processing (NLP) in AI
- Computer Vision: Applications and Challenges
- Internet of Things (IoT) and its Transformative Power
- Blockchain Technology: Beyond Cryptocurrencies
- Augmented Reality (AR) and Virtual Reality (VR) in Computing
- Edge Computing: Enhancing Network Performance
- Quantum Computing: A Glimpse into the Future
- 6G Technology: Enabling the Next Generation of Connectivity
Cybersecurity
- Cyber Threats: Types, Trends, and Prevention Strategies
- Ethical Hacking: Unveiling Security Vulnerabilities
- Biometric Security Systems: Enhancing Authentication
- Cryptography: Ensuring Secure Communication
- Security Measures for Computer Networks: A Practical Guide
- Privacy Concerns in the Digital Age: Safeguarding Information
- Incident Response Planning for Cybersecurity
- Cloud Security Best Practices
- Cybersecurity Awareness Training for Employees
- The Future of Cybersecurity: Emerging Challenges
Data Science and Big Data
- Introduction to Data Science: Concepts and Applications
- Data Analysis Techniques: From Descriptive to Predictive Analytics
- Big Data Technologies: Hadoop, Spark, and Beyond
- Data Warehousing: Storing and Retrieving Massive Datasets
- Data Visualization Tools: Making Sense of Complex Data
- Predictive Modeling in Business: Leveraging Data Insights
- Internet of Things (IoT) and Big Data Integration
- Real-Time Analytics: Turning Data into Actionable Insights
- Data Ethics: Navigating the Challenges of Responsible Data Use
- Data-driven Decision Making in Organizations
Computer Hardware and Networking
- Latest Advancements in Computer Hardware
- The Role of Graphics Processing Units (GPUs) in Modern Computing
- Networking Protocols: A Deep Dive into TCP/IP, UDP, and More
- Wireless Technologies: Wi-Fi 6 and Beyond
- Cloud Computing Models: IaaS, PaaS, and SaaS Explained
- Edge Computing vs. Cloud Computing: Choosing the Right Approach
- Green Computing: Sustainable Practices in IT
- Quantum Computing and its Potential Impact on Industry
- 5G Technology: Revolutionizing Mobile Communication
- Wearable Technology: Integrating Computing into Everyday Life
Artificial Intelligence (AI) Applications
- AI in Healthcare: Transforming Diagnosis and Treatment
- AI in Finance: Applications and Risk Management
- AI in Customer Service: Enhancing User Experience
- AI in Education: Personalized Learning and Assessment
- AI in Autonomous Vehicles: Navigating the Future
- AI in Agriculture: Precision Farming and Crop Monitoring
- AI in Cybersecurity: Detecting and Preventing Threats
- AI in Natural Language Processing (NLP): Conversational Interfaces
- AI in Robotics: Innovations and Challenges
- AI in Retail: Personalized Shopping Experiences
Internet and Web Technologies
- Evolution of the Internet: From ARPANET to the Present
- Web Development Trends: Responsive Design and Progressive Web Apps
- Content Management Systems (CMS): Choosing the Right Platform
- E-commerce Platforms: Building Successful Online Stores
- Search Engine Optimization (SEO) Strategies for Web Visibility
- Cloud-based Web Hosting Solutions: Comparisons and Best Practices
- Web Accessibility: Designing Inclusive and User-Friendly Websites
- Social Media Integration: Enhancing Online Presence
- Web Security Best Practices: SSL, HTTPS, and Beyond
- The Future of the Internet: Trends and Predictions
Mobile Technologies
- Mobile Operating Systems: A Comparison of iOS and Android
- Mobile App Monetization Strategies: Ads, Subscriptions, and Freemium Models
- Cross-platform Mobile Development: Pros and Cons
- Mobile Payment Technologies: From NFC to Cryptocurrencies
- Mobile Health (mHealth) Applications: Improving Healthcare Access
- Location-based Services in Mobile Apps: Opportunities and Challenges
- Mobile Gaming Trends: Augmented Reality and Multiplayer Experiences
- The Impact of 5G on Mobile Applications
- Mobile App Testing: Ensuring Quality User Experiences
- Mobile Security: Protecting Devices and User Data
Human-Computer Interaction (HCI)
- User Experience (UX) Design Principles: Creating Intuitive Interfaces
- Usability Testing Methods: Evaluating the User-Friendliness of Products
- Interaction Design Patterns: Enhancing User Engagement
- Accessibility in Design: Designing for All Users
- Virtual Reality (VR) and User Experience: Design Considerations
- Gamification in User Interface Design: Enhancing Engagement
- Voice User Interface (VUI) Design: Building Natural Interactions
- Biometric User Authentication: Balancing Security and Convenience
- The Evolution of Graphical User Interfaces (GUIs)
- Wearable Technology Design: Integrating Fashion and Functionality
Cloud Computing
- Cloud Service Models: IaaS, PaaS, and SaaS Explained
- Cloud Deployment Models: Public, Private, and Hybrid Clouds
- Cloud Security Best Practices: Protecting Data in the Cloud
- Serverless Computing: Streamlining Application Development
- Cloud Computing in Business: Cost Savings and Scalability
- Cloud-Native Technologies: Containers and Orchestration
- Microservices Architecture in the Cloud: Breaking Down Monoliths
- Cloud Computing Trends: Edge Computing and Multi-cloud Strategies
- Cloud Migration Strategies: Moving Applications to the Cloud
- Cloud Computing in Healthcare: Enhancing Patient Care
Robotics and Automation
- Robotics in Manufacturing: Increasing Efficiency and Precision
- Autonomous Robots: Applications and Challenges
- Humanoid Robots: Advancements in AI-driven Robotics
- Robotic Process Automation (RPA): Streamlining Business Processes
- Drones in Industry: Surveillance, Delivery, and Beyond
- Surgical Robotics: Innovations in Medical Procedures
- Robotic Exoskeletons: Assisting Human Mobility
- Social Robots: Interacting with Humans in Various Settings
- Ethical Considerations in Robotics and AI
- The Future of Robotics: Trends and Predictions
Ethical Considerations in Technology
- Responsible AI: Ethical Considerations in Artificial Intelligence
- Data Privacy Laws: Navigating Compliance and Regulations
- Bias in Algorithms: Addressing and Mitigating Unintended Consequences
- Ethical Hacking: Balancing Security Testing and Privacy Concerns
- Technology and Mental Health: Addressing Digital Well-being
- Environmental Impact of Technology: Green Computing Practices
- Open Source Software: Community Collaboration and Ethical Licensing
- Technology Addiction: Understanding and Combating Dependencies
- Social Media Ethics: Privacy, Fake News, and Cyberbullying
- Ethical Considerations in Biometric Technologies
Future Trends in Technology
- The Future of Computing: Quantum Computing and Beyond
- Edge AI: Bringing Intelligence to the Edge of Networks
- Biocomputing: Merging Biology and Computing
- Neurotechnology: Brain-Computer Interfaces and Cognitive Enhancement
- Sustainable Technologies: Innovations in Green Computing
- 7G and Beyond: Envisioning the Next Generation of Connectivity
- Space Technology and Computing: Exploring the Final Frontier
- Biohacking and DIY Tech: A Look into Citizen Science
- Tech for Social Good: Using Technology to Address Global Challenges
- The Convergence of Technologies: AI, IoT, Blockchain, and More
Miscellaneous Topics
- Technology and Education: Transforming Learning Experiences
- Digital Transformation: Strategies for Modernizing Businesses
- Tech Startups: Navigating Challenges and Achieving Success
- Women in Technology: Empowering Diversity and Inclusion
- The History of Computing: Milestones and Innovations
- Futuristic Interfaces: Brain-Computer Interfaces and Holography
- Tech and Art: Exploring the Intersection of Creativity and Technology
- Hackathons: Fostering Innovation in Tech Communities
- The Role of Technology in Disaster Management
- Exploring Careers in Technology: Opportunities and Challenges
Tips for Effective Computer Presentations
- Mastering the Art of Public Speaking in the Tech Industry
- Designing Engaging Visuals for Technical Presentations
- The Dos and Don’ts of Live Demonstrations in Tech Presentations
- Building a Compelling Narrative: Storytelling Techniques in Tech Talks
- Handling Q&A Sessions: Tips for Addressing Audience Questions
- Time Management in Tech Presentations: Balancing Content and Interaction
- Incorporating Humor in Technical Presentations: Dos and Don’ts
- Creating Interactive Workshops: Engaging Audiences in Hands-on Learning
- Leveraging Social Media for Tech Presentations: Tips for Promotion
- Continuous Learning in the Tech Industry: Strategies for Staying Informed
Case Studies and Real-World Applications
Real-world examples and case studies add practical relevance to computer presentations. Showcase successful projects, discuss challenges faced, and share lessons learned.
Analyzing the impact of technology in real-world scenarios provides valuable insights for the audience and encourages a deeper understanding of the subject matter.
Future Trends in Computer Presentation Topics
Predicting future trends in technology is both exciting and challenging. Presenters can offer insights into upcoming technological developments, anticipate challenges and opportunities, and encourage continuous learning in the rapidly evolving tech landscape.
Discussing the potential impact of technologies like 6G, augmented reality, or advancements in quantum computing sparks curiosity and keeps the audience abreast of the latest innovations.
In conclusion, computer presentations serve as powerful tools for knowledge sharing and skill development in the tech industry. Whether you’re presenting to novices or seasoned professionals, the choice of topics, presentation skills, and a thoughtful approach to ethical considerations can elevate the impact of your presentation.
As technology continues to evolve, staying informed and exploring diverse computer presentation topics will be instrumental in fostering a culture of continuous learning and innovation.
Embrace the dynamic nature of technology and embark on a journey of exploration and enlightenment through engaging computer presentations.
Related Posts

Step by Step Guide on The Best Way to Finance Car

The Best Way on How to Get Fund For Business to Grow it Efficiently
- Question Papers
- Scholarships
100+ Computer Science Presentation Topics (Updated)
This is a list of computer science Presentation Topics for students and professionals. These updated topics can be used for PowerPoint Paper presentation, Poster Presentation, classroom ppt presentation, seminars, seminars, webinars and conferences. etc. These presentation topics will be beneficial for students of Engineering and management courses such as BE Computer science, B Tech IT, MCA, BCA and MBA.
Below is the list of Best Computer Science Presentation Topics.
Artificial intelligence
Advanced Research Projects Agency Network (ARPANET)
AI & critical systems
Quantum Computing
Arithmetic logic unit (ALU)
Accelerated Graphics Port (often shortened to AGP)
ATX (Advanced Technology eXtended)
Sixth Sense Technology: Concept VS. Reality
BASIC – Beginner’s All-purpose Symbolic Instruction Code
Foldable Phones: Future of Mobiles
Basic computer skills
Blu-ray Disc
Cloud computing
CD-ROM (compact disc read-only memory)
Machine Learning
Cellular architecture
Central Processing Unit (CPU)
Cloud Print for Android
Chip (integrated circuit)
Computer multitasking
Cloud computing applications
Cloud computing basics
Cloud Printing for Windows
Computer architectures
Edge Computing
Computer Diagnostic Softwares
Computer form factor
Computer hardware troubleshooting
Cyber Security: New Challenges
Computer Networks
Computer software programs
Computer tracking software
The world of Blockchain
Conventional Binary Numbering System
Conventional PCI (PCI is an initialism formed from Peripheral Component Interconnect
DASD (Direct Access Storage Device)
Internet of Things (IoT)
Desktop Computers
Digital Visual Interface (DVI)
Transparent Display: Concept Vs Reality
DIMM – DIMM which means (dual in-line memory module)
DisplayPort
DNA computers
DVD (Digital Video Disc or Digital Versatile Disc)
Dynamic random-access memory (DRAM)
EEPROM (E2PROM) – Electrically Erasable Programmable Read-Only Memory
Electronic Delay Storage Automatic Calculator (EDSAC)
Embedded computers
Google cloud computing
EPROM – An EPROM (rarely EROM), or erasable programmable read-only Memory
Evolution of Computers
Expansion card (expansion board, adapter card or accessory card)
ExpressCard
FDDI – Fiber Distributed Data Interface
Intelligent Apps
Flash Memory
Graphics processors
Google Glass: Future of Computers!
Hard disk drive (HDD)
Harvard Architecture vs Von Neumann architecture
HDMI (High-Definition Multimedia Interface)
Standardization of web
Image scanner
Input and output devices (collectively termed I/O)
Type C port: The Gamechanger
IOPS (Input/Output Operations Per Second, pronounced eye-ops)
Latest Computer Technologies
Latest Trends in Computer Science
Mainframe computers
Manchester Small-Scale Experimental Machine (SSEM or “Baby”)
Mechanical Analog Computers
Mini-VGA connectors
Motherboard – the central printed circuit board (PCB)
Multiprocessing
Network Topologies
Neural computers
Non-Uniform Memory Access (NUMA) computers
Non-volatile memory
Neuralink: The brain’s magical future
Non-volatile random-access memory
Operating system (OS)
Optical computers
Optical disc drive
Optical disc drive (ODD)
Palmtop computer
Neuralink: Next Big Tech?
PCI Express (Peripheral Component Interconnect Express)
PCI-X, short for PCI-eXtended
Personal Computers (PC)
Personal Digital Assistant (PDA)
Photolithographed semiconductors
Programmable read-only memory (PROM)
Programming language
PSU (power supply unit)
Quantum computer vs Chemical computer
RAID (redundant array of independent disks)
Random-access memory or RAM
Read-only memory or ROM
Register machine vs Stack machine
Remote computer access
Scalar processor vs Vector processor
SIMM, or single in-line memory module
Solid State Drive (SSD)
Spintronics based computer
Static random-access memory (SRAM)
Super Computers
Synchronous dynamic random access memory (SDRAM)
Teleprinter
Ternary computers
Video Graphics Array (VGA) connector
Wearable computer
Virtual Reality
This is all about latest and best presentation topics for computer science and applications studies.
You’ll also like to READ:
Share with friends

