- Skip to content
- Skip to search
- Skip to footer

VLAN Configuration Guide, Cisco IOS XE 17.13.x (Catalyst 9200 Switches)
Bias-free language.
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Configuring VTP
- Configuring VLANs
- Configuring Voice VLANs
- Configuring VLAN Trunks
Configuring Private VLANs
- Configuring Wired Dynamic PVLAN

Chapter: Configuring Private VLANs
Prerequisites for private vlans, restrictions for private vlans, private vlan domains, secondary vlans, private vlans ports, private vlans in networks, ip addressing scheme with private vlans, private vlans across multiple devices, private vlans and unicast, broadcast, and multicast traffic, private vlans and svis, private vlans and switch stacks, private vlan with dynamic mac address, private vlan with static mac address, private vlan interaction with vacl/qos, private vlans and ha support, default private-vlan configurations, secondary and primary vlan configuration, private vlan port configuration, configuring and associating vlans in a private vlan, configuring a layer 2 interface as a private vlan host port, configuring a layer 2 interface as a private vlan promiscuous port, mapping secondary vlans to a primary vlan layer 3 vlan interface, monitoring private vlans, example: configuring and associating vlans in a private vlan, example: configuring an interface as a host port, example: configuring an interface as a private vlan promiscuous port, example: mapping secondary vlans to a primary vlan interface, example: monitoring private vlans, where to go next, additional references, feature history for private vlans.
When configuring private VLANs on the device, always use the default Switch Database Management (SDM) template to balance system resources between unicast routes and Layer 2 entries. If another SDM template is configured, use the sdm prefer default global configuration command to set the default template.
Do not configure fallback bridging on the device with private VLANs.
Do not configure a remote SPAN (RSPAN) VLAN as a primary or a secondary VLAN of a private-VLAN.
Do not configure private VLAN ports on interfaces configured for these other features:
Dynamic-access port VLAN membership
Dynamic Trunking Protocol (DTP)
IP Source Guard
IPv6 First Hop Security (FHS)
IPv6 Security Group (SG)
Multicast VLAN Registration (MVR)
Web Cache Communication Protocol (WCCP)
Port Aggregation Protocol (PAgP) and Link Aggregation Control Protocol (LACP) are supported only for Private VLAN promiscuous trunk ports and Private VLAN isolated trunk ports.
You can configure IEEE 802.1x port-based authentication on a private-VLAN port, but do not configure 802.1x with port security, voice VLAN, or per-user ACL on private-VLAN ports.
A private-VLAN host or promiscuous port cannot be a SPAN destination port. If you configure a SPAN destination port as a private-VLAN port, the port becomes inactive.
If you configure a static MAC address on a promiscuous port in the primary VLAN, you need not add the same static address to all associated secondary VLANs. Similarly, if you configure a static MAC address on a host port in a secondary VLAN, you need not add the same static MAC address to the associated primary VLAN. Also, when you delete a static MAC address from a private-VLAN port, you do not have to remove all instances of the configured MAC address from the private VLAN.
Configure Layer 3 VLAN interfaces (switch value interfaces) only for primary VLANs.
Private VLAN configured with MACsec or Virtual Private LAN Services (VPLS) or Cisco Software-Defined Access solution on the same VLAN does not work.
Information About Private VLANs
The following sections provide information about Private VLANs:
The private VLAN feature addresses two problems that service providers face when using VLANs:
To enable IP routing, each VLAN is assigned a subnet address space or a block of addresses, which can result in wasting the unused IP addresses, and cause IP address management problems.
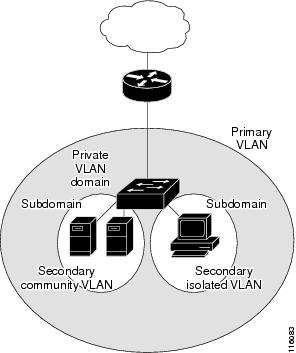
There are two types of secondary VLANs:
Isolated VLANs—Ports within an isolated VLAN cannot communicate with each other at the Layer 2 level.
Community VLANs—Ports within a community VLAN can communicate with each other but cannot communicate with ports in other communities at the Layer 2 level.
Private VLANs provide Layer 2 isolation between ports within the same private VLAN. Private VLAN ports are access ports that are one of these types:
Promiscuous—A promiscuous port belongs to the primary VLAN and can communicate with all interfaces, including the community and isolated host ports that belong to the secondary VLANs associated with the primary VLAN.
Isolated—An isolated port is a host port that belongs to an isolated secondary VLAN. It has complete Layer 2 separation from other ports within the same private VLAN, except for the promiscuous ports. Private VLANs block all traffic to isolated ports except traffic from promiscuous ports. Traffic received from an isolated port is forwarded only to promiscuous ports.
Community—A community port is a host port that belongs to a community secondary VLAN. Community ports communicate with other ports in the same community VLAN and with promiscuous ports. These interfaces are isolated at Layer 2 from all other interfaces in other communities and from isolated ports within their private VLAN.
