- Privacy Policy
Buy Me a Coffee

Home » 500+ Cyber Security Research Topics

500+ Cyber Security Research Topics

Cybersecurity has become an increasingly important topic in recent years as more and more of our lives are spent online. With the rise of the digital age, there has been a corresponding increase in the number and severity of cyber attacks. As such, research into cybersecurity has become critical in order to protect individuals, businesses, and governments from these threats. In this blog post, we will explore some of the most pressing cybersecurity research topics, from the latest trends in cyber attacks to emerging technologies that can help prevent them. Whether you are a cybersecurity professional, a Master’s or Ph.D. student, or simply interested in the field, this post will provide valuable insights into the challenges and opportunities in this rapidly evolving area of study.
Cyber Security Research Topics
Cyber Security Research Topics are as follows:
- The role of machine learning in detecting cyber threats
- The impact of cloud computing on cyber security
- Cyber warfare and its effects on national security
- The rise of ransomware attacks and their prevention methods
- Evaluating the effectiveness of network intrusion detection systems
- The use of blockchain technology in enhancing cyber security
- Investigating the role of cyber security in protecting critical infrastructure
- The ethics of hacking and its implications for cyber security professionals
- Developing a secure software development lifecycle (SSDLC)
- The role of artificial intelligence in cyber security
- Evaluating the effectiveness of multi-factor authentication
- Investigating the impact of social engineering on cyber security
- The role of cyber insurance in mitigating cyber risks
- Developing secure IoT (Internet of Things) systems
- Investigating the challenges of cyber security in the healthcare industry
- Evaluating the effectiveness of penetration testing
- Investigating the impact of big data on cyber security
- The role of quantum computing in breaking current encryption methods
- Developing a secure BYOD (Bring Your Own Device) policy
- The impact of cyber security breaches on a company’s reputation
- The role of cyber security in protecting financial transactions
- Evaluating the effectiveness of anti-virus software
- The use of biometrics in enhancing cyber security
- Investigating the impact of cyber security on the supply chain
- The role of cyber security in protecting personal privacy
- Developing a secure cloud storage system
- Evaluating the effectiveness of firewall technologies
- Investigating the impact of cyber security on e-commerce
- The role of cyber security in protecting intellectual property
- Developing a secure remote access policy
- Investigating the challenges of securing mobile devices
- The role of cyber security in protecting government agencies
- Evaluating the effectiveness of cyber security training programs
- Investigating the impact of cyber security on the aviation industry
- The role of cyber security in protecting online gaming platforms
- Developing a secure password management system
- Investigating the challenges of securing smart homes
- The impact of cyber security on the automotive industry
- The role of cyber security in protecting social media platforms
- Developing a secure email system
- Evaluating the effectiveness of encryption methods
- Investigating the impact of cyber security on the hospitality industry
- The role of cyber security in protecting online education platforms
- Developing a secure backup and recovery strategy
- Investigating the challenges of securing virtual environments
- The impact of cyber security on the energy sector
- The role of cyber security in protecting online voting systems
- Developing a secure chat platform
- Investigating the impact of cyber security on the entertainment industry
- The role of cyber security in protecting online dating platforms
- Artificial Intelligence and Machine Learning in Cybersecurity
- Quantum Cryptography and Post-Quantum Cryptography
- Internet of Things (IoT) Security
- Developing a framework for cyber resilience in critical infrastructure
- Understanding the fundamentals of encryption algorithms
- Cyber security challenges for small and medium-sized businesses
- Developing secure coding practices for web applications
- Investigating the role of cyber security in protecting online privacy
- Network security protocols and their importance
- Social engineering attacks and how to prevent them
- Investigating the challenges of securing personal devices and home networks
- Developing a basic incident response plan for cyber attacks
- The impact of cyber security on the financial sector
- Understanding the role of cyber security in protecting critical infrastructure
- Mobile device security and common vulnerabilities
- Investigating the challenges of securing cloud-based systems
- Cyber security and the Internet of Things (IoT)
- Biometric authentication and its role in cyber security
- Developing secure communication protocols for online messaging platforms
- The importance of cyber security in e-commerce
- Understanding the threats and vulnerabilities associated with social media platforms
- Investigating the role of cyber security in protecting intellectual property
- The basics of malware analysis and detection
- Developing a basic cyber security awareness training program
- Understanding the threats and vulnerabilities associated with public Wi-Fi networks
- Investigating the challenges of securing online banking systems
- The importance of password management and best practices
- Cyber security and cloud computing
- Understanding the role of cyber security in protecting national security
- Investigating the challenges of securing online gaming platforms
- The basics of cyber threat intelligence
- Developing secure authentication mechanisms for online services
- The impact of cyber security on the healthcare sector
- Understanding the basics of digital forensics
- Investigating the challenges of securing smart home devices
- The role of cyber security in protecting against cyberbullying
- Developing secure file transfer protocols for sensitive information
- Understanding the challenges of securing remote work environments
- Investigating the role of cyber security in protecting against identity theft
- The basics of network intrusion detection and prevention systems
- Developing secure payment processing systems
- Understanding the role of cyber security in protecting against ransomware attacks
- Investigating the challenges of securing public transportation systems
- The basics of network segmentation and its importance in cyber security
- Developing secure user access management systems
- Understanding the challenges of securing supply chain networks
- The role of cyber security in protecting against cyber espionage
- Investigating the challenges of securing online educational platforms
- The importance of data backup and disaster recovery planning
- Developing secure email communication protocols
- Understanding the basics of threat modeling and risk assessment
- Investigating the challenges of securing online voting systems
- The role of cyber security in protecting against cyber terrorism
- Developing secure remote access protocols for corporate networks.
- Investigating the challenges of securing artificial intelligence systems
- The role of machine learning in enhancing cyber threat intelligence
- Evaluating the effectiveness of deception technologies in cyber security
- Investigating the impact of cyber security on the adoption of emerging technologies
- The role of cyber security in protecting smart cities
- Developing a risk-based approach to cyber security governance
- Investigating the impact of cyber security on economic growth and innovation
- The role of cyber security in protecting human rights in the digital age
- Developing a secure digital identity system
- Investigating the impact of cyber security on global political stability
- The role of cyber security in protecting the Internet of Things (IoT)
- Developing a secure supply chain management system
- Investigating the challenges of securing cloud-native applications
- The role of cyber security in protecting against insider threats
- Developing a secure software-defined network (SDN)
- Investigating the impact of cyber security on the adoption of mobile payments
- The role of cyber security in protecting against cyber warfare
- Developing a secure distributed ledger technology (DLT) system
- Investigating the impact of cyber security on the digital divide
- The role of cyber security in protecting against state-sponsored attacks
- Developing a secure Internet infrastructure
- Investigating the challenges of securing industrial control systems (ICS)
- Developing a secure quantum communication system
- Investigating the impact of cyber security on global trade and commerce
- Developing a secure decentralized authentication system
- Investigating the challenges of securing edge computing systems
- Developing a secure hybrid cloud system
- Investigating the impact of cyber security on the adoption of smart cities
- The role of cyber security in protecting against cyber propaganda
- Developing a secure blockchain-based voting system
- Investigating the challenges of securing cyber-physical systems (CPS)
- The role of cyber security in protecting against cyber hate speech
- Developing a secure machine learning system
- Investigating the impact of cyber security on the adoption of autonomous vehicles
- The role of cyber security in protecting against cyber stalking
- Developing a secure data-driven decision-making system
- Investigating the challenges of securing social media platforms
- The role of cyber security in protecting against cyberbullying in schools
- Developing a secure open source software ecosystem
- Investigating the impact of cyber security on the adoption of smart homes
- The role of cyber security in protecting against cyber fraud
- Developing a secure software supply chain
- Investigating the challenges of securing cloud-based healthcare systems
- The role of cyber security in protecting against cyber harassment
- Developing a secure multi-party computation system
- Investigating the impact of cyber security on the adoption of virtual and augmented reality technologies.
- Cybersecurity in Cloud Computing Environments
- Cyber Threat Intelligence and Analysis
- Blockchain Security
- Data Privacy and Protection
- Cybersecurity in Industrial Control Systems
- Mobile Device Security
- The importance of cyber security in the digital age
- The ethics of cyber security and privacy
- The role of government in regulating cyber security
- Cyber security threats and vulnerabilities in the healthcare sector
- Understanding the risks associated with social media and cyber security
- The impact of cyber security on e-commerce
- The effectiveness of cyber security awareness training programs
- The role of biometric authentication in cyber security
- The importance of password management in cyber security
- The basics of network security protocols and their importance
- The challenges of securing online gaming platforms
- The role of cyber security in protecting national security
- The impact of cyber security on the legal sector
- The ethics of cyber warfare
- The challenges of securing the Internet of Things (IoT)
- Understanding the basics of malware analysis and detection
- The challenges of securing public transportation systems
- The impact of cyber security on the insurance industry