151+ Interesting Computer Presentation Topics For Students
In the dynamic world of technology, effective communication is key, and mastering the art of computer presentations is more crucial than ever. Whether you’re a student looking for captivating topics for your next presentation, a professional aiming to enhance your presentation skills, or simply someone intrigued by the intersection of technology and communication, this blog is tailored for you. Explore diverse computer presentation topics, from the latest software innovations to strategies for creating visually compelling slides. Join us on a journey of discovery and empowerment in the realm of computer presentations. Let’s turn your ideas into impactful presentations!
Table of Contents
About Computer Presentation Topic
Selecting an engaging computer presentation topic is crucial for captivating your audience. The chosen topic should resonate with the audience’s interests, incorporate current trends, and possess interdisciplinary appeal. Whether you’re addressing elementary students or higher education classes, tailoring the topic to the educational level is essential. Integrating technology trends, such as artificial intelligence, virtual reality, and cybersecurity, adds a modern touch. Successful presentations involve overcoming challenges like stage fright and technical glitches, while effective delivery includes mastering body language, vocal modulation, and humor. Stay updated with future trends to keep your presentations innovative and impactful.
Benefits of Choosing Computer Presentation Topics
Choosing the right computer presentation topics offers a multitude of benefits for presenters and their audiences:
- Capturing Audience Attention: Intriguing topics immediately grab the audience’s interest, creating a positive first impression and setting the tone for an engaging presentation.
- Encouraging Active Participation: Interesting topics inspire audience involvement, fostering a dynamic environment where questions are asked, discussions arise, and participants actively contribute to the presentation.
- Enhancing Learning and Retention: Well-chosen topics promote effective learning by making the material memorable. Engaged audiences are more likely to retain information and apply it beyond the presentation.
- Building Presenter Confidence: Presenting on a topic that excites you boosts confidence, making it easier to connect with the audience and deliver a compelling presentation.
- Creating Memorable Experiences: Choosing intriguing topics ensures that your presentation leaves a lasting impression on the audience, increasing the likelihood that they’ll remember and appreciate your message.
Also Read: Botany Research Topics
List of Computer Presentation Topics For Students
Here is a complete list of computer presentation topics for students in 2024:
Artificial Intelligence (AI)
- Machine Learning Algorithms for Image Recognition
- Natural Language Processing in Virtual Assistants
- Ethics in AI: Bias Detection and Mitigation
- Reinforcement Learning in Autonomous Systems
- Explainable AI: Making Complex Models Understandable
- AI in Healthcare: Predictive Diagnosis Models
- Robotics and AI Integration for Industrial Automation
- AI-powered Chatbots for Customer Service
- AI-based Fraud Detection in Financial Transactions
- Sentiment Analysis using Deep Learning Techniques
- AI-driven Personalized Learning Systems
Cybersecurity
- Blockchain Technology for Secure Transactions
- Cyber Threat Intelligence and Analysis
- Biometric Authentication Systems
- Quantum Cryptography: The Future of Secure Communication
- IoT Security Challenges and Solutions
- Ransomware Detection and Prevention Strategies
- Threat Hunting in Network Security
- Cloud Security Best Practices
- Social Engineering Awareness and Training
- Endpoint Security in a Remote Work Environment
- Security Challenges in Smart Cities
Data Science
- Predictive Analytics for Business Forecasting
- Big Data and Healthcare Analytics
- Data Privacy in the Era of Big Data
- Recommender Systems for E-commerce Platforms
- Time Series Analysis for Stock Market Prediction
- Data Visualization with Augmented Reality
- Fraud Detection using Machine Learning
- Ethical Considerations in Data Science
- Social Media Analytics for Market Insights
- Predicting Disease Outbreaks with Epidemiological Models
- Geospatial Analysis for Urban Planning
Internet of Things (IoT)
- Smart Home Automation Systems
- Industrial IoT for Smart Factories
- IoT-enabled Environmental Monitoring
- Wearable Technology for Health Tracking
- Smart Agriculture: IoT Applications in Farming
- Connected Cars and Vehicular Communication
- IoT-based Energy Management Systems
- Retail IoT: Enhancing Customer Experience
- Security Challenges in IoT Devices
- Smart Cities: Enhancing Urban Living with IoT
- IoT in Education: Interactive Learning Environments
Cloud Computing
- Serverless Computing: Architecture and Applications
- Hybrid Cloud Solutions for Enterprise IT
- Edge Computing and Its Impact on Cloud Services
- Cloud-native Development Best Practices
- Multi-cloud Management Strategies
- Cost Optimization in Cloud Computing
- Cloud Security and Compliance
- DevOps in a Cloud Environment
- Containerization with Docker and Kubernetes
- Cloud-based Data Warehousing
- Disaster Recovery Planning in the Cloud
Mobile App Development
- Cross-platform Mobile App Development with Flutter
- Augmented Reality Apps for Enhanced User Experience
- Mobile Health Apps for Remote Patient Monitoring
- Progressive Web Apps (PWAs) and Their Advantages
- Mobile Gaming: Trends and Future Developments
- Location-based Services in Mobile Applications
- Accessibility in Mobile App Design
- Mobile Wallets and Digital Payment Solutions
- Internet of Things (IoT) Integration in Mobile Apps
- Mobile App Security Best Practices
- Voice Recognition in Mobile Applications
Human-Computer Interaction (HCI)
- User Experience (UX) Design Principles
- Gamification in Interface Design
- Accessibility Technologies for Differently-abled Users
- Virtual Reality (VR) for Immersive User Experiences
- Usability Testing and User Feedback Analysis
- Gesture-based Interfaces in Computing
- Emotional Design in User Interface
- Cognitive Load Reduction in Interface Design
- Human-Centered Design for Healthcare Applications
- Ethical Considerations in HCI Research
- Cross-cultural Aspects of User Interface Design
Software Engineering:
- Agile Development Methodologies in Software Engineering
- Continuous Integration and Continuous Deployment (CI/CD)
- Test-Driven Development (TDD) Practices
- Microservices Architecture: Design and Implementation
- Software Design Patterns and Their Applications
- Code Quality Metrics and Analysis Tools
- DevSecOps: Integrating Security into DevOps Practices
- Scalability in Software Systems
- Software Maintenance and Legacy Code Refactoring
- User Acceptance Testing (UAT) Strategies
- Software Project Management Best Practices
Computer Graphics and Visualization:
- 3D Modeling and Animation Techniques
- Virtual Reality (VR) for Architectural Visualization
- Data Visualization for Business Intelligence
- Augmented Reality (AR) in Educational Materials
- Computer-generated Imagery (CGI) in Film Production
- Interactive Infographics for Information Presentation
- Visual Analytics for Complex Data Sets
- Real-time Rendering in Video Games
- Geometric Algorithms for Computer Graphics
- Motion Capture Technology in Animation
- Computer Vision for Image Recognition
Computer Networks
- Software-Defined Networking (SDN) Applications
- Edge Computing in Network Architecture
- 5G Technology and Its Implications
- Internet Protocol Security (IPsec) Implementation
- Network Function Virtualization (NFV)
- Wi-Fi 6 and the Future of Wireless Networking
- Peer-to-Peer (P2P) Networks and Applications
- Network Traffic Analysis for Security
- Quantum Networking: Concepts and Challenges
- Network Performance Optimization Strategies
- Mobile Edge Computing in 5G Networks
E-Learning and Educational Technology
- Adaptive Learning Systems for Personalized Education
- Gamified Learning Platforms for Student Engagement
- Virtual Labs for Science Education
- Learning Analytics: Data-driven Insights in Education
- Augmented Reality (AR) in Educational Settings
- Blockchain in Education: Credential Verification
- Online Assessment and Proctoring Solutions
- Artificial Intelligence in Educational Chatbots
- Mobile Learning Apps for Skill Development
- Virtual Reality (VR) Field Trips in Education
- Social Learning Platforms for Collaborative Education
Quantum Computing
- Quantum Algorithms for Optimization Problems
- Quantum Cryptography and Key Distribution
- Quantum Machine Learning Models
- Quantum Error Correction Techniques
- Quantum Supremacy and Its Implications
- Topological Quantum Computing
- Quantum Computing in Drug Discovery
- Quantum Computing for Financial Modeling
- Quantum Internet: Connecting Quantum Nodes
- Quantum Simulation for Physical Phenomena
- Quantum Cloud Computing Services
- Biodiversity Monitoring using Technology
Biotechnology and Computational Biology
- Computational Drug Design and Discovery
- Genomic Data Analysis for Precision Medicine
- Bioinformatics Tools for DNA Sequencing Analysis
- Protein Structure Prediction Algorithms
- Systems Biology Approaches in Biotechnology
- Computational Modeling of Biological Systems
- Metagenomics and Microbiome Analysis
- Computational Epidemiology for Disease Modeling
- CRISPR-Cas9: Computational Challenges and Solutions
- Synthetic Biology and Computational Design
- Computational Neurobiology and Brain Modeling
Social Media and Networking
- Sentiment Analysis of Social Media Content
- Social Network Analysis for Influencer Marketing
- Deep Learning for Fake News Detection
- Recommender Systems in Social Media Platforms
- Ethical Implications of Social Media Algorithms
- Virality Prediction in Online Content
- Social Media Analytics for Business Strategy
- User Behavior Modeling in Online Communities
- Privacy Concerns in Social Media Data Mining
- Augmented Reality Filters in Social Media
- 1Impact of Social Media on Mental Health
Green Computing and Sustainability
- Energy-Efficient Computing Technologies
- Sustainable Data Centers and Green IT Practices
- E-waste Management in the Digital Age
- Carbon Footprint Analysis of Cloud Services
- Renewable Energy Integration in Computing Systems
- Green Software Development Practices
- Sustainable IT Policies for Organizations
- Eco-Friendly Hardware Design Principles
- Environmental Impact Assessment in Tech Projects
- Circular Economy Approaches in Electronics
Explore these diverse “Computer Presentation Topics” across various categories to inspire and inform your next compelling project or presentation. Each topic promises to unravel the fascinating intersections of technology and its diverse applications in our rapidly evolving digital landscape.
Future Trends in Computer Presentation Topics
The landscape of computer presentation topics is continually evolving, and staying ahead of future trends is key to delivering impactful presentations:
Emerging Technologies Influence Topics
Future presentations will likely delve into cutting-edge technologies such as artificial intelligence , augmented reality, and blockchain, shaping the landscape of discussion topics.
Interactive and Immersive Presentations
Expect a shift towards more interactive and immersive presentations, leveraging technologies like virtual reality to engage audiences on a deeper level.
Sustainability and Ethical Tech Discussions
With increasing awareness, future presentations may focus on sustainable practices and ethical considerations in technology, reflecting the industry’s evolving values.
Integration of Smart Devices
As smart devices become more prevalent, presentations may explore topics related to seamless integration and collaboration between various technologies.
Adapting to Remote and Hybrid Settings
Future trends will likely involve addressing challenges and opportunities associated with remote or hybrid presentation settings, emphasizing effective communication in a digitally connected world.
In conclusion, mastering the art of computer presentation topics involves a dynamic interplay of creativity, technology, and effective communication. By selecting intriguing topics, presenters can capture the audience’s attention, encourage participation, and leave a lasting impression. Embracing emerging trends such as interactive presentations, ethical tech discussions, and seamless integration of smart devices prepares presenters for the evolving landscape. Overcoming challenges, refining delivery techniques, and staying attuned to audience needs are essential aspects of successful presentations. As technology advances, so too must presentation approaches, ensuring that speakers continue to inspire, educate, and connect with their audiences in the ever-changing world of computer presentations.
1. Can I suggest a presentation topic?
Yes! We welcome your ideas. If you have a compelling computer presentation topic in mind, share it with us through the contact page. Your input matters!
2. Are the computer presentation topics suitable for all skill levels?
Certainly! Our topics cater to a broad audience, accommodating both beginners and seasoned professionals. Whether you’re starting your journey or seeking advanced insights, there’s something for everyone.
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- E & C ENGG
- JAVA PROGRAMS
- PHP PROGRAMS
- ARTIFICIAL INTELLIGENCE
- CLOUD COMPUTING
- WIRELESS TECHNOLOGY
Latest Technical Paper Presentation Topics
- by Ravi Bandakkanavar
- April 14, 2024
This post contains a wide variety of technical papers chosen from various Engineering streams. The latest Technical Paper Presentation Topics include trending topics from emerging Technology like Artificial Intelligence, Machine Learning, 5G Technology, Cybersecurity, and Cloud Computing. It also includes topics from different Engineering streams like Computer Science and Engineering, Electronics Communications and Engineering, Electrical and Electronic Engineering, Mechanical Engineering, and Automobile Engineering.
- Blockchain Technology
- Chat GPT and its capabilities
- How 5G Technology can Revolutionize the Industry?
- 5G Wireless Technology
- Impact of the Internet on Our Daily Life
- The technology behind Face Unlocking in Smartphones
- 3D Printing Technology
- Anti-HIV using nanorobots
- Humanoid Robots
- Virtual Reality: working and examples
- Metaverse and how Apps are developed in Metaverse
- Smart Eye Technology
- Augmented Reality
- Automatic Video Surveillance Systems
- Automatic number plate recognition
- Cloud Computing vs. Distributed Computing
- Importance of Cloud Computing to Solve Analytical Workloads
- Attendance Monitoring Intelligent Classroom
- Automatic Mobile Recharger Station
- Automatic sound-based user grouping for real-time online forums
- Bio-computers/Biomolecular Computers
- What is Big Data?
- Biomedical instrumentation and signal analysis

