

Export role assignments for all Azure subscriptions
Microsoft has done it straightforward to get an overview of Azure role assignments for a subscription. They have added the Download role assignments button in the Azure portal under Subscriptions. When I’m working with customers that have many subscriptions, I’ll like to get an overview of all the subscriptions at once. Therefore I use PowerShell the export role assignments for all Azure subscriptions at once.
Script parameters
There are 2 parameters in the script, $OutputPath and $SelectCurrentSubscription . None of them are mandatory.
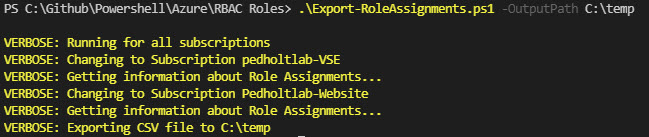
$OutputPath: If defined, a CSV file will be exported to the chosen location. Example: .\Export-RoleAssignments.ps1 -OutputPath C:\temp
$SelectCurrentSubscription: Will only export role assignments from the subscription that are selected. Example: .\Export-RoleAssignments.ps1 -SelectCurrentSubscription
Run Get-Azcontext to view which subscription is selected.
Script Output
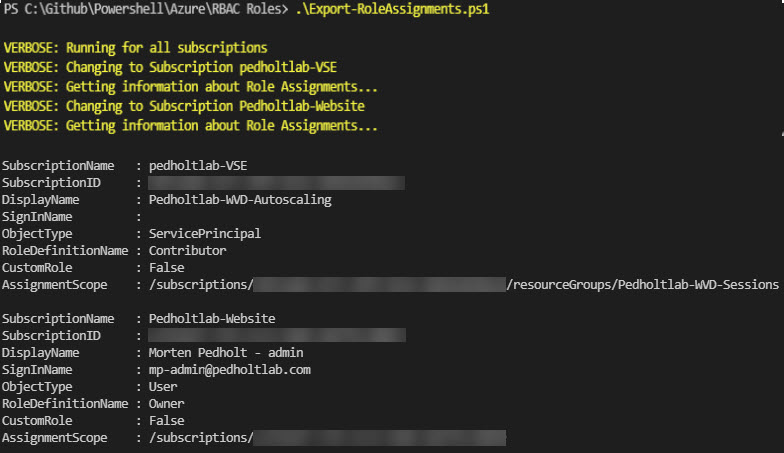
Besides getting an overview of the overall role assignments in an Azure subscription, I also like to know if a role is a Custom or Built-in role. The script will check each assignment if CustomRole is True or False.
Output Example in Powershell Console
Output Example to CSV File
The PowerShell Script
The Powershell script will be available on my account Github . Go there for the latest updates (article script will not be synced with the GitHub version).
3 thoughts on “ Export role assignments for all Azure subscriptions ”
Can you edit the script that when roles assigned to groups the group members are also exported in that csv?
getting the following error on azuread part:
PS C:\scripts> .\azure.ps1 -OutPutPath C:\temp VERBOSE: Running for all subscriptions in tenant VERBOSE: Changing to Subscription Access to Azure Active Directory VERBOSE: Getting information about Role Assignments… WARNING: We have migrated the API calls for this cmdlet from Azure Active Directory Graph to Microsoft Graph. Visit https://go.microsoft.com/fwlink/?linkid=2181475 for any permission issues. Get-AzRoleAssignment : Operation returned an invalid status code ‘BadRequest’ At C:\scripts\azure.ps1:39 char:14 + $roles = Get-AzRoleAssignment | Select-Object RoleDefinitionName, … + ~~~~~~~~~~~~~~~~~~~~ + CategoryInfo : CloseError: (:) [Get-AzRoleAssignment], ErrorResponseException + FullyQualifiedErrorId : Microsoft.Azure.Commands.Resources.GetAzureRoleAssignmentCommand
You have to edit the script for it to work again. You will have to change the API call to Microsoft Graph. Maybe I will do it at some point.
Leave a Reply Cancel reply
Your email address will not be published.
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Understand Azure role assignments
- 2 contributors
Role assignments enable you to grant a principal (such as a user, a group, a managed identity, or a service principal) access to a specific Azure resource. This article describes the details of role assignments.
Role assignment
Access to Azure resources is granted by creating a role assignment, and access is revoked by removing a role assignment.
A role assignment has several components, including:
- The principal , or who is assigned the role.
- The role that they're assigned.
- The scope at which the role is assigned.
- The name of the role assignment, and a description that helps you to explain why the role has been assigned.
For example, you can use Azure RBAC to assign roles like:
- User Sally has owner access to the storage account contoso123 in the resource group ContosoStorage .
- Everybody in the Cloud Administrators group in Microsoft Entra ID has reader access to all resources in the resource group ContosoStorage .