Primary and secondary VLANs have these characteristics:
Primary VLAN—A private VLAN has only one primary VLAN. Every port in a private VLAN is a member of the primary VLAN. The primary VLAN carries unidirectional traffic downstream from the promiscuous ports to the (isolated and community) host ports and to other promiscuous ports.
Isolated VLAN —A private VLAN has only one isolated VLAN. An isolated VLAN is a secondary VLAN that carries unidirectional traffic upstream from the hosts toward the promiscuous ports and the gateway.
Community VLAN—A community VLAN is a secondary VLAN that carries upstream traffic from the community ports to the promiscuous port gateways and to other host ports in the same community. You can configure multiple community VLANs in a private VLAN.
A promiscuous port can serve only one primary VLAN, one isolated VLAN, and multiple community VLANs. Layer 3 gateways are typically connected to the device through a promiscuous port. With a promiscuous port, you can connect a wide range of devices as access points to a private VLAN. For example, you can use a promiscuous port to monitor or back up all the private VLAN servers from an administration workstation.
In a switched environment, you can assign an individual private VLAN and associated IP subnet to each individual or common group of end stations. The end stations need to communicate only with a default gateway to communicate outside the private VLAN.
You can use private VLANs to control access to end stations in these ways:
Configure selected interfaces connected to end stations as isolated ports to prevent any communication at Layer 2. For example, if the end stations are servers, this configuration prevents Layer 2 communication between the servers.
Configure interfaces connected to default gateways and selected end stations (for example, backup servers) as promiscuous ports to allow all end stations access to a default gateway.
You can extend private VLANs across multiple devices by trunking the primary, isolated, and community VLANs to other devices that support private VLANs. To maintain the security of your private VLAN configuration and to avoid other use of the VLANs configured as private VLANs, configure private VLANs on all intermediate devices, including devices that have no private VLAN ports.
Assigning a separate VLAN to each customer creates an inefficient IP addressing scheme:
Assigning a block of addresses to a customer VLAN can result in unused IP addresses.
If the number of devices in the VLAN increases, the number of assigned address might not be large enough to accommodate them.
These problems are reduced by using private VLANs, where all members in the private VLAN share a common address space, which is allocated to the primary VLAN. Hosts are connected to secondary VLANs and the DHCP server assigns them IP addresses from the block of addresses allocated to the primary VLAN. Subsequent IP addresses can be assigned to customer devices in different secondary VLANs, but in the same primary VLAN. When new devices are added, the DHCP server assigns them the next available address from a large pool of subnet addresses.
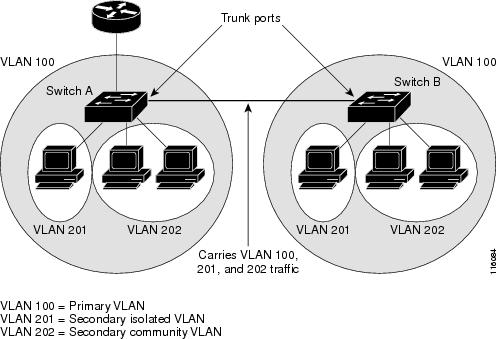
Private VLANs are supported in transparent mode for VTP 1, 2 and 3. Private VLAN is also supported on server mode for VTP 3. If you have a server client setup using VTP 3, private VLANs configured on the server should be reflected on the client.
Private-VLAN Interaction with Other Features
The following sections provide information about Private-VLAN interaction with other features:
In regular VLANs, devices in the same VLAN can communicate with each other at the Layer 2 level, but devices connected to interfaces in different VLANs must communicate at the Layer 3 level. In private VLANs, the promiscuous ports are members of the primary VLAN, while the host ports belong to secondary VLANs. Because the secondary VLAN is associated with the primary VLAN, members of the these VLANs can communicate with each other at the Layer 2 level.
In a regular VLAN, broadcasts are forwarded to all ports in that VLAN. Private VLAN broadcast forwarding depends on the port sending the broadcast:
An isolated port sends a broadcast only to the promiscuous ports or trunk ports.
A community port sends a broadcast to all promiscuous ports, trunk ports, and ports in the same community VLAN.
A promiscuous port sends a broadcast to all ports in the private VLAN (other promiscuous ports, trunk ports, isolated ports, and community ports).
Multicast traffic is routed or bridged across private VLAN boundaries and within a single community VLAN. Multicast traffic is not forwarded between ports in the same isolated VLAN or between ports in different secondary VLANs.
Private VLAN multicast forwarding supports the following:
Sender can be outside the VLAN and the Receivers can be inside the VLAN domain.
Sender can be inside the VLAN and the Receivers can be outside the VLAN domain.
Sender and Receiver can both be in the same community VLAN.
A switch virtual interface (SVI) represents the Layer 3 interface of a VLAN. Layer 3 devices communicate with a private VLAN only through the primary VLAN and not through secondary VLANs. Configure Layer 3 VLAN interfaces (SVIs) only for primary VLANs. You cannot configure Layer 3 VLAN interfaces for secondary VLANs. SVIs for secondary VLANs are inactive while the VLAN is configured as a secondary VLAN.