- Artificial intelligence and the impact of AI on our lives
- Is Artificial Intelligence a Threat or a Benefit?
- Top 10 Ways Artificial Intelligence Future will Change the World
- Artificial Intelligence: Technology that Hosts Race between Enterprises
- The Role of Artificial Intelligence in the Healthcare Industry
- How AI Technology Can Help You Optimize Your Marketing
- Narrow AI vs General AI: Understanding The Key Differences
- Future Of Industrial Robotics With AI
- Causes of CyberCrime and Preventive Measures
- What is Phishing? How to tackle Phishing Attacks?
- What is the Dark Web? How to Protect yourself from the Dark Web?
- Cyberbullying: The emerging crime of 21 st Century
- Anatomy and working of search engines
- Bionic Eye – a possible path toward the Artificial retina
- Bluetooth-based Smart Sensor Networks
- Broadband access via satellite
- Brain-computer interface
- Blue eyes technology
- Brain-controlled car for the disabled using artificial intelligence
- Brain Port device
- Brain Finger Print Technology
- BrainGate Technology
- Digital jewelry
- Development of an Intelligent Fire Sprinkler System
- Capturing packets in secured networks
- Digital Speech Effects Synthesizer
- Aqua communication using a modem
- Serverless Edge Computing
- Intrusion detection system
- How to prepare for a Ransomware attack?
- What is the Dark Web? How to Protect Your Kids from the Dark Web?
Artificial Intelligence Topics for Presentation
- Carbon nanotubes
- Cloud computing
- Mobile Ad hoc Networks (MANETs)
- Narrow AI vs General AI
- Security aspects in mobile ad hoc networks (MANETs)
- Mobile Ad Hoc Network Routing Protocols and applications
- Graphical Password Authentication
- GSM-based Advanced Wireless Earthquake Alarm System for early warning
- Computerized Paper Evaluation using Neural Network
- Deploying a wireless sensor network on an active volcano
- Data Mining and Predictive Analytics
- Understanding Data Science and Data-Driven Businesses
- Dynamic Car Parking Negotiation and Guidance Using an Agent-based platform
- Real-Time Street Light Control Systems
- Data Security in Local Networks using Distributed Firewalls
- Design of a wireless sensor board for measuring air pollution
- Design of diamond-based Photonics devices
- Design of Low-Density Parity-Check Codes
- What is LiDAR Technology?
- Tizen Operating System – One OS for everything
- Authentication using Biometric Technology
- Speech Recognition
- The working of Self-Driving Vehicles
- Speech Processing
- Digit recognition using a neural network
- Digital Audio Effects Control by Accelerometry
- Digital Camera Calibration and Inversion for Stereo iCinema
- Dynamic resource allocation in Grid Computing
- Dynamic Virtual Private Network
- Earth Simulator – Fastest Supercomputer
- Electromagnetic Applications for Mobile and Satellite Communications
- Electronic nose & its application
- Elliptical Curve Cryptography (ECC)
- Cryptocurrency Wallet – is it the Future of Blockchain Technology
- Reactive Power Consumption in Transmission Line
- SPINS – Security Protocol For Sensor Network
- Smart Bandage Technology
- Embedded web server for remote access
- Encrypted Text chat Using Bluetooth
- Electronic toll collection
- Electronic waste (e-waste)
- Apache Hadoop Introduction
- Embedded web server for industrial automation
- Eyegaze system
- Fuel saver system
- Guarding distribution automation system against cyber attacks
- Face detection technology
- Falls detection using accelerometry and barometric pressure
- Fast Convergence algorithms for Active Noise Controlling Vehicles
- Fault-tolerant Routing in Mobile ad-hoc network
- Ferroelectric RAM
- Fingerprint recognition system by neural networks
Technical Paper Topics on CyberSecurity
- Flexible CRT Displays
- Fluorescent Multilayer Disc (FMD)
- Fluorescent Multilayer Optical Data Storage
- Forecasting Wind Power
- Fractal image compression
- Fractal robots
- Geometric Invariants in Biological Molecules
- Global positioning response system
- Broadband over power line
- Card-based security system
- Face Recognition Technology
- GSM Digital Security Systems for Printer
- Groupware Technology
- Indian Regional Navigation Satellite System
- GSM Security And Encryption
- Hardware implementation of background image modeling
- HAVI: Home Audio Video Interoperability
- Hawk Eye – A technology in sports
- High Altitude Aeronautical Platforms
- High-Performance Clusters
- High-Performance DSP Architectures
- High-speed circuits for optical interconnect
- High-speed LANs or the Internet
- Holographic Data Storage
- Holographic Memory
- Holographic Versatile Disc
- Holt-Winters technique for Financial Forecasting
- HomeRF and Bluetooth: A wireless data communications revolution
- How does the Internet work?
- Hyper Transport Technology
- How does a search engine work ?
- How does google search engine work ?
- Human-computer interaction & its future
- Design of a color Sensing System for Textile Industries
- GSM-based Path Planning for Blind Persons Using Ultrasonic
- Imbricate cryptography
- Implementation of hamming code
- Implementation of QUEUE
- Image transmission over WiMAX Systems
- Implantable on-chip Power Supplies
- Integrating Wind Power into the Electricity grid
- Integration of wind and solar energy in smart mini-grid
- Intelligent navigation system
- Intelligent Patient Monitoring System
- Intelligent RAM: IRAM
- Intelligent Software Agents
- Interactive Voice Response System
- Internet architecture and routing
- Internet Protocol duplicate address detection and adaptation
- Investigation of the real-time implementation of learning controllers
- IP spoofing
- IP redirector features
- iSCSI: The future of Network Storage
- ISO Loop magnetic couplers
- Jamming and anti-Jamming Techniques
- Light-emitting polymers
- Load balancing and Fault-tolerant servers
- Light Interception Image Analysis
- Lightning Protection Using LFAM
- Liquid Crystal on Silicon Display (LCOS)
- Location estimation and trajectory prediction for PCS networks
- Low-Power Microelectronics for Biomedical Implants
- Low-Power Oscillator for Implants
- Magnetic Random Access Memory
- Managing Data In Multimedia Conferencing
- Microchip production using extreme UV lithography
- Modeling of wind turbine system for an Interior Permanent magnet generator
- Moletronics – an invisible technology
- Power generation through Thermoelectric generators
- Multi-Protocol Label Switching
- Multiuser Scheduling for MIMO broadcasting
- Multisensor Fusion and Integration
- Parasitic computing
- Password paradigms
- Polymer memory – a new way of using plastic as secondary storage
- Programmable logic devices (PLD)
- Non-Volatile Static RAM
- Optical coherence tomography
- Open source technology
- Ovonic unified memory
- Personal satellite assistant systems
- PH control technique using fuzzy logic
- Pluggable Authentication Modules (PAM)
- Power Efficiency and Security in Smart Homes
- Proactive Anomaly Detection
- Prototype System Design for Telemedicine
- QoS in Cellular Networks Based on MPT
- Quad-Core Processors
- Real-Time Operating Systems on Embedded ICs
- Real-Time Speech Translation
- Real-Time Systems with Linux/RTAI
- Reliable and Fault-Tolerant Routing on Mobile Ad Hoc Network
- Robotic Surgery
- Vehicle monitoring and security system
- Space-time adaptive processing
- Radiofrequency identification (RFID) technology
- Rapid prototyping
Paper Presentation Topics for Computer Science Engineering
- Secured web portal for online shopping
- Securing underwater wireless communication networks
- Security analysis of the micropayment system
- Security requirements in wireless sensor networks
- Semantic web
- Sensitive skin
- Snake robot the future of agile motion
- Software-Defined Radio (SDR)
- Importance of Software-Defined Wide-Area Networks
- SPWM(sinusoidal pulse width modulation) technique for multilevel inverter
- Switchgrass
- Solar Powered Speakers
- Security on Wireless LAN Adaptive cruise control
- Session Initiation Protocol (SIP)
- Shallow water Acoustic Networks
- Significance of real-time transport Protocol in VOIP
- Simulating Quantum Cryptography
- Single photon emission computed tomography
- Smart cameras for traffic surveillance
- Smart Fabrics
- Space Mouse
- Space Robotics
- Speech Enhancement for Cochlear Implants
- Speed Detection of moving vehicles using speed cameras
- Swarm intelligence & traffic safety
- Synthetic Aperture Radar System
- Systems Control for Tactical Missile Guidance
- The Architecture of a Moletronics Computer
- The Evolution of Digital Marketing
- Thermal infrared imaging technology
- Thought Translation Device (TTD)
- Three-dimensional password for more secure authentication
- Ultrasonic motor
- Wearable biosensors
- Traffic Light Control System
- Wireless integrated network sensors
- Ultrasonic detector for monitoring partial discharge
- Ultra-Wideband Communication
- What is IPaaS? Trending IPaaS Services Available In the Market
- Wireless Computer Communications Using Sound Waves
- Click to share on Twitter (Opens in new window)
- Click to share on Facebook (Opens in new window)
- Click to share on LinkedIn (Opens in new window)
- Click to share on Pinterest (Opens in new window)
- Click to share on Pocket (Opens in new window)
213 thoughts on “Latest Technical Paper Presentation Topics”
Hello sir! Hope you are doing well. I have a technical paper presentation this semester, so I would like some suggestions in the domain of HCI, AI- ML, and Data science. Thank you sir.
Hello sir! , Can you help me on what kind of application that are very useful in the present?
Are you looking for mobile applications or web applications? Automating the manual processes will add more value.
work automation (can be delivery, operations, movement, robotics, AI/ML etc) Traffic control systems Communication/Data transfer VR/AR
Hi sir! Can you help me what can feature can i add in Log In System for Covid 19 . Thankyousmuch sir❤️
If you are looking for a Covid application for the information purpose, it may include the following things: 1. Covid statistics (country/state/city/daily/weekly/monthly wise) 2. Individuals health history 3. Vaccination status 4. Hospitals and health centers information
You can add many more things like health hygiene shops, tourism etc.
need some technical topic related to ECE
Did it help? Would you like to express? Cancel reply
Presentory for Windows
Presentory for mac, presentory online.
Rebrand your approach to conveying ideas.
Differentiate your classroom and engage everyone with the power of AI.
Knowledge Sharing
Create inspiring, fun, and meaningful hybrid learning experiences
Create with AI
- AI Tools Tips
Presentation Ideas
- Presentation Topics
- Presentation Elements
- Presentation Software
- PowerPoint Tips
Presentation Templates
- Template Sites
- Template Themes
- Design Ideas
Use Presentory Better
- Creator Hub
More Details
- Basic Knowledge
- Creative Skills
- Inspirational Ideas
Find More Answers
- LOG IN SIGN UP FOR FREE
- Hot Paper Presentation Topics For CSE
- 10 Unique PowerPoint Design Ideas to Captivate Your Audience
- Mastering Business Presentation Skills for Success (Innovative Business Presentation Ideas Updated)
- Creative 8 New Year Presentation Ideas with PowerPoint Themes
- Crafting an Effective PowerPoint Front Page Design for Maximum Impact
- Mastering PESTEL Analysis with PowerPoint: Guide and Templates
- Highlighting The Important Components of Real Estate PowerPoint and How to Make One
- Designing A Sales Plan Presentation for PowerPoint - An Overview of All Details
- Best Presentation Themes to Engage Your Audience in 2023
- Best Presentation Topics for Engineering Students
- 5 Engaging Presentation Topics for University Students
- 10 Interesting Presentation Topics for Students That Will Help You Shine
- Intriguing Topics for Engaging Computer Science Presentations
- Best 10 Selected Current Topics for Presentation to All Audience
- Elevate Your Skills: Best Topics for Presentation in English
- Top MBA Presentation Ideas To Elevate Your MBA Education
- Full Guide About Best ESL Presentation Topics for Students
- A Complete Guide to Create Company Profile PowerPoint Presentation With Templates
Are you searching for paper presentation topics for CSE ? Computer science and engineering is a rapidly emerging field. The latest developments and up-to-date information gain more attention there. That’s why selecting a hot topic boosts academic and professional growth. Presenting such topics elevates networking opportunities and attracts industry experts. Thus, it results in internships or job opportunities.
Moreover, presenting a hot topic can set you apart from your peers. If you aim to publish your paper, addressing current work trends is essential. Keeping in view the importance of technical paper presentation topics for CSE . In this article, we will explore innovative and creative solutions. This paper will discuss top trending topics and presentation ideas.
In this article
- Trending Topics in CSE Presentation
- Presentation Ideas for CSE Students
- Best Presentation Software – Presentory, Making our CSE Presentation Appealing
Part 1. Trending Topics in CSE Presentation
Imagine having an older smartphone without the latest updates of 2023. It is the same as the CSE field without tech revolutions and transformation. Staying up-to-date is the only secret to success in computer science and engineering. Moreover, students choose a career or a professional trying to be market-competitive. Read further to know some impactful CSE presentation topics .
1. Artificial Intelligence
The current most advancing area of CSE is Artificial Intelligence. It refers to the ability of computer-based systems to perform human-like functions and is designed to work like human cognition. AI programs are based on machine learning and deep learning systems. Thus, make a presentation introducing AI and its application in daily life areas.
Later on, discuss expected advancements in those aspects. So, further plans can be prepared and implemented according to your research information. You can also shed light on the potential use of AI in diagnosis and treatments. Also, explore algorithm trading or fraud detection in finance. Moreover, you can discuss how AI in self-driving vehicles can reduce manual labor and risk management.
2. Edge Computing
Edge computing is a turning computing paradigm that involves networks near users. Edge refers to processing data at high speed and bringing it closer to where it is generated. Some of its possible components include edge devices, on-premises infrastructure, and network edge. You can use this PPT topic for CSE students and discover its useful applications.
For instance, discuss the combination of AI and edge computing for city development and traffic management. Moreover, you can examine its role in IoT (Internet of Things) and highlight intelligent devices. Also, explore its role in optimizing manufacturing and quality controls. Above all, guide students on how 5G networks and edge computing enable low latency services.
3. Quantum Computing
An area of computer science that is based on quantum theory. This technology uses the law of mechanics to solve problems of classic computers. Quantum algorithms use new approaches and create multidimensional computational spaces. For your update, Google and Microsoft are developing their quantum computers. You can discuss their claims and implications.
Moreover, elaborate cloud-based quantum and its accessibility to developers. Also, highlight challenges in quantum error correction code to make it more reliable. Furthermore, you can explain the principles of quantum cryptography, including Quantum Key Distribution (QKD).
4. Robotics
It's a branch of CSE that includes robot design, conception, operation, and manufacture. It contains 3 fundamental parts: software, electrical, and mechanical. According to some predictions, 20 million manufacturing jobs will be lost by 2030. In this regard, robotics plays a vital role and sets an automated future. So, many types of robots can be discussed in the presentation paper.
Moreover, you can incorporate AI-supported robotic systems that include machine learning and deep learning in the CSE presentation topic . You can also introduce the use of robotic drones in crop monitoring and harvesting. Also, discuss potential applications in pollution clean-up and robotics surgeries.
5. Cybersecurity
In simple terms, cybersecurity is concerned with protecting digital and computer-based systems. Professionals usually aim to protect the data of companies and software from threats. Statistics show cybersecurity careers have grown 37% in the recent decade. In your presentation, you can cover password-based authentication and biometric authentication.
Furthermore, it explores implementations of the zero-trust security model. Highlight the impact of ransomware attacks and strategies to recover for organizations. Also, you can address security challenges in voting systems. Plus, it emphasizes the importance of blockchain technology and consensus algorithms. Moreover, it can be strongly used in securing mobile applications.
6. Bioinformatics
Bioinformatics refers to storing, interpreting, and analyzing biological data by computer technology. Computational methods, software tools, and algorithms are used to understand genetic variations. Protein structures and DNA structures are also studied by it. Thus, there are a variety of topics to be discussed under bioinformatics.
Highlight personalized medicine field and genomics data of patients for treatment plans. Moreover, it combines AI and deep learning to detect disease and its biomarkers. However, CSE in bioinformatics involves data mining, sequence alignment, genome assembly, etc.

7. Cloud Computing
It refers to a situation where computing is done on the cloud rather than a desktop or portable device. It includes managing, storing, and accessing data from remote servers. For instance, Google launched App Engines as its cloud computing. There are public, private, and hybrid modes of cloud computing. It has become an integral part of computing that supports applications.
You can explore serverless computing, its development, and its benefits in your presentation. Also, one can discuss multi-cloud management tools and simplify its resources. Moreover, you can convey the cost optimization issues and plan cloud cost monitoring. Cloud services are also closely related to 5G technology. In addition, developers can merge edge computing and IoT to provide mobile services with speed.
8. Secured Web Portal for Online Shopping
Web portals are immensely used for shopping for products. It enables a single platform to core services and content. To ensure the privacy of financial information, secure web portals are essential. However, one can utilize blockchain technology for data integrity. Also, MFA technology can be used, such as OTP and biometrics.
Another factor that can be studied is voice activation, such as Alexa and Google Assistant, to tackle security challenges. Furthermore, developers can focus on AI chatbots to protect customers' data. You can also explore Augmented Reality (AR) to examine how they provide secure shopping experiences.
9. Polymer Memory
Plastic memory refers to polymer memory, an emerging concept in CSE. They are used to store memory in devices by using organic polymers. It can be retained and stored in a flexible and environment-friendly way. So, one can introduce this technology along with its working principles. In addition, explore the types of polymers, such as conductive and ferroelectric, in your technical paper presentation topics for CSE.
Furthermore, current obstacles, research, and industry adaptations can be highlighted. Traditional and polymer memory can also be compared regarding cost and benefits. You can also examine commercialization and eco-friendly aspects of it. Plus, the data accessibility, manufacturing costs, and compatibility with devices can be discussed.
10. Screenless Display
Cutting-edge technology to view digital content without any traditional screen is called Screenless Display. It projects information into surroundings or directly into the human eye. In computer science, this technology is revolutionizing the way we interact. For this purpose, AR glasses like Magic Leap are being used. Additionally, working on a Virtual Reality (VR) Headset is going to enhance the gaming experience.
Moreover, you can discuss the Brain-Computer Interfaces (BCIs), which enable thought-controlled devices. Gesture-based interfaces can also be explored that allow digital interaction through body movements. Also, you can teach the project mapping and light-field displays to the students.

Part 2. Presentation Ideas for CSE Students
Nowadays, CSE students are learning about technologies and embracing shining futures. Presentations can play a crucial role in learning and knowledge sharing. In this regard, you have to select a CSE presentation topic that suits your interests and expertise. Below are some creative ideas to brainstorm according to your requirements.
1. Creativity
Technical topics for PPT presentation for CSE that are creative gain audience engagement and interest. However, choose a topic that unleashes your creativity in the project. Students can combine digital art and programming to enhance art experiences. Moreover, you can introduce humanoid robots programmed to perform creative tasks.
You can also discuss how AI can be used in the image recognition of many objects. Furthermore, creative projects at the hackathon can also be presented. It enables you to highlight challenges and innovative coding solutions. By discussing the creative algorithms, the audience can also obtain knowledge and inspiration.
2. Abstraction
Considering your crowd's expertise level, use the abstraction of concepts. Thus, you can break complex data structures into diagrams, graphs, and tables. Moreover, you can visually present the machine learning systems, including the neural networks or clustering algorithms.
Software Defined Networking (SDN) can also be abstracted in neural networks. Also, layers in cybersecurity, digital threats, and encryption can be abstract. So, these kinds of topics prove beneficial in the case of non-technical audiences.
3. Data and Information
For professionals, paper presentation topics for CSE must contain information to deliver. So, select a topic with a background, an introduction, and specific practical methods. Furthermore, data and information are used in many areas, like agriculture, journalism, and health care. For example, AI and data analytics can combine to manage emergency and relief efforts.
Data analytic sensors can also help in personalizing market strategies. Also, data security can be examined in terms of securing transactions. By mixing data and AI, explore the role of data sets used in machine learning training.

4. Algorithms
Algorithms play a vital role in solving problems in various domains. Some of its aspects include algorithm designs, applications, and analysis. Thus, one can explain algorithms like Grover's and Shor's algorithms. Moreover, you can discuss the algorithms in language processing, like machine translation and sentiment analysis.
Also, highlight concepts of routing, online algorithms, and resource allocation. In blockchain technology, Proof of Stake (PoS) and Poof of Work (PoW) algorithms can be explored. You can also explain algorithms designed for distribution and parallel computing.
5. Programming
The heart of computer science engineering is computer programming. However, one can elaborate on code refactoring and secure coding techniques. In addition, discuss concepts like functional programming and Python programming. Also, you can demonstrate TensorFlow, which is a popular machine learning model.
You can also discuss how to utilize Botpress or Dialogflow to create chatbots and discuss integration possibilities. Furthermore, parallelism and concurrency in programming can also be explored in how they relate to multi-processing and multi-threading programming.
6. Internet
Interconnected networks are known as the Internet. Through the internet, people are connected through intricate web servers and data centers. In your presentation, explore an emerging phenomenon like the Internet of Things (IoT). The dark web is another concern of the internet and an upcoming hot topic of the digital age.
Additionally, the fundamentals of internet protocols can be discussed. In addition, internet technologies can be discovered, like HTTP/3 and IPv6. Above all, one can discuss 5G technology, internet models, and applications.
7. Global Impact
Apart from discussing the latest algorithms and programming. One can work on current issues and come up with digital solutions. Highlight a topic that contains global impact, like sustainability or other advancements. Thus, study market trends or challenges and introduce remote job technologies. In the healthcare section, you can discuss the working on telemedicine for underdeveloped regions.
Moreover, you can explore the development of eco-friendly technologies and present global examples. Also, you can explore renewable energy solutions that are more advanced than existing power grids. In addition, brainstorm ideas for electronic recycling that cause worse impacts on health.
Part 3. Best Presentation Software – Presentory, Making Your CSE Presentation Appealing
Despite selecting the best technical paper presentation topics for CSE , making it appealing is also essential. After getting content, people search for PowerPoint templates because presentation templates save time and effort. So, bring a captivating presentation that visually represents data and inspires. In this regard, AI-powered tools are helpful for students and professionals.
Wondershare Presentory is an AI presentation software. It offers AI features to create presentations that capture the viewer’s attention. For presenting the presentation, you can record, create, or livestream videos. It has a user-friendly interface that requires no prior knowledge or skill. Thus, generate a presentation in seconds and deliver it effectively.
Free Download Free Download Try It Online
Key Features
- Create a stunning presentation with polished and innovative templates. Presenters can use templates that suit their topic. Later on, they can change the background of the slides. You can choose meeting rooms or any other color background from the Background options.
- Animate objects and bring life into your presentation. In this tool, there are many slide transitions and animation options. Thus, add emphasis, appear, and exit motion into any object, text, or picture. In this way, key points will be highlighted that you want to keep noticed.
- Surprisingly, this AI tool can generate content by just entering a topic. It will create a structured outline of the presentation. Afterward, the content gets added to slides precisely. Hence, it saves your efforts of hours.
- With built-in AI, you can record or stream your video along with the presentation slides. It allows you to apply makeup and remove blemishes from your face. Also, it enables you to adjust video quality and brightness levels. Moreover, the video can be converted into different layouts.
- This tool contains a cloud service that protects your data. It allows you to collaborate with freedom. You can save your project in the cloud and edit it anytime. Moreover, you can share presentations on any popular platform.
How to Use Presentory and Create CSE Presentation Efficiently
As we have explained, the unique AI features of this AI-powered presentation maker. It contains a user-friendly interface that allows you to generate projects quickly. Read below to get a detailed step-by-step guide on how to use this tool:
Step1 Explore Create with AI Option
After getting Wondershare Presentory on the system, double tap to access its main interface. Then, find "Create With AI" and select this option to explore it.

Step2 Enter the CSE Topic and Get AI Generated Content
From the Presentory AI window, type your topic in the text box named "Type a topic here." Next, hit the "Continue" option after reviewing the outline generated by its AI. Afterward, select a suitable theme from the displayed themes available. Now, press the "Continue" button and wait a few moments.
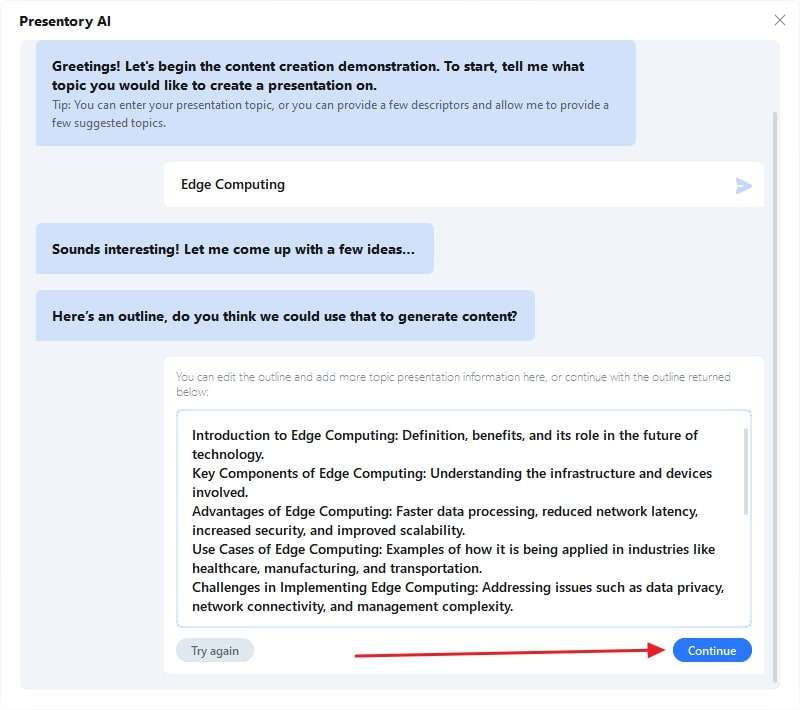
Step3 Insert Animations or Customize as Per Required
With its built-in AI feature, you will get custom-made slides based on your topic and selected theme. To add animations, select the object and tap the "Animation" option at the top-right corner. Select the required animation and set orders of animation in one slide.
From "Resources," choose any sticker or background as needed. After finalizing the presentation, hit the “Project” option in the top bar. There, from the drop-down menu, select “Save Project As”. Then, export the file to your desired location on the device.