- The managed identity associated with an application is allowed to restart virtual machines within Contoso's subscription.
The following shows an example of the properties in a role assignment when displayed using Azure PowerShell :
The following shows an example of the properties in a role assignment when displayed using the Azure CLI , or the REST API :
The following table describes what the role assignment properties mean.
When you create a role assignment, you need to specify the scope at which it's applied. The scope represents the resource, or set of resources, that the principal is allowed to access. You can scope a role assignment to a single resource, a resource group, a subscription, or a management group.
Use the smallest scope that you need to meet your requirements.
For example, if you need to grant a managed identity access to a single storage account, it's good security practice to create the role assignment at the scope of the storage account, not at the resource group or subscription scope.
For more information about scope, see Understand scope .

Role to assign
A role assignment is associated with a role definition. The role definition specifies the permissions that the principal should have within the role assignment's scope.
You can assign a built-in role definition or a custom role definition. When you create a role assignment, some tooling requires that you use the role definition ID while other tooling allows you to provide the name of the role.
For more information about role definitions, see Understand role definitions .
Principals include users, security groups, managed identities, workload identities, and service principals. Principals are created and managed in your Microsoft Entra tenant. You can assign a role to any principal. Use the Microsoft Entra ID object ID to identify the principal that you want to assign the role to.
When you create a role assignment by using Azure PowerShell, the Azure CLI, Bicep, or another infrastructure as code (IaC) technology, you specify the principal type . Principal types include User , Group , and ServicePrincipal . It's important to specify the correct principal type. Otherwise, you might get intermittent deployment errors, especially when you work with service principals and managed identities.
A role assignment's resource name must be a globally unique identifier (GUID).
Role assignment resource names must be unique within the Microsoft Entra tenant, even if the scope of the role assignment is narrower.
When you create a role assignment by using the Azure portal, Azure PowerShell, or the Azure CLI, the creation process gives the role assignment a unique name for you automatically.
If you create a role assignment by using Bicep or another infrastructure as code (IaC) technology, you need to carefully plan how you name your role assignments. For more information, see Create Azure RBAC resources by using Bicep .
Resource deletion behavior
When you delete a user, group, service principal, or managed identity from Microsoft Entra ID, it's a good practice to delete any role assignments. They aren't deleted automatically. Any role assignments that refer to a deleted principal ID become invalid.
If you try to reuse a role assignment's name for another role assignment, the deployment will fail. This issue is more likely to occur when you use Bicep or an Azure Resource Manager template (ARM template) to deploy your role assignments, because you have to explicitly set the role assignment name when you use these tools. To work around this behavior, you should either remove the old role assignment before you recreate it, or ensure that you use a unique name when you deploy a new role assignment.
Description
You can add a text description to a role assignment. While descriptions are optional, it's a good practice to add them to your role assignments. Provide a short justification for why the principal needs the assigned role. When somebody audits the role assignments, descriptions can help to understand why they've been created and whether they're still applicable.
Some roles support role assignment conditions based on attributes in the context of specific actions. A role assignment condition is an additional check that you can optionally add to your role assignment to provide more fine-grained access control.
For example, you can add a condition that requires an object to have a specific tag for the user to read the object.
You typically build conditions using a visual condition editor, but here's what an example condition looks like in code:
The preceding condition allows users to read blobs with a blob index tag key of Project and a value of Cascade .
For more information about conditions, see What is Azure attribute-based access control (Azure ABAC)?
- Delegate Azure access management to others
- Steps to assign an Azure role
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Search code, repositories, users, issues, pull requests...
Provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement . We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
azurerm_role_assignment.role_definition_id changes upon every apply #25328
unique-dominik commented Mar 20, 2024 • edited
magodo commented Mar 21, 2024
Besides, regarding the source of the azurerm_role_assignment.role_definition_id , i.e. the azurerm_role_definition.role_definition_resource_id , its format depends on how we GET it. As a role definition can have multiple assignable scopes, it means you can GET it via different prefix scopes. Depending on how you GET it (e.g. with only the scope prefix, or with one of the assignable_scopes ), it makes the result response's id has the same scope prefix.
Back to the first issue, as the provider version didn't change, and also the API behavior shall remain still. I suspect you've some out-of-band change on the azurerm_role_definition resource (e.g. change of the scope).
- 👀 1 reaction
Sorry, something went wrong.
unique-dominik commented Mar 22, 2024
- 👍 1 reaction
No branches or pull requests

IMAGES
VIDEO
COMMENTS
For your subscriptions, Azure management groups help you efficiently manage: Access. Policies. Compliance. Each management group contains one or more subscriptions. Azure arranges management groups in a single hierarchy. You define this hierarchy in your Microsoft Entra tenant to align with your organization's structure and needs.
