

Essay on Internet Privacy
Students are often asked to write an essay on Internet Privacy in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Internet Privacy
Understanding internet privacy.
Internet privacy is about protecting your personal data online. It’s important because when you use the internet, you share information that others could misuse.
Why is Internet Privacy Important?
Internet privacy is crucial to protect your identity and personal information. Without it, strangers could access your data, leading to potential harm.
How to Maintain Internet Privacy?
You can maintain internet privacy by using strong passwords, enabling privacy settings on social media, and avoiding sharing sensitive information online. Always remember, your online safety is in your hands.
250 Words Essay on Internet Privacy
Introduction to internet privacy.
Internet privacy, often synonymous with online privacy, is a subset of data privacy focusing on the protection of personal information in the digital realm. As the internet becomes increasingly integral to our daily lives, privacy issues have surged to the forefront of societal discourse.
The Importance of Internet Privacy
Internet privacy is crucial for numerous reasons. It safeguards personal data, prevents identity theft, and preserves freedom of speech. In the era of digitalization, a breach in privacy can lead to damaging consequences, ranging from financial loss to emotional distress.
Threats to Internet Privacy
Threats to internet privacy are manifold. They include cybercriminal activities, surveillance by government agencies, data mining by corporations, and even seemingly innocuous social media platforms that collect and utilize user data.
Internet Privacy: A Human Right?
Many argue that internet privacy is a fundamental human right. This perspective highlights the need for stringent laws and policies to protect individuals from intrusive surveillance and unauthorized data collection.
The Role of Individuals in Protecting Privacy
While legislation plays a vital role, individuals must also take proactive steps to safeguard their online privacy. This can include using encrypted communication, regularly updating software, and being mindful of the information shared online.
Internet privacy is a complex and critical issue in the digital age. The collective efforts of individuals, corporations, and governments are necessary to ensure the protection of personal information in the online sphere. As we continue to navigate this interconnected world, the importance of internet privacy will only increase.
500 Words Essay on Internet Privacy
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Internet privacy is crucial for numerous reasons. Primarily, it protects individuals’ identity and personal information from potential cybercriminals. With the rise of the digital economy, people are increasingly sharing their sensitive data online, making them vulnerable to identity theft, cyberstalking, and other forms of cybercrime. Internet privacy also ensures the freedom of speech and thought online, as it allows individuals to express their views without fear of being tracked or monitored.
Despite its importance, internet privacy is under constant threat. Cybercriminals often exploit security breaches to steal sensitive data. Also, many online platforms and services thrive on data collection, often without clear consent from users. Governments, too, may infringe upon internet privacy for surveillance and security purposes.
The Role of Legislation in Internet Privacy
Legislation plays a crucial role in protecting internet privacy. Laws like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States are examples of attempts to regulate data collection and usage. However, enforcing these laws across borders is challenging, and loopholes often exist that allow for continued privacy infringements.
Individual Responsibility and Internet Privacy
While legislation is important, individual responsibility is equally critical in ensuring internet privacy. Users should be aware of the data they share online and the potential risks involved. They should also use privacy-enhancing tools, such as Virtual Private Networks (VPNs), secure browsers, and encryption, to protect their data.
Conclusion: The Future of Internet Privacy
The future of internet privacy is uncertain. On one hand, advancements in technology, such as blockchain and quantum computing, could potentially enhance data security. On the other hand, the increasing digitization of our lives threatens to erode privacy further. The challenge lies in finding a balance between the benefits of the digital age and the preservation of privacy. As we move forward, the discourse on internet privacy will remain a pivotal aspect of our digital lives.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Uses and Abuses of Internet
- Essay on These Days Exposure to Television and Internet
- Essay on Internet Influence on Kids
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

25,000+ students realised their study abroad dream with us. Take the first step today
Here’s your new year gift, one app for all your, study abroad needs, start your journey, track your progress, grow with the community and so much more.

Verification Code
An OTP has been sent to your registered mobile no. Please verify

Thanks for your comment !
Our team will review it before it's shown to our readers.

Speech on Internet Privacy
- Updated on
- Jul 2, 2021

It is rightly said that today’s era is a digital era. We may not realize it now, but the internet has become a new necessity in our lives. It has witnessed a boom like never before. In today’s time, the internet is as important to us as food, water, air is. Having said that, internet or internet privacy does have a dark side about which we must be aware of. Internet users must be well-versed in the methods for safeguarding their data on the internet. In this blog, we have brought to you a speech on internet privacy that you can refer to for your English homework, assignments, and exams.
Table of contents
What is internet privacy, speech on internet privacy: sample 1 (200-300 words), speech on internet privacy: sample 2 (400-500 words), relatable links.
Must Read: Essay on Internet: Advantages and Disadvantages
Before actually skipping onto the speech on internet privacy, let us first discuss what is meant by internet privacy. The amount of privacy protection an individual has while connected to the Internet is defined as online privacy or internet privacy. It discusses the level of internet security accessible for personal and financial information, conversations, and preferences. Internet users frequently try to enhance their online privacy by using anti-virus software, creating strong passwords, disabling tracking, evaluating site security, and selecting for tougher privacy settings. Online privacy threats vary from phishing schemes to viruses, and issues with website security can lead to identity theft. Internet privacy is a complicated topic that encompasses how your personal information is utilized, gathered, shared, and kept on your own devices and when connected to the Internet. Personal information about your habits, purchasing, and location can be gathered and shared with third parties via your phone, GPS, and other devices. Users of the internet and mobile devices have the right to know how their information will be used and to examine online privacy policies.
Also Read: Cyber Security Courses: A Detailed Guide and Top 10 Cybersecurity Skills for Beginners
Good morning everyone! I am Aryaman and today I stand before you to present an insightful and informative speech on Internet Privacy. Privacy, whether offline or online, is definitely our right, which should be demanded and expected no matter what the cost, but one might wonder why there is so much concern centered around internet privacy. Most of our lives have become virtual in the pandemic era, and all activities that were previously done offline are now done online. Be it our bank details, legal discussions with CA , or our professional work-related details, there is no guarantee that privacy on the internet is guarded.
In the year 1997, the Consumer Internet Privacy Protection Act was passed by the government as per which the consumer information shared on the internet should be safeguarded at any cost, but still, it is a matter of utmost concern and importance because the internet offers various communication tools which are frequently used and there too, the information being shared can be tracked by someone who knows how to do it and also technology has grown at a steadfast level that even our old messages that are deleted can be easily retrieved because of availability of countless apps. Certain websites use cookies that record data while we sign up or log in and, even if we are anonymous, it is relatively easy in this technologically advanced era to know our true identity, personal details, and Internet Service Provider details as well.
As a result, whatever web-based email services we use, such as Yahoo, Hotmail, or Gmail, we must be familiar with the privacy policies of those services before signing up or logging in to protect our privacy, and we must not hesitate to take action against heinous cybercrimes if we become aware of any kind of cyber abuse.
Also Read: Safer Internet Day 2021
Good morning everyone! I am Aryaman and today I stand before you to present an insightful and informative speech on Internet Privacy. We can define internet privacy as safeguarding our personal, financial, and other important information when we are online. However, after decoding the definition, one must ask, “Is internet privacy a reality or a myth?”Let us further explore this problem and crack the code. Due to the pandemic, most of our lives have now taken a virtual turn and most of our tasks, be it our work meetings, binge-watching our favorite web series, chatting with friends, online business transactions, and banking transactions, are all done online.
In real life, we only disclose information that we believe is not confidential, but in the online world, simple information such as email IDs and passwords can be traced by a skilled individual, and technology has advanced to the point where the internet and mobile phones are available to children, making them just as vulnerable as adults. After understanding the gravity of the situation, we must explore the ways in which we can ensure our online privacy. To begin with, there are a plethora of software applications that ensure online privacy, such as anti-viruses and anti-malware, and it is critical that these software applications are updated to their most recent version to avoid any sort of privacy problem. Second of all, internet history must be cleared on a regular basis. Online investments and banking transactions must be done through reliable sources only. Thirdly, online shopping must be done on reliable websites only which have credibility and authenticity, and we must avoid giving our information to those websites which don’t seem to be genuine and authentic. Also, we must keep a strong password for our email IDs and for other accounts as well.
We must be well-versed in Internet privacy laws, and if we encounter any type of online privacy issue, we must report it immediately so that the problem does not worsen. After attaining a crystal clear understanding of internet privacy, we must continually educate ourselves about this problem and be aware and prevent ourselves from having any sort of online privacy problem. In the end, I would like to say my heartiest thanks to the audience for listening to my speech on internet privacy with patience.
- Speech on Indian Education System
- Speech on Importance of English
- Generation Gap Speech for Students
- Sample Essay & Speech on Fear for ASL
- Speech on Co-Education For School Students
How did you all find the speech? Do let us know your thoughts on the same in the comments section. Also, feel free to reach our experts at Leverage Edu , to seek guidance at every step of your study abroad education journey.
Team Leverage Edu
Leave a Reply Cancel reply
Save my name, email, and website in this browser for the next time I comment.
Contact no. *

Leaving already?
8 Universities with higher ROI than IITs and IIMs
Grab this one-time opportunity to download this ebook
Connect With Us
25,000+ students realised their study abroad dream with us. take the first step today..

Resend OTP in

Need help with?
Study abroad.
UK, Canada, US & More
IELTS, GRE, GMAT & More
Scholarship, Loans & Forex
Country Preference
New Zealand
Which English test are you planning to take?
Which academic test are you planning to take.
Not Sure yet
When are you planning to take the exam?
Already booked my exam slot
Within 2 Months
Want to learn about the test
Which Degree do you wish to pursue?
When do you want to start studying abroad.
September 2024
January 2025
What is your budget to study abroad?