- The role of cyber security in protecting against ransomware attacks
- The challenges of securing remote work environments
- Understanding the threats and vulnerabilities associated with social engineering attacks
- The impact of cyber security on the education sector
- Investigating the challenges of securing supply chain networks
- The challenges of securing personal devices and home networks
- The importance of secure coding practices for web applications
- The impact of cyber security on the hospitality industry
- The role of cyber security in protecting against identity theft
- The challenges of securing public Wi-Fi networks
- The importance of cyber security in protecting critical infrastructure
- The challenges of securing cloud-based storage systems
- The effectiveness of antivirus software in cyber security
- Developing secure payment processing systems.
- Cybersecurity in Healthcare
- Social Engineering and Phishing Attacks
- Cybersecurity in Autonomous Vehicles
- Cybersecurity in Smart Cities
- Cybersecurity Risk Assessment and Management
- Malware Analysis and Detection Techniques
- Cybersecurity in the Financial Sector
- Cybersecurity in Government Agencies
- Cybersecurity and Artificial Life
- Cybersecurity for Critical Infrastructure Protection
- Cybersecurity in the Education Sector
- Cybersecurity in Virtual Reality and Augmented Reality
- Cybersecurity in the Retail Industry
- Cryptocurrency Security
- Cybersecurity in Supply Chain Management
- Cybersecurity and Human Factors
- Cybersecurity in the Transportation Industry
- Cybersecurity in Gaming Environments
- Cybersecurity in Social Media Platforms
- Cybersecurity and Biometrics
- Cybersecurity and Quantum Computing
- Cybersecurity in 5G Networks
- Cybersecurity in Aviation and Aerospace Industry
- Cybersecurity in Agriculture Industry
- Cybersecurity in Space Exploration
- Cybersecurity in Military Operations
- Cybersecurity and Cloud Storage
- Cybersecurity in Software-Defined Networks
- Cybersecurity and Artificial Intelligence Ethics
- Cybersecurity and Cyber Insurance
- Cybersecurity in the Legal Industry
- Cybersecurity and Data Science
- Cybersecurity in Energy Systems
- Cybersecurity in E-commerce
- Cybersecurity in Identity Management
- Cybersecurity in Small and Medium Enterprises
- Cybersecurity in the Entertainment Industry
- Cybersecurity and the Internet of Medical Things
- Cybersecurity and the Dark Web
- Cybersecurity and Wearable Technology
- Cybersecurity in Public Safety Systems.
- Threat Intelligence for Industrial Control Systems
- Privacy Preservation in Cloud Computing
- Network Security for Critical Infrastructure
- Cryptographic Techniques for Blockchain Security
- Malware Detection and Analysis
- Cyber Threat Hunting Techniques
- Cybersecurity Risk Assessment
- Machine Learning for Cybersecurity
- Cybersecurity in Financial Institutions
- Cybersecurity for Smart Cities
- Cybersecurity in Aviation
- Cybersecurity in the Automotive Industry
- Cybersecurity in the Energy Sector
- Cybersecurity in Telecommunications
- Cybersecurity for Mobile Devices
- Biometric Authentication for Cybersecurity
- Cybersecurity for Artificial Intelligence
- Cybersecurity for Social Media Platforms
- Cybersecurity in the Gaming Industry
- Cybersecurity in the Defense Industry
- Cybersecurity for Autonomous Systems
- Cybersecurity for Quantum Computing
- Cybersecurity for Augmented Reality and Virtual Reality
- Cybersecurity in Cloud-Native Applications
- Cybersecurity for Smart Grids
- Cybersecurity in Distributed Ledger Technology
- Cybersecurity for Next-Generation Wireless Networks
- Cybersecurity for Digital Identity Management
- Cybersecurity for Open Source Software
- Cybersecurity for Smart Homes
- Cybersecurity for Smart Transportation Systems
- Cybersecurity for Cyber Physical Systems
- Cybersecurity for Critical National Infrastructure
- Cybersecurity for Smart Agriculture
- Cybersecurity for Retail Industry
- Cybersecurity for Digital Twins
- Cybersecurity for Quantum Key Distribution
- Cybersecurity for Digital Healthcare
- Cybersecurity for Smart Logistics
- Cybersecurity for Wearable Devices
- Cybersecurity for Edge Computing
- Cybersecurity for Cognitive Computing
- Cybersecurity for Industrial IoT
- Cybersecurity for Intelligent Transportation Systems
- Cybersecurity for Smart Water Management Systems
- The rise of cyber terrorism and its impact on national security
- The impact of artificial intelligence on cyber security
- Analyzing the effectiveness of biometric authentication for securing data
- The impact of social media on cyber security and privacy
- The future of cyber security in the Internet of Things (IoT) era
- The role of machine learning in detecting and preventing cyber attacks
- The effectiveness of encryption in securing sensitive data
- The impact of quantum computing on cyber security
- The rise of cyber bullying and its effects on mental health
- Investigating cyber espionage and its impact on national security
- The effectiveness of cyber insurance in mitigating cyber risks
- The role of blockchain technology in cyber security
- Investigating the effectiveness of cyber security awareness training programs
- The impact of cyber attacks on critical infrastructure
- Analyzing the effectiveness of firewalls in protecting against cyber attacks
- The impact of cyber crime on the economy
- Investigating the effectiveness of multi-factor authentication in securing data
- The future of cyber security in the age of quantum internet
- The impact of big data on cyber security
- The role of cybersecurity in the education system
- Investigating the use of deception techniques in cyber security
- The impact of cyber attacks on the healthcare industry
- The effectiveness of cyber threat intelligence in mitigating cyber risks
- The role of cyber security in protecting financial institutions
- Investigating the use of machine learning in cyber security risk assessment
- The impact of cyber attacks on the transportation industry
- The effectiveness of network segmentation in protecting against cyber attacks
- Investigating the effectiveness of biometric identification in cyber security
- The impact of cyber attacks on the hospitality industry
- The future of cyber security in the era of autonomous vehicles
- The effectiveness of intrusion detection systems in protecting against cyber attacks
- The role of cyber security in protecting small businesses
- Investigating the effectiveness of virtual private networks (VPNs) in securing data
- The impact of cyber attacks on the energy sector
- The effectiveness of cyber security regulations in mitigating cyber risks
- Investigating the use of deception technology in cyber security
- The impact of cyber attacks on the retail industry
- The effectiveness of cyber security in protecting critical infrastructure
- The role of cyber security in protecting intellectual property in the entertainment industry
- Investigating the effectiveness of intrusion prevention systems in protecting against cyber attacks
- The impact of cyber attacks on the aerospace industry
- The future of cyber security in the era of quantum computing
- The effectiveness of cyber security in protecting against ransomware attacks
- The role of cyber security in protecting personal and sensitive data
- Investigating the effectiveness of cloud security solutions in protecting against cyber attacks
- The impact of cyber attacks on the manufacturing industry
- The effective cyber security and the future of e-votingness of cyber security in protecting against social engineering attacks
- Investigating the effectiveness of end-to-end encryption in securing data
- The impact of cyber attacks on the insurance industry
- The future of cyber security in the era of artificial intelligence
- The effectiveness of cyber security in protecting against distributed denial-of-service (DDoS) attacks
- The role of cyber security in protecting against phishing attacks
- Investigating the effectiveness of user behavior analytics
- The impact of emerging technologies on cyber security
- Developing a framework for cyber threat intelligence
- The effectiveness of current cyber security measures
- Cyber security and data privacy in the age of big data
- Cloud security and virtualization technologies
- Cryptography and its role in cyber security
- Cyber security in critical infrastructure protection
- Cyber security in the Internet of Things (IoT)
- Cyber security in e-commerce and online payment systems
- Cyber security and the future of digital currencies
- The impact of social engineering on cyber security
- Cyber security and ethical hacking
- Cyber security challenges in the healthcare industry
- Cyber security and digital forensics
- Cyber security in the financial sector
- Cyber security in the transportation industry
- The impact of artificial intelligence on cyber security risks
- Cyber security and mobile devices
- Cyber security in the energy sector
- Cyber security and supply chain management
- The role of machine learning in cyber security
- Cyber security in the defense sector
- The impact of the Dark Web on cyber security
- Cyber security in social media and online communities
- Cyber security challenges in the gaming industry
- Cyber security and cloud-based applications
- The role of blockchain in cyber security
- Cyber security and the future of autonomous vehicles
- Cyber security in the education sector
- Cyber security in the aviation industry
- The impact of 5G on cyber security
- Cyber security and insider threats
- Cyber security and the legal system
- The impact of cyber security on business operations
- Cyber security and the role of human behavior
- Cyber security in the hospitality industry
- The impact of cyber security on national security
- Cyber security and the use of biometrics
- Cyber security and the role of social media influencers
- The impact of cyber security on small and medium-sized enterprises
- Cyber security and cyber insurance
- The impact of cyber security on the job market
- Cyber security and international relations
- Cyber security and the role of government policies
- The impact of cyber security on privacy laws
- Cyber security in the media and entertainment industry
- The role of cyber security in digital marketing
- Cyber security and the role of cybersecurity professionals
- Cyber security in the retail industry
- The impact of cyber security on the stock market
- Cyber security and intellectual property protection
- Cyber security and online dating
- The impact of cyber security on healthcare innovation
- Cyber security and the future of e-voting
- Cyber security and the role of open source software
- Cyber security and the use of social engineering in cyber attacks
- The impact of cyber security on the aviation industry
- Cyber security and the role of cyber security awareness training
- Cyber security and the role of cybersecurity standards and best practices
- Cyber security in the legal industry
- The impact of cyber security on human rights
- Cyber security and the role of public-private partnerships
- Cyber security and the future of e-learning
- Cyber security and the role of mobile applications
- The impact of cyber security on environmental sustainability
- Cyber security and the role of threat intelligence sharing
- Cyber security and the future of smart homes
- Cyber security and the role of cybersecurity certifications
- The impact of cyber security on international trade
- Cyber security and the role of cyber security auditing
About the author
Muhammad Hassan
Researcher, Academic Writer, Web developer
You may also like