If you try to configure a VLAN with an active SVI as a secondary VLAN, the configuration is not allowed until you disable the SVI.
If you try to create an SVI on a VLAN that is configured as a secondary VLAN and the secondary VLAN is already mapped at Layer 3, the SVI is not created, and an error is returned. If the SVI is not mapped at Layer 3, the SVI is created, but it is automatically shut down.
When the primary VLAN is associated with and mapped to the secondary VLAN, any configuration on the primary VLAN is propagated to the secondary VLAN SVIs. For example, if you assign an IP subnet to the primary VLAN SVI, this subnet is the IP subnet address of the entire private VLAN.
Private VLANs can operate within the switch stack, and private-VLAN ports can reside on different member switches in the stack. However, the following changes to the stack can impact private-VLAN operation:
If a stack contains only one private-VLAN promiscuous port and the member switch that contains that port is removed from the stack, host ports in that private VLAN lose connectivity outside the private VLAN.
If an active switch that contains the only private-VLAN promiscuous port in the stack fails or leaves the stack and a new active switch is elected, host ports in a private VLAN that had its promiscuous port on the old active switch lose connectivity outside of the private VLAN.
If two stacks merge, private VLANs on the winning stack are not affected, but private-VLAN configuration on the losing switch is lost when that switch reboots.
The MAC addresses learnt in the secondary VLAN are replicated to the primary VLAN and not vice-versa. This saves the hardware l2 cam space. The primary VLAN is always used for forwarding lookups in both directions.
Dynamic MAC addresses learned in Primary VLAN of a private VLAN are then, if required, replicated in the secondary VLANs. For example, if a MAC-address is dynamically received on the secondary VLAN, it will be learnt as part of primary VLAN. In case of isolated VLANs, a blocked entry for the same mac will be added to secondary VLAN in the mac address table. So, MAC learnt on host ports in secondary domain are installed as blocked type entries. All mac entries are learnt on secondary VLANs, even if the traffic ingresses from primary VLAN.
However, if a MAC-address is dynamically learnt in the primary VLAN it will not get replicated in the associated secondary VLANS.
Users are not required to replicate the Static MAC Address CLI for private VLAN hosts as compare to legacy model.
In the legacy model, if the user configures a static MAC address, they need to add the same static MAC address in the associated VLAN too. For example, if MAC address A is user configured on port 1/0/1 in VLAN 101, where VLAN 101 is a secondary VLAN and VLAN 100 is a primary VLAN, then the user has to configure
In this device, the user does not need to replicate the mac address to the associated VLAN. For the above example, user has to configure only
Private VLANs are bidirectional in case of this device, as compared to “Unidirectional” in other platforms.
After layer-2 forward lookup, proper egress VLAN mapping happens and all the egress VLAN based feature processing happens in the egress VLAN context.
When a frame in Layer-2 is forwarded within a private VLAN, the VLAN map is applied at the ingress side and at the egress side. When a frame is routed from inside a private VLAN to an external port, the private-VLAN map is applied at the ingress side. Similarly, when the frame is routed from an external port to a Private VLAN, the private-VLAN is applied at the egress side. This is applicable to both bridged and routed traffic.
For upstream traffic from secondary VLAN to primary VLAN, the MAP of the secondary VLAN is applied on the ingress side and the MAP of the primary VLAN is applied on the egress side.
For downstream traffic from primary VLAN to secondary VLAN, the MAP of the primary VLAN is applied in the ingress direction and the MAP of the secondary VLAN is applied in the egress direction.
If we have two private VLAN domains - PV1 (sec1, prim1) and PV2 (sec2, prim2). For frames routed from PV1 to PV2:
The MAP of sec1 and L3 ACL of prim1 is applied in the ingress port.
The MAP of sec2 and L3 ACL of prim2 is applied in the egress port.
For packets going upstream or downstream from isolated host port to promiscuous port, the isolated VLAN’s VACL is applied in the ingress direction and primary VLAN’s VACL is applied in the egress direction. This allows user to configure different VACL for different secondary VLAN in a same primary VLAN domain.
PVLAN will work seamlessly with High Availability (HA) feature. The Private VLAN existing on the active switch before changeover should be the same after changeover (new active switch should have similar PVLAN configuration both on IOS side and FED side as that of the old active switch).
Private-VLAN Configuration Guidelines
The following sections provide information about Private-VLAN configuration guidelines:
No private VLANs are configured.
Follow these guidelines when configuring private VLANs:
Private VLANs are supported in transparent mode for VTP 1, 2 and 3. If the device is running VTP version 1 or 2, you must set VTP to transparent mode. After you configure a private VLAN, you should not change the VTP mode to client or server. VTP version 3 supports private VLANs in all modes.
With VTP version 1 or 2, after you have configured private VLANs, use the copy running-config startup config privileged EXEC command to save the VTP transparent mode configuration and private-VLAN configuration in the device startup configuration file. Otherwise, if the device resets, it defaults to VTP server mode, which does not support private VLANs. VTP version 3 does support private VLANs.