How would you describe this article ?
Please rate this article
We would like to hear more.
Home — Essay Samples — Law, Crime & Punishment — Privacy & Security — Internet Privacy
Essays on Internet Privacy
The importance of writing an essay on internet privacy.
Writing an essay on internet privacy is crucial in today's digital age. With the increasing use of the internet for communication, social networking, and online transactions, the issue of privacy has become more important than ever. It is essential to educate people about the potential risks and threats to their privacy online and to advocate for stronger privacy protections.
Internet privacy is a fundamental human right, and writing an essay on this topic can help raise awareness about the importance of protecting personal information online. It can also encourage individuals to take steps to safeguard their privacy and advocate for laws and regulations that protect their rights.
When writing an essay on internet privacy, it is important to research and gather relevant information from credible sources. This may include academic journals, government reports, and reputable news outlets. It is also important to consider different perspectives and arguments on the topic to provide a well-rounded and comprehensive analysis.
Additionally, it is crucial to clearly articulate the potential risks and threats to internet privacy, such as data breaches, online surveillance, and identity theft. Providing real-life examples and case studies can help illustrate the impact of these issues on individuals and society as a whole.
Furthermore, it is essential to offer practical tips and solutions for protecting internet privacy, such as using strong passwords, enabling two-factor authentication, and being cautious about sharing personal information online. By empowering individuals with the knowledge and tools to protect their privacy, the essay can have a positive impact on the reader and the broader community.
Writing an essay on internet privacy is important for raising awareness, advocating for stronger privacy protections, and empowering individuals to safeguard their personal information online. By conducting thorough research, considering different perspectives, and providing practical solutions, the essay can help contribute to a more privacy-conscious and informed society.
- The importance of internet privacy in the digital age
In today's technology-driven world, internet privacy has become a major concern for individuals and businesses alike. With the increasing amount of personal information being shared online, it is important to understand the importance of protecting one's privacy on the internet. This essay will delve into the reasons why internet privacy is important and the potential consequences of not safeguarding one's online information.
- The evolution of internet privacy laws
Over the years, there have been significant developments in internet privacy laws as governments and regulatory bodies have recognized the need to protect individuals' personal information online. This essay will explore the evolution of internet privacy laws, including the landmark legislation and regulations that have been enacted to safeguard online privacy rights.
- The impact of social media on internet privacy
Social media has revolutionized the way we communicate and share information, but it has also raised concerns about internet privacy. This essay will examine the impact of social media on internet privacy, including the risks associated with sharing personal information on social networking platforms and the measures individuals can take to protect their privacy online.
- The role of technology in internet privacy
Advancements in technology have both enhanced and compromised internet privacy. This essay will discuss the role of technology in internet privacy, including the development of encryption tools, the rise of data breaches, and the potential implications of emerging technologies on online privacy rights.
- The ethical considerations of internet privacy
As individuals and businesses navigate the digital landscape, ethical considerations surrounding internet privacy have come to the forefront. This essay will explore the ethical implications of internet privacy, including the ethical responsibilities of organizations to protect user data and the ethical dilemmas individuals face when sharing personal information online.
- The impact of data breaches on internet privacy
Data breaches have become a prevalent threat to internet privacy, as cybercriminals continue to target organizations to access sensitive personal information. This essay will examine the impact of data breaches on internet privacy, including the potential consequences for individuals and businesses and the measures that can be taken to mitigate the risks of data breaches.
- The future of internet privacy
As technology continues to evolve, the future of internet privacy remains uncertain. This essay will speculate on the future of internet privacy, including the potential challenges and opportunities that lie ahead as individuals and organizations strive to protect their online privacy rights.
- The intersection of internet privacy and cybersecurity
Internet privacy and cybersecurity are closely intertwined, as both are essential for protecting personal information online. This essay will explore the intersection of internet privacy and cybersecurity, including the measures that can be taken to safeguard online privacy and the role of cybersecurity in mitigating privacy risks.
- The global perspective on internet privacy
Internet privacy is a universal concern, and different countries have varying approaches to protecting online privacy rights. This essay will provide a global perspective on internet privacy, including the international laws and regulations that govern internet privacy and the challenges of ensuring privacy rights in a global digital landscape.
- The responsibility of individuals in protecting their internet privacy
Ultimately, individuals play a crucial role in protecting their internet privacy. This essay will discuss the responsibility of individuals in safeguarding their online privacy, including the best practices for maintaining internet privacy and the potential consequences of neglecting online privacy protection.
Is Google Making Usupid Summary
The internet makes children smarter, made-to-order essay as fast as you need it.
Each essay is customized to cater to your unique preferences
+ experts online
The Internet: a Challenge to Copyright Protection
The importance of internet privacy and net neutrality to internet users in the modern era, why internet privacy should be protected, the importance of internet privacy, let us write you an essay from scratch.
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
The Importance of Staying Safe on Social Media
Cyber crime and internet privacy, the crucial role of internet privacy for a user, a privacy aspect to the internet of things, get a personalized essay in under 3 hours.
Expert-written essays crafted with your exact needs in mind
Identifying Threats and Vulnerabilities in Home Internet Connection
Human rights on the digital era, brief history of cyber security, privacy issues in a smart city, the concepts and outcomes of net neutrality, the singaporean government's ideologically conservative view on the internet, enhancing online security: qr code-based authentication for banking, secure online auction system, iot: addressing security challenges and possible solutions, analysis of the benefits of internet censorship, internet censorship as a modern way to protect the youth, internet censorship as the new 'norm', internet censorship: beneficial, but restrictive, personal outlook on the issue of internet censorship, useful alternatives for internet censorship, wikipedia censorship: the advantage for governments authorities, the data protection: how your personal information is used by organisations, businesses or the government, protect your data. then hope for a tech revolution, how technological advancement is going to affect us, should the internet be regulated: exploring possibilites to follow, relevant topics.
- Serial Killer
- War on Drugs
- School Shooting
- Child Abuse
- Broken Windows Theory
- Criminal Psychology
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
https://www.nist.gov/blogs/taking-measure/why-security-and-privacy-matter-digital-world
Taking Measure
Just a Standard Blog
Why Security and Privacy Matter in a Digital World

One cannot pick up a newspaper, watch TV, listen to the radio, or scan the news on the internet without some direct or veiled reference to the lack of information security or intrusions into personal privacy. Many intrusions into government and private-sector systems have exposed sensitive mission, business and personal information. Every day it seems that more and more systems are breached and more and more personal information is made available either on the web or, worse, the dark web . Given this backdrop, it is often easy to get lost in the details of cybersecurity and privacy and the seemingly endless discussions about cyber attacks, system breaches, frameworks, requirements, controls, assessments, continuous monitoring and risk management and forget why security and personal privacy matter in an increasingly digital world.
We are witnessing and taking part in the greatest information technology revolution in the history of mankind as our society undergoes the transition from a largely paper-based world to a fully digital world. As part of that transformation, we continue to push computers closer to the edge. The “edge” today is the burgeoning and already vast world of the “Internet of Things,” or IoT. This new world consists of an incredibly diverse set of familiar everyday technologies, including dishwashers, refrigerators, cameras, DVRs, medical devices, satellites, automobiles, televisions, traffic lights, drones, baby monitors, building fire/security systems, smartphones and tablets. It also includes technologies that are perhaps less familiar to the average person but absolutely vital to maintaining and safeguarding the familiar world in which they live: advanced military weapons systems; industrial and process control systems that support power plants and the nationwide electric grid, manufacturing plants and water distribution plants; emergency response systems; banking and financial systems; and transportation systems—in short, our most critical infrastructure. Yes, we have fully embraced this emerging technology and pushed computers, software and devices everywhere to the edge of this new world. And as those technologies, both familiar and critical, become increasingly integrated with IoT, so does information , all kinds of information, including intellectual property and your personal information.
It goes without saying that innovations in information technology and IoT will continue to make us more productive, help us solve difficult and challenging problems, entertain us, allow us to communicate with virtually anyone in the world instantaneously, and provide all kinds of additional, and previously unimaginable, benefits. For instance, who wouldn’t want an app that tells you the optimal time to go to the restroom during the movie you’re about to see at your local theater? These new technologies are not only compelling, but also intoxicating and addicting—leaving us with a huge blind spot that puts us at great risk of losing our property, our privacy, our security and, in some cases, our lives.
We have built an incredibly complex information technology infrastructure consisting of millions of billions of lines of code, hardware platforms with integrated circuits on computer chips, and millions of applications on every type of computing platform from smart watches to mainframes. And right in the middle of all that complexity, your information is being routinely processed, stored and transmitted through global networks of connected systems. From a security and privacy perspective, we are not only concerned about the confidentiality, integrity and availability of the data contained in the systems embedded deep in the nation’s critical infrastructure, but also of our personal information.
Recognizing the importance of both security and privacy safeguards for systems, organizations and individuals, NIST recently initiated several groundbreaking projects to bring these concepts closer together—to facilitate the development of stronger, more robust security and privacy programs and provide a unified approach for protecting all types of information, including personal information. The first installment in this new approach occurred with the release of NIST Special Publication 800-53, Revision 5 , which provided, for the first time in the standards community, a consolidated catalog of security and privacy controls—standing side by side with the broad-based safeguards needed to protect systems and personal privacy.
Today, NIST is announcing the second installment of the unified approach to privacy and security by releasing a discussion draft of NIST Special Publication 800-37, Revision 2 . This publication responds to the President’s Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure and the Office of Management and Budget’s Memorandum M-17-25 (implementation guidance for the Executive Order) to develop the next-generation Risk Management Framework (RMF 2.0) for systems, organizations and individuals. RMF 2.0 provides a disciplined, structured and repeatable process for organizations to select, implement, assess and continuously monitor security and privacy controls.
NIST Special Publication 800-37, Revision 2, empowers customers to take charge of their protection needs and provide security and privacy solutions to support organizational missions and business objectives. It includes a new organizational preparation step, instituted to achieve more timely, effective, efficient and cost-effective risk management processes. The organizational preparation step incorporates concepts from the Cybersecurity Framework to facilitate better communication between senior leaders and executives at the enterprise and mission/business process levels and system owners—conveying acceptable limits regarding the implementation of security and privacy controls within the established organizational risk tolerance. The enterprise-wide preparation also facilitates the identification of common controls and the development of organization-wide tailored security and privacy control baselines. This significantly reduces the workload on individual system owners, provides more customized security and privacy solutions, and lowers the overall cost of system development and protection.
And finally, RMF 2.0 helps organizations reduce the complexity of their IT infrastructure by consolidating, standardizing and optimizing systems, applications and services through the application of enterprise architecture concepts and models. Such complexity reduction is critical to identifying, prioritizing and focusing organizational resources on high-value assets that require increased levels of protection—taking steps commensurate with risk such as moving assets to cloud-based systems or shared services, systems and applications.
The transformation to consolidated security and privacy guidelines will help organizations strengthen their foundational security and privacy programs, achieve greater efficiencies in control implementation, promote greater collaboration of security and privacy professionals, and provide an appropriate level of security and privacy protection for systems and individuals.
About the author

Ron Ross is a computer scientist and Fellow at the National Institute of Standards and Technology. He specializes in cybersecurity, risk management, and systems security engineering. Ron is a retired Army officer who, when not defending cyberspace, follows his passion for NASCAR and takes care of his adopted rescue dog, Sophie.
Related posts

Demystifying Quantum: It’s Here, There and Everywhere

Riding the Wind: How Applied Geometry and Artificial Intelligence Can Help Us Win the Renewable Energy Race