200+ Funny Research Topics

500+ Sports Research Topics

500+ Environmental Research Topics

500+ Economics Research Topics

500+ Physics Research Topics

500+ Google Scholar Research Topics
- Search Menu
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

High-Impact Research Collection
Explore a collection of freely available high-impact research from 2020 and 2021 published in the Journal of Cybersecurity .
Browse the collection here

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics for 2024
Home Blog Security 60+ Latest Cyber Security Research Topics for 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cyber security thesis topics /ideas helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security research questions, cyber security topics for the project, best cyber security research topics, research titles about cyber security and web security research topics.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics for 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A) Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B) Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C) Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D) Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E) Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F) Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G) Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H) Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I) Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J) Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
Research Topics & Ideas: Cybersecurity
50 Topic Ideas To Kickstart Your Research

If you’re just starting out exploring cybersecurity-related topics for your dissertation, thesis or research project, you’ve come to the right place. In this post, we’ll help kickstart your research by providing a hearty list of cybersecurity-related research topics and ideas , including examples from recent studies.
PS – This is just the start…
We know it’s exciting to run through a list of research topics, but please keep in mind that this list is just a starting point . These topic ideas provided here are intentionally broad and generic , so keep in mind that you will need to develop them further. Nevertheless, they should inspire some ideas for your project.
To develop a suitable research topic, you’ll need to identify a clear and convincing research gap , and a viable plan to fill that gap. If this sounds foreign to you, check out our free research topic webinar that explores how to find and refine a high-quality research topic, from scratch. Alternatively, consider our 1-on-1 coaching service .

Cybersecurity-Related Research Topics
- Developing machine learning algorithms for early detection of cybersecurity threats.
- The use of artificial intelligence in optimizing network traffic for telecommunication companies.
- Investigating the impact of quantum computing on existing encryption methods.
- The application of blockchain technology in securing Internet of Things (IoT) devices.
- Developing efficient data mining techniques for large-scale social media analytics.
- The role of virtual reality in enhancing online education platforms.
- Investigating the effectiveness of various algorithms in reducing energy consumption in data centers.
- The impact of edge computing on the performance of mobile applications in remote areas.
- The application of computer vision techniques in automated medical diagnostics.
- Developing natural language processing tools for sentiment analysis in customer service.
- The use of augmented reality for training in high-risk industries like oil and gas.
- Investigating the challenges of integrating AI into legacy enterprise systems.
- The role of IT in managing supply chain disruptions during global crises.
- Developing adaptive cybersecurity strategies for small and medium-sized enterprises.
- The impact of 5G technology on the development of smart city solutions.
- The application of machine learning in personalized e-commerce recommendations.
- Investigating the use of cloud computing in improving government service delivery.
- The role of IT in enhancing sustainability in the manufacturing sector.
- Developing advanced algorithms for autonomous vehicle navigation.
- The application of biometrics in enhancing banking security systems.
- Investigating the ethical implications of facial recognition technology.
- The role of data analytics in optimizing healthcare delivery systems.
- Developing IoT solutions for efficient energy management in smart homes.
- The impact of mobile computing on the evolution of e-health services.
- The application of IT in disaster response and management.
Cybersecurity Research Ideas (Continued)
- Assessing the security implications of quantum computing on modern encryption methods.
- The role of artificial intelligence in detecting and preventing phishing attacks.
- Blockchain technology in secure voting systems: opportunities and challenges.
- Cybersecurity strategies for protecting smart grids from targeted attacks.
- Developing a cyber incident response framework for small to medium-sized enterprises.
- The effectiveness of behavioural biometrics in preventing identity theft.
- Securing Internet of Things (IoT) devices in healthcare: risks and solutions.
- Analysis of cyber warfare tactics and their implications on national security.
- Exploring the ethical boundaries of offensive cybersecurity measures.
- Machine learning algorithms for predicting and mitigating DDoS attacks.
- Study of cryptocurrency-related cybercrimes: patterns and prevention strategies.
- Evaluating the impact of GDPR on data breach response strategies in the EU.
- Developing enhanced security protocols for mobile banking applications.
- An examination of cyber espionage tactics and countermeasures.
- The role of human error in cybersecurity breaches: a behavioural analysis.
- Investigating the use of deep fakes in cyber fraud: detection and prevention.
- Cloud computing security: managing risks in multi-tenant environments.
- Next-generation firewalls: evaluating performance and security features.
- The impact of 5G technology on cybersecurity strategies and policies.
- Secure coding practices: reducing vulnerabilities in software development.
- Assessing the role of cyber insurance in mitigating financial losses from cyber attacks.
- Implementing zero trust architecture in corporate networks: challenges and benefits.
- Ransomware attacks on critical infrastructure: case studies and defence strategies.
- Using big data analytics for proactive cyber threat intelligence.
- Evaluating the effectiveness of cybersecurity awareness training in organisations.
Recent Cybersecurity-Related Studies
While the ideas we’ve presented above are a decent starting point for finding a research topic, they are fairly generic and non-specific. So, it helps to look at actual studies in the cybersecurity space to see how this all comes together in practice.
Below, we’ve included a selection of recent studies to help refine your thinking. These are actual studies, so they can provide some useful insight as to what a research topic looks like in practice.
- Cyber Security Vulnerability Detection Using Natural Language Processing (Singh et al., 2022)
- Security for Cloud-Native Systems with an AI-Ops Engine (Ck et al., 2022)
- Overview of Cyber Security (Yadav, 2022)
- Exploring the Top Five Evolving Threats in Cybersecurity: An In-Depth Overview (Mijwil et al., 2023)
- Cyber Security: Strategy to Security Challenges A Review (Nistane & Sharma, 2022)
- A Review Paper on Cyber Security (K & Venkatesh, 2022)
- The Significance of Machine Learning and Deep Learning Techniques in Cybersecurity: A Comprehensive Review (Mijwil, 2023)
- Towards Artificial Intelligence-Based Cybersecurity: The Practices and ChatGPT Generated Ways to Combat Cybercrime (Mijwil et al., 2023)
- ESTABLISHING CYBERSECURITY AWARENESS OF TECHNICAL SECURITY MEASURES THROUGH A SERIOUS GAME (Harding et al., 2022)
- Efficiency Evaluation of Cyber Security Based on EBM-DEA Model (Nguyen et al., 2022)
- An Overview of the Present and Future of User Authentication (Al Kabir & Elmedany, 2022)
- Cybersecurity Enterprises Policies: A Comparative Study (Mishra et al., 2022)
- The Rise of Ransomware: A Review of Attacks, Detection Techniques, and Future Challenges (Kamil et al., 2022)
- On the scale of Cyberspace and Cybersecurity (Pathan, 2022)
- Analysis of techniques and attacking pattern in cyber security approach (Sharma et al., 2022)
- Impact of Artificial Intelligence on Information Security in Business (Alawadhi et al., 2022)
- Deployment of Artificial Intelligence with Bootstrapped Meta-Learning in Cyber Security (Sasikala & Sharma, 2022)
- Optimization of Secure Coding Practices in SDLC as Part of Cybersecurity Framework (Jakimoski et al., 2022)
- CySSS ’22: 1st International Workshop on Cybersecurity and Social Sciences (Chan-Tin & Kennison, 2022)
As you can see, these research topics are a lot more focused than the generic topic ideas we presented earlier. So, for you to develop a high-quality research topic, you’ll need to get specific and laser-focused on a specific context with specific variables of interest. In the video below, we explore some other important things you’ll need to consider when crafting your research topic.
Get 1-On-1 Help
If you’re still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic.