VTP version 1 and 2 do not propagate private-VLAN configuration. You must configure private VLANs on each device where you want private-VLAN ports unless the devices are running VTP version 3, as VTP3 propagate private vlans.
You cannot configure VLAN 1 or VLANs 1002 to 1005 as primary or secondary VLANs. Extended VLANs (VLAN IDs 1006 to 4094) can belong to private VLANs.
A primary VLAN can have one isolated VLAN and multiple community VLANs associated with it. An isolated or community VLAN can have only one primary VLAN associated with it.
Although a private VLAN contains more than one VLAN, only one Spanning Tree Protocol (STP) instance runs for the entire private VLAN. When a secondary VLAN is associated with the primary VLAN, the STP parameters of the primary VLAN are propagated to the secondary VLAN.
When copying a PVLAN configuration from a tftp server and applying it on a running-config, the PVLAN association will not be formed. You will need to check and ensure that the primary VLAN is associated to all the secondary VLANs.
You can also use configure replace flash:config_file force instead of copy flash:config_file running-config .
You can enable DHCP snooping on private VLANs. When you enable DHCP snooping on the primary VLAN, it is propagated to the secondary VLANs. If you configure DHCP on a secondary VLAN, the configuration does not take effect if the primary VLAN is already configured.
When you enable IP source guard on private-VLAN ports, you must enable DHCP snooping on the primary VLAN.
We recommend that you prune the private VLANs from the trunks on devices that carry no traffic in the private VLANs.
You can apply different quality of service (QoS) configurations to primary, isolated, and community VLANs.
Note the following considerations for sticky ARP:
Sticky ARP entries are those learned on SVIs and Layer 3 interfaces. These entries do not age out.
The ip sticky-arp global configuration command is supported only on SVIs belonging to private VLANs.
The ip sticky-arp interface configuration command is only supported on:
Layer 3 interfaces
SVIs belonging to normal VLANs
SVIs belonging to private VLANs
For more information about using the ip sticky-arp global configuration and the ip sticky-arp interface configuration commands, see the command reference for this release.
You can configure VLAN maps on primary and secondary VLANs. However, we recommend that you configure the same VLAN maps on private-VLAN primary and secondary VLANs.
PVLANs are bidirectional. They can be applied at both the ingress and egress sides.
When a frame inLayer-2 is forwarded within a private VLAN, the VLAN map is applied at the ingress side and at the egress side. When a frame is routed from inside a private VLAN to an external port, the private-VLAN map is applied at the ingress side. Similarly, when the frame is routed from an external port to a Private VLAN, the private-VLAN is applied at the egress side.
The MAP of sec1 and L3 ACL of prim1 is applied in the ingress port .
The MAP of sec1 and L3 ACL of prim2 is applied in the egress port.
For packets going upstream or downstream from isolated host port to promiscuous port, the isolated VLAN’s VACL is applied in the ingress direction and primary VLAN’S VACL is applied in the egress direction. This allows user to configure different VACL for different secondary VLAN in a same primary VLAN domain.
To filter out specific IP traffic for a private VLAN, you should apply the VLAN map to both the primary and secondary VLANs.
You can apply router ACLs only on the primary-VLAN SVIs. The ACL is applied to both primary and secondary VLAN Layer 3 traffic.
Although private VLANs provide host isolation at Layer 2, hosts can communicate with each other at Layer 3.
Private VLANs support these Switched Port Analyzer (SPAN) features:
You can configure a private-VLAN port as a SPAN source port.
You can use VLAN-based SPAN (VSPAN) on primary, isolated, and community VLANs or use SPAN on only one VLAN to separately monitor egress or ingress traffic.
Follow these guidelines when configuring private VLAN ports:
Use only the private VLAN configuration commands to assign ports to primary, isolated, or community VLANs. Layer 2 access ports assigned to the VLANs that you configure as primary, isolated, or community VLANs are inactive while the VLAN is part of the private VLAN configuration. Layer 2 trunk interfaces remain in the STP forwarding state.
Do not configure ports that belong to a PAgP or LACP EtherChannel as private VLAN ports. While a port is part of the private VLAN configuration, any EtherChannel configuration for it is inactive.
Enable Port Fast and BPDU guard on isolated and community host ports to prevent STP loops due to misconfigurations and to speed up STP convergence. When enabled, STP applies the BPDU guard feature to all Port Fast-configured Layer 2 LAN ports. Do not enable Port Fast and BPDU guard on promiscuous ports.
If you delete a VLAN used in the private VLAN configuration, the private VLAN ports associated with the VLAN become inactive.
Private VLAN ports can be on different network devices if the devices are trunk-connected and the primary and secondary VLANs have not been removed from the trunk.
How to Configure Private VLANs
The following sections provide information about configuring Private VLANs:
To configure a private VLAN, perform these steps:
Step 2
Create the primary and secondary VLANs and associate them.
Step 3
Configure interfaces to be isolated or community host ports, and assign VLAN membership to the host port.
Step 4
Configure interfaces as promiscuous ports, and map the promiscuous ports to the primary-secondary VLAN pair.