From Diamonds in Your Computer to Safer Medications, NIST Researchers Look at What’s Next for 2024 and Beyond
Good afternoon Mr. Ross, I just want to let you know that I do admire your leadership at NIST with such an incredible publications like the SP-800's and others to keep our beautiful country safe. I did work before supporting and improving the ICD503 and your publications were read and exercise by me in order to do my job. I want to thank you for giving me opportunity to continue reading every day on your new development publications on Cyber Security and Information Assurance that are my passion. Have a wonderful day.
Best Regards Carlos G. Salinas
Thank you for your kind remarks, Mr. Salinas. They are very much appreciated. It is an honor and a privilege to be able to serve our public and private sector customers by providing standards, guidelines, and best practices to help them build robust security and privacy programs.
I only just now received the link to the draft SP 800-37. In my opinion, NIST did a great job on RMF already. Unfortunately, I am familiar with a segment of government that immediately assumes it must have its own variations of anything and everything. This "organization" made a mess of RMF from the start, seemingly only wanting to make it as painless as possible. They failed in that by the way. If I had to pick one overriding issue that I would change If I could, it would be the apparent universality of the term "organization" used in so many controls absent a consistent understanding of who or what part of a large organization is being addressed. When an assessment procedure tells me "organizations" are automatically compliant because <insertAgencyNameHere> has defined the <widget> for me, and this control part is not identified as a tier 1 or common offering, several veins of logic are now varicose. The very next control or part may speak of "organization" as if it is the CCP or the ISO without regard for what precedes or follows. My assumption is that many people worked on controls independently and never came to agreement on a standard definition of "organization."
Beautiful blog author.Thank you for sharing.Keep it up.Good wishes for your work.
Beautiful blog post author.Thank you.
Excellent post & thank you so much for sharing
Thank you for your post.
Add new comment
- No HTML tags allowed.
- Web page addresses and email addresses turn into links automatically.
- Lines and paragraphs break automatically.
Internet Privacy - Essay Examples And Topic Ideas For Free
Internet privacy refers to the right or expectation of privacy in the digital realm, encompassing issues related to the protection of personal data, confidentiality, and anonymity online. Essays on internet privacy could delve into the risks and challenges associated with digital surveillance, data breaches, or online tracking, the impact of laws and regulations on privacy, or the ways in which individuals and organizations can protect privacy online. They might also explore the ethical, social, and political implications of privacy in the digital age, or the tensions between privacy, security, and convenience online. A substantial compilation of free essay instances related to Internet Privacy you can find at PapersOwl Website. You can use our samples for inspiration to write your own essay, research paper, or just to explore a new topic for yourself.
Impact of Technology on Privacy
The 21st Century is characterized by the heavy impact technology has on us as a society while it continues to develop new devices and modernize technology. Millions of individuals around the world are now connected digitally, in other words, people globally rely heavily on smartphones tablets, and/ or computers that store or save a majority of their personal information. Critical and extremely personal data is available and collected in these smart technology such as credit card details, fingerprint layout, and […]
A World Without Internet
On the street is the 21st century. Almost all people on our planet have access to the Internet. And they are actively using it. But they forget that they use it almost around the clock. From watching the weather in the morning to texting on social media in the evening. Instead of writing an essay by hand, a modern student simply downloads it. People on the Internet are already looking for work, pay for housing and communal services, participate in […]
Positive and Negative Effects of Internet
The topic of the pros and cons of the Internet is one of the most controversial topics. People often cannot give a definite answer to it. The topic of the Internet is quite versatile. Let's look at it from the positive side first. The Internet is the greatest invention of mankind, which made life easier and continues to do it for us hundreds of times. Its first plus is, of course, the available information. Now you can find out any […]
We will write an essay sample crafted to your needs.
Security Versus Freedom?
Welcome to the Digital Age. In today’s connected world, we are living much of our live online. As a result, companies everywhere are creating large storehouses of data on all of us. The most obvious information being collected is social media data. Everything we post publicly and some cases privately, is being stored and analysed. But it is not just social media, there is now a digital record of everything we buy, everything we watch, where we go and what […]
Internet Access Restrictions May Vary
Fantastic. In most instances, they are placed on search quarries and are most prominent at education centers. This is simply to keep minds safe from content unsuitable for most ages (Gonchar). Although this is an effective plan with good intentions, it can become more effective by being enforced on younger ages rather than those who have already been exposed to the negative side of the internet. As you enter high school you have nearly done and seen everything there […]
Securing Cyberspace: Crafting Tomorrow’s Internet Privacy Laws
In an era where digital footprints shape our daily lives, the quest to safeguard personal privacy in the vast expanse of the internet has become more critical than ever before. Transitioning from the pixels that construct our online world to the intricate policies governing its boundaries signifies a pivotal juncture in the evolution of digital governance. As we navigate through this landscape of data, the formulation of robust internet privacy legislation emerges as a beacon of protection against the perils […]
Silent Struggle: Assessing Threats to Internet Privacy and Security
In today's digital age, the internet serves as the cornerstone of modern communication, commerce, and entertainment. However, amidst the convenience and connectivity it offers, lurks a pervasive and often invisible battle for privacy and security. From data breaches to surveillance, the threats to our online well-being are manifold and ever-evolving. One of the most concerning threats is the rampant collection and misuse of personal data by corporations and governments alike. Every click, search, and purchase leaves a digital footprint, eagerly […]
Safeguarding Cyberspace: the Vital Role of AI in Preserving Online Privacy
In an era where our digital footprints grow larger with every click, the question of how to protect our online privacy becomes increasingly pertinent. Enter Artificial Intelligence, our modern-day guardians in the complex realm of cyberspace. Far beyond mere machines crunching numbers, AI has evolved into a formidable force in the fight against privacy breaches. The first and foremost duty of AI guardians is to fortify our virtual boundaries. Picture them as vigilant sentinels stationed at the gates of our […]
Preserving Digital Integrity: a Scholarly Evaluation of Internet Privacy
In the contemporary digital epoch, where the internet serves as an omnipotent conduit for global interaction, commerce, and information dissemination, the concept of cyber privacy emerges as a pivotal concern. As an academic critic, entrusted with scrutinizing the intricacies of cyber privacy, it becomes essential to unravel the diverse facets of this intricate matter, ranging from its legal and ethical dimensions to its societal and technological reverberations. Cyber privacy fundamentally entails the right of individuals to govern their personal information […]
Additional Example Essays
- Positive Effects of Social Media
- Instagram and body dysmorphia
- The Negative Effects of Social Media On Mental Health
- The Mental Health Stigma
- How the Roles of Women and Men Were Portrayed in "A Doll's House"
- Psychiatric Nurse Practitioner
- Substance Abuse and Mental Illnesses
- Importance Of Accountability
- Are Electric Cars Better Than Petrol Diesel Cars?
- "A Doll's House" as a Modern Tragedy
- Poems “The Negro Speaks of Rivers” and “Still I Rise”
- The Unique Use of Literary Devices in The Tell-Tale Heart
1. Tell Us Your Requirements
2. Pick your perfect writer
3. Get Your Paper and Pay
Hi! I'm Amy, your personal assistant!
Don't know where to start? Give me your paper requirements and I connect you to an academic expert.
short deadlines
100% Plagiarism-Free
Certified writers
- Skip to main content
- Keyboard shortcuts for audio player

- LISTEN & FOLLOW
- Apple Podcasts
- Google Podcasts
- Amazon Music
Your support helps make our show possible and unlocks access to our sponsor-free feed.
Your Technology Is Tracking You. Take These Steps For Better Online Privacy

Laurel Wamsley

Before I became a reporter at NPR, I worked for a few years at tech companies.
One of the companies was in the marketing technology business — the industry that's devoted in part to tracking people and merging their information, so they can be advertised to more effectively.
That tracking happens in multiple senses: physical tracking, because we carry our phones everywhere we go. And virtual tracking, of all the places we go online.
The more I understood how my information was being collected, shared and sold, the more I wanted to protect my privacy. But it's still hard to know which of my efforts is actually effective and which is a waste of time.
So I reached out to experts in digital security and privacy to find out what they do to protect their stuff – and what they recommend most to us regular folks.
Here's what they told me.

How Are Apple, Amazon, Facebook, Google Monopolies? House Report Counts The Ways
1. to protect your accounts, practice good security hygiene..
There are some steps that make sense for almost all of us, says Eva Galperin , director of cybersecurity at the Electronic Frontier Foundation. Those include using strong passwords, two-factor authentication, and downloading the latest security updates.
She and other experts make a distinction between privacy and security when it comes to your data. Security generally refers to protecting against someone trying to access your stuff — such as stealing your credit card number or hacking your accounts. Privacy is more often used to talk about keeping your movements from being tracked for purposes of advertising or surveillance.
It turns out that the steps to protect your security are more clear-cut than those for privacy — but we'll come back to that.

TED Radio Hour
Edward snowden: why does online privacy matter.
Use strong passwords or passphrases for your accounts. Longer than a password, passphrases should be strong and unique for each site. Don't use 1234. Bring some randomness and special characters into it. And don't use the same password for different websites: You don't want all your accounts to be compromised just because one gets hacked.
Use a password manager to keep track of your passwords, Galperin says — then all you have to do is remember the passphrase for your password manager.
Turn on two-factor authentication for your important accounts. You've seen this: Usually you're asked to put in your mobile number so that you can receive a text with an additional number you input before you can log in.
That's the most common type of two-factor authentication — but it's not the strongest, Galperin says, because SMS messages can be intercepted by your Internet provider, law enforcement or the government.
If you want to go a step further, Galperin recommends using an application that sends the second factor to an app on your phone, such as Authy or Google Authenticator , as these are harder to intercept. (Full disclosure here: NPR receives funding from Google and Facebook.) You can also use a physical key you carry with you that plugs into your computer's USB port and serves as the second factor.


6 Tips For Making A Career Change, From Someone Who Has Done It
Download the latest security updates.
Those nudges you get from your computer or phone to install the latest security update? You should download those.
"Most applications, when they're compromised, are not compromised by scary zero-day bugs that nobody knows about," Galperin says. "They are compromised by problems that everybody knows exist that have been publicly reported, and that the company has fixed and they have issued a patch in their security update. But if you do not take the security update, you do not get the benefit of the work of the security engineers at that company."

How To Sign Up To Work The Polls On Election Day
2. beware of phishing..
Not all attacks on our security come through malware or hackers invisibly breaking into your account. It's common that we're tricked into handing over our passwords or personal information to bad actors.
These attempts can happen via email, text message or a phone call. And generally they're trying to get your username and password, or perhaps your Social Security number. But there are often signs that these messages aren't legit – spelling or grammar errors, links to websites other than the one it should be linking to, or the email is coming from a weird domain.
If it feels fishy, it might be phishing.

Twitter Expands Warning Labels To Slow Spread of Election Misinformation
3. protect what matters most..
Depending on your situation, you might want to take additional precautions to safeguard your privacy and security.
To figure out what steps people should take to safeguard their stuff, Galperin suggests you make a security plan. The Electronic Frontier Foundation has a guide to doing this, which starts by asking yourself these questions:
- What do I want to protect?
- Whom do I want to protect it from?
- How bad are the consequences if I don't?
- How likely is it to need protecting?
- And how much trouble am I willing to go through to try to protect it?
Resources For Securing Your Data
The Surveillance Self-Defense site from the Electronic Frontier Foundation is a good place to start. Here's its guide to making your own security plan and figuring out what you most want to protect.
From Tactical Tech, here are handy how-to kits for different scenarios, including securing your data , increasing your online privacy and making your phone less addictive .
You can use the answers to those questions to focus your efforts on securing the things that matter most to you.
4. Delete some apps from your phone. Use a browser instead.
Matt Mitchell is a tech fellow at the Ford Foundation, and the founder of CryptoHarlem , an organization that teaches people to protect their privacy, including from surveillance.
Apps can learn a lot about you due to all the different types of data they can access via your phone. Seemingly harmless apps – like say, a flashlight app — could be selling the data they gather from you.
That's why Mitchell recommends "Marie Kondo-ing" your apps: Take a look at your smartphone and delete all the apps you don't really need. For many tasks, you can use a browser on your phone instead of an app.
Privacy-wise, browsers are preferable, because they can't access as much of your information as an app can.
I mentioned to Mitchell that even though I use Facebook and Twitter, I don't have those apps on my phone — partly so that I'll use them less, and partly for privacy reasons. I wanted to know — did I accomplish anything by not having those apps on my phone?
"You've accomplished a lot," he says. He compares it to oil companies turning crude into petrol: Your data can be turned into profit for these companies. "Every time you don't use an app, you're giving them less data, which is less money."
Mitchell says that's true even if you've been on Facebook a long time, and it feels like the company already knows everything about you. He compares it to smoking: It's never too late to cut back or quit — you'll still benefit by giving it less data to harvest.
5. To protect your chats, use an encrypted app for messaging.
If you want the contents of your messages to be secure, it's best to use an app that has end-to-end encryption, such as Signal or WhatsApp. That means you and the recipient can read the message you send — but no one in the middle.
But even though the contents of your messages are protected by encryption in apps such as Signal and WhatsApp, your metadata isn't — and someone could learn a lot about you from your metadata, Galperin warns. She compares it to what you can learn just by looking at the outside of an envelope in the mail: who sent it to whom, when and where it was sent from.
And WhatsApp is owned by Facebook — so when you share your contacts with WhatsApp, Facebook is getting that info, though it can't read the contents of your messages.
If you're on an iPhone, iMessages are encrypted when you're messaging another iOS device — but not when you're messaging an Android phone. Signal offers encrypted messaging on both Android and iPhone.
What about Facebook Messenger? Jen King , director of privacy at Stanford Law School's Center for Internet and Society, advises against using the Messenger app.
The app "has access to far more info on your phone than using Facebook through a browser," she says, recommending something such as WhatsApp or regular SMS texting instead.
And if encryption matters to you, be careful about backing up your chats to the cloud. If you back up your WhatsApp messages to iCloud or Google Drive , for example, they're no longer encrypted.
"That backup is just a database. And that database is easy for someone to open and read," Mitchell says, if they were able to access your cloud account. To keep your messages from prying eyes, turn off cloud backups and delete existing WhatsApp backups from iCloud or Google Drive.

