

The SAFe® Epic – an example
We often have questions about what a “good” sufficiently developed SAFe Epic looks like. In this example we use with clients during the Lean Portfolio Management learning journey, we dive into an example of real-world details behind an epic hypothesis statement.
For now, we have not provided a fully developed SAFe Lean Business Case as an example because business cases are typically highly contextual to the business or mission. That being said please remember that the core of the business case is established and driven from the Epic Hypothesis Statement and carried over into the documented business case.
Agile Lifecycle Management Solution Enabler Epic
Epic Owner: John Q. Smith
Epic Description
The big awesome product company requires a common platform for collaboration on work of all types across the portfolio for all teams, managers, architects, directors, and executives including customer collaboration and feedback loops. This solution will solve the problems in our system where we have poor quality or non-existent measurement and multiple disparate systems to manage and report on work.
For the Portfolio Teams
Who needs to manage their work, flow, and feedback
The single-source system of record for all work
IS A web-based software tool suite that provides customizable workflows that support the enterprise strategic themes related to creating better business and IT outcomes using guidance from the Scaled Agile Framework for Lean Enterprises (SAFe), Technology Business Management (TBM), and Value Stream Management (VSM) via the Flow Framework
THAT will provide a common place for all customers and portfolio stakeholders to have a transparent vision into all of the work occurring in the system/portfolio, provide a mechanism to manage capacity at scale, and enable easier concurrent road mapping
UNLIKE the current array of disparate, ad hoc tools and platforms
OUR SOLUTION will organize all work in a holistic, transparent, visible manner using a common enterprise backlog model combined with an additive enterprise agile scaling framework as guidance including DevOps, Lean+Systems Thinking, and Agile
Business Outcomes:
- Validate that the solution provides easy access to data and/or analytics, and charts for the six flow metrics: distribution, time, velocity, load, efficiency, and predictability for product/solution features (our work). (binary)
- The solution also provides flow metrics for Lean-Agile Teams stories and backlog items. (binary)
- 90% of teams are using the solution to manage 100% of their work and effort within the first year post implementation
- All features and their lead, cycle, and process times (for the continuous delivery pipeline) are transparent. Feature lead and cycle times for all value streams using the system are visible. (binary)
- Lean flow measurements — Lead and cycle times, six SAFe flow metrics, and DevOps metrics enabled in the continuous delivery pipeline integrated across the entire solution platform (binary)
- Activity ratios for workflow, processes, and steps are automatically calculated (binary)
- Percent complete and accurate (%C&A) measures for value streams automatically calculated or easily accessible data (binary)
- Number of documented improvements implemented in the system by teams using data/information sourced from the ALM solution > 25 in the first six months post implementation
- Number of documented improvements implemented in the system by teams using data/information sourced from the ALM solution > 100 in the first year post implementation
- Flow time metrics improve from baseline by 10% in the first year post implementation (lead time for features)
- Portfolio, Solution/Capability, and Program Roadmaps can be generated by Lean Portfolio Management (LPM), Solution Management, and Product Management at will from real-time data in the ALM (binary)
- Roadmaps will be available online for general stakeholder consumption (transparency)
- Increase customer NPS for forecasting and communication of solution progress and transparency of execution by 20% in the first year post implementation (survey + baseline)
- Build a taxonomy for all work including a service catalog (binary)
- Run the system and the system produces the data to produce the capacity metrics for all value streams to enable the LPM guardrail (binary)
- Stops obfuscation of work hidden in the noise of the one sized fits all backlog model (everything is a CRQ/Ticket) and allows for more accurate and representative prioritization including the application of an economic decision-making framework using a taxonomy for work (binary)
- Enables full truth in reporting and transparency of actual flow to everyone, real-time – including customers (100% of work is recorded in the system of record)
- Enables live telemetry of progress towards objectives sourced through all backlogs, roadmaps, and flow data and information (dependent)
- 90% of teams are using the solution to manage 100% of their capacity within the first year post implementation
Leading Indicators:
- Total value stream team member utilization > 95% daily vs. weekly vs. per PI
- Low daily utilization < 75% indicates there is a problem with the solution, training, or something else to explore
- % of teams using the ALM solution to manage 100% of their work and effort
- Number of changes in the [old solutions] data from the implementation start date
- Usage metrics for the [old solutions]
- We can see kanban systems and working agreements for workflow state entry and exit criteria in use in the system records
- Teams have a velocity metric that they use solely for the use of planning an iterations available capacity and not for measuring team performance (only useful for planning efficiency performance)
- Teams use velocity and flow metrics to make improvements to their system and flow (# of improvements acted from solution usage)
- Teams are able to measure the flow of items per cycle (sprint/iteration) and per effort/value (story points; additive)
- Program(s)[ARTs] are able to measure the flow of features per cycle (PI) and per effort/value (story points; additive from child elements)
- Portfolio(s) are able to measure the flow of epics per cycle (PI) and per effort/value (story points; additive from child elements)
- % of total work activity and effort in the portfolio visible in the solution
- Show the six flow metrics
- Features (Program) – current PI and two PI’s into the future
- Epics and Capabilities – current PI up to two+ years into the future
- are the things we said we were going to work on and what we actually worked on in relation to objectives and priorities (not just raw outputs of flow) the same?
- The portfolio has a reasonable and rationalized, quality understanding of how much capacity exists across current and future cycles (PI) in alignment with the roadmap
- Identification and reporting of capacity across Portfolio is accurate and predictable;
- Identification of Operational/Maintenance-to-Enhancement work ratio and work activity ratios and % complete and accurate (%C&A) data readily available in the system
- including operations and maintenance (O&M) work and enhancements,
- highlighting categories/types of work
- Work activity ratios are in alignment with process strategy and forecasts, process intent, and incentivizing business outcomes;
- allows leadership to address systemic issues;
- data is not just reported, but means something and is acted upon through decision-making and/or improvements
- # of epics created over time
- # of epics accepted over time
- # of MVP’s tested and successful
- Parameters configured in the tool to highlight and constrain anti-patterns
- Stimulates feedback loop to assist in making decisions on whether to refine/improve/refactor and in that case, what to refine/improve/refactor
- Strategic themes, objectives, key results, and the work in the portfolio – Epics, Capabilities, Features, Stories traceability conveyed from Enterprise to ART/Team level
Non-Functional Requirements
- On-Premise components of the ALM solution shall support 2-Factor Authentication
- SaaS components of the ALM solution shall support 2-Factor Authentication and SAML 2.0
- The system must be 508 compliant
- The system must be scalable to support up to 2000 users simultaneously with no performance degradation or reliability issues
- Must be the single-source system for all work performed in the portfolio and value streams.
- ALM is the single-source system of record for viewing and reporting roadmap status/progress toward objectives
Building your Experiment – The Minimum Viable Product (MVP)
Once you have constructed a quality hypothesis statement the product management team should begin work on building the lean business case and MVP concept. How are you going to test the hypothesis? How can we test the hypothesis adequately while also economically wrt to time, cost, and quality? What are the key features that will demonstrably support the hypothesis?
- Name First Last
Developing a Winning Epic Hypothesis Statement that Captivates Stakeholders using SAFe

The Scaled Agile Framework®, or SAFe, was created in 2011 and built upon the classic Agile manifesto by incorporating key ideas from the Lean methodology.
Organisations using this framework can accomplish a wide range of advantages, according to SAFe developers, such as:
20-50% increases in productivity
30-75% quicker time to market
10-50%Increases in employee engagement

Assume that in order to reap the benefits of project management, your Executive Action Team (EAT) wants to embrace a Lean-Agile mentality. If so, it needs to become proficient in crafting and presenting an Epic Hypothesis Statement (EHS). Check out the Agile certification course to learn more.
Creating a strong EHS and persuading your stakeholders to embrace your bold idea are crucial to attaining business agility and optimising development procedures. On the other hand, neglecting to do so will impede your pipeline for continuous delivery and hinder you from effectively creating functional software.
It’s imperative that you nail your EHS pitch because there is a lot riding on it. We’ve developed this useful tool to assist you pitch your Epic Hypothesis Statement to your EAT in order to support these efforts.
What Is an Executive Action Team (EAT)?
One of the cross-functional teams in the SAFe framework is the Executive Action Team (EAT). This group drives organisational transformation and eliminates barriers to systemic advancement. Additionally, the EAT will hear your EHS and choose whether or not to add it to the Epic queue.
The idea that change must originate at the top is one of the fundamental tenets of the lean-agile approach. An effective EHS pitch will pique the interest of Executive Action Team stakeholders and persuade them to adopt your Epic Hypothesis Statement.
What Is an Epic Hypothesis Statement (EHS)?
A comprehensive hypothesis that outlines an epic or sizable undertaking intended to overcome a growth impediment or seize a growth opportunity is called the Epic Hypothesis Statement (EHS).
Epics are typically customer-facing and always have a large scale. They need to assist a business in meeting its present requirements and equip it to face obstacles down the road.
The Epic Hypothesis Statement (EHS) is typically delivered to the EAT in the style of an elevator pitch: it is brief, simple, and concise, although the statement itself will be highly thorough.
Key Components of an Epic Hypothesis Statement
The Portfolio Kanban system’s initial funnelling phase is expanded upon in the Epic Hypothesis Statement. The concept started out as just one, like “adding self-service tools to the customer’s loan management portal.”
You must refine this fundamental concept into a fully realised endeavour in your role as the Epic Owner. In the event that your theory is verified, you must also describe the anticipated advantages the firm will enjoy. Your EHS also has to have leading indications that you can track as you move toward validating your hypotheses.
Let’s expand on the example of the self-service tool.
You could expand on the basic premise of integrating self-service capabilities into the loan management portal that is visible to customers if you wanted to develop an EHS. Indicate which specific tools you want to use and how they will enhance the client journey in your explanation of the initiative.
For example, the following could be considered expected benefit outcomes of this initiative:
- A reduction in calls to customer service
- Better customer satisfaction and engagement
- improved image of the brand
It’s true that some advantages would be hard to measure. Complementary objectives and key results (OKRs) are therefore quite important to include in your EHS since they will support your pitch to your EAT regarding the benefits of your EHS.
Pitching Your EHS
It’s time to submit your finished Epic Hypothesis Statement to the EAT for consideration. You need to do the following if you want to involve your stakeholders.
Make Use of Powerful Visuals
The Agile manifesto and the Portfolio Kanban system both stress the value of visualisation. Including images in your EHS pitch demonstrates to your audience that you understand these approaches in their entirety and aids with their understanding of your concept.
Explain the Applicability of Your OKRs
Your suggested endeavour and the OKRs you’ve chosen should be clearly connected. Nevertheless, it never hurts to emphasise this point by outlining how each OKR you select will assist in monitoring the advancement of your theory’s proof.
Close the Deal with a Powerful Concluding Statement
Your Epic Hypothesis Statement is ultimately a sales pitch. Handle it as such by providing a succinct yet captivating conclusion. Go over the possible advantages of your project again, and explain why you think it will help the business achieve its short- and long-term objectives.
The Perfect EHS Pitch Starts with a Great Idea
By utilising the aforementioned strategies and recommendations, you can create an extensive EHS that grabs the interest of your stakeholders. But never forget that the quality of your idea will determine how well your pitch goes.
Work with your EAT to integrate ideas that have a significant impact into your workflow for managing your portfolio. Next, choose a notion you are enthusiastic about and develop your hypothesis around it. You’ll have no trouble crafting the ideal EHS pitch.
Conclusion To learn more about Agile and SAFe, check out the SAFe Agile certification course online.
What is Interruption Testing?
Approaches for being a lead business analyst, leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Related Articles

Why Should You Become Scrum Certified?