Step 5
If inter-VLAN routing will be used, configure the primary SVI, and map secondary VLANs to the primary.
Step 6
Verify private-VLAN configuration.
The private-vlan commands do not take effect until you exit VLAN configuration mode.
To configure and associate VLANs in a Private VLAN, perform these steps:
vlan vlan-id
Enters VLAN configuration mode and designates or creates a VLAN that will be the primary VLAN. The VLAN ID range is 2 to 1001 and 1006 to 4094.
private-vlan primary
Designates the VLAN as the primary VLAN.
Returns to global configuration mode.
Step 7
(Optional) Enters VLAN configuration mode and designates or creates a VLAN that will be an isolated VLAN. The VLAN ID range is 2 to 1001 and 1006 to 4094.
Step 8
private-vlan isolated
Designates the VLAN as an isolated VLAN.
Step 9
Step 10
(Optional) Enters VLAN configuration mode and designates or creates a VLAN that will be a community VLAN. The VLAN ID range is 2 to 1001 and 1006 to 4094.
Step 11
private-vlan community
Designates the VLAN as a community VLAN.
Step 12
Step 13
Step 14
Step 15
Step 16
Enters VLAN configuration mode for the primary VLAN designated in Step 4.
Step 17
private-vlan association [ add | remove ] secondary_vlan_list
Associates the secondary VLANs with the primary VLAN. It can be a single private-VLAN ID or a hyphenated range of private-VLAN IDs.
The secondary_vlan_list parameter cannot contain spaces. It can contain multiple comma-separated items. Each item can be a single private-VLAN ID or a hyphenated range of private-VLAN IDs.
The secondary_vlan_list parameter can contain multiple community VLAN IDs but only one isolated VLAN ID.
Enter a secondary_vlan_list , or use the add keyword with a secondary_vlan_list to associate secondary VLANs with a primary VLAN.
Use the remove keyword with a secondary_vlan_list to clear the association between secondary VLANs and a primary VLAN.
The command does not take effect until you exit VLAN configuration mode.
Step 18
Returns to privileged EXEC mode.
Step 19
show vlan private-vlan [ type ] or show interfaces status
Verifies the configuration.
Step 20
copy running-config startup config
Saves your entries in the device startup configuration file.
Follow these steps to configure a Layer 2 interface as a private-VLAN host port and to associate it with primary and secondary VLANs:
show interfaces [ interface-id ] switchport
copy running-config startup-config
(Optional) Saves your entries in the configuration file.
Follow these steps to configure a Layer 2 interface as a private VLAN promiscuous port and map it to primary and secondary VLANs:
If the private VLAN will be used for inter-VLAN routing, you configure an SVI for the primary VLAN and map secondary VLANs to the SVI.
Follow these steps to map secondary VLANs to the SVI of a primary VLAN to allow Layer 3 switching of private VLAN traffic:
Enter a secondary_vlan_list , or use the add keyword with a secondary_vlan_list to map the secondary VLANs to a primary VLAN.
Use the remove keyword with a secondary_vlan_list to clear the mapping between secondary VLANs and a primary VLAN.
show interfaces private-vlan mapping
The following table displays the commands used to monitor private VLANs.
Configuration Examples for Private VLANs
This following sections provide configuration examples for Private VLANSs:
This example shows how to configure VLAN 20 as a primary VLAN, VLAN 501 as an isolated VLAN, and VLANs 502 and 503 as community VLANs, to associate them in a private VLAN, and to verify the configuration:
This example shows how to configure an interface as a private VLAN host port, associate it with a private VLAN pair, and verify the configuration:
This example shows how to configure an interface as a private VLAN promiscuous port and map it to a private VLAN. The interface is a member of primary VLAN 20 and secondary VLANs 501 to 503 are mapped to it.
Use the show vlan private-vlan or the show interface status privileged EXEC command to display primary and secondary VLANs and private-VLAN ports on the device.
This example shows how to map the interfaces fo VLANs 501 and 502 to primary VLAN 10, which permits routing of secondary VLAN ingress traffic from private VLANs 501 and 502:
This example shows output from the show vlan private-vlan command:
You can configure the following:
VLAN trunking
VLAN Membership Policy Server (VMPS)
Voice VLANs
Related Documents
Standards and rfcs.
This table provides release and related information for features explained in this module.
These features are available on all releases subsequent to the one they were introduced in, unless noted otherwise.
Use Cisco Feature Navigator to find information about platform and software image support. To access Cisco Feature Navigator, go to https://cfnng.cisco.com/ .
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )

CCNA 200-301
- CCNA 200-301 Labs
- CCNP 350-401 ENCOR
- CCNP 350-401 ENCOR Labs
- CCNP 300-410 ENARSI
- CCIE Enterprise Infrastructure
- Cisco Packet Tracer Lab Course
- NRS II IRP Course
- NRS II MPLS Course
- NRS II Service Architecture
- Nokia Configuration Course
- Nokia SRC Program
- JNCIA Junos
- HCIA (HCNA)
- HCIA Configuration Course
- What is Huawei R&S Certification?