California Rings In The New Year With A New Data Privacy Law
6. turn off ad personalization..
Whenever possible, Mitchell recommends going into your settings and turning off ad personalization, which often gives companies permission to do invasive tracking.
Opting Out Of Ad Personalization On Some Major Platforms
Google and Android
Here's a link to limit ad personalization on Google and Android.
This page shows you how to opt out of ad personalization on Apple. As of this writing, it hasn't been updated for iOS 14. If you have updated to iOS 14, go to Settings > Privacy > Apple Advertising > turn off Personalized Ads.
- On this page , you can go to the ad settings tab and toggle the settings to not allowed.
- This page has steps to disconnect your activity off Facebook that is shared with Facebook, and clear that history.
- On the Off-Facebook activity page , under What You Can Do, you can click on More Options > Manage Future Activity > and toggle it to off. ( This page has those steps.)
This page explains how to opt out of ad personalization.
He also recommends going to myactivity.google.com and deleting everything you can. On the left, there's a tab that says "Delete activity by." Select "All time." On your My Google Activity page, you can turn off Web & App Activity, Location History and YouTube History.
"It will show you every search term and everything you've ever done, every YouTube video you've ever looked at, all that stuff," he says. "It'll say, are you sure you want to delete this? 'Cause if you delete this, it might affect some stuff." Mitchell says: Delete it.
7. It's difficult to protect your privacy online if there aren't laws to protect your privacy online.
Tighter privacy settings only get you so far without laws that protect your privacy, says Ashkan Soltani , the former chief technologist for the Federal Trade Commission and one of the architects of the 2018 California Consumer Privacy Act .
Activist Aims To Strengthen California's Consumer Privacy Act
There are laws around health information and credit and financial information, he explains, and some states have Internet privacy-related laws .
But nationally, the U.S. doesn't have a universal data privacy law safeguarding everyday online privacy.
Soltani says he rarely recommends steps such as using ad blockers or VPNs for most people. They require too much attention and persistence to deliver on privacy, and even then they are limited in their effectiveness.
"The incentives are so high on the other side," Soltani says, "to uniquely identify people and track them that [users] will never have enough motivation and incentive to do it to the degree of this multibillion dollar ad tech industry."
So how do you protect your privacy? Get involved and call your congressperson, he says — tell the policymakers that you care about online privacy.
8. Start small and take it one step at a time.
Faced with this landscape, getting a tighter hold on your digital privacy and security can feel daunting. But Galperin has this sound advice: Just do a little bit at a time.
You don't need to make a list of all of your accounts to integrate into a password manager — you can just do each account as you log into it.
Even just doing the basics — strengthening your passwords, turning on two-factor authentication and watching out for scammers — can make your accounts a lot more secure. Then keep going: There are a lot of other steps you might want to take, depending on your needs.
We're going to be on the Internet for a long time. The more each of us understands how our data are collected and used — and how to keep private what we want to keep private — the better, safer and healthier our digital lives will be.
The podcast portion of this episode was produced by Audrey Nguyen. She also contributed research.
We'd love to hear from you. Leave us a voicemail at 202-216-9823, or email us at [email protected] .
For more Life Kit, subscribe to our newsletter .
- Life Kit: Life Skills
- School Guide
- English Grammar Free Course
- English Grammar Tutorial
- Parts of Speech
- Figure of Speech
- Tenses Chart
- Essay Writing
- Email Writing
- NCERT English Solutions
- English Difference Between
- SSC CGL English Syllabus
- SBI PO English Syllabus
- SBI Clerk English Syllabus
- IBPS PO English Syllabus
- IBPS CLERK English Syllabus
800 Words Essay On Internet in English for Students
- 500+ Words Essay on Newspaper in English For Students
- 500+Words Essay on My Hobby in English
- My Aim in Life Essay For Students: 100, 200 & 500 Words Essay
- 500+ Words Essay on Importance of Education in English
- Essay on My Father in English: 300, 500 & 800 Words Essay
- Essay Writing on Cell Phones For Students
- Essay on Science in English: Check 200, 300 & 500 Words Essay
- Essay on My Family: Short, 10 Lines, 100 Words Essay
- 200+ Action Words in English: Know How to Use
- Essay on my Best Friend: 10 Lines, 100 Words, 200 Words Essay
- Essay on My House in English: Check 300, 500 & 800 Words Essay
- Importance of Sports for Students in English
- Essay on Summer Vacation For Students in English: Samples Class 3 to 5
- 70+ New Words in English With Their Meaning
- Essay on My Favourite Book For Students
- Essay on My Favourite Teacher (10 Lines, 100 Words, 200 Words)
- Essay on My Mother: 10 lines, 100 Words and 200 words essay
- A Guide to Writing an Essay for Job Interviews
- Important Questions On Computer Internet For Bank Exam
- Active and Passive Voice Rules for Competitive Exams
- English Grammar : Learn Rules of Grammar and Basics
- 7 Colours of the Rainbow - VIBGYOR
- Difference between Laptop and Tablet
- Parts of Speech: Definitions, Examples & 8 Types
- 12 Months Name in English and Hindi
- Spotting Errors: Verbal Ability Questions and Answers
- Difference between Save and Save As
- Names of Colours - List of Colours Names in English
- Spotting Error Practice Questions Based On English Grammar "Noun"
The internet has transformed the world in ways that were unimaginable just a few decades ago. It has revolutionized how we communicate, access information, conduct business, and even how we entertain ourselves. The internet has become an integral part of our daily lives, and it’s hard to imagine a world without it.
At its core, the Internet is a vast network of interconnected computers and servers that allows for the exchange of information and data across the globe. It was originally conceived as a way for researchers and scientists to share information and collaborate on projects, but it has since evolved into a ubiquitous platform that has permeated every aspect of modern life.
One of the most significant impacts of the internet has been on communication. Before the internet, communication was limited by geography and time zones. People had to rely on physical mail, telephone calls, or face-to-face meetings to communicate with one another. The internet has made communication instantaneous and borderless. With the rise of email, instant messaging, video conferencing, and social media platforms, people can communicate with each other from anywhere in the world, at any time.
The internet has also revolutionized the way we access information. In the past, people had to rely on physical libraries, books, and other printed materials to access information. Today, with the internet, a wealth of information is available at our fingertips. From online encyclopedias to news websites, academic journals, and online databases, the internet has made it possible to access information on virtually any topic imaginable.
Another significant impact of the internet has been on the economy and the way we conduct business. The rise of e-commerce has made it possible for businesses to reach a global market and sell their products and services online. Online shopping has become increasingly popular, and many traditional brick-and-mortar stores have had to adapt to this new reality by establishing an online presence.
Furthermore, the internet has enabled the rise of the gig economy, where people can work as freelancers or contractors for multiple clients and projects simultaneously. This has created new opportunities for individuals to earn a living and has allowed businesses to access a global talent pool.
The internet has also had a profound impact on education. Online learning platforms and distance education programs have made it possible for students to access educational resources and attend classes from anywhere in the world. This has opened up new opportunities for people who may not have had access to traditional educational institutions due to geographical or financial constraints.
However, the internet has also brought with it a number of challenges and concerns. One of the biggest concerns is privacy and security. With so much personal information being shared online, there is a risk of data breaches and cyber attacks. Companies and individuals need to be vigilant about protecting their personal information and implementing strong cybersecurity measures.
Another concern is the spread of misinformation and fake news. The internet has made it easier for anyone to publish and share information, regardless of its accuracy or credibility. This has led to the proliferation of fake news and conspiracy theories, which can have serious consequences for individuals and society as a whole.
There is also concern about the impact of the internet on mental health and well-being. The constant exposure to social media and the pressure to curate a perfect online persona can lead to feelings of anxiety, depression, and low self-esteem. Additionally, the addictive nature of the internet and the constant stream of information can contribute to decreased attention spans and difficulty focusing on tasks.
Despite these challenges, the internet has proven to be an invaluable tool that has transformed the way we live, work, and interact with the world around us. It has opened up new opportunities for communication, education, and economic growth, and has made it possible for people to connect and collaborate in ways that were previously unimaginable.
As we move forward, it is important to address the challenges and concerns surrounding the internet while also embracing its potential for innovation and progress. This may involve implementing stronger cybersecurity measures, promoting digital literacy and critical thinking skills, and encouraging responsible and ethical use of the internet.
In conclusion, the internet has had a profound impact on virtually every aspect of modern life. It has revolutionized communication, education, business, and access to information. While it has brought with it a number of challenges and concerns, the internet has proven to be an invaluable tool that has transformed the way we live and interact with the world around us. As we continue to navigate the digital age, it is important to embrace the opportunities that the internet provides while also addressing its challenges and promoting responsible and ethical use.
Uses of Internet
In the 21st century, the internet has become an indispensable part of our daily lives, revolutionizing the way we connect, learn, work, and entertain ourselves. Its multifaceted uses have permeated every aspect of society, bringing about unprecedented convenience and opportunities.
Communication stands out as one of the internet’s most significant uses. Instant messaging, video calls, and social media platforms have transcended geographical barriers, allowing people to stay connected with friends and family across the globe. The internet has turned the world into a global village, fostering a sense of unity and understanding among diverse cultures.
Education has undergone a remarkable transformation due to the internet. Online courses, tutorials, and educational resources have made learning accessible to anyone with an internet connection. Students can pursue degrees, acquire new skills, and access a wealth of information at their fingertips, democratizing education and breaking down traditional barriers to learning.
The internet has also redefined the way we work. Remote collaboration tools, cloud computing, and virtual offices have become essential components of the modern workplace. This shift has not only increased efficiency but has also opened up new opportunities for freelancers and remote workers, contributing to the rise of the gig economy.
In the realm of information, the internet has become an unparalleled resource. Search engines allow us to access vast amounts of information on any topic imaginable. This democratization of information has empowered individuals, encouraging critical thinking and facilitating informed decision-making.
Entertainment has undergone a digital revolution, with streaming services, online gaming, and social media platforms providing endless avenues for amusement. The internet has not only transformed how we consume content but has also given rise to new forms of artistic expression and creativity.
In conclusion, the internet’s uses are multifaceted and far-reaching, impacting every facet of our lives. From connecting people across the globe to revolutionizing education, work, and entertainment, the internet continues to be a transformative force, shaping the present and influencing the future. As we navigate the digital landscape, it is essential to harness the potential of the internet responsibly, ensuring that it remains a force for positive change in the years to come.
Convenience Due to Internet
The advent of the internet has ushered in an era of unprecedented convenience, transforming the way we live, work, and interact with the world. In our fast-paced lives, the internet has become a cornerstone of efficiency and ease, offering a multitude of conveniences that have reshaped our daily routines.
Communication is perhaps the most obvious and impactful convenience brought about by the internet. Instant messaging, email, and social media platforms have revolutionized the way we connect with others. Whether it’s staying in touch with loved ones, collaborating with colleagues, or reaching out to friends across the globe, the internet has made communication instantaneous and seamless.
The convenience of online shopping has fundamentally altered the retail landscape. With just a few clicks, consumers can browse, compare prices, and purchase a vast array of products from the comfort of their homes. The rise of e-commerce platforms has not only made shopping more convenient but has also introduced the concept of doorstep delivery, saving time and eliminating the need for physical store visits.
Information retrieval has been transformed by the internet’s vast repository of knowledge. Search engines provide instant access to information on any conceivable topic, enabling users to quickly find answers, conduct research, and stay informed. This ease of information retrieval has empowered individuals, making knowledge more accessible than ever before.
The workplace has undergone a paradigm shift with the internet, enabling remote work and flexible schedules. Online collaboration tools, cloud computing, and virtual communication platforms have made it possible for individuals to work from virtually anywhere, reducing the constraints of traditional office settings and commuting.
Entertainment has also become infinitely more convenient through streaming services, online gaming, and digital media platforms. The ability to access a diverse range of content on-demand has given consumers unprecedented control over their entertainment choices, eliminating the need to adhere to fixed schedules or physical media.
In conclusion, the internet has woven a tapestry of convenience into the fabric of our lives. From streamlined communication and effortless online shopping to boundless information access and flexible work arrangements, the conveniences offered by the internet have become integral to our modern existence. As we navigate this digital landscape, the ongoing evolution of internet technologies continues to enhance and redefine the meaning of convenience in our interconnected world.
Also Read: Rabindranath Tagore Essay in English For Students 500+ Words Essay on Mother Teresa in English For Students Pandit Jawaharlal Nehru Essay in English For Students APJ Abdul Kalam Essay For Students: Check 500 Words Essay
Essay On Internet- FAQs
What is internet short essay.
In the modern time, internet has become is one of the most powerful and interesting tools all across the world. The Internet is a network of networks and collection of many services and resources which benefits us in various ways. Using internet we can access World Wide Web from any place.
What is Internet in 150 words?
The internet is the most recent man-made creation that connects the world. The world has narrowed down after the invention of the internet. It has demolished all boundaries, which were the barriers between people and has made everything accessible. The internet is helpful to us in different ways.
What is internet 100 words?
A. The internet, a recent man-made marvel, has brought the world closer. It has shattered all barriers and made everything accessible. The internet serves us in countless ways, from sharing information with people across the world to staying connected with our loved ones.
Please Login to comment...
Similar reads.
- English Blogs
- School English
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- Share full article
Advertisement
Supported by
The Battle for Digital Privacy Is Reshaping the Internet
As Apple and Google enact privacy changes, businesses are grappling with the fallout, Madison Avenue is fighting back and Facebook has cried foul.