Selecting a hot topic for presentation can elevate your growth. CSE students can use topics like computing edge, algorithms, and robotics. Thus, this guide has discussed technical paper presentation topics for CSE . After selecting the topic, getting a tool for impactful presentations is essential.
In this regard, Wondershare Presentory is the most accurate tool for diverse needs. Its AI features can generate content and insert it in attractive templates with one click. Also, you can record videos and change the presentation background. Last but not least, it provides rich resource assets. All in all, it holds all the dynamic features that a presenter looks for.
You May Also Like
- How to Use Slides Changing Remote to Control Presentation from Mobile Devices
Related articles
- IEEE CS Standards
- Career Center
- Subscribe to Newsletter
- IEEE Standards
- For Industry Professionals
- For Students
- Launch a New Career
- Membership FAQ
- Membership FAQs
- Membership Grades
- Special Circumstances
- Discounts & Payments
- Distinguished Contributor Recognition
- Grant Programs
- Find a Local Chapter
- Find a Distinguished Visitor
- Find a Speaker on Early Career Topics
- Technical Communities
- Collabratec (Discussion Forum)
- Start a Chapter
- My Subscriptions
- My Referrals
- Computer Magazine
- ComputingEdge Magazine
- Let us help make your event a success. EXPLORE PLANNING SERVICES
- Events Calendar
- Calls for Papers
- Conference Proceedings
- Conference Highlights
- Top 2024 Conferences
- Conference Sponsorship Options
- Conference Planning Services
- Conference Organizer Resources
- Virtual Conference Guide
- Get a Quote
- CPS Dashboard
- CPS Author FAQ
- CPS Organizer FAQ
- Find the latest in advanced computing research. VISIT THE DIGITAL LIBRARY
- Open Access
- Tech News Blog
- Author Guidelines
- Reviewer Information
- Guest Editor Information
- Editor Information
- Editor-in-Chief Information
- Volunteer Opportunities
- Video Library
- Member Benefits
- Institutional Library Subscriptions
- Advertising and Sponsorship
- Code of Ethics
- Educational Webinars
- Online Education
- Certifications
- Industry Webinars & Whitepapers
- Research Reports
- Bodies of Knowledge
- CS for Industry Professionals
- Resource Library
- Newsletters
- Women in Computing
- Digital Library Access
- Organize a Conference
- Run a Publication
- Become a Distinguished Speaker
- Participate in Standards Activities
- Peer Review Content
- Author Resources
- Publish Open Access
- Society Leadership
- Boards & Committees
- Local Chapters
- Governance Resources
- Conference Publishing Services
- Chapter Resources
- About the Board of Governors
- Board of Governors Members
- Diversity & Inclusion
- Open Volunteer Opportunities
- Award Recipients
- Student Scholarships & Awards
- Nominate an Election Candidate
- Nominate a Colleague
- Corporate Partnerships
- Conference Sponsorships & Exhibits
- Advertising
- Recruitment
- Publications
- Education & Career
Oral Presentation of Papers at the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR)
Long Beach, California—It is the heart of the CVPR 2019 Conference, bringing record attendance from 68 countries and a record number of paper submissions: The technical program.
With 1,294 research papers accepted from a record pool of 5,160 submissions this year, the authors’ technical presentations offered seemingly endless opportunities to listen and learn.
Only 288 papers were admitted into the so-called “oral sessions,” or presentations. Conference organizers reviewed and rated all papers, and the highest-rated papers were granted an oral presentation.
All 1,294 papers and their authors, however, were allowed to present their work in the conference’s poster sessions, so if a paper wasn’t granted an oral presentation, the authors could present their work on an eight-foot-by-four-foot poster on the exhibition floor or elsewhere in the Long Beach Convention & Entertainment Center.
Indeed, the volume of papers prompted organizers to limit each oral presentation to five minutes, in contrast to a typical limit of 15 minutes or so. Presentations were grouped in threes, for a total of 15 minutes, plus three minutes for questions about any of the three papers as a group. Then it was on to the next group of three.
The fast-paced presentations lasted over three days, with overflow rooms equipped with a big-screen feed from the packed ballrooms where the presentations occurred.
Here is a peek at just a handful of the paper presentations during the weeklong conference. The 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR) is the premier event for technology professionals leading computer vision, machine learning, and artificial intelligence — the sectors behind such innovations as self-driving cars, facial recognition, and social media apps.
Paper Title: “Meta-Learning with Differentiable Convex Optimization”

Of the three venues for the oral sessions, the 1,758-seat Terrace Theater was certainly the grandest, with two balconies.
Attendees nearly filled the grand hall to hear the meta-learning paper by Kwonjoon Lee of University of California, San Diego; Subhransu Maji of Amazon Web Services and University of Massachusetts, Amherst; Avinash Ravichandran of Amazon Web Services; and Stefano Soatto of Amazon Web Services and University of California, Los Angeles.
“RePr: Improved Training of Convolutional Filters”

The view from the top balcony of the Terrace Theater was impressive as the oral presentation of the paper by Aaditya Prakash and James Storer, both of Brandeis University, and Dinei Florencio and Cha Zhang, both of Microsoft Research.
“A well-trained Convolutional Neural Network can easily be pruned without significant loss of performance. This is because of unnecessary overlap in the features captured by the network’s filters. Innovations in network architecture such as skip/dense connections and Inception units have mitigated this problem to some extent, but these improvements come with increased computation and memory requirements at run-time. We attempt to address this problem from another angle – not by changing the network structure but by altering the training method,” they wrote.
“Fast Spatially-Varying Indoor Lighting Estimation”

The conference’s vast size required large ballrooms to hold audiences.
Hundreds of listeners packed into the convention center’s Promenade Ballroom to hear a presentation on “Fast Spatially-Varying Indoor Lighting Estimation” by Kalyan Sunkavalli, Sunil Hadap, and Nathan Carr, all of Adobe Research; and Mathieu Garon and Jean-Francois Lalonde, both of Universite Laval.

“MeshAdv: Adversarial Meshes for Visual Recognition”

“Highly expressive models such as deep neural networks (DNNs) have been widely applied to various applications. However, recent studies show that DNNs are vulnerable to adversarial examples, which are carefully crafted inputs aiming to mislead the predictions,” the researchers wrote.
“High-Quality Face Capture Using Anatomical Muscles”

“FML: Face Model Learning from Videos”

Read more related articles about CVPR:
- How CVPR 2019 Conference—Tech’s Premier Event for Computer Vision — Broke Records on All Fronts. Cite Self-Driving Cars and Your Social Media Apps, says Finance Co-Chair Walter Scheirer
- Poster Sessions Provoke Deep Discussions at the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR)
- Opening Remarks and Awards of the Record-Breaking 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR)
- Industry Exhibitors Take Over Hundreds of Thousands of Square Feet at the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR)
- Tutorials Detail Advances in Robotics, AR/VR, and Self-Driving Cars at the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR)
- Workshops of 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR)

About Michael Martinez
Michael Martinez, the editor of the Computer Society’s Computer.Org website and its social media, has covered technology as well as global events while on the staff at CNN, Tribune Co. (based at the Los Angeles Times), and the Washington Post. He welcomes email feedback, and you can also follow him on LinkedIn .

About Lori Cameron
Lori Cameron is Senior Writer for IEEE Computer Society publications and digital media platforms with over 20 years of technical writing experience. She is a part-time English professor and winner of two 2018 LA Press Club Awards. Contact her at [email protected] . Follow her on LinkedIn.
Recommended by IEEE Computer Society

The Asilomar Microcomputer Workshop: Its Origin Story, and Beyond

How to Convince Your Boss to Send You to a Conference

IEEE Quantum Week: A Vibrant, Diverse, and Valuable Resource for Recruiters

Computer Vision for Disaster Responses

Addressing the Digital Challenges Posed by Extremism and Exploitation

Recap: International Symposium on AI and Robotics

Celebrating the Invention of Electronic Digital Computing

Boost Your Resume with this Computer Game Event — IEEE GameSIG Showcase
Login Required
You have to login to use this feature.
Newest papers see more
Journals & conferences , newest uploads see more, popular keywords , most liked papers see more, science categories , best talks see more, popular searches , most viewed see more, date published , random see more.

Princeton Correspondents on Undergraduate Research
How to Make a Successful Research Presentation
Turning a research paper into a visual presentation is difficult; there are pitfalls, and navigating the path to a brief, informative presentation takes time and practice. As a TA for GEO/WRI 201: Methods in Data Analysis & Scientific Writing this past fall, I saw how this process works from an instructor’s standpoint. I’ve presented my own research before, but helping others present theirs taught me a bit more about the process. Here are some tips I learned that may help you with your next research presentation:
More is more
In general, your presentation will always benefit from more practice, more feedback, and more revision. By practicing in front of friends, you can get comfortable with presenting your work while receiving feedback. It is hard to know how to revise your presentation if you never practice. If you are presenting to a general audience, getting feedback from someone outside of your discipline is crucial. Terms and ideas that seem intuitive to you may be completely foreign to someone else, and your well-crafted presentation could fall flat.
Less is more
Limit the scope of your presentation, the number of slides, and the text on each slide. In my experience, text works well for organizing slides, orienting the audience to key terms, and annotating important figures–not for explaining complex ideas. Having fewer slides is usually better as well. In general, about one slide per minute of presentation is an appropriate budget. Too many slides is usually a sign that your topic is too broad.

Limit the scope of your presentation
Don’t present your paper. Presentations are usually around 10 min long. You will not have time to explain all of the research you did in a semester (or a year!) in such a short span of time. Instead, focus on the highlight(s). Identify a single compelling research question which your work addressed, and craft a succinct but complete narrative around it.
You will not have time to explain all of the research you did. Instead, focus on the highlights. Identify a single compelling research question which your work addressed, and craft a succinct but complete narrative around it.
Craft a compelling research narrative
After identifying the focused research question, walk your audience through your research as if it were a story. Presentations with strong narrative arcs are clear, captivating, and compelling.
- Introduction (exposition — rising action)
Orient the audience and draw them in by demonstrating the relevance and importance of your research story with strong global motive. Provide them with the necessary vocabulary and background knowledge to understand the plot of your story. Introduce the key studies (characters) relevant in your story and build tension and conflict with scholarly and data motive. By the end of your introduction, your audience should clearly understand your research question and be dying to know how you resolve the tension built through motive.
- Methods (rising action)
The methods section should transition smoothly and logically from the introduction. Beware of presenting your methods in a boring, arc-killing, ‘this is what I did.’ Focus on the details that set your story apart from the stories other people have already told. Keep the audience interested by clearly motivating your decisions based on your original research question or the tension built in your introduction.
- Results (climax)
Less is usually more here. Only present results which are clearly related to the focused research question you are presenting. Make sure you explain the results clearly so that your audience understands what your research found. This is the peak of tension in your narrative arc, so don’t undercut it by quickly clicking through to your discussion.
- Discussion (falling action)
By now your audience should be dying for a satisfying resolution. Here is where you contextualize your results and begin resolving the tension between past research. Be thorough. If you have too many conflicts left unresolved, or you don’t have enough time to present all of the resolutions, you probably need to further narrow the scope of your presentation.
- Conclusion (denouement)
Return back to your initial research question and motive, resolving any final conflicts and tying up loose ends. Leave the audience with a clear resolution of your focus research question, and use unresolved tension to set up potential sequels (i.e. further research).
Use your medium to enhance the narrative
Visual presentations should be dominated by clear, intentional graphics. Subtle animation in key moments (usually during the results or discussion) can add drama to the narrative arc and make conflict resolutions more satisfying. You are narrating a story written in images, videos, cartoons, and graphs. While your paper is mostly text, with graphics to highlight crucial points, your slides should be the opposite. Adapting to the new medium may require you to create or acquire far more graphics than you included in your paper, but it is necessary to create an engaging presentation.
The most important thing you can do for your presentation is to practice and revise. Bother your friends, your roommates, TAs–anybody who will sit down and listen to your work. Beyond that, think about presentations you have found compelling and try to incorporate some of those elements into your own. Remember you want your work to be comprehensible; you aren’t creating experts in 10 minutes. Above all, try to stay passionate about what you did and why. You put the time in, so show your audience that it’s worth it.
For more insight into research presentations, check out these past PCUR posts written by Emma and Ellie .
— Alec Getraer, Natural Sciences Correspondent
Share this:
- Share on Tumblr

- PRO Courses Guides New Tech Help Pro Expert Videos About wikiHow Pro Upgrade Sign In
- EDIT Edit this Article
- EXPLORE Tech Help Pro About Us Random Article Quizzes Request a New Article Community Dashboard This Or That Game Popular Categories Arts and Entertainment Artwork Books Movies Computers and Electronics Computers Phone Skills Technology Hacks Health Men's Health Mental Health Women's Health Relationships Dating Love Relationship Issues Hobbies and Crafts Crafts Drawing Games Education & Communication Communication Skills Personal Development Studying Personal Care and Style Fashion Hair Care Personal Hygiene Youth Personal Care School Stuff Dating All Categories Arts and Entertainment Finance and Business Home and Garden Relationship Quizzes Cars & Other Vehicles Food and Entertaining Personal Care and Style Sports and Fitness Computers and Electronics Health Pets and Animals Travel Education & Communication Hobbies and Crafts Philosophy and Religion Work World Family Life Holidays and Traditions Relationships Youth
- Browse Articles
- Learn Something New
- Quizzes Hot
- This Or That Game New
- Train Your Brain
- Explore More
- Support wikiHow
- About wikiHow
- Log in / Sign up
- Education and Communications
- Presentations
How to Prepare a Paper Presentation
Last Updated: October 4, 2023 Fact Checked
This article was co-authored by Patrick Muñoz . Patrick is an internationally recognized Voice & Speech Coach, focusing on public speaking, vocal power, accent and dialects, accent reduction, voiceover, acting and speech therapy. He has worked with clients such as Penelope Cruz, Eva Longoria, and Roselyn Sanchez. He was voted LA's Favorite Voice and Dialect Coach by BACKSTAGE, is the voice and speech coach for Disney and Turner Classic Movies, and is a member of Voice and Speech Trainers Association. There are 9 references cited in this article, which can be found at the bottom of the page. This article has been fact-checked, ensuring the accuracy of any cited facts and confirming the authority of its sources. This article has been viewed 362,602 times.
A paper is bad enough, but presentations are even more nerve-wracking. You've got the writing down, but how do you turn it into a dynamic, informative, enjoyable presentation? Why, here's how!
Guidelines and Audience

- Know how long the speech must be.
- Know how many points you're required to cover.
- Know if you must include sources or visuals.

- If you're presenting to people you know, it'll be easy to know what to break down and what to gloss over. But if you're presenting to unknown stockholders or faculty, for instance, you need to know about them and their knowledge levels, too. You may have to break your paper down into its most basic concepts. Find out what you can about their backgrounds.

- Does the facility have a computer and projector screen?
- Is there a working WiFi connection?
- Is there a microphone? A podium?
- Is there someone who can assist you in working the equipment before your presentation?
Script and Visuals

- Only have one point per notecard -- that way you won't end up searching the notecard for your information. And don't forget to number the cards in case you get mixed up! And the points on your cards shouldn't match your paper; instead of regurgitating information, discuss why the key points of your paper are important or the different points of view on this topic within the field.

- As you go through this outline, remove any jargon if it may not be understood.

- If you won't have access to the proper technology, print visual aids on poster board or foam-core board.
- If using presentation software, use words sparingly, but enough to get your point across. Think in phrases (and pictures!), not sentences. Acronyms and abbreviations are okay on the screen, but when you talk, address them fully. And remember to use large fonts -- not everyone's vision is fantastic. [7] X Research source

- It's okay to be a bit repetitive. Emphasizing important ideas will enhance comprehension and recall. When you've gone full circle, cycle back to a previous point to lead your audience to the right conclusion.
- Minimize the unnecessary details (the procedure you had to go through, etc.) when highlighting the main ideas you want to relay. You don't want to overload your audience with fluff, forcing them to miss the important stuff.
- Show enthusiasm! A very boring topic can be made interesting if there is passion behind it.
Practice, Practice, and More Practice

- If you can grab a friend who you think has a similar knowledge level to your audience, all the better. They'll help you see what points are foggier to minds with less expertise on the topic.

- It'll also help you with volume. Some people get rather timid when in the spotlight. You may not be aware that you're not loud enough!