You Might Also Like:

Submit a Comment Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- Print Friendly
- Open access
- Published: 05 January 2022
A decade of research on patterns and architectures for IoT security
- Tanusan Rajmohan 1 ,
- Phu H. Nguyen ORCID: orcid.org/0000-0003-1773-8581 2 &
- Nicolas Ferry 3
Cybersecurity volume 5 , Article number: 2 ( 2022 ) Cite this article
10k Accesses
10 Citations
Metrics details
Security of the Internet of Things (IoT)-based Smart Systems involving sensors, actuators and distributed control loop is of paramount importance but very difficult to address. Security patterns consist of domain-independent time-proven security knowledge and expertise. How are they useful for developing secure IoT-based smart systems? Are there architectures that support IoT security? We aim to systematically review the research work published on patterns and architectures for IoT security (and privacy). Then, we want to provide an analysis on that research landscape to answer our research questions. We follow the well-known guidelines for conducting systematic literature reviews. From thousands of candidate papers initially found in our search process, we have systematically distinguished and analyzed thirty-six (36) papers that have been peer-reviewed and published around patterns and architectures for IoT security and privacy in the last decade (January 2010–December 2020). Our analysis shows that there is a rise in the number of publications tending to patterns and architectures for IoT security in the last three years. We have not seen any approach of applying systematically architectures and patterns together that can address security (and privacy) concerns not only at the architectural level, but also at the network or IoT devices level. We also explored how the research contributions in the primary studies handle the different issues from the OWASP Internet of Things (IoT) top ten vulnerabilities list. Finally, we discuss the current gaps in this research area and how to fill in the gaps for promoting the utilization of patterns for IoT security and privacy by design.
Introduction
The Internet of Things (IoT) is becoming more popular as many “things” are getting more intelligent and connected, e.g., smartphones, smart cars, smart energy grids, smart cities. The IEEE Standards Association defines an IoT system as “a system of entities (including cyber-physical devices, information resources, and people) that exchange information and interact with the physical world by sensing, processing information, and actuating” (IEEE SA 2018 ). In 2019, the International Data Corporation (IDC) made a forecast that there will be 41.6 billion IoT devices in the field by 2025. Footnote 1 Most of the critical infrastructures pointed in the EU’s Directive on security of network and information systems Footnote 2 such as for energy, water, transport, and healthcare are or will be IoT-based. For instance, smart cities are integrating IoT sensors with analytic to streamline spending, improve infrastructural efficiency. Footnote 3 Internet-connected pacemakers have been implanted for millions to help control their abnormal heart rhythms. The IoT will thus play a key role in the digitalization of the society and IoT security issues will “affect not only bits and bytes”, but also “flesh and blood” (Schneier 2017 ). Without solid security in place, attacks and malfunctions in IoT-based critical infrastructures may outweigh any of its benefits (Roman et al. 2011 ). On the other hand, privacy is also very important in the IoT. Many “things” that people use in daily activities at work and at home are now connected to the Internet. This means that sensitive private data can be exposed via the Internet. Privacy challenges are just as important to tackle in comparison to security challenges in the IoT. The heterogeneous networking technologies and resource-constrained devices of the IoT that can only afford lightweight security and privacy solutions are proven to be weak links for IoT systems (Porambage et al. 2016 ). It is also possible that security and privacy are often overlooked by IoT solutions providers (Richa 2021 ), e.g., because of complexity, time-to-market pressure, or due to a lack of knowledge. A way to address this issue could be based on security patterns, which have proven to be very valuable for practitioners, especially non-security experts (Schumacher et al. 2013 ; Fernandez-Buglioni 2013 ).
In the software engineering discipline, patterns document well-known solutions that contain domain-independent knowledge and expertise in a reusable way. The solutions documented by patterns are known to be sound because they are tested over time (Schmidt and Buschmann 2003 ). Moreover, the pros and cons of a pattern are often explicitly documented. Therefore, sketching a solution based on a pattern can provide a good baseline for building the system. Using patterns and architecture alone is not enough but can provide an important support in the development methods for secure systems such as the ones surveyed in Nguyen et al. ( 2015 ). Security patterns consist of domain-independent, time-proven security knowledge, and expertise. Security patterns can contribute to the security and privacy of systems because they offer invaluable help in applying solid design solutions that, for example, secure the user authentication, information processing and storing, secure communication with other devices and with the server. Books and catalogs of security patterns, such as Schumacher et al. ( 2013 ), Fernandez-Buglioni ( 2013 ), Nguyen et al. ( 2015 ) and Steel and Nagappan ( 2006 ) should be useful for users to unravel security challenges by utilizing time-proven security knowledge and expertise.
However, the IoT era introduces new security challenges that existing approaches and methods cannot address. Footnote 4 For example, the cross-domain cyber-to-physical (C2P) attack is the least understood one comparing to P2C, C2C, or P2P attack categories (Yampolskiy et al. 2013 ). IoT systems, especially mission-critical ones, having intrinsic complexity and heterogeneity, broader attack surfaces, often live under uncertainty, which exacerbates security issues (Ciccozzi et al. 2017 ). Indeed, nowadays IoT systems often span across the Cloud layer, the Fog/Edge layer, and the IoT field-devices layer consisting of many smart, connected devices. The explosion in connectivity created a larger attack surface area (Covington and Carskadden 2013 ). Besides, the IoT field-devices often operate under dynamic (physical) execution environments, involving dynamic actuation, but have limited data delivery and storage facilities. In other words, uncertainty is inherent in IoT systems. We are very much interested in examining the landscape of patterns and architectures being applied for the IoT domain, whose security (and privacy) challenges are huge. How have the existing security patterns been applied in tackling IoT security challenges? Are there any new security patterns that have been specifically introduced to address new security challenges in IoT?
To make sense of the research landscape of methodologies around patterns for security and privacy in IoT, we have conducted a systematic literature review (SLR) following the most popular guidelines from Kitchenham et al. ( 2011 ), Kitchenham and Charters ( 2007 ), Petersen et al. ( 2015 ) and Wohlin ( 2014 ). Our SLR has three fundamental objectives. First, we need to find out the approaches around patterns and architectures for IoT security and privacy, called the primary studies of our SLR. Second, by analyzing the primary studies, we can perceive gaps in the state-of-the-art of patterns and architectures for IoT security and privacy. We are particularly interested in how advanced patterns and architectures are, and their approaches to address IoT security. Third, based on the results, we identify the gaps to support security and privacy in modern IoT systems and propose further research to fill the gaps. The main contributions of this work are our responses to the accompanying research questions (RQ)s.
RQ1 What are the publication statistics of the research on patterns and architectures for IoT security and privacy?
RQ2 What are the technical details of these security patterns and architectures for addressing IoT security and privacy?
RQ3 What are the “gaps” to make security patterns and architectures more applicable for IoT?
From thousands of candidate papers initially found in our search process, we have systematically distinguished and analyzed 36 papers that have been published around patterns and architectures for IoT security in the last decade. Our analysis results show the trend of an increasing number of published papers in this research area in three recent years. We have performed our analysis based on a taxonomy that we built for this research area. Our analysis sheds some light on the state of the art around patterns and architectures for IoT security and the current limitations. Based on our analysis, we provides some suggestions for a way forward of this research topic. Specifically, the contributions in this paper include:
We have an exhaustive database search process. Moreover, we manually conducted snowballing (backward and forward as suggested in Wohlin 2014 ). We identified and included six new primary studies from this snowballing process. Therefore, our final set of primary studies reported in this paper is 36 (see “ Our systematic literature review approach ” section).
We have defined a clear taxonomy (see “ Taxonomy of the research area ” section) and provided in-depth analyses on the architectures and patterns from the primary studies (see “ Technical aspects of the primary studies (RQ2) ” section). For example, we summarize all the patterns from the primary studies and also discuss how the architectures from the primary studies cover the seven layers of the IoT World Forum Reference Model of the IoT architecture (Juxtology 2018 ).
We have provided discussion on the existing gaps and limitations in “ Gaps and limitations (RQ3) ” section. For example, we discuss the gaps in the research contributions from the primary studies regarding how they handle the different issues presented by the OWASP IoT top ten vulnerabilities list (OWASP 2018 ). Last but not least, we explicitly discuss the possible threats to validity of our study in “ Threats to validity ” section to give readers more insights in this work.