Agile Scrum Beginners Guide

How to Become Certified Scrum Master

Feature Driven Programming

agility at scale
- Case Studies
Implementing SAFe: Requirements Model (v6)
Table of Contents
What is the SAFe Requirements Model?
The SAFe Requirements Model is a hierarchical structure that manages and organizes requirements in large-scale Agile projects.
The SAFe Requirements Model helps organizations align their business objectives with their development efforts, ensuring that teams deliver value incrementally while focusing on the overall strategy. The SAFe Requirements Model is organized into three levels:
- Epics are high-level initiatives representing significant organizational value and span multiple planning intervals.
- Features are mid-level requirements that provide more detailed descriptions of the functionality needed to achieve the goals set forth by the Epics.
- Stories are the smallest units of work, representing individual tasks to be completed by Agile teams, typically within a single iteration.
What are SAFe Epics?
Portfolio Epics are large-scale business initiatives that drive change and provide substantial business benefits.
The strategic investment themes drive all new development, and requirements epics are derived from these decisions.
Epics are large-scale development initiatives that realize the value of investment themes.
Epics in the SAFe Requirements Model are large-scale, cross-cutting initiatives that encapsulate significant development efforts and provide substantial value to the organization or end-users. They can be business epics, which focus on delivering customer or user value, or enabler epics, which address technical or architectural enhancements to support the development of business epics. Epics typically span multiple Agile Release Trains (ARTs) and Planning Intervals (PIs), requiring collaboration and coordination among various teams.
Epics are the highest-level requirements artifact used to coordinate development. In the requirements model, they sit between investment themes and features.
- Epics are usually driven (parented by) investment themes. However, some epics can be independent (they do not require a parent to exist).
- Epics are not implemented directly. Instead, they are broken down into Features and User Stories, which the teams use for actual coding and testing.
- Epics are not directly testable. They are tested through the acceptance tests associated with the features and stories that implement them.
What are the key elements of a SAFe Epic Statement?
An Epic Statement comprises a brief description, the customer or business benefit, and the success criteria.
When documenting epics in SAFe, the following key elements are included:
What are the differences between SAFe Business Epics and Enabler Epics?
Business Epics delivers direct business value, while Enabler Epics provides the technological or architectural advancements necessary to support business Epics.
In the SAFe Requirements Model, the difference between enabler epics and business epics lies in their focus and purpose:
- Business Epics: These are large-scale initiatives aimed at delivering customer or user value, addressing new features, products, or services that have a direct impact on the organization’s business outcomes. Business epics typically focus on solving customer problems, capturing market opportunities, or improving the user experience.
- Enabler Epics: These epics focus on technical, architectural, or process enhancements that support the development and delivery of business epics. Enabler epics may not provide direct customer value but are essential for improving the organization’s underlying infrastructure, technology, or capabilities, making it easier to deliver business value more efficiently and effectively.
Business Epics and Enabler Epics in SAFe serve different but equally important roles. Business Epics are initiatives that deliver direct customer or business value. They represent substantial investments and have a clear tie to business outcomes. On the other hand, Enabler Epics support the implementation of Business Epics. They represent the necessary technological or architectural advancements that facilitate the delivery of business value. While they may not directly impact the customer, they are vital in realizing Business Epics.
What is the SAFe Portfolio Backlog?
The Portfolio Backlog is a prioritized list of Portfolio Epics.
The Portfolio Backlog within SAFe serves as the repository for upcoming Portfolio Epics. It is a prioritized list of Epics, with those at the top representing the highest priority and most significant initiatives that need to be undertaken. This backlog helps to align the organization around the most important strategic initiatives, allowing for effective decision-making and allocation of resources across the portfolio.
The Portfolio Backlog provides a clear picture of the organization’s direction and value delivery at the Portfolio level, guiding the allocation of resources, funding, and coordination of efforts across multiple Agile Release Trains (ARTs) and Solution Trains to align with the overall strategy.
What are SAFe Product Features?
SAFe Product Features are serviceable system components that provide business value and address user needs.
Features are described as follows:
Features are services provided by the system that fulfill stakeholder needs.
Within the realm of SAFe, Product Features are distinct pieces of functionality that are of value to the user or the business. They are typically larger than individual User Stories and represent services the system provides that fulfill specific user needs. Features form a critical part of the Program Backlog.
In describing the features of a product or system, we take a more abstract and higher-level view of the system of interest. In so doing, we have the security of returning to a more traditional description of system behavior, the feature.
Features as ART-Level Artifacts
A “Feature” in the SAFe Requirements Model is a high-level, functional requirement that delivers value to the end-user or customer. Features are typically part of a larger product or system and are aligned with the goals of a specific Planning Interval (PI), which usually spans 8-12 weeks.
Features live above software requirements and bridge the gap from the problem domain (understanding the needs of the users and stakeholders in the target market) to the solution domain (specific requirements intended to address the user needs).
Features are usually expressed as bullet points or, at most, a couple of sentences. For instance, you might describe a few features of an online email service like this:
Enable “Stars” for marking important conversations or messages, acting as a visual reminder to follow up on a message or conversation later. Introduce “Labels” as a “folder-like” metaphor for organizing conversations.
Feature Statement and Template
In the SAFe Requirements Model, a feature is typically documented using the following:
What are the differences between SAFe Features and SAFe Capabilities?
SAFe Features are system functionality that provides value to users, while SAFe Capabilities are higher-level functionalities that provide value to customers and stakeholders.
SAFe distinguishes between Features and Capabilities based on their level of abstraction and scope. Features at the Program Level are functionality increments that address user needs and deliver value. They are smaller in scope and more detailed compared to Capabilities. On the other hand, Capabilities are placed at the Large Solution Level, representing higher-level functionalities that deliver value to customers and stakeholders. They are typically bigger, encompass broader functionality, and may require multiple Agile Release Trains (ARTs) to implement.
The main difference between capabilities and features in the SAFe Requirements Model lies in their scope and granularity:
- Capabilities : Capabilities are high-level functional requirements that describe essential building blocks of a solution in the Large Solution level of the SAFe Requirements Model. They span multiple Agile Release Trains (ARTs) and represent the functionality needed to deliver value to end-users or customers. Capabilities provide a broader perspective on the solution and help coordinate efforts among multiple ARTs working together.
- Features : Features are smaller, more granular functional requirements at the Program level in the SAFe Requirements Model. They describe specific functionalities or enhancements that deliver value within a single Agile Release Train (ART). Features are derived from capabilities and are broken down into user stories, which Agile teams implement during iterations.
In summary, capabilities are high-level, cross-ART functional requirements for large-scale solutions. At the same time, features are more granular, ART-specific requirements that deliver value as part of a product or system.
How are SAFe Features tested?
SAFe Features are tested through iteration testing, integration testing, and system demos.
The SAFe approach to testing Features involves three specific practices, ensuring functionality and integration, and they are:
- Iteration Testing , where each feature is tested during the iteration it’s developed.
- Integration Testing is where Features are tested in conjunction with other system elements to ensure they work together properly.
- System Demos allow stakeholders to inspect the integrated system and provide feedback, enabling further refinement and validation of Features.
Story-level testing ensures that methods and classes are reliable (unit testing) and stories serve their intended purpose (functional testing). A feature may involve multiple teams and numerous stories. Therefore, testing feature functionality is as crucial as testing story implementation.
Moreover, many system-level “what if” considerations (think alternative use-case scenarios) must be tested to guarantee overall system reliability. Some of these can only be tested at the full system level. So indeed, features, like stories, require acceptance tests as well.
Every feature demands one or more acceptance tests, and a feature cannot be considered complete until it passes.
What are Nonfunctional Requirements?
Nonfunctional Requirements (NFRs) are specifications about system qualities such as performance, reliability, and usability.
In SAFe, Nonfunctional Requirements (NFRs) denote the ‘ilities’ – system attributes like scalability, reliability, usability, and security. Unlike functional requirements, which define what a system does, NFRs describe how it does it. These are critical factors that shape system behavior and often have system-wide implications. NFRs are a constant consideration throughout the development process, helping to ensure that the system meets the necessary standards and delivers a satisfying user experience.
Nonfunctional Requirements as Backlog Constraints
From a requirements modeling perspective, we could include the NFRs in the program backlog, but their behavior tends to differ. New features usually enter the backlog, get implemented and tested, and then are removed (though ongoing functional tests ensure the features continue to work well in the future). NFRs restrict new development, reducing the level of design freedom that teams might otherwise possess. Here’s an example:
For partner compatibility, implement SAML-based single sign-on (NFR) for all products in the suite.
In other cases, when new features are implemented, existing NFRs must be reconsidered, and previously sufficient system tests may need expansion. Here’s an example:
The new touch UI (new feature) must still adhere to our accessibility standards (NFR).
Thus, in the requirements model, we represented NFRs as backlog limitations.
We first observe that nonfunctional requirements may constrain some backlog items while others do not. We also notice that some nonfunctional requirements may not apply to any backlog items, meaning they stand alone and pertain to the entire system.
Regardless of how we view them, nonfunctional requirements must be documented and shared with the relevant teams. Some NFRs apply to the whole system, and others are specific to a team’s feature or component domain.
How are Nonfunctional Requirements tested?
Nonfunctional Requirements are tested through methods like performance testing, usability testing, and security testing.
The testing of Nonfunctional Requirements (NFRs) in SAFe involves specialized techniques corresponding to each type of NFR. For instance, performance testing measures system responsiveness and stability under varying workloads. Usability testing assesses the system’s user-friendliness and intuitiveness. Security testing evaluates the system’s resistance to threats and attacks. By testing NFRs, teams ensure that the system delivers the right functionality and provides the right quality of service, thereby maximizing user satisfaction and trust.
Most nonfunctional (0…*) requirements necessitate one or more tests. Instead of labeling these tests as another form of acceptance tests and further overusing that term, we’ve called them system qualities tests. This name implies that these tests must be conducted periodically to verify that the system still exhibits the qualities expressed by the nonfunctional requirements.
What is the SAFe ART Backlog?
The SAFe Program Backlog is a prioritized list of features awaiting development within an Agile Release Train.
Within SAFe, the Program Backlog serves as a holding area for upcoming Features, which are system-level services that offer user benefits and are set to be developed by a specific Agile Release Train (ART). These Features are prioritized based on their value, risk, dependencies, and size. The backlog helps provide transparency and drives PI planning, guiding the ART toward achieving the desired outcomes.
Features are brought to life by stories. During release planning, features are broken down into stories, which the teams utilize to implement the feature’s functionality.
What are SAFe User Stories?
SAFe User Stories are short, simple descriptions of a feature told from the perspective of the person who desires the capability, usually a user or customer.
User Stories within SAFe are a tool for expressing requirements. They focus on the user’s perspective, facilitating a clear understanding of who the user is, what they need, and why they need it. User Stories promote collaboration and customer-centric development by emphasizing value delivery and verbal communication.
What is the definition of a SAFe User Story?
A SAFe User Story is a requirement expressed from the end-user perspective, detailing what the user wants to achieve and why.
In SAFe, a User Story is an informal, natural language description of one or more features of a software system. It is centered around the end-user and their needs, providing context for the development team. User stories are the agile alternative to traditional software requirements statements (or use cases in RUP and UML), serving as the backbone of agile development. Initially developed within the framework of XP, they are now a staple of agile development in general and are covered in most Scrum courses.
In the SAFe Requirements Model, user stories replace traditional software requirements, conveying customer needs from analysis to implementation.
A user story is defined as:
A user story is a concise statement of intent that outlines what the system needs to do for the user.
Typically, user stories follow a standard (user voice) format:
As a <role>, I can <activity> so that <business value>.
This format encompasses elements of the problem space (the delivered business value), the user’s role (or persona), and the solution space (the activity the user performs with the system). For example:
“As a Salesperson (<role>), I want to paginate my leads when I send mass e-mails (<what I do with the system>) so that I can quickly select a large number of leads (<business value I receive>).”
What are the 3-Cs of user stories?
The 3-Cs of user stories refer to Card, Conversation, and Confirmation.
In the realm of SAFe, these three Cs are fundamental to the creation and execution of User Stories. The “Card” typically represents the User Story, written in simple language. “Conversation” signifies the collaborative discussions that clarify the details of the User Story and refine its requirements. “Confirmation” establishes acceptance criteria to determine when the User Story is completed successfully. This trio of components ensures clarity and shared understanding in value delivery.
- “Card” refers to the two or three sentences that convey the story’s intent.
- “Conversation” involves elaborating on the card’s intent through discussions with the customer or product owner. In other words, the card also signifies a “commitment to a conversation” about the intent.
- “Confirmation” is the process by which the team, via the customer or customer proxy, determines that the code fulfills the story’s entire intent.
Note that stories in XP and Agile are often manually written on physical index cards. However, agile project management tools usually capture the “card” element as text and attachments in the enterprise context. Still, teams frequently use physical cards for planning, estimating, prioritizing, and visibility during daily stand-ups.
This straightforward alliteration and Agile’s passion for “all code is tested code” demonstrates how quality is achieved during code development rather than afterward.
The SAFe Requirements model represents the confirmation function as an acceptance test verifying that the story has been implemented correctly. We’ll refer to it as story acceptance tests to distinguish it from other acceptance tests and consider them an artifact separate from the (user) story.
The model is explicit in its insistence on the relationship between the story and the story acceptance test as follows:
- In the one-to-many (1..*) relationship, every story has one (or more) acceptance tests.
- It’s done when it passes. A story cannot be considered complete until it has passed the acceptance test(s).
Acceptance tests are functional tests that confirm the system implements the story as intended. Story acceptance tests are automated whenever possible to prevent the creation of many manual tests that would quickly hinder the team’s velocity.
What is the difference between SAFe Enabler Stories and SAFe User Stories?
SAFe Enabler Stories support the exploration, architecture, infrastructure, and compliance activities needed to build a system, unlike User Stories, which focus on end-user functionality.
The main difference between an enabler user story and a typical user story in the SAFe Requirements Model lies in their focus and purpose:
- Enabler Story: An enabler story represents work needed to support the development of a product or system but does not necessarily deliver customer value directly. Enabler user stories are used to address technical or architectural needs, reduce technical debt, or improve infrastructure. They are often larger and more complex than typical user stories, as they address non-functional requirements crucial for the product’s success.
- User Story: A typical user story represents a specific feature or functionality that delivers value to the customer or end-user. Typical user stories are more focused and granular than enabler user stories, describing specific actions or behaviors the user can perform with the product. They are usually smaller and more straightforward than enabler user stories, making them easier to estimate and prioritize.
Enabler Stories in SAFe facilitate the technical aspects of the system under development, such as architectural advancements or exploration activities. They differ from User Stories, which are primarily concerned with user-facing functionalities. Although Enabler Stories do not directly deliver user-valued functionality, they are vital for the evolution of the system and the delivery of future user value.
What are User Story sub-tasks?
User Story sub-tasks are smaller, manageable tasks derived from a User Story to facilitate its implementation.
Sub-tasks provide a way to break down a User Story into smaller, actionable pieces of work. These smaller tasks make the implementation more manageable and provide a clear path to completion. Sub-tasks can be assigned to different team members and tracked separately, providing a granular view of progress toward completing the User Story.
To ensure that teams fully comprehend the work required and can meet their commitments, many agile teams adopt a detailed approach to estimating and coordinating individual work activities necessary to complete a story. This is done through tasks, which we’ll represent as an additional model element:
Tasks implement stories. Tasks are the smallest units in the model and represent activities specific team members must perform to achieve the story. In our context:
A task is a small unit of work essential for completing a story.
Tasks have an owner (the person responsible for the task) and are estimated in hours (typically four to eight). The burndown (completion) of task hours indicates one form of iteration status. As suggested by the one-to-many relationship shown in the model, even a small story often requires more than one task, and it’s common to see a mini life cycle coded into a story’s tasks. Here’s an example:
- Task 1: Define acceptance test—Josh, Don, Ben
- Task 2: Code story—Josh
- Task 3: Code acceptance test—Ben
- Task 4: Get it to pass—Josh and Ben
- Task 5: Document in user help—Carly