- Do the same with your conclusion. Thank everyone for their time and open the floor for any questions, if allowed.
- Make eye contact with people in the audience to help build your connection with them.
What Is The Best Way To Start a Presentation?
Community Q&A
- Most people get nervous while public speaking. [10] X Research source You are not alone. [11] X Trustworthy Source Mayo Clinic Educational website from one of the world's leading hospitals Go to source Thanks Helpful 0 Not Helpful 1
- Visual aids not only help the audience, but they can help jog your memory if you forget where you are in your presentation. Thanks Helpful 0 Not Helpful 0
- Rehearse in front of a mirror before your presentation. Thanks Helpful 0 Not Helpful 0

- Answer questions only if it is related to your presentation. Keep these to the end of your talk. Thanks Helpful 76 Not Helpful 14
You Might Also Like

- ↑ https://theihs.org/blog/prepare-for-a-paper-presentation-at-an-academic-conference/
- ↑ https://writingcenter.unc.edu/conference-papers/
- ↑ https://www.ncsl.org/legislators-staff/legislative-staff/legislative-staff-coordinating-committee/tips-for-making-effective-powerpoint-presentations.aspx
- ↑ https://www.youtube.com/watch?v=4qZMPW5g-v8
- ↑ https://twp.duke.edu/sites/twp.duke.edu/files/file-attachments/paper-to-talk.original.pdf
- ↑ http://www.cs.swarthmore.edu/~newhall/presentation.html
- ↑ https://www.forbes.com/sites/georgebradt/2014/09/10/big-presentation-dont-do-it-have-a-conversation-instead/#6d56a3f23c4b
- ↑ https://www.psychologytoday.com/us/blog/smashing-the-brainblocks/201711/why-are-we-scared-public-speaking
- ↑ https://www.mayoclinic.org/diseases-conditions/specific-phobias/expert-answers/fear-of-public-speaking/faq-20058416
About This Article

To prepare a paper presentation, create an outline of your content, then write your script on note cards or slides using software like PowerPoint. Be sure to stick to one main point per card or slide! Next, design visual aids like graphics, charts, and bullet points to illustrate your content and help the audience follow along. Then, practice giving your presentation in front of friends and family until you feel ready to do it in class! For tips on creating an outline and organizing your information, read on! Did this summary help you? Yes No
- Send fan mail to authors
Reader Success Stories
Vignesh Sanjeevi
Mar 8, 2016
Did this article help you?
Pulicheri Gunasri
Mahesh Prajapati
Sep 14, 2017
Geraldine Jean Michel
Oct 25, 2016

Featured Articles

Trending Articles

Watch Articles

- Terms of Use
- Privacy Policy
- Do Not Sell or Share My Info
- Not Selling Info
wikiHow Tech Help Pro:
Develop the tech skills you need for work and life

Paper Presentation Topics for CSE
Students of Computer Science Engineering must present papers when undertaking this discipline. Computer Science essentially deals with scientific study of computers, its uses in computation and data processing, advanced algorithmic properties, systems control, artificial intelligence etc. The students enrolled for computer science engineering learn programming, design and analysis of theories relating to computers and different application-based software.
- Artificial Intelligence in Machine refers to the intelligence of machines and the branch of computer science that aims to create it
- Aspect-oriented programming (AOP) is a programming paradigm in which secondary or supporting functions are isolated from the main program’s business logic
- ATM networks refer to a computerized telecommunications device that provides the clients of a financial institution with access to financial transactions in a public space without the need for a cashier, human clerk or bank teller.
- Augmented Reality: refers to a direct or indirect view of a physical real-world environment whose elements are merged with virtual computer-generated imagery – creating a mixed reality.
- Authentication and Key Agreement (AKA) refers to a security protocol used in 3G networks.
- Automatic number plate recognition
- Autonomic Computing
- Auto-pilots
- Backup and Recovery planning
- Cluster computing
- Computational Intelligence and Linguistics
- Computational neuroscience
- Content Management Systems
- Co-operative LINUX
- Cross Platform Component Object Model
- Data Mining and Data Warehousing
- Data Mining concepts & Models
- Data over Cable System (DOCSIS)
- Data Warehouse
- Embedded Configurable Operating system
- Embedded Linux
- Software model checking
- Software Testing & Quality Assurance
- Split Range Synchronization
- Stealth Virus
- Embedded systems and vlsi an architectural approach to reduce leakage energy in memory
- Embedded web server for remote access
- MANET – The Art of Networking without a Network
- Media gateways
- Detection of Reviews using Sentiment analysis: deals with finding a positive review from thousands of reviews
- Mesh Based Geometric data processing
- Micro chip production using extreme UV lithography
- Micro Total analysis systems
- Microcontroller Based Automation
- Microcontroller Based Power Theft Identification
- Digital Jewelry: Digital jewelry can best be defined as wireless, wearable computers that allow you to communicate by ways of e-mail, voicemail, and voice communication.
- Database Migration
- Earth Simulator- Fastest Supercomputer
- Elliptical Curve Cryptography(ECC)
- Multimedia Broadcasting via Satellite
- New Dimension of Data Security using Neural Networks
- Night Vision Technology
- Nonvolatile Flash Memory
- 5 Pen PC Technology is a gadget package including five functions: a pen-style cellular phone with a handwriting data input function, virtual keyboard, a very small projector, camera scanner, and personal ID key with cashless pass function.
- Object oriented technologies
- Online software Distribution
- Static Random Access Memory refers to a type of semiconductor memory that uses bistable latching circuitry (Flip-flop) to store each bit.
- Multimedia-oriented web based instructional system
- Multiple clients communication
- Multiple Domain Orientation
- Wireless Advanced Flight Systems Aircraft Monitoring System
- Vehicle Speed Sensing and Smoke Detecting System
- Time Complexity: In computer science, the time complexity of an algorithm quantifies the amount of time taken by an algorithm to run as a function of the size of the input to the problem.
- Intelligent Fire Sprinkler System
- Search Engine Optimization
- Cyber Crime refers to anything done in the cyber space with a criminal intent.
- Search for extra terrestrial intelligence using satellite communication
- Secure Computing
- The Generic Access Network or GAN refers to a wireless communication system were the mobile phone sets functions seamlessly between WANs or Wide Area Networks and LANs or Local Area Networks. With this technology, the cell phone subscriber is able to communicate by data, voice and multimedia.
- Secure Socket Layer (SSL)
- Web Mining: Web mining is the use of data mining techniques to automatically extract knowledge from Web content, structure and services.
- Optical Disc Data Security
- Optical networking
- Personal Mass Media Blogging, Syndication, Podcasting, and Vidcasting
- Personal Satellite assistant Systems
- Pervasive computing
- Radio-frequency identification (RFID) is a technology that uses communication via radio waves to exchange data between a reader and an electronic tag attached to an object, for the purpose of identification and tracking.
- Secured web portal for online shopping
- Wireless integrated network sensors provide a new monitoring and control capability for transportation, manufacturing, health care, environmental monitoring and safety and security.
- Palm Vein Technology: An individual’s palm vein image is converted by algorithms into data points, which is then compressed, encrypted, and stored by the software and registered along with the other details in his profile as a reference for future comparison.
- Brain chips: Brain chips are made with a view to enhance the memory of human beings, to help paralyzed patients, and are also intended to serve military purposes.
- VoIP in mobile phones
- Mobile Adhoc Network
- Network Security
- CDMA & Blue Tooth Technology
- Cloud Computing: Cloud computing promises to change the way people make use of computing resources. Using the Internet as the backbone, cloud computing claims to provide computing as a “utility” to end users “as and when needed” basis.
- Mobile Number Portability requires that mobile telephone customers can keep their telephone number-including the prefix-when switching from one provider of mobile telecommunications services to another.
- 5G Wireless Systems is a name used in some research papers and projects to denote the next major phase of mobile telecommunications standards beyond the upcoming 4G standards.
- Airborne Internet will not be totally wireless; but will contain the ground-based components to any type of airborne Internet network. This means that consumers will have to install an antenna on their home or business in order to receive signals from the network hub overhead.
- Google Chrome OS is a Linux operating system designed by Google to work exclusively with web applications. It is intended to focus on Web applications while running a fast and simple interface, based off Google’s existing Chrome browser.
- Image processing in computer vision
- Distributed and parallel systems
- Embedded Systems
- Software quality assurance
- Business Intelligence ERP
- Grid Computing
- Artificial Neural Networks
- Advanced Databases
- Image processing and applications
- Mobile Networking
- Natural Language Processor
- Motion Extraction Techniques Based Identifying the Level of Perception Power from Video

- Publication Recognition
How to Make a PowerPoint Presentation of Your Research Paper
- 4 minute read
- 122.6K views
Table of Contents
A research paper presentation is often used at conferences and in other settings where you have an opportunity to share your research, and get feedback from your colleagues. Although it may seem as simple as summarizing your research and sharing your knowledge, successful research paper PowerPoint presentation examples show us that there’s a little bit more than that involved.
In this article, we’ll highlight how to make a PowerPoint presentation from a research paper, and what to include (as well as what NOT to include). We’ll also touch on how to present a research paper at a conference.
Purpose of a Research Paper Presentation
The purpose of presenting your paper at a conference or forum is different from the purpose of conducting your research and writing up your paper. In this setting, you want to highlight your work instead of including every detail of your research. Likewise, a presentation is an excellent opportunity to get direct feedback from your colleagues in the field. But, perhaps the main reason for presenting your research is to spark interest in your work, and entice the audience to read your research paper.
So, yes, your presentation should summarize your work, but it needs to do so in a way that encourages your audience to seek out your work, and share their interest in your work with others. It’s not enough just to present your research dryly, to get information out there. More important is to encourage engagement with you, your research, and your work.
Tips for Creating Your Research Paper Presentation
In addition to basic PowerPoint presentation recommendations, which we’ll cover later in this article, think about the following when you’re putting together your research paper presentation:
- Know your audience : First and foremost, who are you presenting to? Students? Experts in your field? Potential funders? Non-experts? The truth is that your audience will probably have a bit of a mix of all of the above. So, make sure you keep that in mind as you prepare your presentation.
Know more about: Discover the Target Audience .
- Your audience is human : In other words, they may be tired, they might be wondering why they’re there, and they will, at some point, be tuning out. So, take steps to help them stay interested in your presentation. You can do that by utilizing effective visuals, summarize your conclusions early, and keep your research easy to understand.
- Running outline : It’s not IF your audience will drift off, or get lost…it’s WHEN. Keep a running outline, either within the presentation or via a handout. Use visual and verbal clues to highlight where you are in the presentation.
- Where does your research fit in? You should know of work related to your research, but you don’t have to cite every example. In addition, keep references in your presentation to the end, or in the handout. Your audience is there to hear about your work.
- Plan B : Anticipate possible questions for your presentation, and prepare slides that answer those specific questions in more detail, but have them at the END of your presentation. You can then jump to them, IF needed.
What Makes a PowerPoint Presentation Effective?
You’ve probably attended a presentation where the presenter reads off of their PowerPoint outline, word for word. Or where the presentation is busy, disorganized, or includes too much information. Here are some simple tips for creating an effective PowerPoint Presentation.
- Less is more: You want to give enough information to make your audience want to read your paper. So include details, but not too many, and avoid too many formulas and technical jargon.
- Clean and professional : Avoid excessive colors, distracting backgrounds, font changes, animations, and too many words. Instead of whole paragraphs, bullet points with just a few words to summarize and highlight are best.
- Know your real-estate : Each slide has a limited amount of space. Use it wisely. Typically one, no more than two points per slide. Balance each slide visually. Utilize illustrations when needed; not extraneously.
- Keep things visual : Remember, a PowerPoint presentation is a powerful tool to present things visually. Use visual graphs over tables and scientific illustrations over long text. Keep your visuals clean and professional, just like any text you include in your presentation.
Know more about our Scientific Illustrations Services .
Another key to an effective presentation is to practice, practice, and then practice some more. When you’re done with your PowerPoint, go through it with friends and colleagues to see if you need to add (or delete excessive) information. Double and triple check for typos and errors. Know the presentation inside and out, so when you’re in front of your audience, you’ll feel confident and comfortable.
How to Present a Research Paper
If your PowerPoint presentation is solid, and you’ve practiced your presentation, that’s half the battle. Follow the basic advice to keep your audience engaged and interested by making eye contact, encouraging questions, and presenting your information with enthusiasm.
We encourage you to read our articles on how to present a scientific journal article and tips on giving good scientific presentations .
Language Editing Plus
Improve the flow and writing of your research paper with Language Editing Plus. This service includes unlimited editing, manuscript formatting for the journal of your choice, reference check and even a customized cover letter. Learn more here , and get started today!

- Manuscript Preparation
Know How to Structure Your PhD Thesis

- Research Process
Systematic Literature Review or Literature Review?
You may also like.

What is a Good H-index?

What is a Corresponding Author?

How to Submit a Paper for Publication in a Journal
Input your search keywords and press Enter.