By Brian X. Chen
Listen to This Article
SAN FRANCISCO — Apple introduced a pop-up window for iPhones in April that asks people for their permission to be tracked by different apps.
Google recently outlined plans to disable a tracking technology in its Chrome web browser.
And Facebook said last month that hundreds of its engineers were working on a new method of showing ads without relying on people’s personal data.
The developments may seem like technical tinkering, but they were connected to something bigger: an intensifying battle over the future of the internet. The struggle has entangled tech titans, upended Madison Avenue and disrupted small businesses. And it heralds a profound shift in how people’s personal information may be used online, with sweeping implications for the ways that businesses make money digitally.
At the center of the tussle is what has been the internet’s lifeblood: advertising .
More than 20 years ago, the internet drove an upheaval in the advertising industry. It eviscerated newspapers and magazines that had relied on selling classified and print ads, and threatened to dethrone television advertising as the prime way for marketers to reach large audiences.
Instead, brands splashed their ads across websites, with their promotions often tailored to people’s specific interests. Those digital ads powered the growth of Facebook, Google and Twitter, which offered their search and social networking services to people without charge. But in exchange, people were tracked from site to site by technologies such as “ cookies, ” and their personal data was used to target them with relevant marketing.
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data collection. Apple, citing the mantra of privacy, has rolled out tools that block marketers from tracking people. Google, which depends on digital ads, is trying to have it both ways by reinventing the system so it can continue aiming ads at people without exploiting access to their personal data.

If personal information is no longer the currency that people give for online content and services, something else must take its place. Media publishers, app makers and e-commerce shops are now exploring different paths to surviving a privacy-conscious internet, in some cases overturning their business models. Many are choosing to make people pay for what they get online by levying subscription fees and other charges instead of using their personal data.
Jeff Green, the chief executive of the Trade Desk, an ad-technology company in Ventura, Calif., that works with major ad agencies, said the behind-the-scenes fight was fundamental to the nature of the web.
“The internet is answering a question that it’s been wrestling with for decades, which is: How is the internet going to pay for itself?” he said.
The fallout may hurt brands that relied on targeted ads to get people to buy their goods. It may also initially hurt tech giants like Facebook — but not for long. Instead, businesses that can no longer track people but still need to advertise are likely to spend more with the largest tech platforms, which still have the most data on consumers.
David Cohen, chief executive of the Interactive Advertising Bureau, a trade group, said the changes would continue to “drive money and attention to Google, Facebook, Twitter.”
The shifts are complicated by Google’s and Apple’s opposing views on how much ad tracking should be dialed back. Apple wants its customers, who pay a premium for its iPhones, to have the right to block tracking entirely. But Google executives have suggested that Apple has turned privacy into a privilege for those who can afford its products.
For many people, that means the internet may start looking different depending on the products they use. On Apple gadgets, ads may be only somewhat relevant to a person’s interests, compared with highly targeted promotions inside Google’s web. Website creators may eventually choose sides, so some sites that work well in Google’s browser might not even load in Apple’s browser, said Brendan Eich, a founder of Brave, the private web browser.
“It will be a tale of two internets,” he said.
Businesses that do not keep up with the changes risk getting run over. Increasingly, media publishers and even apps that show the weather are charging subscription fees, in the same way that Netflix levies a monthly fee for video streaming. Some e-commerce sites are considering raising product prices to keep their revenues up.
Consider Seven Sisters Scones, a mail-order pastry shop in Johns Creek, Ga., which relies on Facebook ads to promote its items. Nate Martin, who leads the bakery’s digital marketing, said that after Apple blocked some ad tracking, its digital marketing campaigns on Facebook became less effective. Because Facebook could no longer get as much data on which customers like baked goods, it was harder for the store to find interested buyers online.
“Everything came to a screeching halt,” Mr. Martin said. In June, the bakery’s revenue dropped to $16,000 from $40,000 in May.
Sales have since remained flat, he said. To offset the declines, Seven Sisters Scones has discussed increasing prices on sampler boxes to $36 from $29.
Apple declined to comment, but its executives have said advertisers will adapt. Google said it was working on an approach that would protect people’s data but also let advertisers continue targeting users with ads.
Since the 1990s, much of the web has been rooted in digital advertising. In that decade, a piece of code planted in web browsers — the “cookie” — began tracking people’s browsing activities from site to site. Marketers used the information to aim ads at individuals, so someone interested in makeup or bicycles saw ads about those topics and products.
After the iPhone and Android app stores were introduced in 2008, advertisers also collected data about what people did inside apps by planting invisible trackers. That information was linked with cookie data and shared with data brokers for even more specific ad targeting.
The result was a vast advertising ecosystem that underpinned free websites and online services. Sites and apps like BuzzFeed and TikTok flourished using this model. Even e-commerce sites rely partly on advertising to expand their businesses.
But distrust of these practices began building. In 2018, Facebook became embroiled in the Cambridge Analytica scandal, where people’s Facebook data was improperly harvested without their consent. That same year, European regulators enacted the General Data Protection Regulation , laws to safeguard people’s information. In 2019, Google and Facebook agreed to pay record fines to the Federal Trade Commission to settle allegations of privacy violations.
In Silicon Valley, Apple reconsidered its advertising approach. In 2017, Craig Federighi, Apple’s head of software engineering, announced that the Safari web browser would block cookies from following people from site to site.
“It kind of feels like you’re being tracked, and that’s because you are,” Mr. Federighi said. “No longer.”
Last year, Apple announced the pop-up window in iPhone apps that asks people if they want to be followed for marketing purposes. If the user says no, the app must stop monitoring and sharing data with third parties.
That prompted an outcry from Facebook , which was one of the apps affected. In December, the social network took out full-page newspaper ads declaring that it was “standing up to Apple” on behalf of small businesses that would get hurt once their ads could no longer find specific audiences.
“The situation is going to be challenging for them to navigate,” Mark Zuckerberg, Facebook’s chief executive, said.
Facebook is now developing ways to target people with ads using insights gathered on their devices, without allowing personal data to be shared with third parties. If people who click on ads for deodorant also buy sneakers, Facebook can share that pattern with advertisers so they can show sneaker ads to that group. That would be less intrusive than sharing personal information like email addresses with advertisers.
“We support giving people more control over how their data is used, but Apple’s far-reaching changes occurred without input from the industry and those who are most impacted,” a Facebook spokesman said.
Since Apple released the pop-up window, more than 80 percent of iPhone users have opted out of tracking worldwide, according to ad tech firms. Last month, Peter Farago, an executive at Flurry, a mobile analytics firm owned by Verizon Media, published a post on LinkedIn calling the “time of death” for ad tracking on iPhones.
At Google, Sundar Pichai, the chief executive, and his lieutenants began discussing in 2019 how to provide more privacy without killing the company’s $135 billion online ad business. In studies, Google researchers found that the cookie eroded people’s trust. Google said its Chrome and ad teams concluded that the Chrome web browser should stop supporting cookies.
But Google also said it would not disable cookies until it had a different way for marketers to keep serving people targeted ads. In March, the company tried a method that uses its data troves to place people into groups based on their interests, so marketers can aim ads at those cohorts rather than at individuals. The approach is known as Federated Learning of Cohorts, or FLOC.
Plans remain in flux. Google will not block trackers in Chrome until 2023 .
Even so, advertisers said they were alarmed.
In an article this year, Sheri Bachstein, the head of IBM Watson Advertising, warned that the privacy shifts meant that relying solely on advertising for revenue was at risk. Businesses must adapt, she said, including by charging subscription fees and using artificial intelligence to help serve ads.
“The big tech companies have put a clock on us,” she said in an interview.
Kate Conger contributed reporting.
Brian X. Chen is the lead consumer technology writer for The Times. He reviews products and writes Tech Fix , a column about the social implications of the tech we use. Before joining The Times in 2011, he reported on Apple and the wireless industry for Wired. More about Brian X. Chen
Tech Fix: Solving Your Tech Problems
Switching From iPhone to Android: Even if you manage to ditch your iPhone, Apple’s hooks are still there .
Trying Meta’s Smart Glasses: What happens when a columnist and a reporter use A.I. Ray-Bans to scan groceries, monuments and zoo animals? Hilarity, wonder and lots of mistakes ensued .
Ditch Your Wallet: Using your phone as a digital wallet is attainable , but it requires preparation and some compromise.
Managing Subscriptions: The dream of streaming — watch what you want, whenever you want, for a sliver of the price of cable! — is coming to an end as prices go up. Here’s how to juggle all your subscriptions and even cancel them .
Apple’s Vision Pro: The new headset teaches a valuable lesson about the cost of tech products: The upsells and add-ons will get you .
Going Old School: Retro-photography apps that mimic the appearance of analog film formats make your digital files seem like they’re from another era. Here’s how to use them .
Numbers, Facts and Trends Shaping Your World
Read our research on:
Full Topic List
Regions & Countries
- Publications
- Our Methods
- Short Reads
- Tools & Resources
Read Our Research On:
Americans’ complicated feelings about social media in an era of privacy concerns
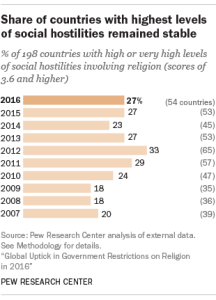
Amid public concerns over Cambridge Analytica’s use of Facebook data and a subsequent movement to encourage users to abandon Facebook , there is a renewed focus on how social media companies collect personal information and make it available to marketers.
Pew Research Center has studied the spread and impact of social media since 2005, when just 5% of American adults used the platforms. The trends tracked by our data tell a complex story that is full of conflicting pressures. On one hand, the rapid growth of the platforms is testimony to their appeal to online Americans. On the other, this widespread use has been accompanied by rising user concerns about privacy and social media firms’ capacity to protect their data.
All this adds up to a mixed picture about how Americans feel about social media. Here are some of the dynamics.
People like and use social media for several reasons
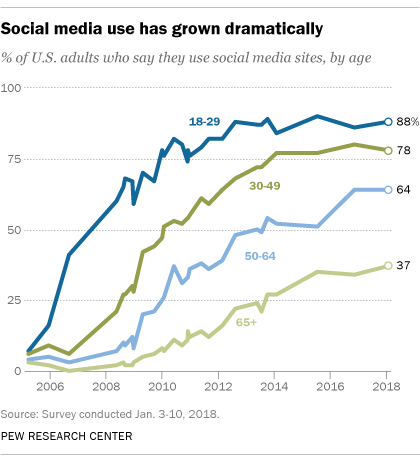
About seven-in-ten American adults (69%) now report they use some kind of social media platform (not including YouTube) – a nearly fourteenfold increase since Pew Research Center first started asking about the phenomenon. The growth has come across all demographic groups and includes 37% of those ages 65 and older.
The Center’s polls have found over the years that people use social media for important social interactions like staying in touch with friends and family and reconnecting with old acquaintances. Teenagers are especially likely to report that social media are important to their friendships and, at times, their romantic relationships .
Beyond that, we have documented how social media play a role in the way people participate in civic and political activities, launch and sustain protests , get and share health information , gather scientific information , engage in family matters , perform job-related activities and get news . Indeed, social media is now just as common a pathway to news for people as going directly to a news organization website or app.
Our research has not established a causal relationship between people’s use of social media and their well-being. But in a 2011 report, we noted modest associations between people’s social media use and higher levels of trust, larger numbers of close friends, greater amounts of social support and higher levels of civic participation.
People worry about privacy and the use of their personal information
While there is evidence that social media works in some important ways for people, Pew Research Center studies have shown that people are anxious about all the personal information that is collected and shared and the security of their data.
Overall, a 2014 survey found that 91% of Americans “agree” or “strongly agree” that people have lost control over how personal information is collected and used by all kinds of entities. Some 80% of social media users said they were concerned about advertisers and businesses accessing the data they share on social media platforms, and 64% said the government should do more to regulate advertisers.
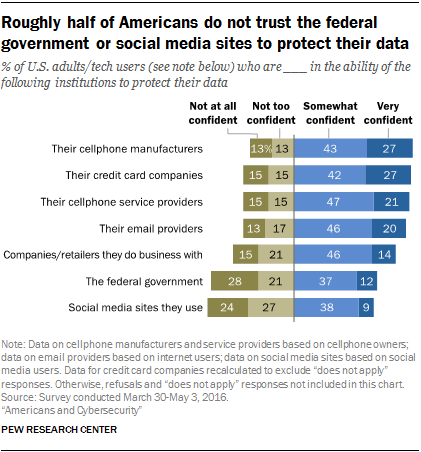
Another survey last year found that just 9% of social media users were “very confident” that social media companies would protect their data . About half of users were not at all or not too confident their data were in safe hands.
Moreover, people struggle to understand the nature and scope of the data collected about them. Just 9% believe they have “a lot of control” over the information that is collected about them, even as the vast majority (74%) say it is very important to them to be in control of who can get information about them.
Six-in-ten Americans (61%) have said they would like to do more to protect their privacy. Additionally, two-thirds have said current laws are not good enough in protecting people’s privacy, and 64% support more regulation of advertisers.
Some privacy advocates hope that the European Union’s General Data Protection Regulation , which goes into effect on May 25, will give users – even Americans – greater protections about what data tech firms can collect, how the data can be used, and how consumers can be given more opportunities to see what is happening with their information.
People’s issues with the social media experience go beyond privacy
In addition to the concerns about privacy and social media platforms uncovered in our surveys, related research shows that just 5% of social media users trust the information that comes to them via the platforms “a lot.”
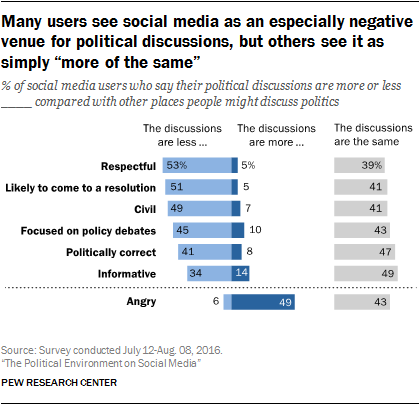
Moreover, social media users can be turned off by what happens on social media. For instance, social media sites are frequently cited as places where people are harassed . Near the end of the 2016 election campaign, 37% of social media users said they were worn out by the political content they encountered, and large shares said social media interactions with those opposed to their views were stressful and frustrating. Large shares also said that social media interactions related to politics were less respectful, less conclusive, less civil and less informative than offline interactions.
A considerable number of social media users said they simply ignored political arguments when they broke out in their feeds. Others went steps further by blocking or unfriending those who offended or bugged them.
Why do people leave or stay on social media platforms?
The paradox is that people use social media platforms even as they express great concern about the privacy implications of doing so – and the social woes they encounter. The Center’s most recent survey about social media found that 59% of users said it would not be difficult to give up these sites, yet the share saying these sites would be hard to give up grew 12 percentage points from early 2014.
Some of the answers about why people stay on social media could tie to our findings about how people adjust their behavior on the sites and online, depending on personal and political circumstances. For instance, in a 2012 report we found that 61% of Facebook users said they had taken a break from using the platform. Among the reasons people cited were that they were too busy to use the platform, they lost interest, they thought it was a waste of time and that it was filled with too much drama, gossip or conflict.
In other words, participation on the sites for many people is not an all-or-nothing proposition.
People pursue strategies to try to avoid problems on social media and the internet overall. Fully 86% of internet users said in 2012 they had taken steps to try to be anonymous online. “Hiding from advertisers” was relatively high on the list of those they wanted to avoid.
Many social media users fine-tune their behavior to try to make things less challenging or unsettling on the sites, including changing their privacy settings and restricting access to their profiles. Still, 48% of social media users reported in a 2012 survey they have difficulty managing their privacy controls.
After National Security Agency contractor Edward Snowden disclosed details about government surveillance programs starting in 2013, 30% of adults said they took steps to hide or shield their information and 22% reported they had changed their online behavior in order to minimize detection.
One other argument that some experts make in Pew Research Center canvassings about the future is that people often find it hard to disconnect because so much of modern life takes place on social media. These experts believe that unplugging is hard because social media and other technology affordances make life convenient and because the platforms offer a very efficient, compelling way for users to stay connected to the people and organizations that matter to them.
Note: See topline results for overall social media user data here (PDF).
- Emerging Technology
- Online Privacy & Security
- Privacy Rights
- Social Media
- Technology Policy Issues