In most cases, tasks are “children” of their associated story (deleting the story parent deletes the task). However, for flexibility, the model also supports stand-alone tasks and tasks that support other team objectives. This way, a team need not create a story to parent an item like “install more memory in the file server.”
What are User Story Acceptance tests?
User Story Acceptance tests are predefined criteria that a User Story must meet to be considered complete.
Acceptance tests for User Stories in SAFe provide clear, specific criteria determining when the story is done. These criteria are defined by the Product Owner in collaboration with the team and quality specialists and are based on the user’s expectations. They ensure the delivered functionality meets the desired value and quality, driving user satisfaction.
What are User Story Unit Tests?
User Story Unit Tests are low-level tests designed to verify the functionality of individual components of a User Story.
Unit tests in the context of User Stories involve testing individual components or units of the software to ensure they perform as expected. Developers typically create these tests during the implementation of the User Story. They form the first line of defense in catching and correcting defects, ensuring the integrity of the codebase, and promoting high-quality delivery.
Unit tests verify that the smallest module of an application (a class or method in object-oriented programming; a function or procedure in procedural programming) functions as intended. Developers create unit tests to check that the code executes the logic of the specific module. In test-driven development (TDD), the test is crafted before the code. Before a story is complete, the test must be written, passed, and incorporated into an automated testing framework.
Mature agile teams employ extensive practices for unit testing and automated functional (story acceptance) testing. Moreover, for those in the process of implementing tools for their agile project, adopting this meta-model can provide inherent traceability of story-to-test without burdening the team. Real Quality in Real Time
The fusion of crafting a streamlined story description, engaging in a conversation about the story, expanding the story into functional tests, augmenting the story’s acceptance with unit tests, and automating testing are how Scaled Agile teams achieve top-notch quality during each iteration. In this manner: Quality is built in, one story at a time. Ongoing quality assurance is accomplished through continuous and automated execution of the aggregated functional and unit tests.
How are Stories used in User Research or Data Science contexts?
Stories in User Research or Data Science represent hypotheses or questions about user behavior that need to be answered using data.
In User Research or Data Science, stories often take the form of hypotheses or research questions about user behavior. These stories guide the research process, providing clear objectives and helping to structure the analysis. By focusing on the user and their needs, these stories promote a user-centric approach to data analysis, helping to uncover meaningful, actionable insights.
Research (User Research, Data Science Research, etc.) has become integral to software development in today’s data-driven landscape. Like traditional software development, research activities also benefit from breaking work into smaller, manageable tasks. Although not officially part of the SAFe Requirements Model, we have devised a variation on the user story to address this unique aspect of data science projects. This document integrates with the team level in SAFe, ensuring that data science work aligns with Agile principles and practices.
What is a hypothesis test?
A hypothesis test is a statistical method used to make decisions or draw conclusions about population parameters based on sample data.
Within the statistical domain, hypothesis testing serves as a cornerstone methodology. It’s a process that allows analysts to test assumptions (hypotheses) about a population parameter. It involves formulating a null and alternative hypothesis, choosing a significance level, calculating the test statistic, and interpreting the results. This technique enables uncertainty-free decision-making, allowing organizations to draw data-driven conclusions and make informed decisions.
What is a hypothesis test in an Agile context?
A hypothesis test in an Agile context is a method used to validate assumptions about user behavior, system performance, or other product aspects based on collected data.
Hypothesis testing in Agile, particularly in fields like AI, research, data science, or user research, is a powerful tool for evidence-based decision-making. It involves creating a hypothesis about a particular user behavior, system characteristic, or other aspect of the product. This hypothesis is tested using real-world data collected from users, system logs, experiments, or other sources. The hypothesis test results confirm or reject the initial assumptions, providing insights into product development and improvement. It aligns with the Agile principle of learning through iteration, allowing teams to make data-informed decisions and continuously improve the product based on user feedback and empirical evidence.
What are Analytical Stories, and how are they used for data-driven insights?
Analytical Stories are questions or hypotheses guiding data analysis to obtain valuable business insights.
Analytical stories focus on data-driven insights, predictions, or recommendations that help solve business problems or enhance decision-making. They describe the desired outcome or question to be answered using data analysis, machine learning, or AI techniques. Analytical stories typically involve data exploration, feature engineering, model development, and validation. They include a clear objective, relevant data sources, and success criteria to measure the effectiveness of the analysis.
A typical Analytical Story includes the following seven elements:
What are Infrastructure Tasks?
Infrastructure Tasks are activities related to setting up or maintaining the technical environment that supports software development.
Infrastructure Tasks within SAFe encompass the essential activities that enable and support the development and delivery of software. These tasks range from setting up development environments and configuring servers to maintaining databases and managing network resources. While these tasks may not directly contribute to end-user features, they create a stable, efficient environment for delivering value. They are thus an integral part of the SAFe framework.
What is the Team Backlog?
Scaled Agile teams must maintain the utmost efficiency to ensure overall organizational effectiveness. To achieve this, we must adopt the simplest and leanest possible requirements model that caters to the needs of all stakeholders, especially team members. This model must be quintessentially agile, consistent with most agile training and common practice, and devoid of unnecessary administrative overhead, manual traceability, reporting, or detailed requirements.
Initially introduced by Scrum as a product backlog , the term “backlog” has evolved in our enterprise model to accommodate various levels of work. As a result, we use the term backlog in a more generalized sense. In the Big Picture, we refer to the backlog we’re discussing here as the Scaled Agile team’s local backlog.
This local backlog is the Scaled Agile team’s single, definitive source of work, containing all tasks (primarily user stories) that must be completed. Managed and maintained by the team, it serves as their repository for all identified work items, with its contents typically of little concern to others within the enterprise. The team has full autonomy over managing, tooling, and organizing their backlog to meet their iteration objectives.
The product owner, a Scaled Agile team member, is responsible for maintaining and prioritizing the backlog.
The Scaled Agile team’s backlog consists of all the team’s identified work items. In the meta-model, we generically refer to these work items as stories (or backlog items). For our purposes, we define a story as follows:
A story is a work item contained in the team’s backlog.
This simple definition encapsulates the agile approach’s focus on value delivery. The user story is a special kind that defines the system’s behavior and value for the user. We need to expand the model slightly to make the user story explicit.
With this minor addition, the backlog now consists of user stories and other work items. Other work items include refactors, defects, support and maintenance, tooling, and infrastructure work. These other work items help the team track all tasks needed to deliver value and enable better estimation of the time required to deliver user stories. We will discuss the rationale for specifically identifying these other work items later.
What is the SAFe Product Roadmap?
The SAFe Product Roadmap visually summarizes a product’s direction, highlighting upcoming features and milestones.
The Product Roadmap in SAFe outlines the anticipated journey of a product over time. It visually communicates the direction and progress of the product by displaying upcoming Features and Significant Milestones. This roadmap aids in setting expectations for stakeholders and helps align teams toward common objectives. It is a strategic tool that shows a high-level view of the product’s evolution while providing a common understanding of its future direction.
What is the composition and purpose of the Product Roadmap?
The Product Roadmap comprises planned features, milestones, and timelines to align stakeholders on a product’s future direction.
The Product Roadmap in SAFe combines planned Features, significant Milestones, and Timelines.
- Features derived from the Program Backlog represent the upcoming functionality increments.
- Milestones denote important events or achievements.
- Timelines provide a temporal context for the Features and Milestones.
The central purpose of the roadmap is to provide a shared understanding of the product’s future direction among all stakeholders. It aids expectation management, facilitates strategic decision-making, and promotes team alignment.
The Roadmap comprises a series of planned release dates, each with a theme and a prioritized set of features. Although it is mechanically simple to represent the Roadmap, determining its content is different.
The outcomes of release planning are utilized to update the (product or solution) Roadmap, which offers an understanding of how the enterprise aims to deliver increasing value over time.
How do you balance flexibility and expectation management with Product Roadmaps?
Balancing flexibility and expectation management with Product Roadmaps involves frequent revisiting, stakeholder communication, and applying a rolling wave planning approach.
Achieving the right balance between flexibility and expectation management when dealing with Product Roadmaps involves three specific activities, and they are:
- The roadmap is a living document that is revisited and updated frequently to adapt to changing circumstances.
- Regular communication with stakeholders to set and manage expectations effectively.
- Applying a rolling wave planning approach allows the teams to plan in detail for the near term while keeping a flexible outlook for the distant future. This method enables the roadmap to remain a useful strategic tool, providing direction without constraining agility.
In the SAFe Requirements Model, the Roadmap comprises a series of planned release dates, each with a theme, a set of objectives, and a prioritized feature set. The “next” release on the Roadmap is committed to the enterprise based on the work completed in the most recent release planning session. Releases beyond the next one are not committed, and their scope is somewhat vague.
Thus, the Roadmap embodies the enterprise’s current “plan of intent” for upcoming and future releases. However, it is subject to change—as development facts, business priorities, and customer needs change—therefore, release plans beyond the next release must not be used to establish external commitments.
What is the SAFe Product Vision?
SAFe Product Vision is a clear, inspiring goal representing the future state of a product.
In the SAFe Requirements Model, the Product Vision is a high-level, strategic description of the desired end state for a product or solution. The Product Vision guides Agile teams, helping them make decisions, prioritize features, and align their work with the organization’s broader objectives. Fostering a shared understanding and commitment across teams and stakeholders is essential, ensuring consistent direction throughout the product development process.
What are the key elements of the SAFe Product Vision?
The key aspects of the SAFe Product Vision include target state, customers, needs, and differentiation.
The Product Vision addresses six specific questions, and they are:
- What is this program’s strategic intent?
- What problem will the application, product, or system resolve?
- What features and benefits will it offer?
- Who will it cater to?
- What performance, reliability, etc., will it deliver?
- What platforms, standards, applications, etc., will it support?
The Product Vision in SAFe defines the ‘target state’ – a snapshot of the product’s desired future. It identifies customers or the audience who will benefit from the product. It outlines ‘needs’ – the problems or challenges the product will address. Lastly, it spells out ‘differentiation’ – how the product stands out from its competitors. Together, these components shape a comprehensive and compelling vision that informs and motivates everyone involved in the product’s development.
How is the SAFe Product vision documented?
The SAFe Product vision is documented using a vision statement, vision board, datasheet, draft press release, or vision box.
Since the product and software requirements specification documents and the like are unlikely to exist, directly communicating the Vision for the Scaled Agile program must take a different form. Agile teams take a variety of approaches to communicating the Vision. These include the following:
- Vision document
- Vision Board
- Draft press release
- Preliminary data sheet
- Backlog and Vision briefing
Documenting the Product Vision in SAFe can be approached in several ways. One common method is a ‘vision statement’ – a concise, written articulation of the product’s future state. Alternatively, a ‘vision board’ is created using images and text to represent the product’s goals visually. Another approach is a ‘vision box,’ a mock-up of the product’s packaging containing key information about the product. These methods help communicate the vision clearly and compellingly, enabling all stakeholders to align their efforts toward achieving it.
Product Vision Statement and Template
The Product Vision document in SAFe typically includes the following elements:
How do you balance the Product Vision and Timelines in SAFe?
Balancing the Product Vision and Timelines in SAFe requires continuous alignment of stakeholders, prioritizing based on value, and maintaining a sustainable pace.
Achieving equilibrium between the Product Vision and Timelines in SAFe involves three strategies, and they are:
- Regular alignment of stakeholders ensures everyone understands the product’s direction and the timelines involved.
- Prioritizing Features based on their value and dependencies ensures the most impactful work is done first.
- Maintaining a sustainable pace of development prevents burnout and ensures the team consistently delivers value over time, thereby upholding the Product Vision while adhering to the set Timelines.
What is the Architectural Runway in SAFe?
Architectural Runway in SAFe is the technical foundation that supports upcoming feature delivery without substantial redesign.
In SAFe, the Architectural Runway refers to the pre-existing, evolving technical infrastructure that enables the smooth delivery of impending features, minimizing the need for extensive, time-consuming redesigns. It’s a critical part of Agile development, ensuring readiness for future iterations, and is maintained and extended by implementing Enabler Epics and stories.
What is the Purpose of Architectural Runway?
The purpose of Architectural Runway is to ensure readiness for the implementation of upcoming features with minimal redesign.
The architectural runway is defined as follows:
A system with architectural runway contains existing or planned infrastructure sufficient to allow the incorporation of current and anticipated requirements without excessive refactoring.
The primary role of the Architectural Runway in SAFe is to provide a robust, flexible technical framework that aids in the swift and efficient delivery of impending features. Organizations can avoid the delays and resources associated with substantial system redesigns by having a well-maintained Architectural Runway, thereby promoting a smooth, continuous flow of value to the end users.
What are the Architectural Requirements in SAFe?
Architectural Requirements in SAFe are the technical prerequisites necessary for feature implementation.
Architectural requirements in SAFe denote the technical conditions that must be met to facilitate the successful deployment of new features. They define the system’s architecture, design, and infrastructure guidelines. This information directs teams when constructing or modifying the system, ensuring alignment with the system’s overall design and the company’s strategic objectives.
Architectural Runway and the Enterprise Portfolio
Addressing crucial technology initiatives.
In the context of an enterprise’s portfolio of products and in the face of a series of shorter, incremental releases, architectural runway answers a crucial question:
What technology initiatives need to be underway now so that we can reliably deliver a new class of features in the next year or so?
Distinguishing from Side R&D Projects
Here, we’re not discussing side R&D projects that an enterprise may use to determine technology strategies, establish feasibility, etc. Those are localized efforts and are managed by teams or system architects. Instead, we’re discussing large-scale changes to the code base necessary to support features on the current roadmap and changes that could affect most, or even all, development teams.
Examples of Large-Scale Architectural Changes
Here are some examples:
- Implement a standard install, licensing, and user authentication model across each product in the suite.
- Convert the transaction server to a microservices-based architecture.
- Redesign the operating system to support symmetrical multiprocessing.
The Importance of Timely Implementation
These changes are not simple refactors. They will involve significant, structural changes that could affect millions of lines of code and require dozens (or even hundreds) of person-years. And, if the enterprise wants to accomplish it next year or even the year after, it must start now.
To start now, this work needs to be defined and communicated to the team like any other major initiative, even though the end-user value may be a year or so down the road.
Collaborative Maintenance of the Architectural Runway
The System Architect/Engineer continuously maintains and evolves the architectural runway in collaboration with Agile teams, allowing for faster delivery of value to customers and reducing technical debt. It is critical to enable the product’s scalability, performance, and maintainability throughout its lifecycle.
How are SAFe Architectural Epics Implemented?
SAFe Architectural Epics are implemented through prioritization, analysis, implementation, and acceptance steps within the Portfolio Kanban system.
Architectural Epics in SAFe are significant initiatives that guide the evolution of the system’s technical aspects. Their implementation follows a structured approach within the Portfolio Kanban system.
- The Architectural Epic and its benefits are documented.
- Architectural Epics are prioritization based on the cost of delay or WSJF.
- Detailed analysis, including Lightweight Business Case development, follows.
- The implementation stage begins upon approval, spanning multiple Planning Intervals (PIs) if needed.
- The acceptance step concludes the process, validating that Epic’s intended benefits have been realized.
Architectural epics will be implemented incrementally in the main code line, just like any other epic. By doing so, development teams commit to a “do no harm” refactoring approach. In other words, they implement these large-scale refactors in small increments. At each PSI, they commit to “do no harm” to the systems or its users. They roll out the architectural changes piecemeal and reveal the new capabilities to the users only when there’s sufficient infrastructure to do so. It isn’t easy. It is agile. And it does work.
How is the SAFe Architectural Runway sustained?
You sustain the SAFe Architectural Runway by continuously implementing Enabler Epics and Enabler Stories.
Sustaining the Architectural Runway in SAFe involves a continual focus on implementing Enabler Epics and Enabler Stories. These elements enhance and extend the existing technical infrastructure, ensuring it stays aligned with current and future business needs. Regularly addressing the technical debt and investing in the system’s modularity, scalability, and security are other crucial aspects of maintaining a healthy Architectural Runway. This proactive approach ensures the system remains flexible and capable of supporting the swift, efficient delivery of new features.