700+ Seminar Topics for CSE (Computer Science) with ppt (2024)
Seminar Topics for Computer Science (CSE) with ppt and report (2024) : As technology is emerging day by day. new technologies are coming quickly. And Seminar topics for Computer Science are becoming must find for every student. There are lots of students in Computer Science and Engineering who need quick seminar topics for CSE with ppt and report.
Table of Contents
We understand the burden students are facing today. So we have made a huge collection of Seminar Topics for CSE with ppt and report.
I hope you will save a lot of time with these Seminar Topics for CSE with ppt.
Seminar Topics for Computer Science with ppt and report (2024)
Technical seminar topics for cse with abstract.
3D Printing
3D Printing is the process to develop a 3D printed object with the help of additive processes. Here, there are three-dimensional objects created by a 3D printer using depositing materials as per the digital model available on the system.
4G Technology
4G Technology can be defined as the fourth generation communication system that let users use broadband type speed without any need for Wi-Fi. It is simply called an advanced level radio system that makes the system efficient and quicker. Over the years, it has become an important part of people’s lives globally.
5 Pen PC Technology
5 Pen PC Technology is simply a cluster of gadget that comes with a great sort of features. It includes a virtual keyboard, projector, personal ID key, a pen-shaped mobile phone, and a camera scanner. Using this technology, an crystal clear digital copy of handwritten details can be created.
Android is an operating system created mainly for smartphone and tablets. It is a brilliant technology that allows the users to perform a variety of functions like using GPS for checking traffic areas, etc. Android is the mastermind behind everything ranging from top tablets to 5G phones.
AppleTalk is a networking protocol used in Mac computer systems and devices for making communication. It was originally introduced in 1984 by Apple and get replaced by TCP/IP in 2009 with the release of macOS X v10.6.
Blackberry Technology
Blackberry Technology is an integrated e-mail system provided by the Blackberry company in their handheld devices. Here, there is a unique PIN provided to every phone for identifying the device. This technology can even get accessed in an offline area without any need for wireless service.
Bluejacking
Bluejacking is a technique used by hackers to send messages to a different user with the help of Bluetooth connection. The most common use of this technology is sending unwanted images, text messages or sounds to other Bluetooth equipment in the network range.
Blue-ray Disc
Blu-Ray is an high-definition disc format that let the users see images with extreme level depth, detail, and color. It was released in 2006 as a successor to DVD for improving the experience of the users. This type of discs streams data at 36 megabits per second that is much fast than a DVD.
Cloud Computing
Cloud computing is an advanced method for delivering resources by utilizing the internet. This technology has made it possible to access their resources by saving them to a remote database. It eliminates the burden to store files on an external device.
CAD/CAM is well-known software whose main motive is to simply the design and machining process. It is simply collaboration between computers and machines that make the job of the designers as well as manufacturers easier. It is created after decades of research and testing process.
Cryptography
Cryptography is simply a technique for transforming the basic text into unintelligible ones and vice-versa. This amazing process not only gives protection to the data from online theft but also utilized for the user authentication process. It is used commonly in banking and e-commerce industry in various countries globally.
CORBA (Common Object Request Broker Architecture) is a special architecture whose main job is explaining a unique mechanism for better distribution of objects over a certain network. It let them make communication with each other without any platform and language boundary. This specification created by Object Management Group.
Geographic Information System
GIS fully abbreviated as Geographic Information System is an approach that collects, operate, and analyze data in the framework. There are many types of data integrated by this system along with the spatial location. Apart from that, there is lots of information that further visualized with the help of maps and 3D scenes.
Cyber Crime
Cyber crime is a crime form where the computer is utilized as a weapon. It includes things like spamming, hacking, phishing, etc. On top of that, computers are used for stealing personal data of individuals in these types of crimes. Despite the advancement in technology, the frequency of cyber crimes is increasing every year.
Computer Forensics
Computer Forensics is a technique that involve investigation and analysis processes for collecting and saving important pieces of evidence from certain computing equipment. The main use of these data is to present a strong case in the court of law. This process is performed by Forensic Computer Analysts.
Data Warehousing
Data Warehousing is a technique for gathering and controlling data from a great sort of resources with a motive to give useful insights on the business. This technology is used for connecting and analyzing business data so that it gets available to the businesses within a short time.
Database Management System (DBMS)
Database Management System is a special application package whose main motive is defining, manipulating, and controlling data. Due to this process, the developers no longer need to frame programs to maintain data. There are many fourth-generation query languages available on the internet for better interaction in a database.
Direct Memory Access (DMA )
Direct Memory Access is a computing technique used for the transfer of data from RAM in a computer to a different area in the system without CPU processing. In simple words, its main duty is to transfer or get data to or from main memory so that memory operations become faster.
Digital Watermarking
Digital Watermarking is an extensive technique for embedding data into different types of digital forms. It includes audio, video, images, and other similar objects. The majority of digital devices can easily read and detect digital watermarks by validating the original content.
Domain Name System (DNS)
The Domain Name System (DNS) can simply be called phonebook that comes with the information of domain names location is stored for further translation into IP addresses. In simple words, it translates the domain names into IP addresses allowing browsers to load resources on the internet.
Distributed Systems
A distributed system can be called a cluster of computer systems that work in collaboration with each other to look like as a single entity to the end-user. All the computers in the system are connected through a distribution middleware. The main purpose of this system is sharing various resources to the users with a single network.
Nanoparticles
A nanoparticle is a material used for making computer hardware components with a motive to boost the density of solid-state memory. The complete process is performed by followed a process known with the name of nanotechnology. It let the memory consume low power along with reducing chances of failure.
SCADA is a computer technology used for collecting and checking real-time data. It is fully abbreviated as Supervisory Control and Data Acquisition. The main purpose of this application can be founded in the telecommunications, energy, gas refining, and transportation industry.
LAN WAN MAN
LAN (Local Area Network) is a cluster of network devices that are connected with each other in the same building. MAN (Metropolitan Area Network) performs the same job but covers a large area than LAN like a city or town. WAN (Wide Area Network) covers a bigger area than both LAN and MAN.
A black hole is a fascinating object that is located in outer space. They have a very dense nature and a pretty solid gravitational attraction that even light can’t grasp after coming closer to them. Its existence was predicted first by Albert Einstein in 1916.
Distributed denial-of-service attack (DDoS)
Distributed Denial of Service (DDoS) is a DOS attack that includes a variety of compromised systems. It is often related to the Trojan which is a common form of malware. It includes attackers who transmit data to enjoy vulnerabilities harming the business systems.
E-ball Technology
E-Ball is a sphere-shaped computer system that comes with all features of a traditional computer but has a very smaller size. It even comes with a large screen display along with mouse and keyboard. It is designed in such a way that portability gets a great boost.
Enterprise Resource Planning (ERP)
Enterprise Resource Planning is a business modular software that created for integration of major functional areas in the business processes of the company in a unified area. It comes with core software components that are known as modules targeting major areas in businesses that include production, finance, accounting, and many more.
Extreme Programming (EP)
Extreme Programming (XP) is a software development process whose main mission is creating top-quality software matching needs of clients. It is pretty useful where there are software requirements that change on a dynamic basis. Also, this methodology is used in areas where risks result from fixed time projects
Biometric Security System
Biometric Security is a well-known security system that mainly utilized for authenticating and giving access to the company for verification of a person’s characteristics instantly. It is one of the most powerful techniques used for identity verification in various countries globally.
Common Gateway Interface (CGI)
The Common Gateway Interface (CGI) is a detailed specification that shows the way a program interact with an HTTP server. It works as a middleware between external databases and WWW servers. There are particular information and formatting processes performed by CGI software for WWW servers.
Carbon Nano Technology
The carbon nanotechnology is a process to control atom assembly of molecules at certain dimensions. The main material used for this process is Carbon nanobeads.
Middleware Technologies
The middleware technologies are an application that used making a connection between network requests created by a client for back-end data requested by them. It is a very common software used in the software world in both complexes as well as existing programs.
Invisibility Cloaks
Invisibility Cloaks also known as a clocking device is a method for steering light waves near a material to make it look invisible. There is a great role played by the viewer’s eyes and the instrument used on the level of visibility.
Computer Peripheral
A computer peripheral is a device whose main job is adding information and instructions in the system for storing and then transferring the process data to the user or a device that comes under the system’s administration. Some common examples of a computer peripheral are a printer, scanner, mouse, and keyboard.
Mobile Number Portability (MNP)
Mobile Number Portability (MNP) is an advanced level technology using which the mobile phone subscribers can change their cellular operator without changing their number. It was launched in Singapore about two decades ago, but since then expanded to almost every country across the globe. The complete process to change operator is very customer-friendly and easier.
HTML fully abbreviated as Hypertext Markup Language is a computer language that is mainly used for creating paragraphs, headings, links, blockquotes, and sections in a web page or applications. However, it isn’t a programming language and doesn’t come with the desired features for developing dynamic functionality.
Technical Seminar Topics for CSE
- IP Spoofing
- Mobile Phone Cloning
- Bluetooth Technology
- Mobile Computing
- Pill Camera
- Human Computer Interface
- Software Testing
- Data Mining
- Artificial Neural Network (ANN)
- Wireless Sensor Networks (WSN)
- Wireless Mesh Network
- Digital Light Processing
- Distributed Computing
- Night Vision Technology
- Wireless Application Protocol
- 4G Wireless System
- Artificial Eye
- Asynchronous Chips
- Graphics Processing Unit (GPU)
- Wireless Communication
- Agent Oriented Programming
- Autonomic Computing
- GSM (Global System for Mobile Communications)
- Interferometric Modulator (IMOD)
- Microsoft Surface
- Cryptography and Network Security
- 5G Technology
- FERROELECTRIC RAM (FRAM)
- Object Oriented Programming (OOP)
- Network Topology
- Project Loon
- Storage Area Network (SAN)
- Hybridoma Technology
- Ribonucleic Acid (RNA)
- Cryptocurrency
- Handheld Computers
- Specialized Structured Svms In Computer Vision
- Intel Centrino Mobile Technology
- Digital Audio Broadcasting
- Screenless Display
- Cloud Storage
- IP Telephony
- Microprocessor and Microcontrollers
- Strata Flash Memory
- Gaming Consoles
- The Qnx Real-Time Operating System
- High Performance DSP Architectures
- Tamper Resistance
- MiniDisc system
- XBOX 360 System
- Single Photo Emission Computerized Tomography (SPECT)
- Tactile Interfaces For Small Touch Screen
- Cooperative Linux
- Breaking the Memory Wall in MonetDB
- Synchronous Optical Networking
- Virtual Keyboard Typing
- Optical Networking and Dense Wavelength Division Multiplexing
- Driving Optical Network Evolution
- Low Energy Efficient Wireless Communication Network Design
- Hyper-Threading technology
- Money Pad The Future Wallet
- Remote Method Invocation (RMI)
- Goal-line technology
- Security And Privacy In Social Networks
- Yii Framework
- Digital Preservation
- Optical Storage Technology
- Nvidia Tesla Personal Supercomputer
- Dynamic Cache Management Technique
- Real-Time Task Scheduling
- Session Initiation Protocol (SIP)
- Conditional Access System
- Project Oxygen
- Big Data To Avoid Weather Related Flight Delays
- Operating Systems with Asynchronous Chips
- Predictive Analysis
- Sandbox (computer security)
- Network Address Translation
- Biometrics Based Authentication
Also See: 105+ Technical IEEE Seminar Topics for CSE
Best Seminar Topics for CSE
- Google Chrome OS
- Google Glass
- Intrusion Detection Systems (IDS)
- Jini Technology
- LAMP Technology
- Mind Reading
- Meta Search Engine
- Nanotechnology
- Network Security
- Operating System
- Restful Web Services
- SDLC (Software Development life cycle)
- Sixth Sense Technology
- Software Reuse
- Service Oriented Architecture (SOA)
- Steganography
- Search Engine Optimization(SEO)
- Tidal Energy
- UNIX Operating System
- Virtual Private Network (VP N)
- Voice over Internet Protocol (VoIP)
- Wearable Computing
- Holographic Memory
- Data Storage On Fingernail
- Green Computing
- Universal Serial Bus (USB)
- Computer Networks
- Agile Methodology
- Parts of a Computer
- Human Area Network Technology
- Smart Dustbins for Smart Cities
- Open Graphics Library (Open Gl)
- Elastic Quotas
- Java Server Pages Standard Tag Library (Jstl)
- Mobile Computing Framework
- Zenoss Core
- Smart Pixel Arrays
- Local Multipoint Distribution Service
- Nano Computing
- Quantum Cryptography
- Anonymous Communication
- NFC and Future
- Cluster Computing
- Fog Computing
- Intel Core I9 Processor
- Python Libraries for Data Science
- Google Project Loon
- 64-Bit Computing
- Holographic Versatile Disc (Hvd)
- Virtual Instrumentation
- 3G-vs-WiFi Interferometric Modulator (IMOD)
- Compositional Adaptation
- Wireless Networked Digital Devices
- Helium Drives
- Param 10000
- Palm Operating System
- Meteor Burst Communication
- Cyberterrorism
- Location-Aware Computing
- Programming Using Mono Software
- Utility Fog
- Terrestrial Trunked Radio
- Blockchain Technology
- Exterminator
- Internet Telephony Policy in INDIA
- Voice Portals
- The Callpaper Concept
- Google cloud computing (GCP)
- Web Scraping
- Edge Computing
- Compact peripheral component interconnect
- Health Technology
- Smart Card-Based Prepaid Electricity System
- Phase Change Memory – PCM
- Biometrics in SECURE e-transaction
- Wireless Chargers (Inductive charging)
- Bluetooth V2.1
- Virtual Surgery
Also See: 200+ Paper Presentation Topics For CSE
Seminar Topics for BCA, MSC (Computer Science) and M-Tech
- Genetic Engineering
- Grid Computing
- Optical Coherence Tomography
- Google Wave
- Wireless Fidelity(WiFi)
- Online Voting System
- Digital Jewellery
- Random Access Memory (RAM)
- Quantum Computing
- Digital Cinema
- Polymer Memory
- Rover Technology
- E-Paper Technology
- Image Processing
- Online/Internet Marketing
- Google App Engine
- Computer Virus
- Virus and Anti Viruses
- Artificial Intelligence (AI)
- Gi-Fi Technology
- Mobile Jammer
- X-MAX Technology
- Space Mouse
- Diamond Chip
- Linux Operating Systems
- Web Services on Mobile Platform
- Smart Memories
- Client Server Architecture
- Biometric Authentication Technology
- Smart Fabrics
- 3D Internet
- Bio-metrics
- Dual Core Processor
- Wireless Mark-up Language (WML)
- Transactional Memory
- Visible light communication
- MIND READING COMPUTER
- Eye Tracking Technology
- Confidential Data Storage and Deletion
- USB Microphone
- Pivothead video recording sunglasses
- Slammer Worm
- XML Encryption
- Compute Unified Device Architecture (CUDA)
- Integer Fast Fourier Transform
- Extensible Stylesheet Language
- Free Space Laser Communications
- AC Performance Of Nanoelectronics
- Graphical Password Authentication
- Infinite Dimensional Vector Space
- Near Field Communication(NFC)
- Holographic versetail disc
- Efficeon Processor
- Advanced Driver Assistance System (ADAS)
- Dynamic TCP Connection Elapsing
- Symbian Mobile Operating System
- Artificial Passenger
- RESTful Web Services
- Google Chrome Laptop or Chrome Book
- Focused Web Crawling for E-Learning Content
- Tango technology
- Distributed Interactive Virtual Environment
- Place Reminder
- Encrypted Hard Disks
- Bacterio-Rhodopsin Memory
- Zettabyte file System (ZFS)
- Generic Visual Perception Processor GVPP
- Teleportation
- Digital twin (DT)
- Apache Cassandra
- Microsoft Hololens
- Digital Currency
- Intrusion Tolerance
- Finger Reader
- DNA digital data storage
- Spatial computing
- Linux Kernel 2.6
- Packet Sniffers
- Personal Digital Assistant
- Dynamic TCP Connecting Elapsing
- Hyper Transport Technology
- Multi-Protocol Label Switching (MPLS)
- Natural Language Processing
- Self Defending Networks
- Optical Burst Switching
- Pervasive Computing
Top 10 Seminar topics for CSE
1. Embedded Systems
An embedded system can be called a combination of hardware and software that created for a particular function in a system. Some major locations of an embedded system are household appliances, medical devices, industrial machines, vending machines, mobile devices, and many more.
2. Digital Signature
A digital signature can be called an electronic signature used for guaranteeing the authenticity of a digital document. It is a very useful technique that mainly used for validating authenticity along with integrating certain software, a message or a document.
3. 3D Internet
3D Internet is a next level and advanced method where two powerful technologies- the Internet and 3D graphics are combined. The main purpose of this ultra-level technique is providing realistic 3D graphics with the help of internet. Also known as Virtual Worlds, this interactive and engaging system is used by top organizations like Microsoft, Cisco, IBM, etc.
4. Generations of Computer
The generations of computers are the advancement in technology that has resulted in creating lots of computer equipment over the years. There are five generations of computers that include vacuum tubes, transistors, microprocessors, artificial intelligence, and microprocessors.
5. Blue Eyes Technology
Blue Eyes is an advanced technology that created with a mission to develop computational machines with sensory powers. There is a non-obtrusive sensing technique used by this technology with the use of latest video cameras and microphones. In simple words, it is a machine that understands the requirements of users and what he/she needs to see.
6. History of Computers
Many people believe that computers arrived in the business world in the 19 th century, but the reality is the world computer first used in 1613. The earliest form of computers was the tally stick that was just an old memory used for writing numbers and messages. Since then, there are tons of revolutions that resulted in this business that results in the creation of present-day computers.
7. Nanomaterials
Nanomaterials are the chemical materials that are processed at a minimum dimension, i.e., 1-100nm. They are developed naturally and possess physical as well as chemical properties. These materials are used in a variety of industries are cosmetics, healthcare, and sports among others.
8. Search Engine
A search engine is an online software whose main purpose is searching a database having details regarding the query of the user. There is a complete list of results matching perfectly to the query provided by this software. Google is the best example of a search engine.
9. Firewall
Firewall is security equipment whose main aim is having an eye on the incoming and outgoing traffic in the network. Furthermore, it allows or block data packets according to rules set by the security. In a simple definition, we will say it is created for creating a bridge of internet network & incoming traffic with external sources like the internet.
10. DNA Computing
DNA Computing is a method of computations with the help of biological molecules. This technique doesn’t use basic silicon chips that are quite common in other computation processes. It was invented by American Computer scientist Leonard Adleman in 1994 and displayed the way molecules can be utilized for solving computational issues.
List of Latest Technologies in Computer Science
- Plan 9 Operating System
- FeTRAM: A New Idea to Replace Flash Memory
- Cloud drive
- PON Topologies
- Digital Scent Technology
- Integrated Services Digital Network (ISDN)
- Magnetoresistive Random Access Memory
- Cryptography Technology
- Sense-Response Applications
- Blade Servers
- Revolutions Per Minute, RPM
- Secure Shell
- Ovonic Unified Memory (OUM)
- Facebook Thrift
- Chameleon Chip
- Wiimote Whiteboard
- Scrum Methodology
- liquid cooling system
- Smart Client Application Development Using .Net
- Child Safety Wearable Device
- Tizen Operating System – One OS For Everything
- Surround Systems
- Trustworthy Computing
- Design and Analysis of Algoritms
- Digital Media Broadcasting
- Socks – Protocol (Proxy Server)
- Transient Stability Assessment Using Neural Networks
- Ubiquitous Computing
- Snapdragon Processors
- Datagram Congestion Control Protocol (Dccp)
- Graph Separators
- Facebook Digital Currency – Diem (Libra)
- Design And Implementation Of A Wireless Remote
- A Plan For No Spam
- Quantum machine learning
- Pivot Vector Space Approach in Audio-Video Mixing
- Image Guided Therapy (IGT)
- Distributed Operating Systems
- Orthogonal Frequency Division Multiplplexing
- Idma – The Future Of Wireless Technology
- Shingled Magnetic Recording
- Intel MMX Technology
- Data Scraping
- Itanium Processor
- Social Impacts Of Information Technology
- Digital Video Editing
- Wolfram Alpha
- Brain computer interface
- HelioSeal Technology
- JOOMLA and CMS
- Intelligent Cache System
- Structured Cabling
- Deep Learning
- Ethical Hacking on Hacktivism
- Data-Activated Replication Object Communications (DAROC)
- Strata flash Memory
- Controller Area Network (CAN bus)
- USB Type-C – USB 3.1
You are on Page 1
PAGE 1 || PAGE 2 || PAGE3 || PAGE4
It was all about Seminar Topics for CSE with ppt and report (2024). If you feel any problem regarding these seminar topics for computer science then feel free to ask us in the comment section below. Or if you liked it then please share it with your friends on facebook and other social media websites so that they can also take help from it.
108 Comments Already
please kindly assist me with a model on network for data hiding with encryption and steganographic algorithm for my research
Hello Danjuma, Data Hiding with encryption is called steganography. https://studymafia.org/steganography-seminar-ppt-with-pdf-report/ Go to this links and get it.
i need a ppt and documentation on secure atm by image processing topic plz send meon this email i thankful of u
Its Urgent Sir,I need Pollar pillow PPT and cicret bracelet PPT And Pdf….
hello sir /mam.. i want my seminar on topic hacking.all rhe information regarding this topic n d queries thar can arise from this topic…plz send me on my email id its urgent for me sir plzz
please am writing on gps tracking system i need help
Hello Zion https://studymafia.org/global-positioning-system-seminar-pdf-report-and-ppt/ Go to this link For GPS tracking system.
I need ppt and report for topic- “a watermarking method for digital speech self-recovery”. Please send
I need the report on the topic “low power DDR4 RAM ” can anyone help me with this…. plz share
I need a seminar report and ppt based on the topic, PRISM: fine grained resource aware scheduling for map reduce .
I need seminar report on salesforce technology.#ASAP
It is just an outdated topic Alok, Please move on to another topic, I am sorry but also this will not help you in your engineering.
sir i want ppt and report on DATA CROWDSOURCING
i need ppt report on mona secure multi -owner data sharing for dynamic groups in the cloud
I need the material on the role of social network in the society
I need the material on the impact of internet and associated problems in the society.
I need 5 seminar topics based on CSE that should be very easy and should be understandble to every one easily so plzz send me notification on my gmail…
Sir please send me latest seminar topics for computer science and engineering .I need 3 seminar topics based on cse that should be very easy and easy to understand to every one and also me,please sir send me ppt and documentation please sir don’t ignore me please sir because I give seminar on 09/07/2016 please sir understand, send ppts and documentations to my mail sir.I wait for your mail sir please sir don’t ignore me sir
if you got send for me sir
please i need material for ‘career in computer science for wealth presentation’
Go to this links https://studymafia.org/light-tree-seminar-report-with-ppt-and-pdf/
Thanks for the comment, I will upload your seminar soon here.
Hello Srinivas, here is your seminar of 5G Technology with ppt and pdf report that you requested. https://studymafia.org/5g-technology-ppt-and-pdf-seminar-report-free/ Go to this link
Hello Don, We do not provide any hacking ppt and report, but yes I can provide you Ethical hacking ppt and pdf report https://studymafia.org/ethical-hacking-seminar-ppt-with-pdf-report/ Go to this link
All These are related to computer science,still there are three more pages on it. https://studymafia.org/technical-ieee-seminar-topics-for-cse-with-ppt-and-pdf-report/ https://studymafia.org/latest-seminar-topics-for-cse/ https://studymafia.org/paper-presentation-topics-for-cse/ Go to these links.
Hello Azeez,Your seminar is on the website now 🙂 Have Fun 🙂
Go to these pages, https://studymafia.org/latest-seminar-topics-for-cse/ https://studymafia.org/paper-presentation-topics-for-cse/
Hello Roopa Go to this link https://studymafia.org/technical-ieee-seminar-topics-for-cse-with-ppt-and-pdf-report/
Hey Anuradha, I will provide you very soon, please give me some time.
Nice topic, Will upload soon.
It is live on the website 🙂
Hello Likitha, Please go to this link, it is on our website 🙂 https://studymafia.org/5g-technology-ppt-and-pdf-seminar-report-free/
all These are related to computer science,still there are three more pages on it. https://studymafia.org/technical-ieee-seminar-topics-for-cse-with-ppt-and-pdf-report/ https://studymafia.org/latest-seminar-topics-for-cse/ https://studymafia.org/paper-presentation-topics-for-cse/ – See more at: https://studymafia.org/seminar-topics-for-computer-science-with-ppt-and-report/#sthash.1kXifFkV.dpuf
Hello Doris, Computer science is a part of It world so all these seminars are related to IT World. Thanks
HELLO SIR CAN I GET SEMINAR TOPICS ON WEB DESIGN. THANKS
Hey Mimari, thanks for the comment, we got your request of web designing seminar, we will upload it soon 🙂
go to this link studymafia.org/li-fi-technology-seminar-ppt-with-pdf-report/
studymafia.org/blue-eyes-technology-seminar-ppt-with-pdf-report-2/
please kindly assist me with internet without ip address a new approach in computer architecture
sir i want to market servey report from ppt seminar
Hello Lakhan, I didn’t get your topic really.
Hello Divya Mam, go to this link studymafia.org/artificial-intelligence-ai-seminar-pdf-report-and-ppt/
Hello Sir..Can i have a seminar on google self driving car tech… including something related to cps.
hey can u upload a documentation on Cassandra.
please do i find to teach me how to write a complete program to solve the problem of simoutenous equation i mean the pseudocode the flowchart and a program using FORTRAN
hey can I have ppt and pdf on femtocell
sir !! i need seminar reports and ppts on following two topics, can i get them in urgent? please.. 1.Clouddrops 2.icloud 3.touchless touchscreen atleast reply me
I need seminar reports n ppt on following two topics 1. Augmented reality 2. Head maounted displays
go to this link https://studymafia.org/augmented-reality-seminar-and-ppt-with-pdf-report/
plsssssss provide plant leaf diesease identification system for android
Please provide ppt and report on “web mining algorithm using link analysis”
Please Mr Sumit Thakur i need project materials and software on Security Information System (for national civil defense) asap, please please please
It will be updated soon 🙂
go for google wave https://studymafia.org/google-wave-seminar-ppt-and-pdf-report/ or Search engine optimization https://studymafia.org/seo-seminar-ppt-with-pdf-report/
Thank you Mr.Sumit Thakur. I recently heard about Screenless displays. I think its not the latest one. What do you say?? if you have ppt and report of it mail me..
Hey….i want a ppt on deepweb and dark web urgntly with pdf report
I’ve been following your site for quite some time now and I must confess, you’re doing an amazing job here.
please I need three good project topic and possible materials on computer science.
GO to this link https://studymafia.org/firewall-seminar-report-with-ppt-and-pdf/
go to this link https://studymafia.org/firewall-seminar-report-with-ppt-and-pdf/
Hello Avni, Go to this link https://studymafia.org/computer-networks-seminar-pdf-report-ppt/
I need ppt and report on speed breakers and ditches
Hello Mr.Thakur I wanted ppt on data coloring. could you please provide it?
hello sir, I request a ppt and report for the topic “Millimeter wave wireless communications for IOT cloud supported autonomous vehicles:overview, design and challenges”
please send link to download seminar report and ppt for “understanding smartphone sensor and app data for enhancing security of secret questions”
Sir, pls i need ppt and report of “eye movement based human computer interaction” .its found in this site .. it’s very urgent
Go to this link https://studymafia.org/digital-signature-seminar-and-ppt-with-pdf-report/
Sir I need to Final Year IT Btech project report on website ‘Digital India Village Development’
sir plz provide me report on olap(online analytical processing)
Sir please i need a report for Interactive emotional lighting using physiological signals.
hello !!! please i am computer science student final year HERE is MY PROJECT TOPIC #ORTHOPAEDIC EXPERT SYSTEM i need a little knowledge about it someone help please
We are currently not working on projects.
Hello sir…i am a mca student..pls suggest me latest seminar topic and pls send me the seminar report on “Internet of BioNano things”.Send me on this email
Hello Jyo, I didn’t find anything related to your topic.
Hello Micheal, You seminar will be on our website soon.
Hello Pratyusha, Good topic, will be updated soon.
GO to this link https://studymafia.org/speech-recognition-seminar-ppt-and-pdf-report/
Hello Mam, Here are the links https://studymafia.org/4g-technology-seminar-and-ppt-with-pdf-report/ https://studymafia.org/5g-technology-ppt-and-pdf-seminar-report-free/
Will be updated soon
Sir,I want seminar report and PPT of the topic multi-touch interaction.
Hello sir!Could u please send me a ppt for am image based hair modeling and dynamic simulation method
I seriously need seminar topics for education in computer please I would be glad if my request is granted please send to my mail.
hello please i also need a topic about fog computing, IoT or Mikrotic please help me
hello Final Report for Foreign Students
We invite submissions of high quality and origin reports describing fully developed results or on-going foundational and applied work on the following topics of advanced algorithms in Natural Language Processing: in this topic ( Literature survey of short text similarity.) Reporting requirements: (1) Reports must not less 5 pages and exceed 8 pages, using IEEE two-column template. All papers should be in Adobe portable document format (PDF) format. Authors should submit their paper via electronic submission system. All papers selected for this conference are peer-reviewed and will be published in the regular conference proceedings by the IEEE Computer Society Press. Submissions must not be published or submitted for another conference. The best quality papers presented in the conference will be selected for journal special issues by creating an extended version. (2) No copy of any sentences from published papers. You may get zero score for some detected copy sentence.
please i need seminar paper on fog computing with go comparative study with full report
Hello Sir, Can you please help me out with presentation and report on the topic “Blind Aid Stick:Hurdle Recognition,Simulated Perception,Android Integrated Voice Based Cooperation via GPS Along with Panic Alert System”.
Hello,we have been ask to find research papers for certain topics regarding seminar presentation and then do comparative analysis.so please help with the topic “AI in control systems”.
Is there any topics related to routing. Please suggest me if there are.
hello sir please i need your help on a seminar topic Examination biometric verification case study of WAEC… thanks for understanding
Sir pls I need the ppt and report of review cash receipt generating system; challenges and merit
Hello sir please provide ppt and report on following two topics I get them in urgent please digital library mobile based network monitory system
please sir i need a ppt about modal logic in computer science
introduction of modal logic history of modal logic syntax of modal logic application of modal logic proof of modal logic
i need material on opportunities network and software defined network. please send as soon as possible. thank you sir
Please I need a full report on entrepredemic, please help me with it
I need a ppt on Expert Addmision System with flowchart.
please kindly help me with a proper write up on this seminar topic “I CLOUD”, Thank you for considering me.
Hello All my friends, I am not able to answer each your comment, so please come to our facebook fan page https://www.facebook.com/studymafia1/ where we can discuss your problems and can take new seminar request directly 🙂
sir , i need the ppt on topic:”Securing Mobile Healthcare Data: A Smart Card Based Cancelable Finger-Vein Bio-Cryptosystem” .
which is from ieee access ,and some links of videos to understand it .
plz replay me as soon as possible as im having the seminar with in this weak ,
Sir I need latest IEEE published papers seminar topics on any domain in cse
Sir! I need PPT and Documentation on this below Title. “Securing data with blockchain and Ai” So, please send me sir!
I want ppt and documentation on the topic CLOUD ROBOTICS
Sir could you please give me the PPT and Report for the topic Web Vulnerability Detection ,The Case of Cross-Site Request Forgery could u please help me send me the link where i can find ppt for this topic!!!
Hello Sir,thanks for the good work you’re doing.
Please I need seminar on “Security in Cloud Computing” thank you
U r doing a great work it helps most of the student. Sir I want Air cargo tracking system ppt and synopsis can u plz share the link where we can get ppt .
Thank you for your help, i really appreciate and acknowledge your effort. But am doing my own seminar on “Digital Currency Diffusion Policy in Nigeria” pls help. Thank you
Please I need something on Networking tools and Cable Management
I need ppt on blockchain
I want Q learning based teaching-learning optimization for distributed two stage hybrid flow shop scheduling with fuzzy processing time ppt with report for technical presentation please send me please I need it urgent pls
i need project report and presentation of ONLINE FOOD ORDERING SYSTEM.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
This site uses Akismet to reduce spam. Learn how your comment data is processed .