Lee Rainie is director of internet and technology research at Pew Research Center
Many Americans think generative AI programs should credit the sources they rely on
Americans’ use of chatgpt is ticking up, but few trust its election information, q&a: how we used large language models to identify guests on popular podcasts, computer chips in human brains: how americans view the technology amid recent advances, striking findings from 2023, most popular.
1615 L St. NW, Suite 800 Washington, DC 20036 USA (+1) 202-419-4300 | Main (+1) 202-857-8562 | Fax (+1) 202-419-4372 | Media Inquiries
Research Topics
- Age & Generations
- Coronavirus (COVID-19)
- Economy & Work
- Family & Relationships
- Gender & LGBTQ
- Immigration & Migration
- International Affairs
- Internet & Technology
- Methodological Research
- News Habits & Media
- Non-U.S. Governments
- Other Topics
- Politics & Policy
- Race & Ethnicity
- Email Newsletters
ABOUT PEW RESEARCH CENTER Pew Research Center is a nonpartisan fact tank that informs the public about the issues, attitudes and trends shaping the world. It conducts public opinion polling, demographic research, media content analysis and other empirical social science research. Pew Research Center does not take policy positions. It is a subsidiary of The Pew Charitable Trusts .
Copyright 2024 Pew Research Center
Terms & Conditions
Privacy Policy
Cookie Settings
Reprints, Permissions & Use Policy
- Galileo Galilei: sample essay
- Kids and violence: sample essay
- Sample essay about Muhammad Ali
- Learning for adults: essay sample
- Breast cancer: sample essay
- Ulysses S. Grant: essay sample
- Sample essay about muckrakers
- Teen pragnency: essay sample
- Sample essay aabout a soul
- Paper sample about happiness
- Schizophrenia: essay sample
- Essay example about death penalty
- Sample paper about corruption
- Gender on business: sample essay
- Mozart: essay sample
- An essay sample on Illicit traffic in drugs
- Analyzing the generation gap
- Pit bulls and fighting
- Reasons for a belief in God
- Italian dessert Tiramisu
- Terrorism in Pakistan
- Lives on the boundary
- History of fingerprints
- If I were Lyndon Johnson
- The Western expansion
- Workplace violence
- Compare & contrast paper ideas
- College cause and effect essay topics
- Good descriptive paper topics
- GED paper topics
- Catchy essay paper topics
- Capital punishment essay topics
- Ideas for your descriptive paper
- Choosing topics for a law paper
- Death of a Salesman essay ideas
- Huckleberry Finn: argument paper topics
- College persuasive essay topic ideas
- Unique illustration essay topic prompts
- Topics for an essay on Nicholas Sparks
- Business cause and effect essay topics
- Informative essay topic ideas
- Choosing topics for a profile essay
- Argumentative essay topics on politics
- Selecting paper topics about the military
- Process analysis essay topics
- College essay topics in accounting
- Ideas about violent video games
- Argumentative paper topic suggestions
- Offbeat topic ideas on Macbeth
- Essay prompts on Streetcar Named Desire
- Selection of topics about Dorian Gray
- Argumentative essay ideas on bullying
- 23 topics on a Midsummer Night’s Dream
- Essay ideas on yourself in 10 years
- Choosing topics about global warming
- Environmental science essay prompts
- Argumentative essay ideas on psychology
- Picking topics about religion & belief
- Best essay ideas on euthanasia
- Writing service
- Essay on a book
- Writing companies
writing rogue
Acute essay topics on internet privacy: 20 expert suggestions.
Internet privacy is a very important topic nowadays. Many people are afraid that they’re watched by the government through the Internet and these suspicions aren’t always baseless. If your teacher assigned you to write an essay on Internet privacy, there are many narrow topics that you may choose from.
Topics on Internet Privacy
- The history of Internet privacy.
- Levels of Internet privacy.
- Risks to Internet privacy.
- Internet privacy and HTTP cookies.
- Device fingerprinting and Internet privacy.
- Photos in social networks and Internet privacy.
- Search engines and Internet privacy.
- Reducing the risks to Internet privacy.
- Real life implications related to Internet privacy.
- Global policies about Internet privacy.
- User-generated content and Internet privacy costs.
- Internet privacy and social media.
- Effects of privacy seals and warnings on online privacy behavior.
- Damages for Internet privacy violations.
- Internet privacy and politics.
- The installment of malware on your computer by major companies.
- The lack of regulation in Internet privacy.
- Internet privacy and intellectual property.
- Weak passwords and Internet privacy.
- The future of Internet privacy.
Writing an Essay
A good topic isn’t enough to get an excellent mark for your work. You should conduct thorough research and present your points or arguments properly. Ask your teacher about sources that you should use to succeed. Acquire these sources and find there, at least, three points that can support your main idea. It’s important to defend your statements using factual evidence rather than just your opinion. Before you start writing your paper, it’s advisable to make a good outline. This will help you structure your text properly. Compose your essay using appropriate writing techniques and transitions between paragraphs to make your text flow smoothly. Proofread your paper to eliminate errors made during the process of writing. Come up with your title after your paper has been complete to make it 100% relevant to the text.
Getting Help
If you aren’t sure that you’ll be able to write an impressive paper by yourself, you should ask other people to help you. If you cannot spend money on this, just regularly visit your instructor and ask them to consult you about your next steps. If you can pay for assistance, you may hire a professional tutor who will teach you how to deal with academic assignments. You may also contact essay writing companies to compose papers for you in exchange for payment. Services of professional agencies won’t disappoint you.
Writing Ideas
- Personal statement writing guide
- Boosting geography essay writing skills
- Literary essay about Animal Farm
- Document based question essay
- How to settle down with a good service
- Writing about Tommy Hilfiger
- Paper writing help: disadvantages
- Looking for a cheap custom essay
- Writing a literary essay conclusion
- Informative explanatory essay
- Essay about school environment
Writing help
Popular essay writing service for generation Z - Zessay.com - very quality service and nice website.
Hints for beginners
- Ways to improve your grades
- Pay someone to write my paper
- Free pesuasive paper
- Life without technology paper
- Finding trusted paper writing help
- Long essay about summer vacation
- Finding a paper sample about market
- Pros and cons of writing services
- Where to buy cheap papers?
- How to complete an IB literary essay
Paper topics
- Persuasive essay topics for 5th grade
- High school paper ideas
- Choosing definition essay topics
- Informative essay topics on caffeine
- Medical argumentative essay topics
- Picking topics related to entertainment
- Essay topics on Scottish independence
- Good ideas about Internet privacy
Apr 27, 2024 © WritingRogue.com. | Developing Strong Writing Habits For Students
Essay On Internet for Students and Children
500+ words essay on internet.
We live in the age of the internet. Also, it has become an important part of our life that we can’t live without it. Besides, the internet is an invention of high-end science and modern technology . Apart from that, we are connected to internet 24×7. Also, we can send big and small messages and information faster than ever. In this essay on the Internet, we are going to discuss various things related to the internet.