What are the risks of neglecting the Architectural Runway?
The continuous build-out and maintenance of new architectural runways are the responsibility of all mature agile teams. Failing to do so will result in one of two negative outcomes:
- Release dates will be missed because large-scale, just-in-time infrastructure refactoring adds unacceptable risk to scheduling.
- Failure to systematically extend the architecture means teams eventually run out of runway. New features cannot be added without significant refactoring. Velocity slows. The system eventually becomes so brittle and unstable that it has to be entirely rewritten.
How is the Architecture Maintained at the Portfolio, Program, and Team Levels?
This work must happen continuously at each Portfolio, Program, and Team level.
Portfolio Level
The Scaled Agile Portfolio-level architectural runway is achieved by defining, communicating, and implementing architecture epics that drive the company’s technology vision. Some will require significant levels of investment and consume substantial resources. In the short term, some may even reduce the velocity of current and new feature implementations. Because failing to implement them will eventually compromise the company’s position in the market, architectural epics must be visible, estimated, and planned just like any other epic.
Program Level
At the Program level, product managers, system teams, project teams, and architects translate the architectural epics into architectural features relevant to each release. They are prioritized, estimated, and resourced like any other feature. And, like features, each architectural initiative must also be conceptually complete at each release boundary to not compromise the new release.
At the Team level, refactors and design spikes are often necessary to extend the runway and are prioritized along with user stories. This way, architectural work is visible, accountable, and demonstrable at every iteration boundary. This is achieved by agreement and collaboration with system architects, product owners, and agile tech leads, who determine what spikes need to happen and when.
What are Investment Themes?
Investment themes are categories of investments aligned to SAFe’s business strategy.
In SAFe, Investment Themes are broad categories that reflect the business’s strategic objectives and are used to guide resource allocation. They serve as a way to group Portfolio Epics that align with a particular business goal or strategy. This helps the organization ensure its investments align with strategic priorities and facilitates the decision-making process for funding and resource allocation.
Themes have a longer lifespan than epics and may remain mostly unchanged for a year or more.
Investment themes (or product themes) embody the initiatives that guide an enterprise’s investment in systems, products, applications, and services. They represent crucial product or service value propositions that offer market differentiation and competitive advantage. Collecting strategic investment themes for an enterprise or a business unit within an enterprise establishes the relative investment objectives for that entity. Managers are empowered to develop the initiative in the most economically and business-sensible manner for the enterprise within the partition (budget allocation). However, they typically can only exceed the budget or borrow resources from other themes with the agreement of the relevant stakeholders. Through this process, the enterprise exercises its fiduciary responsibility by directing investment towards agreed-upon business priorities.
What is the Scaled Agile Framework (SAFe)?
The Scaled Agile Framework (SAFe) is a set of organization and workflow patterns for implementing agile practices at an enterprise scale.
SAFe is a comprehensive guideline for large-scale, complex software systems. SAFe delivers Agile practices to individual teams and across teams of teams or Agile Release Trains (ARTs). By aligning the organization around value delivery and establishing a Lean-Agile mindset, SAFe aims to increase productivity, improve product quality, and foster faster time-to-market.
Why is Scaled Agile Requirements Management Important?
Scaled Agile Requirements Management facilitates alignment, visibility, and value delivery at scale in an Agile enterprise.
Requirements management in a SAFe context is central to aligning all Agile teams to deliver customer value. It ensures the requirements are visible, understandable, and actionable across all enterprise levels – from Portfolio to Program to Team. This alignment and transparency lead to improved productivity, quality, and customer satisfaction
What are the key benefits of implementing the SAFe Requirements Model?
Implementing the SAFe Requirements Model boosts an enterprise’s alignment, transparency, agility, and customer-value delivery.
Implementing the SAFe Requirements Model presents nine specific benefits for multi-team environments, and they are:
- Enhanced Alignment : The SAFe Requirements Model aligns teams, programs, and portfolios to strategic objectives, ensuring everyone is working towards the same goals.
- Improved Transparency : By making requirements traceable and visible at all levels, the model fosters transparency and improves decision-making.
- Increased Agility : The iterative nature of the SAFe Requirements Model allows organizations to adapt quickly to changes, making them more responsive to market shifts and customer needs.
- Customer-Centric Focus : The model’s emphasis on delivering customer value ensures products and services meet customer needs, improving customer satisfaction.
- Risk Reduction : Regular feedback and iterative development reduce the risk of major failures, as issues are be identified and addressed earlier in the process.
- Higher Quality Outputs : With continuous feedback and iterative refinement, the quality of the final product or service is likely to be higher.
- Efficient Resource Utilization : With clear, traceable, and actionable requirements, teams work more efficiently, reducing wasted time and resources.
- Improved Collaboration : The model fosters a culture of collaboration and shared understanding, promoting better communication within and across teams.
- Business Success : With a focus on delivering value to customers, the SAFe Requirements Model ultimately contributes to business success by creating products and services that customers want and need.
The SAFe Requirements Model ensures that requirements are clearly understood, traceable, and actionable across all organizational levels. It promotes alignment between business strategy and technology execution, boosting efficiency and effectiveness. Fostering iterative development and continuous feedback enhances the enterprise’s agility, enabling faster response to changing customer needs. It emphasizes delivering customer value, thus improving customer satisfaction and business success.
What is the connection between SAFe and the SAFe Requirements Model?
The SAFe Framework uses the SAFe Requirements Model to structure, manage, and track requirements at all levels.
In the context of SAFe, the Requirements Model serves as a tool for organizing and understanding the diverse requirements that emerge in an enterprise context. It aids in the translation of business goals into actionable development tasks, facilitating a smoother workflow from concept to cash. It’s built to accommodate Epics, Capabilities, Features, and Stories that represent different levels of granularity in the requirements.
What is the role of the SAFe Requirements Model in modern organizations?
The SAFe Requirements Model acts as a bridge between business strategy and technology execution in modern organizations.
The SAFe Requirements Model helps translate business strategy into technological execution. Structuring requirements at different levels – Epics, Capabilities, Features, and Stories – enables better communication, clearer understanding, and more efficient implementation of strategic initiatives across the organization.
What are the disadvantages of traditional requirement management?
Traditional requirements management methods often lead to delayed feedback, limited adaptability, and misalignment between business and technology teams.
Traditional methods are often linear and rigid, expecting requirements to be fully defined upfront and rarely adapting to changes. This approach results in delayed feedback loops and a lack of agility to respond to changing business needs. Moreover, these methods often struggle to align business strategy with technology execution, leading to miscommunication, misunderstandings, and solutions that don’t meet the intended business value.
How do SAFe and Traditional Requirements Models differ?
The SAFe Requirements Model is iterative, adaptable, and focuses on delivering customer value, contrasting with traditional models, which are linear, rigid, and often business-centric.
Unlike traditional linear and fixed models, the SAFe Requirements Model allows for iterative refinement and adaptation. It promotes continuous feedback and adjustments as a project progresses, ensuring the final product meets customer needs. Moreover, it focuses on delivering customer value rather than meeting rigid business requirements. This customer-centric approach, coupled with flexibility and adaptability, differentiates the SAFe Requirements Model from traditional ones.
How does the SAFe Requirements Model extend the Agile Requirements methods?
The SAFe Requirements Model expands traditional Agile methods to accommodate large-scale, complex enterprises.
Traditional Agile methods are excellent at the team level but struggle when scaling to larger organizations. The SAFe Requirements Model addresses this by introducing a hierarchical structure for requirements that aligns with the layered structure of large enterprises. It integrates Epics, Capabilities, Features, and Stories, ensuring that business objectives are effectively translated into actionable development tasks at all organizational levels.
What are the SAFe Core Competencies?
SAFe’s seven core competencies, including Agile Product Delivery, provide a holistic approach to delivering value in a Lean, Agile, and sustainable manner.
The Scaled Agile Framework (SAFe) defines seven core competencies, and they are:
- Lean-Agile Leadership: Inspires adoption of Agile practices.
- Team and Technical Agility: Enhances team capabilities and technical skills.
- Agile Product Delivery: Delivers customer value through fast, integrated delivery cycles.
- Enterprise Solution Delivery: Manages large-scale, complex solutions.
- Lean Portfolio Management: Aligns strategy and execution.
- Organizational Agility: Enables quick, decentralized decision-making.
- Continuous Learning Culture: Encourages innovation and improvement.
What are the SAFe Principles?
The SAFe Principles are a set of ten fundamental principles derived from Lean and Agile methodologies that guide the implementation of SAFe.
SAFe principles are guidelines derived from Agile practices and methods, Lean product development, and systems thinking to facilitate large-scale, complex software development projects. The ten principles that make up the SAFe framework are as follows:
- Take an economic view: This principle emphasizes the importance of making decisions within an economic context, considering trade-offs between risk, cost of delay, and various operational and development costs.
- Apply systems thinking: This principle encourages organizations to understand the interconnected nature of systems and components and prioritize optimizing the system as a whole rather than individual parts.
- Assume variability; preserve options: This principle highlights the importance of maintaining flexibility in design and requirements throughout the development cycle, allowing for adjustments based on empirical data to achieve optimal economic outcomes.
- Build incrementally with fast, integrated learning cycles: This principle advocates for incremental development in short iterations, which allows for rapid customer feedback and risk mitigation.
- Base milestones on an objective evaluation of working systems: This principle emphasizes the need for objective, regular evaluation of the solution throughout the development lifecycle, ensuring that investments yield an adequate return.
- Make value flow without interruptions: This principle focuses on making value delivery as smooth and uninterrupted as possible by understanding and managing the properties of a flow-based system.
- Apply cadence, and synchronize with cross-domain planning: This principle states that applying a predictable rhythm to development and coordinating across various domains can help manage uncertainty in the development process.
- Unlock the intrinsic motivation of knowledge workers: This principle advises against individual incentive compensation, which can foster internal competition, and instead encourages an environment of autonomy, purpose, and mutual influence.
- Decentralize decision-making: This principle emphasizes the benefits of decentralized decision-making for speeding up product development flow and enabling faster feedback. However, it also recognizes that some decisions require centralized, strategic decision-making.
- Organize around value: This principle advocates that organizations structure themselves around delivering value quickly in response to customer needs rather than adhering to outdated functional hierarchies.
Related Content
Mastering team and technical agility with safe.
Dive into this comprehensive exploration of Team and Technical Agility - a crucial element in contemporary organizations. This blog post intricately discusses its significance, association with the Scaled Agile Framework (SAFe), and the pivotal role it plays in achieving optimal business agility. Delve into the transformation from traditional to…
SAFe Practices: PI Planning
The SAFe planning process, particularly the Program Increment (PI) planning, is critical to achieving agile and efficient product development. By working together, key stakeholders ensure alignment and a shared understanding of product objectives and goals. Preparation activities for PI planning, the two-day PI planning event, and the outputs of…
Mastering Agile Product Delivery with SAFe
This comprehensive guide explores Agile Product Delivery in the context of the Scaled Agile Framework (SAFe). Through it, we delve into key aspects such as Business Agility, Customer Centricity, Design Thinking, Lean UX, and the principles of Developing on Cadence and Releasing on Demand. We further examine how to manage the Agile Release Train…
Implementing Essential SAFe
Discover how to effectively manage programs in a SAFe environment by understanding essential elements like Agile Release Trains, customer-centric strategies, and critical metrics to drive continuous improvement.
Name (required)
Email (required)
Privacy Preference Center
Privacy preferences.
Jira Software
Project and issue tracking
Content collaboration
Jira Service Management
High-velocity ITSM
Visual project management
- View all products
Marketplace
Connect thousands of apps and integrations for all your Atlassian products
Developer Experience Platform
Jira Product Discovery
Prioritization and roadmapping
You might find helpful
Cloud Product Roadmap
Atlassian Migration Program
Work Management
Manage projects and align goals across all teams to achieve deliverables
IT Service Management
Enable dev, IT ops, and business teams to deliver great service at high velocity
Agile & DevOps
Run a world-class agile software organization from discovery to delivery and operations
BY TEAM SIZE
Small Business
BY TEAM FUNCTION
Software Development
BY INDUSTRY
Telecommunications
Professional Services
What's new
Atlassian together.
Get Atlassian work management products in one convenient package for enterprise teams.
Atlassian Trust & Security
Customer Case Studies
Atlassian University
Atlassian Playbook
Product Documentation
Developer Resources
Atlassian Community
Atlassian Support
Enterprise Services
Partner Support
Purchasing & Licensing
Work Life Blog
Support for Server products ends February 15, 2024
With end of support for our Server products fast approaching, create a winning plan for your Cloud migration with the Atlassian Migration Program.
Assess my options