In the remainder of this paper: “ Background ” section gives some background definitions. In “ Our systematic literature review approach ” section, we present our SLR approach. To facilitate data extraction and comparison, “ Taxonomy of the research area ” section describes our classification schemes for the primary studies. We present the results of our SLR in “ Results ” section. Related work is discussed in “ Related work ” section. In “ Threats to validity ” section, we analyze possible threats to the validity of this work. Finally, we conclude the paper with summarizing the main findings in “ Conclusions ” section.
We give the definitions of SLR in the “ Systematic literature review ” section, (security) design patterns in the “ Design pattern ” section, and security architecture in the “ Security architecture ” section that were used to define the scope of this work.
Systematic literature review
A SLR is a study that “reviews all the primary studies relating to a specific research question”, and “uses a well-defined methodology to identify, analyze and interpret all available evidence related to that specific research question in a way that is unbiased and (to a degree) repeatable.” (Kitchenham et al. 2011 )
Design pattern
The primary understanding for a design pattern is that it is a reusable solution for a typical occurring issue in software design. A pattern is ordinarily abstract with the goal that it may be reused, and it is a proven solution for solving a software design problem. A design pattern is not a complete implementation that can be executed and utilized, but more a plan or template for how to take care of an issue that can serve in various circumstances/contexts (Gamma et al. 1994 ; Fernandez-Buglioni 2013 ).
According to Schumacher et al. ( 2013 ), “a security pattern describes a particular recurring security problem that arises in specific contexts, and presents a well-proven generic solution for it. The solution consists of a set of interacting roles that can be arranged into multiple concrete design structures, as well as a process to create one particular such structure.”
Note that there are key security patterns such as from Schumacher et al. ( 2013 ), Fernandez-Buglioni ( 2013 ) and Steel and Nagappan ( 2006 ) that provide guidance at the architecture level. These patterns may also be called security architectures but yet they are design patterns and should be considered as patterns. In other words, we clearly call architectural patterns as patterns, not architectures. This definition means that we only consider an architecture as a pattern if it is explicitly described as a pattern. Any architecture for IoT security that is not a pattern is called “security architecture” in this paper.
Security architecture
The term sofware architecture typically refers to the structure of a software system, including software elements and the relationships between them. Within our SLR, we want to include architectures for IoT security or architectures that were specifically designed with IoT security concerns in mind. When architectures are not formalized as a pattern, we call them IoT security architectures, as opposed to architectural patterns. When a security architecture is generic enough to be used in different contexts, it is called an IoT security reference architecture. It is worth discussing the relationship between IoT security reference architectures and IoT security patterns: (1) IoT security patterns can be extracted from an IoT security reference architecture, and (2) an IoT security reference architecture can leverage and be composed of one or several patterns, including IoT security patterns. By analyzing not only security patterns but also security architectures, our study aims to cover security aspects encompassing not only only one layer of IoT systems but also multiple layers when architectures are key to address.
Our systematic literature review approach
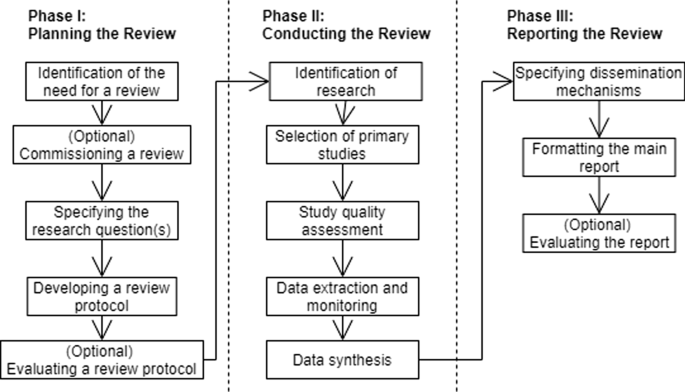
We conducted our SLR using the most popular guidelines from Kitchenham et al. ( 2011 ), Kitchenham and Charters ( 2007 ), Petersen et al. ( 2015 ) and Wohlin ( 2014 ). Three main phases of an SLR are: Planning the Review, Conducting the Review, Reporting the Review (see Fig. 1 ) (Kitchenham and Charters 2007 ).
The process of planning, conducting, and reporting a SLR (Kitchenham and Charters 2007 )
We map the stages associated with planning our SLR with where we present them in this paper:
Identification of the need for a review: In the “ Introduction ” section, we have presented the motivation of our SLR.
Specifying the research question(s): the “ Research questions ” section.
Developing a review protocol: Our review protocol is developed according to the guidelines in Kitchenham and Charters ( 2007 ). The main parts of our review protocol are the research questions (“ Research questions ” section), the inclusion and exclusion criteria (“ Inclusion and exclusion criteria ” section), the search and selection strategy (“ Search and selection strategy ” section), and the taxonomy for data extraction and synthesis (“ Taxonomy of the research area ” section).
The stages associated with conducting our SLR:
Identification of research: Search and selection strategy (“ Search and selection strategy ” section).
Selection of primary studies: Search and selection strategy (“ Search and selection strategy ” section).
Study quality assessment: We only selected peer-reviewed papers with enough details as the primary studies of this SLR (“ Inclusion and exclusion criteria ” section).
Data extraction and monitoring: We extracted data based on the taxonomy defined in “ Taxonomy of the research area ” section.
Data synthesis: We synthesized the extracted data to answer our research questions in “ Results ” section.
The stages associated with reporting our SLR:
Specifying dissemination mechanisms: We specified the journal to publish the results of our SLR.
Formatting the main report: This paper.
With the particular context and motivation displayed in “ Introduction ” section, we introduce our RQs for this paper in “ Research questions ” section. In “ Inclusion and exclusion criteria ” section, we explain the criteria for choosing primary studies to explicitly portray the scope of our SLR and diminish possible bias in our selection procedure. “ Search and selection strategy ” section shows our search strategy to locate the primary studies for answering the RQs.
Research questions
This SLR aims to answer the three RQs presented in “ Introduction ” section. Each is extended with sub-questions.
RQ1 includes three sub-RQs. RQ1.1 In which year(s) are the primary studies published? Answering this question allows us to know when this research topic became fascinating as well as how recent the research on this topic is. It could give an indicator of how much attention security patterns and secure architectures for IoT get from the research community. RQ1.2 — What are the types (i.e., Journal, Conference, Workshop) and target domains (e.g., IoT, Network, Cloud and Software Engineering (SE)) of the venues where the primary studies were published? Answering this question allows us to recognize the target domain for each paper. Note that security patterns are presented in publications across a few related research areas, e.g., IoT, Cloud, SE, Network. The type of paper can give a few hints on the maturity of the primary study. Journal papers should report more mature studies than conference papers. RQ1.3 — How is the distribution of publications in terms of papers affiliated with industry and the academic? We classify a paper as academic if all the associated authors are with a university or a research institute. Moreover, we group papers as industrial if all related authors are with an industrial organization, and characterize the papers as both if there is a coordinated effort of both academia and industry. Answering RQ1.3 will display the collaboration effort between industry and scholar communities. It also demonstrates the interest and needs of IoT security patterns in the industry.
RQ2 has three sub-RQs. RQ2.1 — What type (e.g., security pattern, architecture) of contribution do the primary studies create or use, and how the distribution is between them? Answering RQ2.1 shows how the distribution of patterns and architectures are, as well as how the contribution is used or for what purpose. RQ2.2 — How well do the patterns and architectures cover security and privacy issues? Answering this RQ shows what security patterns and architectures focus on IoT systems’ specific security and privacy concerns. It also shows us what current security and privacy concerns are most covered today. RQ2.3 — What application domains have been addressed by the security patterns and architectures? This RQ can help us to see what application domains have got more attention in the application of security patterns and architectures.
RQ3 also has two sub-RQs. RQ3.1 — What are the current limitations of the IoT security patterns and architectures research? RQ3.2 — What research directions could be recommended for tackling the current limitations? These RQs help to express and suggest the current issues and possible directions for future work.
Inclusion and exclusion criteria
Considering the RQs and the basis of our study introduced in “ Introduction ” section, we predefined the inclusion and exclusion criteria to decrease bias in our methodology of search and selection of primary studies. The primary studies must meet ALL the accompanying inclusion criteria (IC):
(IC1) Contain patterns or architectures (one or more) in some form relevant for IoT systems.
(IC2) Be specifically within the area of IoT, either in a generally applicable domain or in a specific application domain of IoT.
(IC3) Present security (or privacy) concerns explicitly in system design, architecture, or infrastructure.
(IC4) Have a minimum length of four pages in double-column format or six pages in single-column format.
Moreover, when a single approach is presented in more than one paper describing different parts of the approach (e.g., approach itself, empirical study, evaluation), we include all these papers, but still consider them as a single approach (study). When encountering more than one paper describing the same or similar approaches, which were published in different venues, we only include the most recent one that has the most complete description of the approach.