28 October – 30 October 2024
Herndon, va, usa, the 36 th ieee international conference on tools with artificial intelligence (ictai), dear authors,, ictai 2024 uses a double-blind review process. to facilitate this, please ensure that your names and affiliations do not appear anywhere in the submitted paper., best regards ictai 2024 organizing committee, important dates, paper submission: july 1, 2024 paper notification: august 18, 2024 camera ready: september 16, 2024.
The IEEE International Conference on Tools with Artificial Intelligence (ICTAI) is a leading IEEE-CS annual scientific meeting for three decades. It provides a major international forum where the creation and exchange of ideas related to artificial intelligence are fostered among academia, industry, and government agencies. The conference facilitates the cross-fertilization of these ideas and promotes their transfer into practical tools, for developing intelligent systems and pursuing artificial intelligence applications. The ICTAI encompasses all technical aspects of specifying, developing and evaluating the theoretical underpinnings and applied mechanisms of the AI-based components of computer tools such as algorithms, architectures and languages.
Conference Categories
- Evolutionary computing, Bayesian and Neural Networks
- Decision/Utility Theory and Decision Optimization
- Search, SAT, and CSP
- Description Logic and Ontologies
- AI in Computational Biology, Medicine and Biomedical Applications
- AI in WWW, Communication, Social Networking, Recommender Systems, Games and E-Commerce
- AI in Finance and Risk Management
- AI in Robotics, Computer Vision and Games
- AI in Natural Language Processing
- AI in Software Engineering, Real-Time and Embedded Applications, and Sensor Networks
- AI in Cloud Computing, Data-Intensive Applications and Online/Streaming and Multimedia Systems
- AI in Web Search and Information Retrieval
- AI in Computer Security, Data Privacy, and Information Assurance
- Visual Analytics for Big Data
- Computational Modeling for Big Data
- Large-scale Recommendation and Social Media Systems
- Cloud/Grid/Stream Data Mining for Big Velocity Data
- Semantic-based Big Data Mining
- Healthcare, Traffic, Transportation, Environment, etc.
- Bridging AI Models for Advanced AI.
- Dimension Reduction and Feature Selection computing
- Learning Graphical Models and Complex Networks
- Active, Cost-Sensitive, Semi-Supervised, Multi-Instance, Multi-Label and Mulit-Task Learning
- Transfer/Adaptive, Rational and Structured Learning
- Preference/Ranking, Ensemble, and Reinforcement Learning
- Learn continuous-Incremental Learning
- Knowledge Representation, Reasoning
- Knowledge Extraction, Management and Sharing
- Case-based Reasoning and Knowledge-based Systems
- Cognitive Modelling and Semantic Web
- Decision Guidance and Support Systems
- Optimization-based Recommender Systems
- Group, Distributed, and Collaborative Decisions
- Crowd-sourcing and Collective Intelligence Decision-making
- Strategic, Tactical and Operational-level Decisions
- Decision-making in Social and Mobile Networks
- Uncertainty and Fuzziness Representation and Reasoning
- Approximate/Exact Probabilistic Inference
- Knowledge Discovery and Data Mining for Uncertain
- AI Fairness, Accountability and Transparency
- AI interpretability and explainability
- Ethical and Trustworthy AI
Paper Submission
ICTAI 2024 uses a double-blind review process. To facilitate this, authors should ensure that their names and affiliations do not appear anywhere in the submitted paper.
SUBMISSION should be made through the Easy Chair link: https://easychair.org/conferences/?conf=ictai2024 . The submissions should contain original, high quality, not submitted, or published elsewhere work. Papers should be submitted electronically in PDF format and should conform to IEEE specifications (single-spaced, double-column, 10-point font size, up to 8 pages).
Paper Presentation
Each accepted paper should be presented by one of the authors and accompanied by at least one full registration fee payment, to guarantee publication in the proceedings. All accepted papers will be included in the proceedings of ICTAI 2024 that will be published by the IEEE Computer Society.
Special Issues in IEEE & Int. Journals
Extended versions of selected papers from the conference will be reviewed and published in special issues in various IEEE and Int. Journals.
Best ICTAI Papers Recognition Awards
ICTAI provide several financial awards to the top-5 best student papers and to the ICTAI Best Paper Award.
Contact ICTAI 2024
General chair.
Manolis Koubarakis National & Kapodistrian University of Athens, Greece [email protected]
Program Chair
Jessica Lin George Mason University, VA, USA [email protected]
Financial & Registration Chair
Michail Alexiou Kennesaw State University, GA, USA [email protected]
Oriental Journal of Computer Science and Technology An International research journal of Computer Science and Technology
Paper Presentation on Computer Networks
D.G. Krishnamohan
Academic Consultant, Krishna University, Machilipatnam (India).
The primary purpose of a computer network is to share resources. A computer network is referred to as client/server if (at least) one of the computers is used to "serve" other computers referred to as "clients". Besides the computers, other types of devices can be part of the network. In the early days of networking, there will be once central server that contains the data and all the clients can access this data through a Network Interface Card. Later on Client server architecture came into existence, where still burden is there on the server machine. To avoid the disadvantages in distributed computing was introduced which reduces the burden on the server by providing work sharing capabilities1 . This paper describes how the concept of distributed computing came into existence based on the advantages and disadvantages that raised in earlier networking concepts. The concept of distributed computing speaks that once data is available within the server(s), it should be able to be accessed and processed from any kind of client device like computer, mobile phone, PDA, etc.

Upcoming Paper Presentation Competitions in College Fests, Events in April 2024.
Popular cities, popular states.
- Andhra Pradesh
- Maharashtra
Popular Colleges
- All Colleges
Our approach
- Responsibility
- Infrastructure
- Try Meta AI
RECOMMENDED READS
- 5 Steps to Getting Started with Llama 2
- The Llama Ecosystem: Past, Present, and Future
- Introducing Code Llama, a state-of-the-art large language model for coding
- Meta and Microsoft Introduce the Next Generation of Llama
- Today, we’re introducing Meta Llama 3, the next generation of our state-of-the-art open source large language model.
- Llama 3 models will soon be available on AWS, Databricks, Google Cloud, Hugging Face, Kaggle, IBM WatsonX, Microsoft Azure, NVIDIA NIM, and Snowflake, and with support from hardware platforms offered by AMD, AWS, Dell, Intel, NVIDIA, and Qualcomm.
- We’re dedicated to developing Llama 3 in a responsible way, and we’re offering various resources to help others use it responsibly as well. This includes introducing new trust and safety tools with Llama Guard 2, Code Shield, and CyberSec Eval 2.
- In the coming months, we expect to introduce new capabilities, longer context windows, additional model sizes, and enhanced performance, and we’ll share the Llama 3 research paper.
- Meta AI, built with Llama 3 technology, is now one of the world’s leading AI assistants that can boost your intelligence and lighten your load—helping you learn, get things done, create content, and connect to make the most out of every moment. You can try Meta AI here .
Today, we’re excited to share the first two models of the next generation of Llama, Meta Llama 3, available for broad use. This release features pretrained and instruction-fine-tuned language models with 8B and 70B parameters that can support a broad range of use cases. This next generation of Llama demonstrates state-of-the-art performance on a wide range of industry benchmarks and offers new capabilities, including improved reasoning. We believe these are the best open source models of their class, period. In support of our longstanding open approach, we’re putting Llama 3 in the hands of the community. We want to kickstart the next wave of innovation in AI across the stack—from applications to developer tools to evals to inference optimizations and more. We can’t wait to see what you build and look forward to your feedback.
Our goals for Llama 3
With Llama 3, we set out to build the best open models that are on par with the best proprietary models available today. We wanted to address developer feedback to increase the overall helpfulness of Llama 3 and are doing so while continuing to play a leading role on responsible use and deployment of LLMs. We are embracing the open source ethos of releasing early and often to enable the community to get access to these models while they are still in development. The text-based models we are releasing today are the first in the Llama 3 collection of models. Our goal in the near future is to make Llama 3 multilingual and multimodal, have longer context, and continue to improve overall performance across core LLM capabilities such as reasoning and coding.
State-of-the-art performance
Our new 8B and 70B parameter Llama 3 models are a major leap over Llama 2 and establish a new state-of-the-art for LLM models at those scales. Thanks to improvements in pretraining and post-training, our pretrained and instruction-fine-tuned models are the best models existing today at the 8B and 70B parameter scale. Improvements in our post-training procedures substantially reduced false refusal rates, improved alignment, and increased diversity in model responses. We also saw greatly improved capabilities like reasoning, code generation, and instruction following making Llama 3 more steerable.