- Huawei ICT Certifications
- Python Course
- IPv6 Course
- IP Multicast Course
- NRS I Configuration Course
- Cisco Packet Tracer How To Guide
- Online Courses
- Udemy Courses
- CCNA Flashcard Questions
- Protocol Cheat Sheets
- Subnetting Cheat Sheet
- Linux Cheat Sheet
- Python Cheat Sheet
- CLI Commands Cheat Sheets
- Miscellaneous Cheat Sheets
- Cisco Packet Tracer Labs
- Cisco GNS3 Labs
- Huawei eNSP Labs
- Nokia GNS3 Labs
- Short Config Videos
- Network Tools
- IPCisco on Social Media
- Network Engineer Interview Questions
- Personality Interview Training
- Sign In/Up | Members
- Lost password
- Sign In/Sign Up
- ENROLL HERE

- VLAN Port Assignment and VLAN Port Types
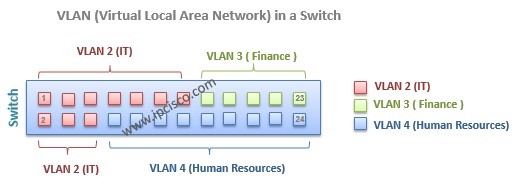
In this lesson, we will focus on some of the key lessons of VLANs. We will learn how to assign ports to VLAN, VLAN Port types and VLAn Tagging.
Table of Contents
Static and Dynamic VLAN Assignments
VLANs can be assigned statically and dynamically . Static configuration is more common, but dynamic is also used.
Static VLAN assignment is like its name. You will statically assign the ports to the VLAN.
Dynamic VLAN assignment can be done by VLAN Membership Policy Server(VMPS) . VMPS needs VLAN-MAC address relationship database. Here, we will use the static one, like many network engineer.
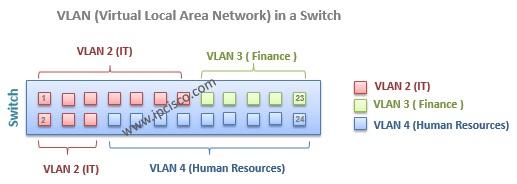
VLAN Port Types
There are two type port used in VLANs. These are: – Access Ports, – Trunk Ports
Access ports are the ports that are member of a single VLAN . Host devices are connected to it. This is also default Cisco switch port type.
Trunk ports are the ports that are member of more than one VLAN or all VLANs . This ports are used between switches. To span VLANs between more than one switch, some ports are needed to carry VLAN information accross the switches. These ports are trunk ports. You can also carry each VLAN without using any trunk port. But this way is not efficient and not common.
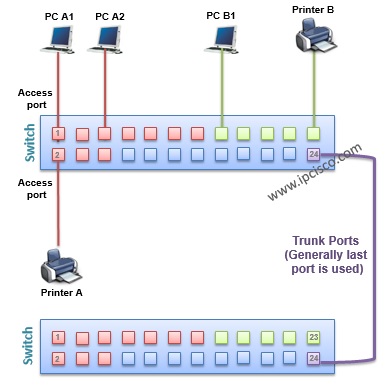
VLAN Frame Tagging
While carrying the frames between VLANs across multiple swithes, frame tagging is required. Because the other end switch need to understand that where the frame will go ( to which VLAN) on the other end. And tagging is used only for the frames going out a trunk port. This is not used for access ports, and anyway this is not necessary.
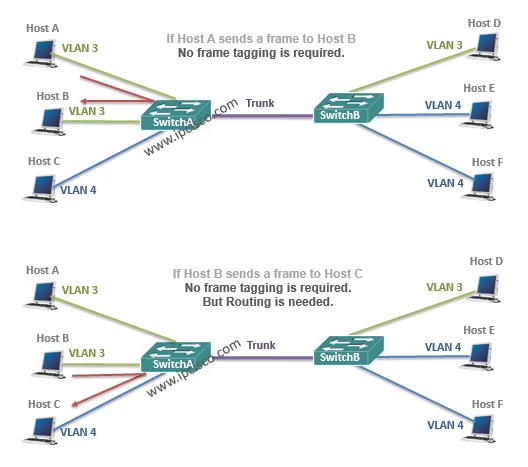
No VLAN Frame Tagging Require
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Network Fundamentals
- Collision Domain vs Broadcast Domain
- Coaxial Cable Details
- Types of Networks
- Top Internet Access Technologies
- WAN Topology Types
- Network Topology Architectures
- Power Over Ethernet (PoE)
- Ethernet Collisions and Troubleshooting
- Cisco NGFW and Cisco NGIPS
- Networking Connectors
- Ping Command
- Basic Cisco Router Configuration on Packet Tracer
- ICMP (Internet Control Message Protocol)
- Address Resolution Protocol (ARP)
- Network Cabling
- Network Devices
- TCP/IP Model
- OSI Referance Model

IPv4 Addressing
- Verify IP Parameters for Client OS
- IPv4 vs IPv6 Comparison
- Cisco IP Address Configuration
- APIPA Address
- Private IP Address Ranges
- Subnetting Examples
- IP Addressing (IPv4)
- IP Subnetting and Subnetting Examples
TCP and UDP
- TCP Header : Sequence & Acknowledgement Number
- TCP Handshake
- TCP versus UDP
- UDP (User Datagram Protocol)
- TCP (Transmission Control Protocol)
- TCP Header : TCP Options
- TCP Header : TCP Window Size, Checksum & Urgent Pointer
- TCP Header : TCP Flags
- Voice VLAN Configuration
- Packet Tracer VLAN Example 2
- How to Configure Cisco VLANs
- VTP Configuration with Packet Tracer
- VTP (VLAN Trunking Protocol)
- DTP and VLAN Frame Tagging protocols ISL, dot1.q