Reach of Internet
It is very difficult to estimate the area that the internet cover. Also, every second million people remain connected to it with any problem or issue. Apart from that, just like all the things the internet also has some good and bad effect on the life of people. So the first thing which we have to do is learn about the good and bad effect of the internet.
Good effects of the internet mean all those things that the internet make possible. Also, these things make our life easier and safer.
Bad effects of the internet mean all those things that we can no longer do because of the internet. Also, these things cause trouble for oneself and others too.
You can access in any corner of the world. Also, it is very easy to use and manage. In today’s world, we cannot imagine our life without it.
Get the huge list of more than 500 Essay Topics and Ideas
Uses Of Internet
From the time it first came into existence until now the internet has completed a long journey. Also, during this journey, the internet has adopted many things and became more user-friendly and interactive. Besides, every big and small things are available on internet and article or material that you require can be obtainable from internet.

Tim Berners-Lee can be called one of the main father of internet as he invented/discovered the WWW (World Wide Web) which is used on every website. Also, there are millions of pages and website on the internet that it will take you years to go through all of them.
The Internet can be used to do different things like you can learn, teach, research, write, share, receive, e-mail , explore, and surf the internet.
Read Essay on Technology here
Convenience Due To Internet
Because of internet, our lives have become more convenient as compared to the times when we don’t have internet. Earlier, we have to stand in queues to send mails (letters), for withdrawing or depositing money, to book tickets, etc. but after the dawn of the internet, all these things become quite easy. Also, we do not have to waste our precious time standing in queues.
Also, the internet has contributed a lot to the environment as much of the offices (government and private), school and colleges have become digital that saves countless paper.
Although, there is no doubt that the internet had made our life easier and convenient but we can’t leave the fact that it has caused many bigger problems in the past. And with the speed, we are becoming addict to it a day in will come when it will become our basic necessity.
{ “@context”: “https://schema.org”, “@type”: “FAQPage”, “mainEntity”: [ { “@type”: “Question”, “name”: “What are the limitation of internet?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Although internet can help you with anything but there are certain limitation to it. First of it does not have a physical appearance. Secondly, it does not have emotions and thirdly, it can’t send you to a place where you can’t go (physically).” } }, { “@type”: “Question”, “name”: “What is the ideal age for using internet?”, “acceptedAnswer”: { “@type”: “Answer”, “text”: “Nowadays everybody from small kids to adult is internet addicts. So it is difficult to decide an ideal age for using internet. However, according to researches using internet from an early age can cause problems in the child so internet usage of small children should be controlled or banned.” } } ] }
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App


1 Minute Speech on Internet Privacy In English
A very good morning to one and all present here. Today, I’ll be giving a short speech on the topic of Internet Privacy.
We, as youngsters, are no strangers to the fact that privacy is an important need that is to be protected in all spectrums of life. Privacy becomes even more important when it pertains to the Internet, a place where this very thing we want to protect become breached.
I believe it is safe to assume that all of us here must be in some social media platform or the other. In all these areas, internet privacy is important as without this, our personal details such as our names, our birthdays, and our emails could be visible to random strangers without our consent. In a world filled with perverts and hackers, this internet privacy is important as even more significant information such as bank accounts and other private information could get leaked.
Social media platforms thus are now amping up security with regards to this.
Related Posts:
- The Last Visit Poem by Taufiq Rafat Summary, Notes and Line by Line Explanation in English
- Short Speech on Social Media in English
- Michael Poem by William Wordsworth Summary, Notes and Line by Line Explanation in English
- Common Conversational Phrases in English [List of 939]
- Fear Poem by Gabriela Mistral Summary, Notes and Line by Line Explanation in English for Students
- Privacy Policy
Government Internet Surveillance: Privacy Threat Essay
Introduction, the internet and surveillance, us government surveillance, surveillance efforts a threat to privacy and civil rights, justification for surveillance, discussion and conclusion.
The internet is the most important invention of the twentieth century and it has dramatically transformed human life. This invention has greatly increased the speed and efficiency with which communication occurs. Its unrivalled benefits in information processing have made this technology a part of most aspects of modern-daily activities.
Boghosian (2013) notes that while the internet plays a major role in improving life in our society, some sinister applications of this invention undermine privacy and civil rights. Perhaps the most troubling applications of the internet in current times are the mass surveillance efforts by the US government. This paper will argue that government internet surveillance is a threat to the privacy and civil rights of US citizens and it must therefore be mitigated.
Government surveillance has existed in various forms for centuries. Through this activity, the government has been able to obtain valuable public and secret information and act on it to aid governance. The internet age has dramatically increased the ability of government to engage in surveillance.
To begin with, the internet has become the most common medium of communication for many people. By monitoring this single communication network, the government has access to virtually all information that is communicated electronically including email habits, credit card, bank records, and phone records (Regan, 2014). The advancement in storage technology has contributed to the pervasive surveillance carried out by the US.
Today, the data that can be stored is nearly infinite due to the tremendous growth in storage capacity and the decline in storage prices. Intelligence agencies are therefore able to collect all available data since it is cheaper and easier than trying to determine what data should be stored and what should be ignored. At the same time, sophisticated computer algorithms make it possible for government agencies to analyze large amounts of data and derive meaning from it.
Scherer (2013) states that while electronic intelligence in the US historically focused on foreign governments, the events of 9/11 led to an increased focus on American citizens. Starting from that year, the NSA turned inward and shifted its focus to include private individuals. This shift was prompted by the understanding that the perpetrators of the 9/11 attacks had resided in the US and made their plans while living in the country. Since then, the government has engaged in widespread surveillance of its citizens in an attempt to prevent crime.
The internet has made it possible for the government to engage in mass surveillance. Through security apparatus such as the NSA, the American government can collect and analyze vast quantities of data about its citizens. These activities often take place without the consent or knowledge of the individual.
Revelations by Snowden showed that the government engaging in surveillance at a scale that a majority of society did not even think was possible (Scherer, 2013). Through US dedicates more than $52.6 billion each year to run a massive secret national security apparatus. This apparatus includes the NSA, which has over 30,000 employees and gathers and stores not only phone records in the US but also metadata on internet traffic.
To increase its surveillance abilities, the US government has engaged in programs aimed at influencing IT companies to provide the NSA with a back door to encrypted communications. Scherer (2013) documents that through such a program, the government denies private citizens of their right to create unbreakable encryption software.
Wide scale surveillance by the government has harmed the privacy rights of US citizens. Government internet surveillance efforts result in a violation of individual privacy as the government intercepts the personal information and communication from US citizens. For privacy to exist, an individual has to have control over himself and the information he shares with others.
Boghosian (2013) notes that attempts to safeguard the privacy of American have been compromised by the government’s demand for unrestricted access to information. Under the Patriot Act, the government has access to a wide array of personal information. Through the National Security Administration (NSA), the government has engaged in large-scale data collection on US citizens.
This data is then analyzed in an effort to identify suspects. However, this data can be used to obtain more information about the private lives of Americans thus violating individual privacy.
The right to free speech and association are affected by the existence of extensive internet surveillance programs. According to the freedom of speech right, an individual is entitled to communicate his personal opinion or ideas with others without the fear of repercussions. The freedom of association guarantees an individual the right to relate with persons or groups of his choosing without any external inhibitions.
Purkayastha and Bailey (2014) observe that mass surveillance undermines free speech as individuals may face retaliation action if they are critical of the government. The government may engage in steps to silence critics who are identified through the surveillance efforts. Private Citizens concerned that their communications may be under surveillance are likely to avoid making their opinions public out of fear of government reprisal. Internet surveillance will therefore have led to the violation of the civil rights of these US citizens.
Government surveillance violates the location privacy of an individual. Boghosian (2013) defines location privacy as the right of an American to move in public without being tracked on monitored. This right is violated by unrestricted surveillance by the government. By monitoring Global Positioning System (GPS) devices, the government can record the precise movement of an individual. His/her exact location at any time can be record and stored helping to create an elaborate profile on the individual’s movement patterns.
The Fourth Amendment, which guarantees Americans protection against unreasonable searchers and seizures is violated by the undiscriminating internet surveillance. Through this mass collection and scrutinizing of personal information, the government violates the requirements of the Fourth Amendment. Scherer (2013) confirms that unreasonable searches that take place with no justification characterize the internet surveillance carried out by the government. The government collects data from all citizens and then analyzes this information in the hope of finding patterns that will help identify criminals.
The US government has justified its aggressive surveillance activities as necessary efforts for the enhancement of national security. In a speech on the importance of surveillance, the US President Barack Obama asserts that these activities enable law enforcement officers to detect terrorists and prevent them from carrying out attacks against the US (Obama, 2014). Even ordinary US citizens recognize this positive role of internet monitoring.
While most Americans are opposed to government surveillance, there is a recognition that the government might need to engage in monitoring efforts in order to safeguard the homeland. Scherer (2013) notes that according to polls, a majority of Americans show continued willingness to give up some of their rights to privacy as part of efforts to combat terrorism.
Government surveillance of the internet helps to protect citizens from the dangers that an abuse of the internet can cause. The internet provides individual users with significant power due to the wide range of information contained on the network and the communication efficiency.
These attributes can be exploited for wrong purposes if the government does not police the network. Seidler (2013) confirms that the government might be forced to carry out secret activities for the benefit of its citizens. Through surveillance, the government can identify questionable activities by citizens and engage in further investigation. Such efforts might lead to the discovery and stopping of criminal elements before they carry out crime.
Under the Obama Administration, the US has continued and even expanded the electronic surveillance implemented by the Bush administration. The justification for this is that the surveillance regime is integral to protecting the US against Foreign and Homegrown terrorists. Even so, Obama (2014) admits that the prevalent internet monitoring creates a potential for abuse. Action therefore needs to be taken against government surveillance on its citizens.
According to the renowned American whistleblower, Edward Snowden, the important players in this issue include “the public, the technologist community, the U.S. courts, Congress and the Executive Branch” (Scherer, 2013, p.81). These bodies need to deliberate on the future of the country if government surveillance is allowed to go on uninhibited.
As it currently stands, Internet surveillance has given the government intrusive police power that can be used against innocent civilians. The liberties of Americans have been constricted by the deployment of the surveillance infrastructure. Action needs to be taken to address these issues and restore the privacy and civil liberties guaranteed to American citizens by the US Constitution.
Boghosian, H. (2013). The Business of Surveillance. Human Rights, 39 (3), 2-23.
Obama, B. (2014). Remarks by the President on Review of Signals Intelligence . Web.
Purkayastha, P., & Bailey, R. (2014). U.S. Control of the Internet Problems Facing the Movement to International Governance. Independent Socialist Magazine, 66 (3), 103-127.
Regan, L. (2014). Electronic Communications Surveillance. Independent Socialist Magazine, 66 (3), 32-42.
Scherer, M. (2013). Number Two Edward Snowden The Dark Prophet. Time, 182 (26), 78-89.
Seidler, N. (2013). A perspective on principles for Internet surveillance .
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2024, February 19). Government Internet Surveillance: Privacy Threat. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/
"Government Internet Surveillance: Privacy Threat." IvyPanda , 19 Feb. 2024, ivypanda.com/essays/government-internet-surveillance-privacy-threat/.
IvyPanda . (2024) 'Government Internet Surveillance: Privacy Threat'. 19 February.
IvyPanda . 2024. "Government Internet Surveillance: Privacy Threat." February 19, 2024. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/.
1. IvyPanda . "Government Internet Surveillance: Privacy Threat." February 19, 2024. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/.
Bibliography
IvyPanda . "Government Internet Surveillance: Privacy Threat." February 19, 2024. https://ivypanda.com/essays/government-internet-surveillance-privacy-threat/.
- Civilization and Its Impact on Inequality
- Do We Need the NSA?
- The Human Right to Privacy: Microsoft and the NSA
- National Security Agency: Joint Capes Brief
- Network System Administrator Responsibilities
- The National Security Agency' Surveillance Program
- PRISM Program: Freedom v. Order
- National Security Agency and Privacy Violation
- Collecting the phone data logs of all citizens
- American National Security and Technology Evolution
- Has E-Government Failed?
- E-Government and Technological Change
- E-Government (M-Government) in Dubai
- Review and Analysis of the U.S. and UK Government Websites
- E-Government Initiatives: A Critical Discussion
My Study Times
Education through Innovation
Internet Privacy Article, Essay , Speech
- Why Internet Privacy Necessary ?
Read Also : Essay on Internet
What is Internet Privacy ?
Internet privacy is the privacy and security level of personal data published via the internet. In other words we can call it as online privacy. Internet privacy is cause for concern because nowadays most of the work of purchases ,communication, gaming , business are done online. In real life, we do not share our personal info with a stranger. We choose what to reveal while dealing with a stranger in any way. In the same way, it is important to consider one’s privacy while dealing businesses online. There are real people working behind inanimate computers or android devices. And that must be considered or checked for sure when a person is working on computer. nowadays since internet is affordable and the children learn to handle it very soon, that makes it more than an important reason for taking internet privacy as a prime matter.