We excluded papers that are not written in English, non-peer-reviewed papers (e.g., “grey” literature, white papers in industry), and papers that are only accessible as extended abstracts, posters, or presentations (not full version). We also did not include multivocal surveys as primary studies because they are secondary studies. We do discuss the surveys on related topics as related work in “ Related work ” section. We also mainly focused our review for the publications in the duration 2010–2020 (see “ Search and selection strategy ” section).
Search and selection strategy
The search strategy utilized is a blend of various kinds, to thoroughly scan for IoT security pattern and architecture papers. The objective is to locate the most relevant papers and, along these lines, discover as many essential IoT security pattern and architecture papers as possible.
Database search
Using online inquiry components of popular publication databases is the most notable approach to scan for essential primary studies when directing supplemental studies (Kitchenham and Charters 2007 ). We used five of the popular publication databases IEEE Xplore, Footnote 5 ACM Digital Library, Footnote 6 ScienceDirect, Footnote 7 Web of Knowledge (ISI), Footnote 8 and Scopus Footnote 9 to search for potential primary studies. Scopus and ACM DL already index SpringerLink Footnote 10 (Tran et al. 2017 ). The five picked databases contain peer-reviewed articles, which give advanced search capacities. Following the guidelines from Kitchenham and Charters ( 2007 ), based on the research questions and keywords utilized in some related articles, we have defined our search keywords. The search query was adopted to fit each of the search engines of the five publication databases. Note that we did not include “misuse pattern” in the search query because misuse patterns (from the point of view of the attacker) are out of scope of this study.
( “Internet of Things” OR “IoT” OR “Cyber Physical Systems” OR “Web of Things” )
( “Security Pattern” OR “Design Pattern” OR “Security Design Pattern” OR “Privacy Pattern” OR “Security Architecture” OR “Secure Architecture” )
During our database search process, we did conduct many rounds of testing the search query on the search engines. On the one hand, this testing process helped us to improve our search query and customize it for better fit the search features. On the other hand, we also saw very few hits returned by the search engines for the duration 2000–2010. Therefore, we mainly focused our review for the publications in the duration 2010–2020.
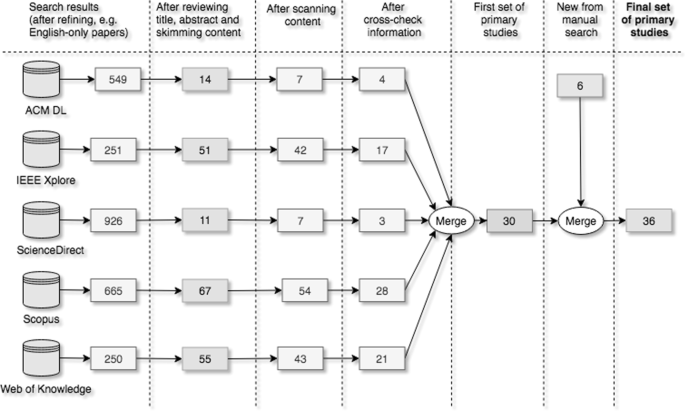
For every candidate paper, we originally reviewed the paper’s title and abstract, trailed by skimming through the contents. On the off chance that an applicant paper shows up in more than one database, we show them in the other database results. When merging to the first set of primary studies, we consolidate the outcomes, so we get the right number of papers without copies. It is portrayed step by step in Fig. 2 .
Overview of the search and selection steps
Manual search
It is unrealistic to guarantee the database search results can cover all IoT security patterns and architectures in our study. We have, therefore, attempted to supplement the database search by doing a manual search. We started by manually searching through published papers from previous journals and conferences. The conferences and journals we went through to find papers were: The International Conference on the Internet of Things, Footnote 11 Pattern Languages of Programs (PLoP), Footnote 12 EuroPLoP, Footnote 13 IEEE ICIOT, Footnote 14 ACM Transactions on Internet of Things (TIOT) Footnote 15 and IEEE Internet of Things Journal. Footnote 16 We also manually did snowballing (backward and forward) on all the primary studies found as suggested in Wohlin ( 2014 ). In the wake of looking through these journals and conferences as well as doing snowballing, we concluded that most of the relevant papers posted or found from our manual search were earlier discovered from the database search, or they did not satisfy our criteria. The papers from the manual search were checked against the automatic results, and vice versa. In the end, we had found six more primary studies from the manual search process.
Note that any candidate paper in doubt was kept for evaluation and cross-checked among the reviewers at each phase of our search and selection process. Our gathering conversations have finally yielded a set of 36 primary studies for data extraction and synthesis to answer the RQs Footnote 17 .
Taxonomy of the research area
In this section, we define a taxonomy for IoT security patterns and architectures. This taxonomy helps us to extract and synthesize data from the primary studies for answering the RQs. We applied a top-down strategy to process data from the literature around IoT, security patterns, IoT architectures, and design patterns to create a first version of the taxonomy. We also tried to validate and enrich the taxonomy by a bottom-up approach. The bottom-up approach is for extracting data from a test set of primary studies. This test set consists of the initial ten primary studies chosen. It helped us to characterize and determine the significant methods and terminology utilized in the primary studies.
Domain specificity
We characterize the domain specificity in the same manner as (Washizaki et al. 2020 ) with minor tweaks. It is essential to examine the applicability and reusability of each IoT security pattern.
General IoT security design patterns, and security architectures, which apply to any IoT system and software.
Specific IoT security design patterns, and security architectures that address specific problem domains (such as healthcare) and technical domains (such as the brain-computer interaction).
Categorization of security pattern research
We classify security patterns according to the main categories presented in Yskout et al. ( 2006 ). First, we distinguish security patterns based on how they affect the software application or the environment (e.g., infrastructure, middleware) in which the application will eventually be deployed.
Application architecture (AA): A pattern’s introduction can affect an extensive part of the application, e.g., by introducing new components in the application, or modifying existing components.
Application design (AD): A pattern’s introduction only has local implications. For example, a pattern can introduce some form of encapsulation of security data.
System (S)/Execution environment: A pattern’s introduction only affects the environment in which the application will be deployed.
We classify the (security, privacy) objectives of the patterns as presented below in “ Security and privacy concerns ” section. More importantly, we detail the patterns by their main properties from the software design pattern template by the Gang of Four (Gamma et al. 1994 ):
Intent: What (in what context) is the pattern used for? What is the purpose of the pattern?
Problem: What problem that the pattern can address. This may also include the different forces (and context) that lead to the problem.
Solution: A description of the solution provided by the pattern.
We also characterize patterns by purpose , method , and research implementation , which is similar to how Washizaki et al. ( 2018 ) did in their paper.
C1 purpose: This part includes the topics addressed by the research, software life-cycle, and the intended users.
C2 method: This part refers to the methodology and modeling methods to define the pattern’s structure and design.
C3 research implementation/validation: This part includes where, how and if the contributions were implemented and tested/validated, and in which context. It also includes analysis of a test case or scenario. Whether the results are automated and encapsulated in a tool, and whether case studies or experiments are conducted to evaluate the results relevant to the original research purpose.
IoT architecture
Many IoT architecture exist in the literature, all decomposed in a different number of layers. In our taxonomy, we leverage the IoT World Forum Reference Model of the IoT architecture (Juxtology 2018 ). This architecture provides a fine-grained granularity over the different layers that typically compose an IoT system. It has recently been adopted in many large scale IoT systems, for instance, as indicated in Create-IoT ( 2018 ), all of the H2020 IoT large scale pilots at the exception of one, have adopted this architecture. It consists of the following seven layers:
L1 physical devices and controllers: Physical layer consisting of devices or “things” of the IoT. The “things”, sensors, and Edge Node devices are classified within this layer.
L2 connectivity: Connectivity spans from the “middle” of an Edge Node device up through transport to the Cloud. This layer maps data from the logical and physical technologies used, the communication between the physical layer and the computing layer, and above.
L3 edge computing: Layer that brings computation and data storage closer to the location it is needed. Protocol conversion, routing to higher-layer software functions, and even “fast path” logic for low latency decision making will be implemented at this layer.
L4 data accumulation: Intermediate storage of incoming storage and outgoing traffic queued for delivery to lower layers. Pure SQL is what the layer is implemented with, but it may require more advanced solutions, i.e., Hadoop & Hadoop File System, Mongo, Cassandra, Spark, or other NoSQL solutions.
L5 data abstraction: Data is made clear and understandable, centers around rendering data and its storage in manners that enable developing more straightforward, performance-enhanced applications. This layer speeds up high priority traffic or alarms, and sort incoming data from the data lake into the appropriate schema and streams for upstream processing. Likewise, application information bound for downstream layers is reformatted appropriately for device communication and queued for processing.