- Cisco Packet Tracer VLAN Configuration Example
- VLANs (Virtual Local Area Networks)
Switching and LANs
- Ethernet Basics
- Cisco Switch Configuration on Cisco Packet Tracer
- MAC Address Lookup
- What is a mac address
- Local Area Networks
- Network Topologies
- Hubs, Switches and Routers
Spanning Tree Protocol
- Loop Guard, Uplink Fast, Backbone Fast and UDLD
- Portfast, Root Guard, BPDU Filter and BPDU Guard
- PVST+ and Rapid PVST+
- STP (Spanning Tree Protocol) Example on Packet Tracer
- RSTP Configuration on Packet Tracer
- STP Portfast Configuration with Packet Tracer
- Spanning Tree Protocol Operation
- Rapid Spanning Tree Protocol (RSTP)
- Spanning Tree Protocol (STP)
Neighbor Discovery
- LLDP Configuration on Cisco IOS
- Neighbour Discovery Protocols
- CDP Configuration with Packet Tracer
EtherChannels
- PAgP Configuration on Cisco Devices
- LACP Configuration on Cisco Devices
- Link Aggregation Control Protocol (LACP)
Routing Fundamentals
- Route Summarization
- Routing Path Determination
- Routing Table
- Static Routes
- IPv4 Floating Static Routes
- Inter VLAN Routing Configuration on Packet Tracer
- Switch Virtual Interface Configuration on Packet Tracer
- Switch Virtual Interfaces
- Inter VLAN Routing with Router on Stick
- IP and Layer 3 Overview
- Static Route Configuration on Cisco Routers
- Dynamic Routing Protocols
- OSPF Cost and SPF Algorithm
- OSPFv3 Configuration Example on Cisco IOS
- OSPFv3 (Open Shortest Path First Version 3)
- Cisco Single Area OSPF Configuration
- Other OSPF Key Points
- OSPF Network Types
- OSPF Area Types
- OSPF LSA Types
- OSPF Packet Types
- OSPF Adjacency
- OSPF(Open Shortest Path First) Overview
WAN (Wide Area Networks)
- MLPPP Configuration on Cisco Packet Tracer
- What is MLPPP?
- Metro Ethernet Technology
- WAN and WAN Technologies
DHCP and DNS
- DNS Configuration on Cisco Routers
- Domain Name System Overview
- Router DHCP Configuration with Packet Tracer
- DHCP IP Allocation Operation
- DHCP (Dynamic Host Configuration Protocol)
- NAT (Network Address Translation)
- PAT Configuration with Packet Tracer
- Dynamic NAT Configuration with Packet Tracer
- Static NAT Configuration with Packet Tracer
First Hop Redundancy
- HSRP Configuration on Cisco IOS
- HSRP (Hot Standby Router Protocol)
- First Hop Redundancy Protocols (FHRPs)
Network Management
- Syslog Overview
- Configuration Register
- TFTP, FTP, SFTP and SCP
- SSH Configuration on Packet Tracer
- Syslog Configuration Cisco
- Cisco NTP Configuration
- NTP (Network Time Protocol)
- SNMP Overview
- SNMP Configuration On Cisco IOS
- Cisco Router Password Recovery
- IPv6 Floating Static Routes
- IPv6 Static and Default Route Configuration
- Stateless Address Auto Configuration
- IPv6 NDP (Neighbour Discovery Protocol)
- IPv6 Configuration on Cisco Packet Tracer
- What does IPv6 bring?
- Subnetting in IPv6
- IPv6 Address Types
- IPv4 and IPv6 Headers
- IPv6 and IPv6 Addresses
Quality of Service
- Network Traffic Types
- Policing and Shaping in QoS
- Classification and Marking in QoS
- Quality of Service Overview
- Radius Configuration for Wireless Users
- Cisco RADIUS Server Configuration on Packet Tracer
- TACACS+ Overview
- RADIUS Overview
- AAA Protocols : RADIUS and TACACS+
- Authentication, Authorization, Accounting (AAA)
- WLAN Frequency Bands
- Other Wireless Network Extention Types
- Wireless Principles
- WLAN Components
- Wireless Network Design Models
- WLC Management Access Connections
- Wireless Access Point Modes
- Wireless Security Protocols
- WLAN Configuration on Packet Tracer
Security Fundamentals
- DHCP Snooping Configuration on Packet Tracer
- Cisco Banner Configuration on Packet Tracer
- What is DHCP Snooping?