Types of Cracking Internet Privacy
Malware using short definitions , phishing is an internet hacking activity used to secure user data ,including username, password, etc.pharming is used to redirect a legitimate website visitor to a different IP address using hacking. Spyware is an offline app that obtains data without a user’s consent. When computer is online, those datas are sent to spy ware sources. Internet privacy threats may be minimized by one’s knowledge and careful examination of online sites before disclosing any personal information.
How to Prevent Internet Privacy ?
Preventive software applications are available and those can be either purchased or downloaded. Examples of such software are antivirus, anti malware, firewalls, etc. and if those are installed ,they must be upgraded to latest versions from time to time to protect the computer from latest viruses and other such online phishing- pharming attack. It is to be noted that new computer viruses are invented daily.
Some other preventive measures are given below:
- shopping must be made from reliable websites only.
- Some websites have low security levels and those must be avoided.
- Browser cache and history must be cleared on a consistent basis .
While choosing passwords, include a combination of special characters, numerals and letters as they make a strong combination for a password.With more and more of our activities and offices are transferring into online modes, it makes sense to educate all internet users to know about the negative elements hidden behind data usage. Not to forget, all those social networking sites which appear very fun to use. Being a technocrat is not bad unless one is a smart user. Uploading a post in the form of a photo can be fun and seem trendy, but we never know if there are lurkers sitting behind computer and looking for their next targets. Many such cases of stealing identity, editing decent photos into indecent ones and thus using them to blackmail people are becoming very common. therefore one must first be very careful at choosing their online friends. Also there are some websites who do not support choosing audiences. That means uploading anything will be visible publicly. For example, twitter. So we must choose carefully what to post and what not.In some websites, information related to bank accounts are asked to enter. This applies during online transaction. One must ensure that it is verified or authorized by a secure site or source such as VISA, verisign, etc.
Questions :
- Internet Privacy Necessary ?
- What is Internet Privacy ?
- Types of Hacking
- How to Choose Strong passwords ?
About Charmin Patel
Blogger and Digital Marketer by Choice and Chemical Engineer By Chance. Computer and Internet Geek Person Who Loves To Do Something New Every Day.
- EssayBasics.com
- Pay For Essay
- Write My Essay
- Homework Writing Help
- Essay Editing Service
- Thesis Writing Help
- Write My College Essay
- Do My Essay
- Term Paper Writing Service
- Coursework Writing Service
- Write My Research Paper
- Assignment Writing Help
- Essay Writing Help
- Call Now! (USA) Login Order now
- EssayBasics.com Call Now! (USA) Order now
- Writing Guides
The Internet Privacy (Essay/Paper Sample)
Table of Contents
The Internet Privacy
Internet privacy entails securing personal data that is published on the internet. This kind of privacy encompasses safeguarding of sensitive and private information, data, preferences, and communications. In the current cyberspace, different people have raised complaints regarding loss of personal information whenever they do online transactions, visit social media sites, and participate in online games as well as attending forums. In such circumstances, many people exhibit incidences of compromised passwords, the revelation of victims’ identities, and fraud. Such privacy issues come as a result of negligence by the users or website developers who do not comply with the regulations and standards that curb privacy violation. Thus, internet privacy is under threat due to the inability of the internet service providers who have no explicit permission to gain access or share confidential information. This essay presents a discussion of internet privacy and how online users fall victims due to increased vulnerability of online security.
Internet privacy is a paradoxical and difficult to understand. People are aware of their behaviors online and are bound to use strong passwords when before accessing their own accounts. In the same note, users are supposed to log out their own accounts when ceasing access to the internet so that they leave it safe and secure from intruders. However, regardless of such knowledge and clear understanding of the privacy policy, they do not bother. Instead, they lament of the increased vulnerability due to such negligence. On a separate note, people tend to care about protecting their personal information and normally feel insecure when issuing it on the internet. Therefore, this behavior brings about privacy paradox since they are unable to gain control of their own digital information.
Internet privacy faces numerous risks that include phishing that encompasses hacking activities that are used to obtain secured information, usernames, passwords, security PIN, credit card numbers and bank account numbers. Furthermore, users have been under attack through pharming which covers redirection of legitimate website users to a new and different IP address. Others include the use of offline applications that get information without user’s consent. In such circumstances, a computer that is online can be accessed to get the previously acquired data that is sent to the spyware source. On a separate note, there is a rise in the usage of malware which allows an illegal damage of computers both online and offline through application viruses, Trojan, and spyware.
Need an essay customized under your requirements? We can help you

In addition to the above measures, users should always keep their operating systems and windows up to date to avoid vulnerability. A rise in software vulnerability is enhanced through the use of outdated systems. This increases loopholes for cyber criminals. For example, Flash and Java are normally vulnerable to security threats hence expose their users to cyber attacks. On the same note, users should avoid accessing free Wi-Fi networks since such networks are used by hackers with network sniffers that retrieve crucial information. Lastly, users should always update and change their privacy settings on regular basis.
In conclusion, the essay has elaborated on internet privacy based on the different risks and vulnerability that users are facing besides highlighting the different measures that should be put in place. However, reduction of vulnerability of internet privacy begins with the user’s behavior regarding internet usage. Users should incorporate all the measures and should be careful when revealing their personal information online. Lastly, users should be aware of their privacy rights and should fight for such rights especially in cases when breaches occur.


IMAGES
VIDEO
COMMENTS
Get custom essay. Ultimately, the importance of internet privacy extends beyond individual convenience; it is a fundamental right that underpins our freedom, security, and individuality in the digital age. By recognizing the significance of internet privacy and taking meaningful steps to protect it, we can ensure that the digital landscape ...
Internet privacy is a subcategory of data privacy, focusing on the protection of user information shared online. It is a significant concern in the digital age, where data is considered the new oil. Internet privacy concerns the safeguarding of personal, financial, and data information of a private individual or organization.
Unfortunately, this has also brought about various challenges that must be addressed 1. Generally, information is a vital treasure in itself, and the more one has the better. Having valuable, intellectual, economic, and social information creates enormous opportunities and advantages for any individual. We will write a custom essay on your topic.
Internet privacy is a complicated topic that encompasses how your personal information is utilized, gathered, shared, and kept on your own devices and when connected to the Internet. Personal information about your habits, purchasing, and location can be gathered and shared with third parties via your phone, GPS, and other devices.
Although every individual has the right to accuse the government and internet service providing companies over their failure to protect their customers' privacy, individuals should recognize, they have a crucial duty to play as far […]
Internet privacy involves the right or mandate of personal privacy concerning the storage, re-purposing, provision to third parties, and display of information pertaining to oneself via the Internet. [1] [2] Internet privacy is a subset of data privacy .
Over 30 years ago, Mason (Citation 1986) voiced ethical concerns over the protection of informational privacy, or "the ability of the individual to personally control information about one's self" (Stone et al., Citation 1983), calling it one of the four ethical issues of the information age.Since the 1980s, scholars have remained concerned about informational privacy, especially given ...
Writing an essay on internet privacy is important for raising awareness, advocating for stronger privacy protections, and empowering individuals to safeguard their personal information online. By conducting thorough research, considering different perspectives, and providing practical solutions, the essay can help contribute to a more privacy ...
One cannot pick up a newspaper, watch TV, listen to the radio, or scan the news on the internet without some direct or veiled reference to the lack of information security or intrusions into personal privacy. Many intrusions into government and private-sector systems have exposed sensitive mission, business and personal information.
9 essay samples found. Internet privacy refers to the right or expectation of privacy in the digital realm, encompassing issues related to the protection of personal data, confidentiality, and anonymity online. Essays on internet privacy could delve into the risks and challenges associated with digital surveillance, data breaches, or online ...
Get involved and call your congressperson, he says — tell the policymakers that you care about online privacy. 8. Start small and take it one step at a time. Faced with this landscape, getting a ...
One of the biggest concerns is privacy and security. With so much personal information being shared online, there is a risk of data breaches and cyber attacks. ... Essay On Internet- FAQs What is internet short essay? In the modern time, internet has become is one of the most powerful and interesting tools all across the world. The Internet is ...
Now that system, which ballooned into a $350 billion digital ad industry, is being dismantled. Driven by online privacy fears, Apple and Google have started revamping the rules around online data ...
Overall, a 2014 survey found that 91% of Americans "agree" or "strongly agree" that people have lost control over how personal information is collected and used by all kinds of entities. Some 80% of social media users said they were concerned about advertisers and businesses accessing the data they share on social media platforms, and ...
After learning about the information that has come to light, students need the opportunity to explore their own thoughts and feelings on this important issue. These 50 new journal prompts offer students the chance to think about their own right to privacy, the government's motives for surveillance, and the ramifications of wide-scale public ...
INTERNET PRIV ACY IN 2020. MICHAEL IHEANYICHUKWU GODWIN ONUGHA (S5230136) Computing Department, Bournemouth University. Fern Barrow, Poole, BH12 5BB, United Kingdom. [email protected] ...
Internet privacy and HTTP cookies. Device fingerprinting and Internet privacy. Photos in social networks and Internet privacy. Search engines and Internet privacy. Reducing the risks to Internet privacy. Real life implications related to Internet privacy. Global policies about Internet privacy.
Physics. Get Started. We live in the age of the internet. And, it has become an important part of our life. Besides, internet is an invention of high-end science and modern technology. Apart from that, we are connected to internet 24x7. In this essay on Internet, we are going to discuss various things related to the internet.
Internet privacy is the security of a user's personal data that is stored or published on the internet. The internet is an important part of every individual's daily life. In today's society, the internet is used by many different people for many reasons. It can be used for research, communication, and purchasing items.
In all these areas, internet privacy is important as without this, our personal details such as our names, our birthdays, and our emails could be visible to random strangers without our consent. In a world filled with perverts and hackers, this internet privacy is important as even more significant information such as bank accounts and other ...
Wide scale surveillance by the government has harmed the privacy rights of US citizens. Government internet surveillance efforts result in a violation of individual privacy as the government intercepts the personal information and communication from US citizens. For privacy to exist, an individual has to have control over himself and the ...
Malware using short definitions , phishing is an internet hacking activity used to secure user data ,including username, password, etc.pharming is used to redirect a legitimate website visitor to a different IP address using hacking. Spyware is an offline app that obtains data without a user's consent. When computer is online, those datas are ...
In conclusion, the essay has elaborated on internet privacy based on the different risks and vulnerability that users are facing besides highlighting the different measures that should be put in place. However, reduction of vulnerability of internet privacy begins with the user's behavior regarding internet usage. Users should incorporate all ...