L6 application layer: At the application layer, information interpretation of multiple IoT sensors or measurements occur, and logic is executed. Monitoring, process optimization, alarm management, statistical analysis, control logic, logistics, consumer patterns, are just a few examples of IoT applications.
L7 collaboration and processes: Application processing to its users, and data processed at lower layers are integrated with business applications. This layer consists of human interaction with all the layers of the IoT system, and economic value is delivered.
Another simpler IoT architecture largely adopted in the literature consists of three layers: perception (L1), network (grouping L2 and L3), and application (grouping L4, L5, L6, L7, and L8). We map how the contributions of today fit in both the IoT World Forum Reference Model of the IoT architecture and the three-layer IoT architecture.
Security and privacy concerns
We analyze the primary studies according to the following security and privacy concerns: confidentiality, integrity, availability (CIA), accountability, and privacy (Ross et al. 2016 ; Kuhn et al. 2001 ; Yskout et al. 2006 ). These concerns are what we consider essential to IoT systems and devices. We also classify security mechanisms such as authentication and authorization when such information are available in the primary studies. We want to see what patterns and architectures uphold and protect against these security and privacy concerns. Their definitions are as follows.
Confidentiality: Ensures the property that information is not made available or disclosed to unauthorized individuals, entities, or processes.
Integrity: Maintains and ensures the accuracy and completeness of the data during its life-cycle.
Availability: The information/service is available when needed.
Authentication: The system/device can verify a claim of identity.
Authorization: The system can determine what resources the entities that have been identified and authenticated can access and what actions they can perform within/on the system.
Accountability: Enables the tracing of important (or all) actions performed on the system back to a particular user, usually by means of logging.
Privacy: The data collected is legally collected and stored, how data is shared, and follow regulatory restrictions from the GDPR (mostly EU), and HIPAA (Office for Civil Rights 2013 ), GLBA (Federal Trade Commission 1999 ) (mostly in the US).
This section presents the main results of our SLR and how our research questions are answered. Table 1 shows an overview of the primary studies that have been found in this review regarding patterns and architectures for IoT security and privacy. Based on the taxonomy in “ Taxonomy of the research area ” section, we have extracted and synthesized the primary studies’ data to answer the RQs. “ High-level statistics (RQ1) ” section shows high-level statistics that help us to answer RQ1. Then, we present low-level details of the primary studies in “ Technical aspects of the primary studies (RQ2) ” section that help us to answer RQ2. Based on our answers to RQ1 and RQ2, we discuss the gaps and limitations as our answer to RQ3.
High-level statistics (RQ1)
In this section, we provide our answers to the RQ1- What are the publication statistics of the research on patterns and architectures for IoT security and privacy?
Answering RQ1.1 In which year(s) are the primary studies published? Fig. 3 shows a rise in the number of conference (C) and journal (J) publications related to IoT security patterns and architectures in the recent three years (2018: 7C, 2019: 5C, 4J and 2020 Footnote 18 : 5C, 5J). This spike shows that security patterns and architectures are gaining more focus over the years and that there is a demand for IoT security pattern and architecture research.
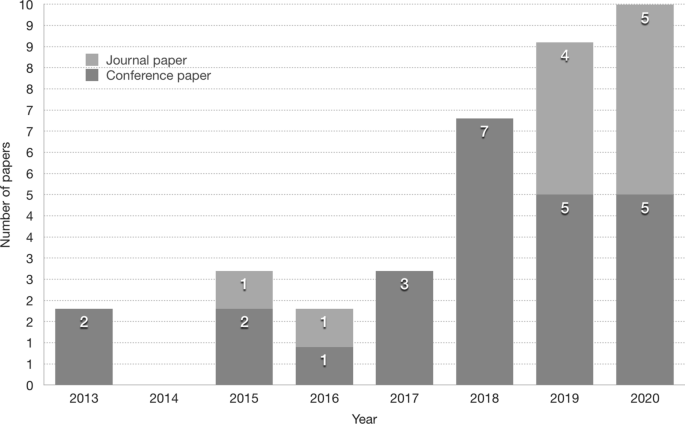
Publications per year, per venue type
Answering RQ1.2 What are the types (i.e., Journal, Conference, Workshop) and target domains (e.g., IoT, Network, Cloud and Software Engineering (SE)) of the venues where the primary studies were published? Research on the IoT, with its heterogeneous nature, traverses through various important research areas, among which we perceived Software Engineering (SE), Cloud, Blockchain, Network, and recently specialized IoT research (Borgia et al. 2016 ). Figure 4 shows the research focus areas of the publication venues where the primary studies have been published. The main research areas that we found are between IoT: 36, Cloud: 4, Network: 7, Blockchain: 7. Note that publication venues often have several research areas in their calls for papers, e.g., IoT, network. Therefore a portion of the papers could be classified in several research areas at the same time (e.g., IoT, network). These numbers do reflect the different dimensions of IoT research, with IoT research domain getting progressively more visible. In other words, IoT-oriented conferences and journals are becoming more popular and have attracted research contributions on patterns and architectures for IoT security and privacy.
The number of primary studies that are published as conference papers are more than double the number of primary studies published in journals. From the number of publications found, we distinguished the distribution of conference papers ( \(\sim\) 69%) and journal papers ( \(\sim\) 31%). It is reasonable that conference papers tend to be published more often and quickly. But, we also see that the number of journal papers has increased since our last study (Rajmohan et al. 2020 ). We do, however, believe and encourage a continued increase of journal papers around this topic. Especially seeing that the growth of IoT is increasing rapidly and that journal papers contribute to more detailed and elaborated contributions.
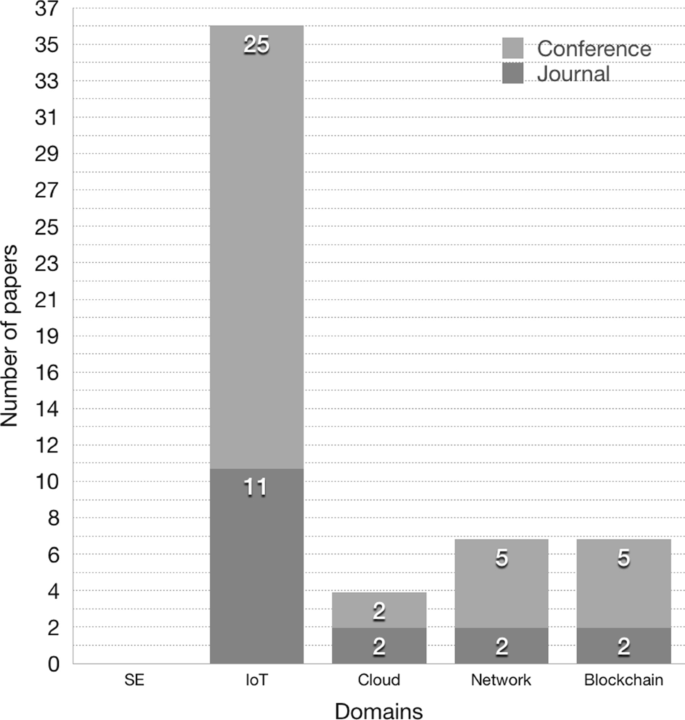
Research topics per publication venue
Answering RQ1.3 How is the distribution of publications in terms of papers affiliated with industry and the academic? Because IoT systems and devices are broadly utilized and growing in the industry and consumer market, we explored how the affiliations of the authors are dispersed from the primary studies. Would the affiliations of the authors have any implication on the publication of security patterns and architectures for IoT? From our analysis, we see that a significant amount of the authors who have published results on IoT security patterns or architectures are from academia ( \(\sim\) 75%). While there are no contributions exclusively from industry, authors working in industry do publish in joint efforts with co-authors from academia. In this work, we call the papers that have such joint efforts of academia-industry collaboration as “joint papers”. We discovered some papers of this type ( \(\sim\) 25%). The percentage of joint papers here is not high, but still remarkable compared to less than 10% of joint papers as primary studies reported in another review on security for cyber-physical systems (Nguyen et al. 2017 ).
Joint papers tend to have more usage examples and illustration contrasted with papers purely from academia. We saw in our study that 89% of the joint papers had graphical illustrations of their contribution in terms of architectural structure or pattern usage areas. The number of joint papers among academia and industry shows a promising collaboration level. We trust that this number continues to grow. The collaboration is win-win for the state of the art and practice, which can lead to the utilization of patterns and architectures proposed to improve products, production process, and internal processes that use IoT devices or systems further. We would be intrigued to see more implementations or examples of security patterns or architectures used by industry in the future.
Technical aspects of the primary studies (RQ2)
All the patterns and architectures in Table 1 have been examined according to our taxonomy (“ Taxonomy of the research area ” section), to give us meaningful information as well as pinpoint how the papers are relevant and where they contribute. The taxonomy was used to ensure that the primary studies have information relevant to this study. We can draw out some key examples, such as papers (Vijayakumaran et al. 2020 ; Vithya Vijayalakshmi and Arockiam 2020 ; Jerald et al. 2019 ; Pacheco et al. 2018 ), which are the ones who cover most security concerns (“ Security and privacy concerns ” section). We based on the (more fine-grained) data extracted from the primary studies to answer RQ2 : What are the technical details of these security patterns and architectures for addressing IoT security and privacy?
Answering RQ2.1 What type (e.g., security pattern, architecture) of contribution do the primary studies create or use, and how the distribution is between them? After finalizing the primary studies set, we found that the primary studies’ main contributions are either architectures ( \(\sim\) 81%) or patterns ( \(\sim\) 19%). These contributions are mostly solution proposals, where some have proper testing and validation ( \(\sim\) 57%) of their concept. Other papers have use case examples ( \(\sim\) 23%) in some form, and some papers even have implementations of their concept ( \(\sim\) 20%). As we presented in “ Security architecture ” section, papers describing frameworks are categorized as architectures (not patterns, if patterns are not explicitly mentioned). Therefore, we see a more significant contribution and more focus on architectures compared to patterns.
Claiming security solely based on a good architecture can be inadequate because it is typically not enough for end-to-end IoT security. We have seen other cases where architectures are not enough to solve the specific issues regarding e.g., user verification on the devices, firmware manipulation, and an attacker disconnects the devices upon will. Such issues are hard to handle only with security architecture solutions. The lack of security patterns is a result of its youth within the domain and security not being the main priority when developing IoT systems. Certain areas of an IoT system may need more attention than others regarding security, and architectures may not solve those issues. From our experience and information gathering, we have seen that the architecture solutions for IoT security have focused a lot on the whole system and all its layers (e.g., Cloud, Edge, IoT devices Juxtology 2018 ), more general system issues, and can target specific domains, but are very seldom enough to solve a specific problem. The architectures tend to focus on multiple layers (e.g., Cloud, Edge Juxtology 2018 ) and are harder to address a single layer issue or an issue in a small part of one of the architectural layers, where some specific security patterns may apply well.