Atlassian Presents: Unleash
Product updates, hands-on training, and technical demos – catch all that and more at our biggest agile & DevOps event.
- Atlassian.com
- Business Strategy
- Docs & Reports
- Human Resources
- Marketing & Sales
- Product Management
- Productivity
- Project Planning
- Software Development / IT
SAFe lean business case template
By scaled agile, inc..
Create a lean business case for your portfolio epic based on SAFe agile practices
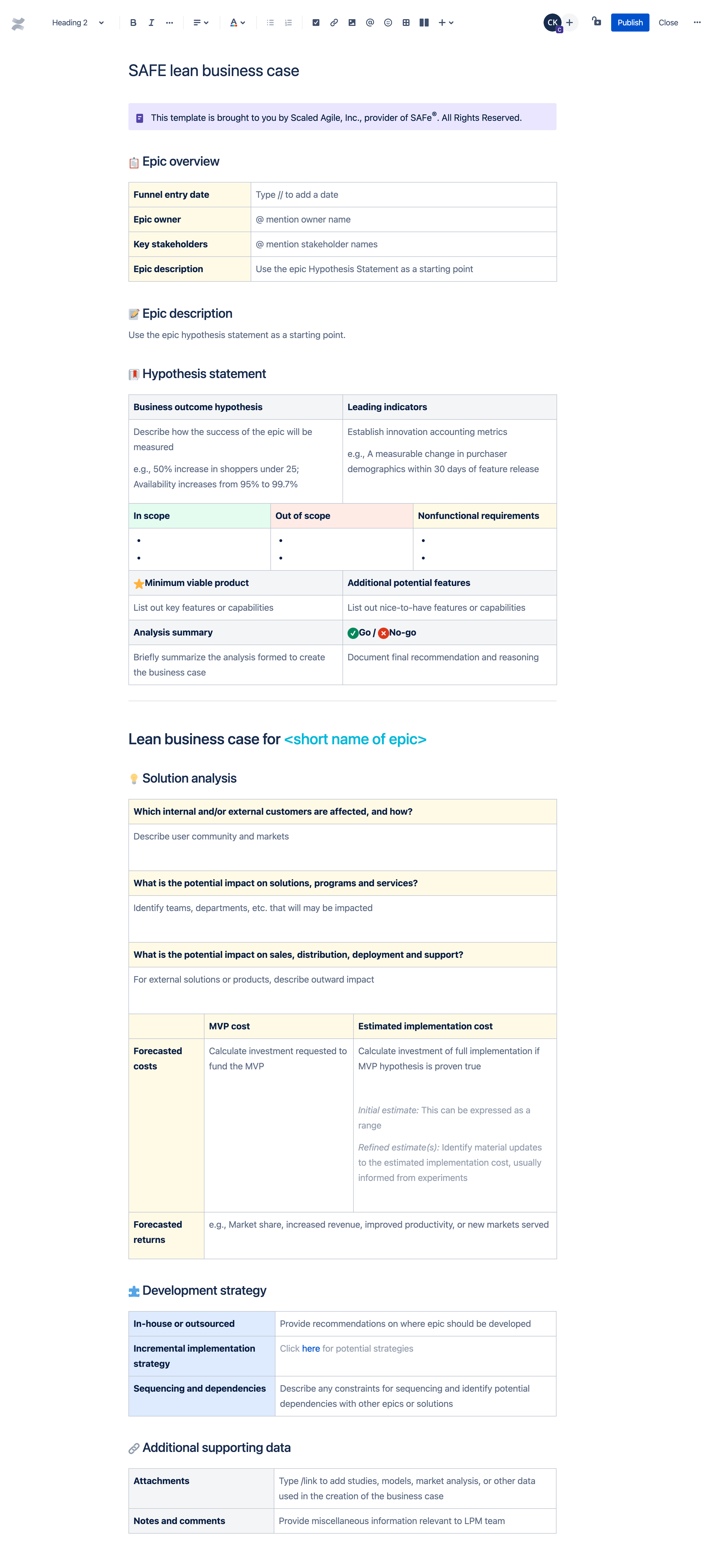
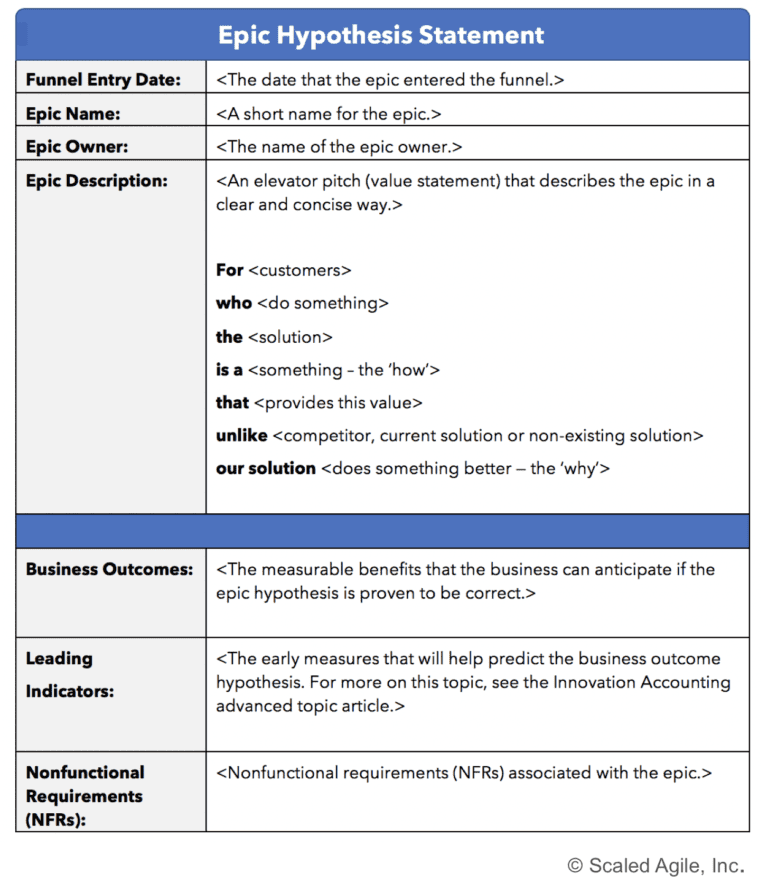
Having one standardized and organized method to keep track of all of your portfolio epics is essential to successful lean portfolio management . Moreover, adopting SAFe practices allows you to manage opportunities and risks via lean business cases that are implemented through the build-measure-learn SAFe Lean Startup Cycle . With this template, you’ll be able to document a business case based on a benefit hypothesis and a defined MVP, rather than a speculative ROI that would require the full potential investment. With Confluence, you can organize all of your portfolio epic documentation in one space, making it easy to analyze inputs, record decisions, and keep everyone aligned to a common objective. Read more on the SAFe epic article .
How to use the SAFe lean business case template
Step 1. determine the scope and details of the epic..
The creation of the business case is usually the primary responsibility of the epic owner. Before diving into the creation of your lean business case, set the stage for this portfolio epic. Make sure you are creating the lean business case at the right time. It is part of the analyzing phase of the portfolio Kanban system. Too early would create waste, and too late risks making investments without understanding the context. First, decide who will be involved in the proposal, to ensure that all sponsoring stakeholders are included. Then, concisely describe the epic, define how the success of the epic will be measured in the Business Outcomes Hypothesis, and establish what leading indicators will be used to indicate progress. This will help you determine the scope of the epic, and most importantly, how to define your MVP. Make sure to include any background analyses you conducted, and leave space to capture the final go/no-go recommendation.

Step 2. Create the lean business case.
Once you’ve laid down the groundwork, you’re ready to write the lean business case. Start by using the Epic Hypothesis Statement to describe the epic. This provides a short and concise way to define the business rationale, or the “why” of this Epic. Then define what is in and out of scope for this epic, as well as any nonfunctional requirements. Then define the MVP that will be used to test the hypothesis, as well as potential features this MVP will spawn Estimate the cost, preferably in the same currency used to run participatory budgeting . Don’t forget to provide an estimate of the overall cost of the Epic, once the MVP is successful. Lastly, document the kind of value return that is expected from the investment in the epic.
Step 3. Document any supporting data.
Document the solution analysis that was carried out during the analyzing phase. Reference any additional resources, links, and supporting evidence so other team members and stakeholders can access it easily. Ensure that the attachments are labeled, using the Notes and Comments section to jot down any miscellaneous evidence. All of this informs the upcoming go/no-go decision. Be careful of information overload. The lean business case was created to make the process of laying out a business case faster and to make the review process easier. Attaching too many support documents in this field can slow down the reviewers and negate some of the benefits. Alternatively, this space can be used to document notes during your team planning meetings.