*Please see evaluation details for setting and parameters with which these evaluations are calculated.
In the development of Llama 3, we looked at model performance on standard benchmarks and also sought to optimize for performance for real-world scenarios. To this end, we developed a new high-quality human evaluation set. This evaluation set contains 1,800 prompts that cover 12 key use cases: asking for advice, brainstorming, classification, closed question answering, coding, creative writing, extraction, inhabiting a character/persona, open question answering, reasoning, rewriting, and summarization. To prevent accidental overfitting of our models on this evaluation set, even our own modeling teams do not have access to it. The chart below shows aggregated results of our human evaluations across of these categories and prompts against Claude Sonnet, Mistral Medium, and GPT-3.5.

Preference rankings by human annotators based on this evaluation set highlight the strong performance of our 70B instruction-following model compared to competing models of comparable size in real-world scenarios.
Our pretrained model also establishes a new state-of-the-art for LLM models at those scales.

To develop a great language model, we believe it’s important to innovate, scale, and optimize for simplicity. We adopted this design philosophy throughout the Llama 3 project with a focus on four key ingredients: the model architecture, the pretraining data, scaling up pretraining, and instruction fine-tuning.
Model architecture
In line with our design philosophy, we opted for a relatively standard decoder-only transformer architecture in Llama 3. Compared to Llama 2, we made several key improvements. Llama 3 uses a tokenizer with a vocabulary of 128K tokens that encodes language much more efficiently, which leads to substantially improved model performance. To improve the inference efficiency of Llama 3 models, we’ve adopted grouped query attention (GQA) across both the 8B and 70B sizes. We trained the models on sequences of 8,192 tokens, using a mask to ensure self-attention does not cross document boundaries.
Training data
To train the best language model, the curation of a large, high-quality training dataset is paramount. In line with our design principles, we invested heavily in pretraining data. Llama 3 is pretrained on over 15T tokens that were all collected from publicly available sources. Our training dataset is seven times larger than that used for Llama 2, and it includes four times more code. To prepare for upcoming multilingual use cases, over 5% of the Llama 3 pretraining dataset consists of high-quality non-English data that covers over 30 languages. However, we do not expect the same level of performance in these languages as in English.
To ensure Llama 3 is trained on data of the highest quality, we developed a series of data-filtering pipelines. These pipelines include using heuristic filters, NSFW filters, semantic deduplication approaches, and text classifiers to predict data quality. We found that previous generations of Llama are surprisingly good at identifying high-quality data, hence we used Llama 2 to generate the training data for the text-quality classifiers that are powering Llama 3.
We also performed extensive experiments to evaluate the best ways of mixing data from different sources in our final pretraining dataset. These experiments enabled us to select a data mix that ensures that Llama 3 performs well across use cases including trivia questions, STEM, coding, historical knowledge, etc.
Scaling up pretraining
To effectively leverage our pretraining data in Llama 3 models, we put substantial effort into scaling up pretraining. Specifically, we have developed a series of detailed scaling laws for downstream benchmark evaluations. These scaling laws enable us to select an optimal data mix and to make informed decisions on how to best use our training compute. Importantly, scaling laws allow us to predict the performance of our largest models on key tasks (for example, code generation as evaluated on the HumanEval benchmark—see above) before we actually train the models. This helps us ensure strong performance of our final models across a variety of use cases and capabilities.
We made several new observations on scaling behavior during the development of Llama 3. For example, while the Chinchilla-optimal amount of training compute for an 8B parameter model corresponds to ~200B tokens, we found that model performance continues to improve even after the model is trained on two orders of magnitude more data. Both our 8B and 70B parameter models continued to improve log-linearly after we trained them on up to 15T tokens. Larger models can match the performance of these smaller models with less training compute, but smaller models are generally preferred because they are much more efficient during inference.
To train our largest Llama 3 models, we combined three types of parallelization: data parallelization, model parallelization, and pipeline parallelization. Our most efficient implementation achieves a compute utilization of over 400 TFLOPS per GPU when trained on 16K GPUs simultaneously. We performed training runs on two custom-built 24K GPU clusters . To maximize GPU uptime, we developed an advanced new training stack that automates error detection, handling, and maintenance. We also greatly improved our hardware reliability and detection mechanisms for silent data corruption, and we developed new scalable storage systems that reduce overheads of checkpointing and rollback. Those improvements resulted in an overall effective training time of more than 95%. Combined, these improvements increased the efficiency of Llama 3 training by ~three times compared to Llama 2.
Instruction fine-tuning
To fully unlock the potential of our pretrained models in chat use cases, we innovated on our approach to instruction-tuning as well. Our approach to post-training is a combination of supervised fine-tuning (SFT), rejection sampling, proximal policy optimization (PPO), and direct preference optimization (DPO). The quality of the prompts that are used in SFT and the preference rankings that are used in PPO and DPO has an outsized influence on the performance of aligned models. Some of our biggest improvements in model quality came from carefully curating this data and performing multiple rounds of quality assurance on annotations provided by human annotators.
Learning from preference rankings via PPO and DPO also greatly improved the performance of Llama 3 on reasoning and coding tasks. We found that if you ask a model a reasoning question that it struggles to answer, the model will sometimes produce the right reasoning trace: The model knows how to produce the right answer, but it does not know how to select it. Training on preference rankings enables the model to learn how to select it.
Building with Llama 3
Our vision is to enable developers to customize Llama 3 to support relevant use cases and to make it easier to adopt best practices and improve the open ecosystem. With this release, we’re providing new trust and safety tools including updated components with both Llama Guard 2 and Cybersec Eval 2, and the introduction of Code Shield—an inference time guardrail for filtering insecure code produced by LLMs.
We’ve also co-developed Llama 3 with torchtune , the new PyTorch-native library for easily authoring, fine-tuning, and experimenting with LLMs. torchtune provides memory efficient and hackable training recipes written entirely in PyTorch. The library is integrated with popular platforms such as Hugging Face, Weights & Biases, and EleutherAI and even supports Executorch for enabling efficient inference to be run on a wide variety of mobile and edge devices. For everything from prompt engineering to using Llama 3 with LangChain we have a comprehensive getting started guide and takes you from downloading Llama 3 all the way to deployment at scale within your generative AI application.
A system-level approach to responsibility
We have designed Llama 3 models to be maximally helpful while ensuring an industry leading approach to responsibly deploying them. To achieve this, we have adopted a new, system-level approach to the responsible development and deployment of Llama. We envision Llama models as part of a broader system that puts the developer in the driver’s seat. Llama models will serve as a foundational piece of a system that developers design with their unique end goals in mind.

Instruction fine-tuning also plays a major role in ensuring the safety of our models. Our instruction-fine-tuned models have been red-teamed (tested) for safety through internal and external efforts. Our red teaming approach leverages human experts and automation methods to generate adversarial prompts that try to elicit problematic responses. For instance, we apply comprehensive testing to assess risks of misuse related to Chemical, Biological, Cyber Security, and other risk areas. All of these efforts are iterative and used to inform safety fine-tuning of the models being released. You can read more about our efforts in the model card .
Llama Guard models are meant to be a foundation for prompt and response safety and can easily be fine-tuned to create a new taxonomy depending on application needs. As a starting point, the new Llama Guard 2 uses the recently announced MLCommons taxonomy, in an effort to support the emergence of industry standards in this important area. Additionally, CyberSecEval 2 expands on its predecessor by adding measures of an LLM’s propensity to allow for abuse of its code interpreter, offensive cybersecurity capabilities, and susceptibility to prompt injection attacks (learn more in our technical paper ). Finally, we’re introducing Code Shield which adds support for inference-time filtering of insecure code produced by LLMs. This offers mitigation of risks around insecure code suggestions, code interpreter abuse prevention, and secure command execution.
With the speed at which the generative AI space is moving, we believe an open approach is an important way to bring the ecosystem together and mitigate these potential harms. As part of that, we’re updating our Responsible Use Guide (RUG) that provides a comprehensive guide to responsible development with LLMs. As we outlined in the RUG, we recommend that all inputs and outputs be checked and filtered in accordance with content guidelines appropriate to the application. Additionally, many cloud service providers offer content moderation APIs and other tools for responsible deployment, and we encourage developers to also consider using these options.
Deploying Llama 3 at scale
Llama 3 will soon be available on all major platforms including cloud providers, model API providers, and much more. Llama 3 will be everywhere .
Our benchmarks show the tokenizer offers improved token efficiency, yielding up to 15% fewer tokens compared to Llama 2. Also, Group Query Attention (GQA) now has been added to Llama 3 8B as well. As a result, we observed that despite the model having 1B more parameters compared to Llama 2 7B, the improved tokenizer efficiency and GQA contribute to maintaining the inference efficiency on par with Llama 2 7B.
For examples of how to leverage all of these capabilities, check out Llama Recipes which contains all of our open source code that can be leveraged for everything from fine-tuning to deployment to model evaluation.
What’s next for Llama 3?
The Llama 3 8B and 70B models mark the beginning of what we plan to release for Llama 3. And there’s a lot more to come.
Our largest models are over 400B parameters and, while these models are still training, our team is excited about how they’re trending. Over the coming months, we’ll release multiple models with new capabilities including multimodality, the ability to converse in multiple languages, a much longer context window, and stronger overall capabilities. We will also publish a detailed research paper once we are done training Llama 3.
To give you a sneak preview for where these models are today as they continue training, we thought we could share some snapshots of how our largest LLM model is trending. Please note that this data is based on an early checkpoint of Llama 3 that is still training and these capabilities are not supported as part of the models released today.

We’re committed to the continued growth and development of an open AI ecosystem for releasing our models responsibly. We have long believed that openness leads to better, safer products, faster innovation, and a healthier overall market. This is good for Meta, and it is good for society. We’re taking a community-first approach with Llama 3, and starting today, these models are available on the leading cloud, hosting, and hardware platforms with many more to come.
Try Meta Llama 3 today
We’ve integrated our latest models into Meta AI, which we believe is the world’s leading AI assistant. It’s now built with Llama 3 technology and it’s available in more countries across our apps.
You can use Meta AI on Facebook, Instagram, WhatsApp, Messenger, and the web to get things done, learn, create, and connect with the things that matter to you. You can read more about the Meta AI experience here .
Visit the Llama 3 website to download the models and reference the Getting Started Guide for the latest list of all available platforms.
You’ll also soon be able to test multimodal Meta AI on our Ray-Ban Meta smart glasses.
As always, we look forward to seeing all the amazing products and experiences you will build with Meta Llama 3.
Our latest updates delivered to your inbox
Subscribe to our newsletter to keep up with Meta AI news, events, research breakthroughs, and more.
Join us in the pursuit of what’s possible with AI.

Product experiences
Foundational models
Latest news
Meta © 2024

IMAGES
VIDEO
COMMENTS
151+ Computer Presentation Topics [Updated 2024] General / By StatAnalytica / 4th January 2024. For both professionals and fans, keeping up with the most recent developments and trends in the rapidly evolving field of technology is essential. One effective way to share and acquire knowledge is through computer presentations.
April 14, 2024. We bring you the latest Paper Presentation Topics for Computer Science Engineering. Click on the topic name to read in detail. These topics give an idea of what topic to choose and what information needs to be included as part of a technical paper. Technical papers have been written in a standard format.
These updated topics can be used for PowerPoint Paper presentation, Poster Presentation, classroom ppt presentation, seminars, seminars, webinars and conferences. etc. These presentation topics will be beneficial for students of Engineering and management courses such as BE Computer science, B Tech IT, MCA, BCA and MBA.
Encouraging Active Participation: Interesting topics inspire audience involvement, fostering a dynamic environment where questions are asked, discussions arise, and participants actively contribute to the presentation. Enhancing Learning and Retention: Well-chosen topics promote effective learning by making the material memorable.
The latest Technical Paper Presentation Topics include trending topics from emerging Technology like Artificial Intelligence, Machine Learning, 5G Technology, Cybersecurity, and Cloud Computing. It also includes topics from different Engineering streams like Computer Science and Engineering, Electronics Communications and Engineering ...
Department of Computer Sciences University of North Texas mailto:[email protected] April, 2000 Congratulations. You are one of only a few who would bother reading a guide on successful presentation style. Most people don't believe they need to learn how to make a presentation. Stand up, present the data, offer conclusions, and answer questions ...
Read further to know some impactful CSE presentation topics . 1. Artificial Intelligence. The current most advancing area of CSE is Artificial Intelligence. It refers to the ability of computer-based systems to perform human-like functions and is designed to work like human cognition.
paper highlights the important points to an effective presentation; however, there is no substitute for the actual practice or experience of delivering a live presentation. The ideas in this paper are a guideline to help make presentations more memorable and dynamic. The Title The title is the author's introduction of the subject to the reader.
Types of CSE Paper Presentation Topics. If you study computer science and engineering in a college or a university, you most likely face assignments such as presentations in the area of numerical computing, discrete algorithms, modeling and simulation, computational data analysis, big data, cloud computing and machine learning, high-performance computing, etc.
Oral Presentation of Papers at the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR) Long Beach, California—It is the heart of the CVPR 2019 Conference, bringing record attendance from 68 countries and a record number of paper submissions: The technical program. With 1,294 research papers accepted from a record pool ...
Here our presence come to help all the students who are not getting right material for their Paper Presentation. Our motto is to provide Paper Presentation topics for cse (2024) with ppt and report in pdf format so that students can easily get them and understand the concept. General Topics Non Technical Topics. Mechanical Engineering MCA.
Papertalk - the platform where scientists talk about their papers. Sign up for free! An account allows you to add your own talks, write comments and organize talks in different watch lists. This is a non-commercial website. If you have any feedback, please share it here .
Turning a research paper into a visual presentation is difficult; there are pitfalls, and navigating the path to a brief, informative presentation takes time and practice. As a TA for GEO/WRI 201: Methods in Data Analysis & Scientific Writing this past fall, I saw how this process works from an instructor's standpoint. I've presented my own ...
Know if you must include sources or visuals. 2. Know your audience. If you're giving a presentation to your classmates, you probably have a rough idea of their knowledge on the topic. But for virtually every other circumstance, you may be in the dark. Either way, cater your paper to make zero assumptions.
Computer Presentation templates ... It's not just a piece of paper, it's your chance to showcase your skills, experience, and personality. If you want to stand out from the... Business. A4 / Like . Download . Download and open in Google Slides . Download as a PowerPoint file ...
Paper Presentation Topics for CSE Students of Computer Science Engineering must present papers when undertaking this discipline. Computer Science essentially deals with scientific study of computers, its uses in computation and data processing, advanced algorithmic properties, systems control, artificial intelligence etc.
Here are some simple tips for creating an effective PowerPoint Presentation. Less is more: You want to give enough information to make your audience want to read your paper. So include details, but not too many, and avoid too many formulas and technical jargon. Clean and professional: Avoid excessive colors, distracting backgrounds, font ...
Journal of The Association of Physicians of India V ol. 65 September 2017. 72. Presenting Research Paper: Learning the steps. Sandeep B Bavdekar 1, Varun Anand2, Shruti Vyas3. Professor and Head ...
Technical Seminar Topics for CSE with Abstract. 3D Printing. 3D Printing is the process to develop a 3D printed object with the help of additive processes. Here, there are three-dimensional objects created by a 3D printer using depositing materials as per the digital model available on the system. 4G Technology.
Paper Presentation Each accepted paper should be presented by one of the authors and accompanied by at least one full registration fee payment, to guarantee publication in the proceedings. All accepted papers will be included in the proceedings of ICTAI 2024 that will be published by the IEEE Computer Society.
This paper describes how the concept of distributed computing came into existence based on the advantages and disadvantages that raised in earlier networking concepts. ... Krishnamohan D. G. Paper Presentation on Computer Networks. Orient. J. Comp. Sci. and Technol;4(2) Copy the following to cite this URL: Krishnamohan D. G. Paper Presentation ...
Premium Google Slides theme and PowerPoint template. A slide deck whose overall look and feel is very techie is what you need to put forward a proposal for a computer science project. And that's what you'll get with this template. The details on the backgrounds are so enticing and the neon tone used for the text contrasts very well with ...
Paper Presentation Topics, PPT Topics, PPT competitions, Paper Presentation events, Seminar Topics. Events. Events. Find the List of Events happening all across India . ... the 9th International Conference on Computer Vision & Image Processing will be held at Indian Institute of Information Technology Design and Manufacturing ( IIITDM), Chennai ...
Everyone in the class will give one presentation on a research paper from a human-computer interaction conference. The goals of this assignment are to. Provide you and the class with an opportunity to learn about recent research in HCI. Provide you with the opportunity to practice your presentation skills, which is critical to your future ...
Today, we're introducing Meta Llama 3, the next generation of our state-of-the-art open source large language model. Llama 3 models will soon be available on AWS, Databricks, Google Cloud, Hugging Face, Kaggle, IBM WatsonX, Microsoft Azure, NVIDIA NIM, and Snowflake, and with support from hardware platforms offered by AMD, AWS, Dell, Intel, NVIDIA, and Qualcomm.