I have an Azure function app that is hosted in subscription "sub-test1" and I want to add role assignment to give the managed system identity(for app) access to the subscription "sub-test1"(current) and I have been able to do it via the following:
Another scenario where you would use management groups is to provide user access to multiple subscriptions. By moving multiple subscriptions under that management group, you can create one Azure role assignment on the management group, which will inherit that access to all the subscriptions. One assignment on the management group can enable users to have access to everything they need instead ...
Step 1: Identify the needed scope. Step 2: Open the Add role assignment page. Step 3: Select the appropriate role. Show 4 more. Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a ...
For your subscriptions, Azure management groups help you efficiently manage: \n \n; Access \n; Policies \n; Compliance \n \n. Each management group contains one or more subscriptions. \n. Azure arranges management groups in a single hierarchy. You define this hierarchy in your Microsoft Entra tenant to align with your organization's structure ...
In the Azure portal, visit the Management groups blade and click Add management group to get started. Next, fill in the Add management group section, specifying the following metadata: Management group ID: This is the Azure AD-wide unique identifier for your management group—you provide the name. Management group display name: Self-explanatory.
Microsoft has done it straightforward to get an overview of Azure role assignments for a subscription. They have added the Download role assignments button in the Azure portal under Subscriptions. When I'm working with customers that have many subscriptions, I'll like to get an overview of all the subscriptions at once.
Essentially to do a role assignment, you deploy into the Scope of the resource E.g. the resource group, Then you use an existing reference, then you can do the role assignment at that scope of that resource. So if you have 2 resource groups, you need to have a module to deploy into the scope of those resources groups Etc. Here is also an ...
Figure 2: Select role. Step 2: On the Members tab, select the user you want to delegate the role assignments task to. Figure 3: Select members. Step 3: On the Condition tab, click Add condition to add the condition to the role assignment. Figure 4: Add condition to role assignment. Step 4: On the Add role assignment condition page, specify how ...
The following shows an example of the Access control (IAM) page for a subscription. Click the Role assignments tab to view the role assignments at this scope. Click Add > Add role assignment. If you don't have permissions to assign roles, the Add role assignment option will be disabled. The Add role assignment page opens. Step 3: Select the ...
⏩ Should we create ONE or MULTIPLE subscriptions in Azure? - What is Role Assignment and how many types of Roles exist? - What are #Azure #Resource #Limits? ...
Step 2: Select the appropriate role. Step 3: Identify the needed scope. Step 4: Check your prerequisites. Show 2 more. Azure role-based access control (Azure RBAC) is the authorization system you use to manage access to Azure resources. To grant access, you assign roles to users, groups, service principals, or managed identities at a particular ...
Step 3: Assign the Reader role. On the Role tab, select Reader as the role and click Next. The Member tab opens. Select User, group, or service principal if it's not selected by default, and then click Select members. In the Select members panel, type Pyra and then select PyraCloud (Azure) from the search results.
I am trying to deploy multiple role assignments to a managed identity through bicep modules. I was able to create multiple role assignments under the same subscription (but under different resource groups) by changing the module scope to the resource group I want. However, I am not able to do it for resource groups from different subscriptions.
Assign roles in Azure RBAC; ... Supports custom roles: Scope can be specified at multiple levels (management group, subscription, resource group, resource) ... Service Administrator and the Co-Administrators have the equivalent access of users who have been assigned the Owner role (an Azure role) at the subscription scope. The following table ...
id - The Role Assignment ID. Timeouts. The timeouts block allows you to specify timeouts for certain actions: create - (Defaults to 30 minutes) Used when creating the Role Assignment. read - (Defaults to 5 minutes) Used when retrieving the Role Assignment. delete - (Defaults to 30 minutes) Used when deleting the Role Assignment. Import
Role assignments enable you to grant a principal (such as a user, a group, a managed identity, or a service principal) access to a specific Azure resource. This article describes the details of role assignments. Role assignment. Access to Azure resources is granted by creating a role assignment, and access is revoked by removing a role assignment.
Azure ARM Template, assign multiple roles to managed identity in Automation Account. I try to build an ARM Template to create Automation Account with System Managed Identity, and in the same template add role assignment on the Subscription level to that System Managed Identity. The code I use is:
@unique-dominik There are two issues around this:. Why the first diff occurs; Why the plan diff after apply occurs; Begin with the 2nd one: The role assignment service will conditionally modify the role_definition_id depending on the azurerm_role_assignment.scope.. E.g. given:
However, the UI only allows me to assign a single role to a user or group. I can't find how to assign multiple roles to a user or group. I can add the user to multiple groups and assign roles to members of that group, which will result in multiple role claims in the token for that user, but this seems awkward. Am I missing something?