Step 4. Keep the epic up to date.
As analysis and implementation of the MVP continue, keep the lean business case up to date to facilitate any portfolio review meetings or future portfolio funding.
Scaled Agile, Inc. is the provider of the Scaled Agile Framework (SAFe). Through courses, trainings, partners, and solutions, Scaled Agile, Inc. provides practices for scaling agile practices across the entire company. Through SAFe, they empower large and complex organizations to achieve the benefits of Lean-Agile software and systems development at scale.
More partners templates View all
1-on-1 meeting.
Run 1-on-1 meetings and maintain productive working relationships.
AWS architecture diagram
Visualize your infrastructure to better identify weaknesses and pinpoint places for refinement.
Brainstorming
Plan, run, and document a remote brainstorming session for your next great idea.

Epical epic. Agile epic examples
What is an agile epic, what to use it for, and foremost how?
Requirements. Small, large, technical, business, operational, and researchable. And above all, plenty of them. During four years of ScrumDesk development, we have more than 800 requirements in our backlog. And these are the only requirements that we have decided to implement without any further ideas that would be nice to have. It is, of course, difficult to navigate such a long list without any additional organization of the backlog structure. And this is where Epic comes to help.
Every Scrum or Agile training introduces the term Epic. In training sessions, epics are presented by only using one image, and essentially, they are not even explained assuming their simplicity. It is not rocket science. However, the question emerges as soon as a product owner starts preparing a backlog of the product. How to organize epics? What are they supposed to describe? How to organize them?
Epic is a set of requirements that together deliver greater business value and touch the same portion of the product, either functional or logical.
Agile Epic, similar to the requirement itself (often User story), is supposed to deal with a problem of single or multiple users and at the same time should be usable and valuable.
How to identify epic?
It is no science at all. Start with thinking about a product from a large perspective. Agile epic is a large high-level functionality. Their size is large, usually in hundreds of story points. However, all these chunks of functionalities must be usable end to end. In practice, we have encountered multiple approaches to epic design. Let’s try to see which one is the best for you.
Epics are managed by product management or other strategic roles. For smaller products, Product Owners identify them. Agile epics help structure your work into valuable parts that can be developed faster while delivering value to users.
I. Epic as a part of the product
Epic can represent a large, high-level yet functional unit of the product. For example, in ScrumDesk we have epics BACKLOG, PLAN, WORK, REPORTS. In the app, you can find parts, and modules, which are called the same way as a given epic.
Top epics of the ScrumDesk product
This backlog organization is appropriate when you are creating a product that you are going to be developing in the long run.
Why use this method of epic organization?
- As a product owner, you simply have to be able to orientate yourself in parts of the product and know what you have or have not finished yet.
- At the same time, it is easy to measure progress by parts of the product.
- The Product Owner is naturally urged to change the order of features in the epic , which leads to the creation of rapid delivery of a minimum of viable product increments .
The disadvantage of this method is the lacking view of the user journey It is not visible which parts of the backlog cover what parts of the user value flow. E.g. process from registration, and basket to payment. Each part of the process can belong to a different epic.
Epics, in this case, do not end here, they are not concluded because the functional unit is delivered in the long term. In years. In the roadmap, the implementation of level features of individual epics is planned.
II. Epic as a part of the business flow
This approach is based on the fact, that we know the flow of values, meaning a business process that we can divide into individual parts and then make it more detailed and deliver iteratively. High-level functionalities follow the business workflows.
Epics by the business workflow
For example, an e-shop. Agile epics candidates would be:
- Product catalog viewing – for portraying categories of goods and a list of goods in each category, filtering and searching for goods.
- Product selection – a selection of interesting products such as favorites, comparing, pricing, or adding to a cart.
- The Cart of the products – browsing the content of a basket, comparing, and counting the total price.
- Payment – choice of payment options, total order, total price, shipping, the payment itself, and payment confirmation.
- Product delivery – a visual display of the delivery status, email, and SMS notifications.
The product owner is naturally able to focus on the delivery of the whole customer’s experience . The first fully functional version is then created quite quickly and is subsequently improved iteratively. Epic Payment is based on VISA, transfer, and cash. In the first version, only Visa payment will be delivered, transfer and cash in the next one.
The development of epics takes a longer time in this case. It does not usually make sense to close them, as they will be further elaborated in the future by other features. Business easily understands the state of the implemented application (e-shop) which simplifies communication and significantly improves cooperation between IT and business. It is important to use commercial terms rather than technological ones.
III. Project as epic
Do you deliver products to a client in various phases and various projects? In this case, it may be easier to create epics according to projects or the project’s phases.
Epics as project or phase
Such epics are usually considered finished (closed) when the project is delivered. The advantage is obvious. There is an absolutely clear state of implementation of the project. Participants and stakeholders have excellent transparency. At the same time, stakeholders can focus on preparing for the next phase of the project.
On the other hand, it can be quite difficult to keep an overview of the functionalities units of the product itself. The state is more perceived by architects rather than the business itself. In real life, we also came across seeing this way to lead to a change in the company’s focus, or even to the degradation of its vision. A company that once wanted to act as a product and solution maker became a company fully listening to clients. Their products became a ‘toy’ in the hands of clients which led to people leaving teams because they have lost the personal connection with the product. They often lose the power to say NO.
It is also practical to use themes for further categorization of requirements . This creates a virtual matrix, in which each requirement belongs to a certain product set and also might belong to a business theme that is communicated to clients. In ScrumDesk we use, for example, themes for identifying clients who had requested larger sets of features, and we, after all, decided to include them in backlogs. As a product owner, I know how to communicate the status of requirements with a client while still keeping my eyes on the implementation of the product itself.
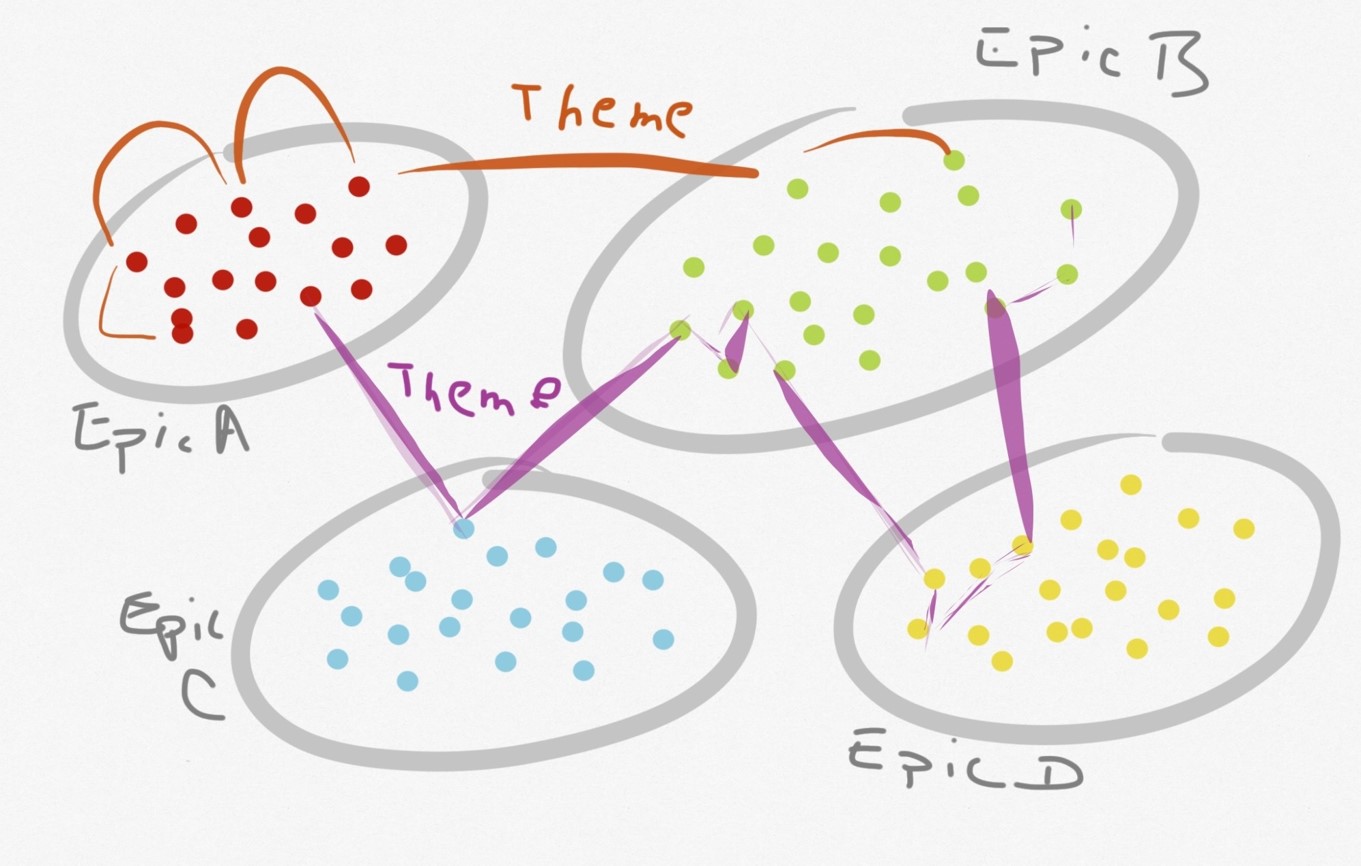
Epics and Themes
Themes in the product world are often determined by top management at strategic meetings and these topics are subsequently implemented in multiple value streams supported by multiple products. An example of such strategic themes can be 3D Maps, AI (Artificial Intelligence) in risky investments, and traveling without physical gates and cards.
Artificial Epics
In addition to business logic, an application has many parts that create a basic core of a product, but a customer rarely notices them.
First of all, you need to think about and register, for example, the design of architecture, suggestion of UX layout of an app, initial frameworks, and technological preparation. In later phases, the functionalities are still touching the entire product at once. E.g. logging, error handling etc. In ScrumDesk we had an epic called #APPLICATION for such requirements.
When we started four years ago, we decided to keep all bugs in epics titled #TECH. Symbol # indicates artificial epic.
Later we changed this strategy and now we are trying to put every requirement, regardless of its type, under the right epic, as the epic either repairs or expands, improves from the technological point of view.
Epic and business value
In Agile, each requirement should deliver additional business value. However, in the case of more complex applications, it is almost impossible to evaluate the value supplied at such a low level. In this case, it is easier to determine the business value at the level of epic . Epic then can analyze, suggest and prepare ahead of implementation itself beforehand.
It is also possible to create a business case and consequently the business value itself. Such an approach is recommended, for example, Scaled Agile Framework, in which the epic adds value to the selected value stream.