- Access Control Lists
- Multifactor Authentication (MFA)
- Dynamic ARP Inspection
- Cyber Attacks, Network Attacks, Threats and Mitigation
- 802.1x (Port Based Network Access Control)
- Switch Port Security Configuration on Cisco Packet Tracer
- Switch Port Security
- Extended Access List Configuration With Packet Tracer
- Standard Access List Configuration With Packet Tracer
- Basic Cisco Router Security Configuration
Automation and Programmability
- Ansible vs Puppet vs Chef
- Chef Overview
- Puppet Overview
- Ansible Overview
- Network Automation Tools
- Interpret JSON Encoded Data
- Cisco DNA Center
- Cisco SD-Access
- Data Serialization Languages: JSON, YAML, XML
- Traditional Network Management versus Cisco DNA Center
- Cisco DNA and Intent-Based Networking (IBN)
- How Network Automation Impacts Network Management
SDN (Software Defined Networking)
- What is SDN ?
- Traditional Network Drawbacks Versus SDN
- What Will SDN Bring?
- SDN Architecture Components
- SDN Terminology
- Virtualization
- Virtual Network Structure
Latest Lessons
- Coaxial Cable Details Part of: CCNA 200-301
- IPv4 vs IPv6 Comparison Part of: CCNA 200-301
- IGMPv3 Overview Part of: IP Multicast Course
- IGMPv3 Overview Part of: CCIE Enterprise Infrastructure
- Subnetting IPv6 Part of: CCIE Enterprise Infrastructure
- IPv6 and Subnetting Part of: CCNP Enterprise 350-401 ENCOR
- IPv6 Link Local Address Type Part of: CCIE Enterprise Infrastructure
- Cisco Switch Configuration on Cisco Packet Tracer Part of: CCNA 200-301
- Switch Configuration on Cisco Packet Tracer Part of: Cisco Packet Tracer Lab Course
- REST API Security Part of: CCNP Enterprise 350-401 ENCOR
- More Lessons
Latest Blog Posts
WHAT YOU WILL FIND?
- 250.000+ Students All Over The World
- 8.000+ Questions & Answers
- 100+ Lab Files & Cheat Sheets
- 30+ IT/Network Courses
- A Real Desire To Help You
- Daily Social Media Shares
- %100 Satisfaction
- CISCO Courses
- NOKIA Courses
- HUAWEI Courses
- JUNIPER Courses
- PYTHON Course
- KEY Courses
- VIDEO Courses
- UDEMY Courses
- Cheat Sheets
- Configuration Files
- Interview Questions
- IPCisco On Social Media
- Pärnu mnt. 139c – 14, 11317, Tallinn, Estonia
- [email protected]

IMAGES
VIDEO
COMMENTS
Book Title. Security Configuration Guide, Cisco IOS XE Bengaluru 17.6.x (Catalyst 9500 Switches) Chapter Title. IEEE 802.1X VLAN Assignment. PDF - Complete Book (12.4 MB) PDF - This Chapter (1.12 MB) View with Adobe Reader on a variety of devices
After creating a VLAN, you can manually assign a port to that VLAN and it will be able to communicate only with or through other devices in the VLAN. Configure the switch port for membership in a given VLAN as follows: Statically assign a VLAN: COS. set vlan number mod/port. IOS. (global) interface type mod/port.
VLAN Configuration Guide, Cisco IOS XE 17.13.x (Catalyst 9200 Switches) Chapter Title. Configuring Private VLANs. PDF - Complete Book (2.75 MB) PDF - This Chapter (1.28 MB) View with Adobe Reader on a variety of devices. Print Results. Updated: December 8, 2023. Chapter: Configuring Private VLANs ...
Interface F0/18 was previously assigned to VLAN 20. The no switchport access vlan command is entered for interface F0/18. Examine the output in the show vlan brief command, as shown in Example 3-3. The show vlan brief command displays the VLAN assignment and membership type for all switch ports. The show vlan brief command displays one line for each VLAN.
Cisco catalyst switches support Dynamic VLANs by using a VLAN Management Policy Server in order to assign specific VLAN IDs to corresponding MAC addresses. Usually, Static assignment of VLANs to switch ports is configured. To be able to do so, first, all different VLAN subnets need to be defined.
This post will deal with creating Layer 2 VLANs on Cisco switches and performing all relevant configurations. Up to 4094 VLANs can be configured on Cisco catalyst switches. ... VLAN assignment on a switch is configured on a per-interface basis. That is, each switch port interface is assigned individually into a Layer 2 VLAN.
VLAN Port Types. There are two type port used in VLANs. These are: - Access Ports, - Trunk Ports. Access ports are the ports that are member of a single VLAN. Host devices are connected to it. This is also default Cisco switch port type. Trunk ports are the ports that are member of more than one VLAN or all VLANs.