Epics in SAFe
How to prepare epics?
Product Owner prepares epics in advance, prior to planning and implementation.
For good preparation he needs support from multiple people:
- an architect for a rough design of the architecture that is needed to implement the epic,
- stakeholders, for whom the functionality will be delivered, for business value determination and business case,
- UX Designer to work out framework principles of interface design and usability of the epic,
- People from service and support for a good design of epic from the operational perspective,
- And whoever else is needed
PREARE EPICS IN SCRUMDESK FOR FREE
Preparation of an epic can, and often has a different process than the requirements themselves. In SAFe ‘Portfolio Kanban’ is recommended for the preparation of epics. Therefore, a separate Kanban board with multiple statuses exists on which the momentum of the epic realization is transparently displayed. This creates space for regular meetings of a small team preparing requirements ahead and continuous improvement of epic details.
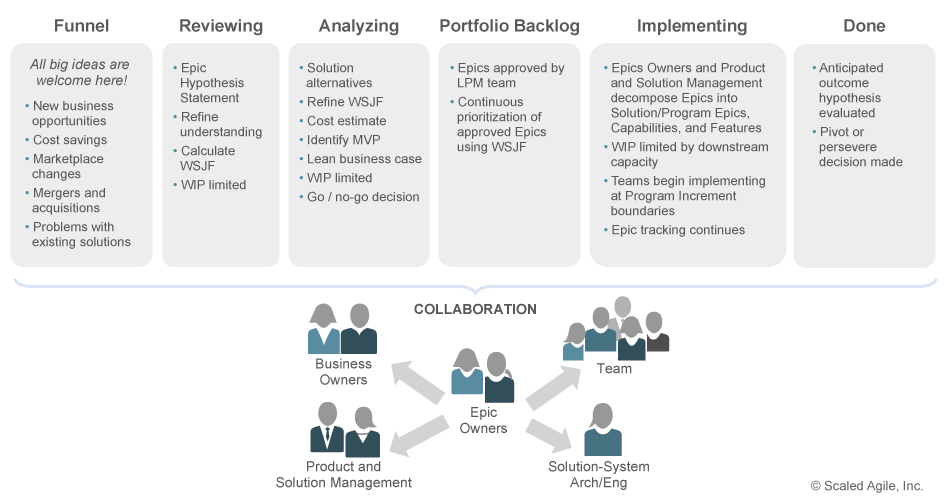
Portfolio Kanban systems for epics management
The Product Owner basically works in two-time spaces. In the first one, he prepares epics for the future, and in the second he contributes to the implementation of already developed epics.
How ScrumDesk helps with epics?
ScrumDesk supports epics from its first version. As we use ScrumDesk for the development of the ScrumDesk, we identified and tried different approaches to backlog organization. In the first version epics were just titles, later we added possibilities to:
- add more details in the description of the epic,
- visualize epics as colored cards in user stories map,
- added an option to track the business value, risk, effort (as an aggregation of child requirements),
- break down epics into features and/or user stories to manage complex backlogs,
- track comments and changes,
- attach files (i.e. business cases),
- possibility to add the timeline for epics and features with the support of agile roadmaps displaying not just plans, but comparing them to reality as well.
Common mistakes
- Epic by technology layer. Database, backend, frontend. Functionality is not covered end-to-end, it only supplies parts of it.
- Epic by product version. The product version is a set of properties from different epics. Unlike the epic, the version has a timeline as well.
- Epic by a customer (stakeholder) to which part of the functionality is being delivered. If you need to evidence the customer, evidence it in a separate attribute and organize the epics according to the procedures above.
- When the product assumptions change, the form of epic organization will not readjust. Adapt and select appropriate approaches as needed. Do not be afraid to work with the backlog and change it so you can orient quickly, you can choose other ways of epics organization and especially to have it transparent for the team as well as stakeholders.
- https://www.flickr.com/photos/sebrendel/8155603332
- http://www.scaledagileframework.com/epic/
- http://www.scaledagileframework.com/portfolio-kanban/
Found this interesting? Share, please!
About the author: dusan kocurek.
The ART of SAFe
Applying Lean and Agile techniques at scale to bring about effective, sustainable improvement in Culture, Execution and Business Results
Monday, January 8, 2018
Effective feature templates for safe, introduction, how much detail is needed, and by when.
- Prior to WSJF assessment
- Prior to PI Planning
Feature Canvas
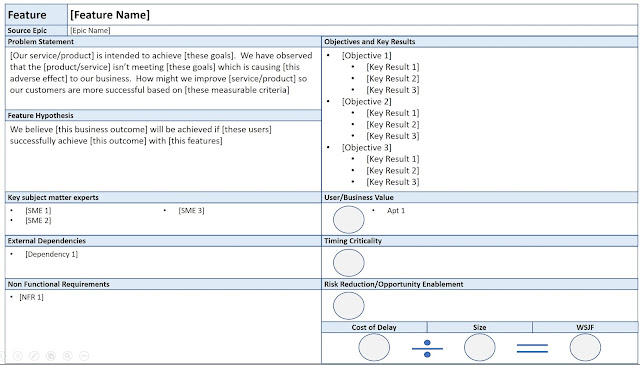
New Product: “The current state of the [domain] has focussed primarily on [customer segments, pain points, etc]. What existing products/services fail to address is [this gap] Our product/service will address this gap by [vision/strategy] Our initial focus will be [this segment]”
Existing Product: “Our [service/product] is intended to achieve [these goals]. We have observed that the [product/service] isn’t meeting [these goals] which is causing [this adverse effect] to our business. How might we improve [service/product] so that our customers are more successful based on [these measurable criteria]?”
“We believe this [business outcome] will be achieved if [these users] successfully achieve [this user outcome] with [this feature]”.
Sample Completed Canvas
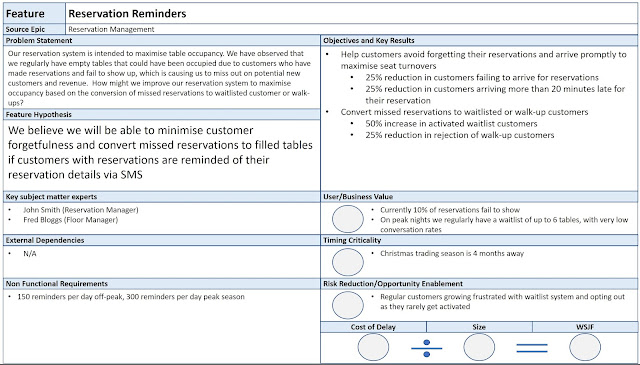
A glimpse at how you might visualise your next WSJF estimation workshop

Detail beyond the Canvas
- User Journeys: Some framing UX exploration is often very useful in preparing a Feature, and makes a great support to teams during PI planning.
- Architectural Impact Assessment: Some form of deliberate architectural consideration of the potential impact of the feature is critical in most complex environments. It should rarely be more than a page – I find a common approach is one to two paragraphs of text accompanied by a high level sequence diagram identifying expected interactions between architectural layers.
- Change Management Impacts: How do we get from deployed software to realised value? Who will need training? Are Work Instructions required?
Tuning your Template
Who completes the canvas/template, 28 comments:.
Awesome work Mark! We have created some for clients too that we can't share. :-(
Thanks for sharing Mark - these are really useful. I really like the hypothesis statements for features and think that this is a major enhancement in SAFE 4.5. I wrote a blog post about it here: http://runningmann.co.za/2017/09/25/the-power-of-feature-hypotheses/ that you might be interested in.
These are awesome Mark. Thanks for sharing
Thanks for sharing your experience on this area with the community Mark. Feature Templates are a very common requirement for Agile practitioners, maybe you can persuade the SAFe community to include an artefact like this in the framework.
Information was good,i like your post. Looking forward for more on this topic. product management
This is great! Do you have the template format available so we don't have to replicate?
great stuff, how would you differentiate this from SAFe Epics
Other problems include editing resistance, lack of or significantly delayed communications and lack of professionalism. website
I discovered your blog site site on the search engines and check several of your early posts. Always maintain up the very good operate. I recently additional increase Rss to my MSN News Reader. Looking for toward reading much more on your part later on!… apple tablet mockup
I genuinely treasure your work , Great post. ipad mockups
When I originally commented I clicked the -Notify me when new surveys are added- checkbox and from now on every time a comment is added I buy four emails with similar comment. Perhaps there is any way you are able to eliminate me from that service? Thanks! web design company san francisco
Good post and a nice summation of the problem. My only problem with the analysis is given that much of the population joined the chorus of deregulatory mythology, given vested interest is inclined toward perpetuation of the current system and given a lack of a popular cheerleader for your arguments, I’m not seeing much in the way of change. web design company san francisco
Cutting up pictures, reestablishing of old photos, working around with watermarks, and other progressed tips and deceives can likewise be found in a high caliber and significant Adobe photograph shop instructional exercise. Professional graphic design
Very efficiently written information. It will be beneficial to anybody who utilizes it, including me. Keep up the good work. For sure i will check out more posts. This site seems to get a good amount of visitors. essay writing service
Their willingness to partner with us has been great. UI design agency
Hey enormous stuff or pleasant information you are offering here. best branding agencies
Nice blog Mark How can I get a downloadable version of this Canvas?
I think you can make video about it. If you want to promote your channel on youtube you can buy youtube subscribers for it
Thanks for this incredible information. I think you could make a video about feauture templates for sale and post it on Instagram. By the way if you want to get more followers for your profile, you can repeatly use the help of https://viplikes.net/buy-instagram-followers to quickly boost their number.
Socialize Club- Buy Facebook live stream views cheap in price but high in quality.We provide you with 100% Real Facebook live stream views delivered at your facebook live video instantly.
Packaging should function as a barrier to air, water vapor, dust, and other contaminants. Because food items might be in liquid form, they must be leak-proof to avoid loss during transportation. BOPP film supplier
percetakan buku online di jakarta percetakan murah jakarta percetakan online jakarta percetakan Jakarta timur cetak murah jakarta cetak online jakarta digital printing jakarta print murah jakarta jasa print murah cetak buku murah di jakarta timur
I use the aforementioned off-page SEO techniques and am currently seeing the results of my labors with page 1 Google search engine rankings. For example, Deanna Hibbs, a full-time working mother, discovered internet marketing while searching for a work schedule other than 9 to 5. SEO philadelphia
thank you for share an informative blog article with us. kitimesblog
Essential phases
This comment has been removed by the author.
We are back in Europe and hope you join us!

Prague, Czech Republic, 15 – 17, May 2023

Evolving the Scaled Agile Framework:
Update to SAFe 5
Guidance for organizing around value, DevSecOps, and agility for business teams

- SAFe Contributors
- Extended SAFe Guidance
- Community Contributions
- SAFe Beyond IT
- Books on SAFe
- Download SAFe Posters & Graphics
- Presentations & Videos
- FAQs on how to use SAFe content and trademarks
- What’s new in the SAFe 5.1 Big Picture
- Recommended Reading
- Learn about the Community
- Member Login
- SAFe Implementation Roadmap
- Find a Transformation Partner
- Find a Platform Partner
- Customer Stories
- SAFe Training
Luck is what happens when preparation meets opportunity. —Seneca
Enablers bring visibility to all the work necessary to support efficient development and delivery of future business requirements. Primarily, enablers are used for exploration, evolving the architecture, improving infrastructure and compliance activities. Since enablers reflect real work they cannot remain invisible. Instead, they’re treated like all other value-added development activities—subject to estimating, visibility and tracking, Work in Process (WIP) limits, feedback, and presentation of results.
Type of Enablers
Enablers can be used for any activities that support upcoming business requirements and generally fall into one of four categories:
- Exploration enablers – These support research, prototyping, and other activities needed to develop an understanding of customer needs, including the exploration of prospective Solutions and evaluating alternatives.
- Architectural enablers – These are created to build the Architectural Runway , which allows smoother and faster development.
- Infrastructure enablers – These are created to build, enhance, and automate the development, testing, and deployment environments. They facilitate faster development, higher-quality testing, and a faster Continuous Delivery Pipeline .
- Compliance enablers – These facilitate managing specific compliance activities, including Verification and Validation (V&V), documentation and signoffs, and regulatory submissions and approvals.
Creating and Managing Enablers
Enablers exist throughout the Framework and are written and prioritized to follow the same rules as their corresponding epics, capabilities, features, and stories.
- Enabler Epics – Are written using the ‘Epic Hypothesis Statement’ format, in the same way as business epics. Enabler epics typically cut across Value Streams and Program Increments (PIs) . To support their implementation, they must include a ‘Lean Business Case’ and are identified and tracked through the Portfolio Kanban system.
- Enabler Features and Capabilities – Defined by Agile Release Trains (ARTs) and Solution Trains . Since these enablers are a type of Feature or Capability , they share the same attributes, including a short phrase, benefit hypothesis and acceptance criteria. They also must be sized to fit within a single PI.
- Enabler Stories – Must fit in Iterations like any Story . Although they may not require the user voice format, their acceptance criteria clarify the requirements and support testing.
Enablers are often created by architects or by engineering. They might be Enterprise Architects supporting the portfolio backlog, or System and Solution Architects/Engineers supporting ARTs and Solution Trains . Architects steer enablers through the Kanban systems, providing the guidance to analyze them and the information to estimate and implement them.
To improve the existing solution, some enablers will emerge locally from the needs of the Agile Teams , ARTs or solution trains to ensure that enough emphasis is placed on furthering the solution and extending the architectural runway. Those that make it through the Kanban systems will be subject to capacity allocation in the Program and Solution Backlogs . This can be applied for enabler work as a whole, or it can distinguish between different types of enablers.
Applying Enablers
Exploration.
Applying enablers for exploration provides a way for Agile teams to discover the details of requirements and design. The nature of Solution Intent is that many requirements begin as variable intent. After all, at the beginning of development little is known about what the customer needs or how to implement it. Customers themselves often don’t understand exactly what they want. Only through iterative product development and demos do they begin to figure out what they need and the solution intent can become fixed.
On the solution side, there are many technical possibilities for how to implement a business need. Those alternatives must be analyzed and are often evaluated through modeling, prototyping, or even concurrent development of multiple solution options (also known as Set-Based Design ).
Architecture
The architectural runway is one of the constructs SAFe uses to implement the concepts behind Agile Architecture . The runway is the basis for developing business initiatives more quickly, on appropriate technical foundations. But the runway is constantly consumed by business epics, features, capabilities, and stories, so it must be maintained. Enablers are the backlog items used to maintain and extend the runway.
Some architectural enablers fix existing problems with the solution—for example, the need to enhance performance. These enablers start out in the backlog, but after implementation, they may become Nonfunctional Requirements (NFRs) which can be considered constraints on new development. In fact, many NFRs come into existence as a result of architectural enablers and tend to build over time, as can be seen in Figure 1.
Infrastructure
Agile development is built on frequent integration. Agile teams integrate their work with other teams on the ART at the System Demos in every iteration. The trains that are part of a Solution Train integrate every PI as part of the Solution Demo . Many Enterprises implement Continuous Integration and Continuous Deployment to ensure that the solution is always running. This reduces the risk at the integration points and permits deployment and early release value.
The System Team assists one or more ARTs in building and using the Agile development environment infrastructure—including the continuous delivery pipeline toolchain—as well as integrating assets from Agile teams. Infrastructure enablers are used as backlog items to advance this work, both to support new user scenarios and to enhance the agility of the enterprise.
By incrementally building the necessary artifacts in the Solution Intent over a series of PIs, SAFe supports continuous verification and validation. Verification activities are implemented as part of the normal workflow (e.g., backlog items or Definition of Done [DoD]). While the artifacts will satisfy the objective evidence needed at the end of development, they are created iteratively throughout the life cycle. Validation occurs when Product Owners, customers, and end-users participate in ART planning and system demos, validating fitness for purpose.
For example, consider that regulations often require design reviews and that all actions need to be recorded and resolved. The design review enabler backlog item offers evidence of the review, and its DoD ensures that actions are recorded and resolved according to the Lean Quality Management System (QMS). If needed, the actions themselves could be tracked as enabler stories. Regulations may also require that all changes be reviewed, which is addressed by a compulsory peer review DoD for all stories.
Implement Architectural Enablers Incrementally
The size and demands of architectural enabler work can make it overwhelming. So, it’s important to remember that it needs to be broken down into smaller stories that fit in an iteration. This can be difficult, however, as architectural and infrastructure changes can potentially stop the existing system from working until the new architecture/infrastructure is in place. When planning enabler work, make sure to organize it so that the system can operate for most of the time on the old architecture or infrastructure. That way, teams can continue to work, integrate, demo, and even release while the enabler work is happening.
As described in [1], there are three options:
- Case A – The enabler is big, but there is an incremental approach to implementation. The system always runs (operates).
- Case B – The enabler is big, but it can’t be implemented entirely incrementally. The system will need to take an occasional break.
- Case C – The enabler is really big, and it can’t be implemented incrementally. The system runs when needed. In other words, do no harm.
Examples of incremental patterns are also described in [2], where the legacy subsystems are gradually ‘strangled’ over time, using proven patterns such as asset capture or event interception.
By creating the technology platforms that deliver business functionality, enablers drive better economics. But innovative product development cannot occur without risk-taking. Therefore, initial technology-related decisions cannot always be correct, which is why the Lean enterprise must be prepared to change course on occasion. In these cases, the principle of sunk costs [3] provides essential guidance: Do not consider money already spent. Incremental implementation helps, as the corrective action can be taken before the investment grows too large.
Implement Enabler Epics Across ARTs and Value Streams
Enabler epics and enabler capabilities can cut across multiple value streams or ARTs. During the analysis phase of the appropriate Kanban system, one of the important decisions to make is whether to implement the enabler in all Solution Trains/ARTs at the same time or to do so incrementally. This is a trade-off between the risk reduction of implementing one solution or system at a time versus the Cost of Delay (CoD) caused by not having the full enabler, as Figure 2 illustrates.
Last update: 10 February 2021
Privacy Overview
Functional cookies help to perform certain functionalities like sharing the content of the website on social media platforms, collect feedbacks, and other third-party features.
Performance cookies are used to understand and analyze the key performance indexes of the website which helps in delivering a better user experience for the visitors.
Analytical cookies are used to understand how visitors interact with the website. These cookies help provide information on metrics the number of visitors, bounce rate, traffic source, etc.
Advertisement cookies are used to provide visitors with relevant ads and marketing campaigns. These cookies track visitors across websites and collect information to provide customized ads.
Other uncategorized cookies are those that are being analyzed and have not been classified into a category as yet.
- Integrations
- Get in touch Get in touch
- Getting Started Guide
- Product Updates
- Get in touch
- How to Start
- First Steps
- Views: Setup & Usage
- Work With Entities
- Track and Measure Progress
- Testing Module/QA Area
- Integrations & API
- Install, Upgrade & Maintenance
- Legal Notes
- Featured Articles
- Filters & Search
- Reports & Dashboards
- Mashups Library
- Service Desk
- Troubleshooting
- Video Tutorials
- Estimating & Planning
- Bug Tracking
- Import & Export Data
- Administration & Settings
- Pricing, Payment & Billing
- Email Support
- Support Desk
- Developers & API
- Request Demo
- Blog & Articles
- Lean Budgeting
Epic Hypothesis Statement (EHS)
- Value Stream Enablement
- Budgeting by Custom Period
- Requirement Enablement
- Work Estimated Cost
- Lean Business Case (LBC)
- Lean Budgeting: Portfolio Epic MVP Cost
- Capacity allocation by value type: Business, Enabler, Technical Debt
Requires the following solution to be installed:
- Requirement Enablement (eaf4ecf8-6dfc-43a7-84b7-e637c70a487e)
Can be extended with the following solution:
- Lean Business Case (1a187fc1-5375-4b6f-b994-ffc74651c666)
- Lean Budgeting: Portfolio Epic MVP Cost (03b2ead1-4496-4c10-bb88-4dfbd1d4c627)
Solution Overview
Since Portfolio Epics are some of the most significant enterprise investments, stakeholders must agree on their intent and definition. The solution enables a Portfolio Epic Hypothesis Statement template (a new tab) for capturing, organizing, and communicating critical information about a Portfolio Epic .
Hypothesis Statement tab contains the following information:
- Funnel Entry Date – shows the date that the Portfolio Epic entered the funnel, i.e. have been created.
- Key Stakeholders – defines a list of Portfolio Epic stakeholders. By default, you'll see here the list of roles responsible for a Portfolio Epic. To add Key Stakeholder and Portfolio Epic Owner roles for a Portfolio Epic , please follow the steps described here .
- Epic Hypothesis Statement – describes a Portfolio Epic from hypothesis statement perspective. Read more details here .
- Business Outcomes – defines how the success of the Portfolio Epic will be measured. For example, 50% increase in shoppers under 25 ; Availability increases from 95% to 99.7% , etc.
- Leading Indicators – e stablishes innovation accounting metrics to provide leading indicators of the outcomes hypothesis. For example: A measurable change in purchaser demographics within 30 days of feature release .
- Non-Functional Requirements - N on-Functional Requirements (NFRs) associated with the Portfolio Epic .
Solution Installation
When you install the solution, it won't automatically add Hypothesis Statement template to existing Portfolio Epics . To fill the field with the template please do the following:
- Open Settings -> Automation Rules
- Set Hypothesis Statement for existing Portfolio Epics
- Click Save and trigger now button
- Disable the rule after run
As a result the existing Portfolio Epics will have Hypothesis Statement template added:
----------------
Version 1.1
Still have a question?
We're here to help! Just contact our friendly support team

IMAGES
VIDEO
COMMENTS
Figure 2 provides an epic hypothesis statement template for capturing, organizing, and communicating critical information about an epic. Figure 2. ... The Epic Owner updates the forecasted completion once work begins on the epic. Implementing Epics. The SAFe Lean startup strategy recommends a highly iterative build-measure-learn cycle for ...
Figure 2 provides an epic hypothesis statement template that can be used to capture, organize, and communicate critical information about an epic. Figure 2. Epic hypothesis statement. ... Continued investment in an Epic that has a dis-proven hypothesis requires the creation of a new epic and approval from the LPM Function. SAFe Lean Startup Cycle
Epic Hypothesis Statement. Funnel Entry Date: <The date that the epic entered the funnel.>. Epic Name: <A short name for the epic.>. Epic Owner: <The name of the epic owner.>. Epic Description: <An elevator pitch (value statement) that describes the epic in a clear and concise way.>.
The SAFe® Epic - an example. We often have questions about what a "good" sufficiently developed SAFe Epic looks like. In this example we use with clients during the Lean Portfolio Management learning journey, we dive into an example of real-world details behind an epic hypothesis statement. For now, we have not provided a fully developed ...
Writing a great hypothesis. Having a clear outcome is not enough. We need to have an idea about how to get there. But unlike a business case, we are open and honest about the very real possibility ...
In SAFe, large initiatives are represented as Epics and are captured using an epic hypothesis statement ... Before attempting to design and build the entire initiative, the epic hypothesis statement template should be used to develop a business outcomes hypothesis, define leading indicators and gain knowledge regarding the expected outcome (see ...
Developing a Winning Epic Hypothesis Statement that Captivates Stakeholders using SAFe. The Scaled Agile Framework®, or SAFe, was created in 2011 and built upon the classic Agile manifesto by incorporating key ideas from the Lean methodology. Organisations using this framework can accomplish a wide range of advantages, according to SAFe ...
What are the key elements of a SAFe Epic Statement? An Epic Statement comprises a brief description, the customer or business benefit, and the success criteria. ... Feature Statement and Template. In the SAFe Requirements Model, a feature is typically documented using the following: Field ... Hypothesis testing in Agile, particularly in fields ...
This is a significant endeavor that will consume a considerable amount of time and money. Before attempting to design and build the entire initiative, the epic hypothesis statement template should be used to develop a hypothesis, test assumptions, and gain knowledge regarding the expected outcome (see Figure 3). Figure 3. Epic hypothesis statement
The Epic Hypothesis Statement expands on the raw concept presented during the funneling phase of the Portfolio Kanban system. Initially, the idea comprised a single concept, such as "adding self-service tools to the customer's loan management portal.". As the Epic Owner, you must hash out this basic idea into a fully developed initiative.
A SAFe portfolio contains one or more Development Value Streams, ... the epic hypothesis statement and the lean business case can be used to define and further elaborate ... The BMC is a one-page template that summarizes the most important aspects of a business model, as illustrated in Figure 10. Figure 10. The Business Model Canvas. Download ...
An important part of defining epics is an Epic Hypothesis Statement. It is an template for capturing, organizing and communicating critical information about an epic. Below figure shows a template ...
Follow this real-world example. Anthony Crain Delivery Manager, Agile Transformation, Cprime. Many of my clients get confused about epics when moving to a Scaled Agile Framework (SAFe) and the SAFe Portfolio Kanban. But one day, in a recent training class, I stumbled upon an example that resonated with everyone and brought clarity to the model.
The Epic Hypothesis Statement is a structured format used to capture, organize, and communicate critical information and assumptions about an epic. Share Post Previous Post Team Sync. Next Post Estimating Poker Subscribe to the SAFe Blog. Recent Posts. Brand New Articles: Extensive Update to AI, Measuring SAFe Success, and Operating Value ...
How to use the SAFe lean business case template . Step 1. Determine the scope and details of the epic. ... Start by using the Epic Hypothesis Statement to describe the epic. This provides a short and concise way to define the business rationale, or the "why" of this Epic. Then define what is in and out of scope for this epic, as well as any ...
I. Epic as a part of the product. Epic can represent a large, high-level yet functional unit of the product. For example, in ScrumDesk we have epics BACKLOG, PLAN, WORK, REPORTS. In the app, you can find parts, and modules, which are called the same way as a given epic. Top epics of the ScrumDesk product.
Introduction. Features are the key vehicle for value flow in SAFe, yet they are also the source of much confusion amongst those implementing it. The framework specifies that "Each feature includes a Benefit Hypothesis and acceptance criteria, and is sized or split as necessary to be delivered by a single Agile Release Train (ART) in a Program ...
The Portfolio Kanban system is a method to visualize and manage the flow of portfolio Epics, from ideation through analysis, implementation, and completion. There are several Kanban systems used throughout SAFe, including the team, program, solution, and portfolio Kanban systems. Each kanban system helps improve the flow of value through the ...
Figure 1. SAFe Requirements Model. For example, a Feature is described by a phrase, benefit hypothesis, and acceptance criteria; a Story is elaborated by a user-voice statement and acceptance criteria. These artifacts mostly replace the traditional system and requirements specifications with new paradigms based on Lean-Agile development.
An Enabler supports the activities needed to extend the Architectural Runway to provide future business functionality. These include exploration, architecture, infrastructure, and compliance. Enablers are captured in the various backlogs and occur throughout the Framework. Enablers bring visibility to all the work necessary to support efficient ...
Solution Overview. Since Portfolio Epics are some of the most significant enterprise investments, stakeholders must agree on their intent and definition. The solution enables a Portfolio Epic Hypothesis Statement template (a new tab) for capturing, organizing, and communicating critical information about a Portfolio Epic.
PK !iÃ*fƒ Ú [Content_Types].xml ¢ ( ´•ËjÃ0 E÷…þƒÑ¶ØJº(¥ÄÉ¢ e hú Š4¶EmIH"×ßw ;¡„$.M¼1Ø3÷Þ# ŒG"uUFKðA["²a2` i•6yʾfoñ#‹ £Di ¤l MÆ·7£ÙÆAˆHmBÊ D÷Äy T"$Ö ¡Jf}% ^}Î ß" ~?
Features and Capabilities. A Feature represents solution functionality that delivers business value, fulfills a stakeholder need, and is sized to be delivered by an Agile Release Train within a PI. Each feature includes a benefit hypothesis and acceptance criteria and is sized or split as necessary to be delivered by a single Agile Release ...