As mentioned, a good architecture is only part of the solution and can be inadequate if we encounter specific security issues for a smaller area rather than the whole system, e.g., the breach on a casino’s thermostat in a fish tank to access customer data (Williams-Grut 2018 ). This breach shows the challenge to ensure end-to-end security for IoT systems, especially at their weakest links, e.g., a thermostat. Therefore, it would be exaggerating to tackle security only at the architectural level. A more straightforward solution would have been a security pattern for authentication of users or networks not to allow external communication to pass through IoT devices or verify the device when communication is sent. A more complete solution would be to employ suitable specific security patterns in a well-designed architecture. In other words, a high-level architecture supporting IoT security is only one side of the coin. The other side of the coin is to address specific IoT security challenges at any weak links such as IoT devices where some specific security patterns can help.
Table 2 shows which concerns regarding security and privacy for IoT are addressed by each of the 36 primary studies. When we compare the number of primary studies to the number of candidate papers we first found while doing the automatic search, there is a big difference. This means that security and IoT are popular keywords in many publications but “security patterns” for IoT is not. However, we still believe 36 is a reasonable amount, yet it ought to be higher with the goal that security patterns become increasingly frequent and accessible for industry and users who want to develop secure IoT systems.
Table 2 also shows us the distribution of the specificity of the various contributions. We see that most contributions fall under the “Generic” regarding application domains (“ Domain specificity ” section), which means that a substantial number of papers are adaptable for a widespread of IoT systems. These “Generic” solutions cover the core functionalities of an IoT system, which is why we labeled them “Generic” compared to the domain-specific solutions, which work within a specific domain for a specific purpose (e.g., smart cars, smart meters, and healthcare systems). As we can see, most of the contributions cover authentication, which is a crucial aspect of any system. One may link the amount of authentication coverage to the fact that several smart devices have been hacked due to a lack of authentication (Wright 2020 ). Even though authentication is the most focused concern in the primary studies, more efforts are needed for end-to-end security, including weak links in IoT systems. We would like to see more of such solutions and solutions for IoT pressing problems, e.g., communication, compatibility, integration, and scalability.
Answering RQ2.2 How well do the patterns and architectures cover security and privacy issues?
Table 2 shows a more detailed list of the concerns mentioned previously and what type of application domain the contributions have. We marked the concerns with an “x” if the concern was directly mentioned in the paper. The concern regarding privacy was only marked if it was explicitly mentioned, and not if they handle only the security concerns even they can contribute to privacy coverage.
Figure 5 displays the mapping of our security concerns based on the contribution. We weight how much each (security or privacy) concern was addressed in the primary studies compared to each other. We do so by simply calculating the percentage of how many times a concern was addressed compared to the total number of the times that all concerns were addressed. Note that as shown in Table 2 , most primary studies address more than one concern. As Fig. 5 shows, there is a widespread of focus between the security concerns (Confidentiality \(\sim\) 16%, Integrity \(\sim\) 19%, Availability \(\sim\) 8%, Authentication \(\sim\) 25%, and Authorization \(\sim\) 17%). Privacy ( \(\sim\) 15%) is relatively focused comparing to the security issues in terms of coverage within the primary studies. The low coverage for the availability concern could come from a lack of explicit explanation in the primary studies or availability was not considered in their solutions at all. In the first case, this is comprehensible as availability is a concern whose scope is broader than the only security domain. Indeed, preserving the availability of a system is tightly coupled to the ability of scaling it. Load scalability is the ability of a service to sustain variable workload while fulfilling quality of service (QoS) requirements, possibly by consuming a variable amount of underlying resources (Ferry et al. 2014 ). It is a core concern when engineering and designing complex system, and, as a result, many design patterns, including architectural patterns, have been defined in the literature from other fields (e.g., Big data, Cloud computing, large-scale systems, middleware).
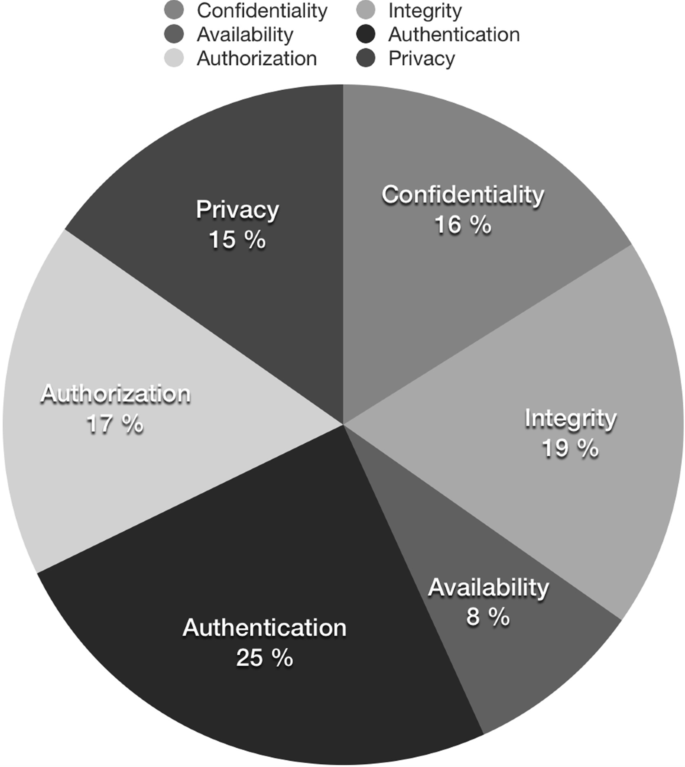
Security concerns based on the contribution
Table 2 can give a closer look on how many contributions of patterns and architectures focusing on the various concerns. For patterns, we see that only two papers out of seven security pattern papers cover the whole CIA (Confidentiality, Integrity, and Availability) triad, while security architecture papers have two out of 29 papers. Availability is the least covered concern in the primary studies. We are unsure if it is because the contributions focus mostly on authentication, but since many of these systems process or share information, we would argue that the basic CIA triad should be focused. Figure 6 illustrates the different security considerations and privacy, and shows which ones are more focused on in the papers found. Authentication is most focused by the primary studies. This point is understandable because authentication is often the foundation for building other security mechanisms such as for authorization, confidentiality, or privacy. But, the low focus on availability is something that should be drawn attention to because availability is crucial in many IoT systems, especially critical ones.
Another thing to notice is that privacy is considered in 18 out of the 36 papers. This number shows that privacy has gained nearly as much attention as security concerns in the primary studies. As mentioned previously, some papers and concerns may contribute indirectly to privacy, e.g., concerns such as authentication and authorization that verify and provide the correct access to users, which can be one way to preserve users’ privacy. But, we only count for privacy if a primary study does mention privacy explicitly.
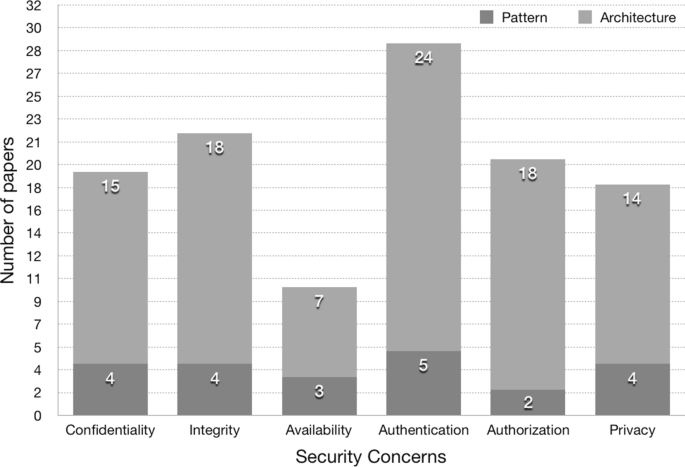
Architectures and patterns with focus on each security concern
Table 3 shows the IoT security and privacy patterns that are presented in the primary studies. It is worth to note that there is one primary study (Pape and Rannenberg 2019 ) dedicated to IoT privacy patterns. There are seven patterns for IoT privacy presented in Pape and Rannenberg ( 2019 ), which describe different possibilities of privacy violation and the corresponding solutions. We summarize these patterns according to the main elements of security pattern in Table 3 . There is another paper that even presents a misuse pattern (Syed et al. 2018 ). Paper Syed et al. ( 2018 ) shows a misuse pattern for Distributed Denial of Service (DDoS) in IoT. They specify appropriate countermeasures for mitigating it, contributing to a specific problem in many IoT systems. Paper Fysarakis et al. ( 2019 ) discusses a pattern-driven framework solution to encode dependencies between the security concerns mentioned in “ Security and privacy concerns ” section. More specifically, paper Fysarakis et al. ( 2019 ) presents orchestration models required for IoT and IIoT applications to guarantee quality properties including security, privacy. In the same direction but more on the trustfulness, paper Pahl et al. ( 2018 ) proposes an architecture pattern based on blockchain to ensure the identity of hardware devices and software applications, the origin and integrity of data and the contractual nature of orchestration. There is only one paper (Schuß et al. 2018 ) that proposes a pattern at the hardware layer for IoT security. Schuß et al. ( 2018 ) show a pattern to secure the device through hardware, by implementing exchangeable cryptographic co-processors. This paper provides security features that can be implemented to a general IoT system, but it requires changes or additions to the hardware. The hardware-based approach in Schuß et al. ( 2018 ) aims at allowing even constrained devices to utilize state-of-the-art cryptographic functions.
While the papers mentioned so far present IoT-specific patterns, the last two papers (Lee and Law 2017 ; Ur-Rehman and Zivic 2015 ) in Table 3 focus more on how generic security patterns can be applied for IoT. For example, both of them show how the well-known Secure Logger pattern can be used in IoT. Paper Lee and Law ( 2017 ) shows multiple patterns in which they describe and explain some usage areas, but they do not show results in these usage areas. It is more for cataloging purposes including other generic security patterns such as Secure Directory, Secure Adapter Pattern, Exception Manager Pattern, and Input Validation Pattern. Paper Ur-Rehman and Zivic ( 2015 ) presents the patterns that are adopted for smart metering systems. The Secure Remote Readout pattern is presented in details in Ur-Rehman and Zivic ( 2015 ). The other patterns are name checked only such as Secure Logger, Key Manager, Wakeup Service, and Transport Layer Security.
As mentioned in the previous section, patterns target more specific parts of an IoT system, which also makes it easier to implement a pattern for that section of the system. In most cases, architectures are harder to implement/adopt because they propose a solution for multiple parts or the whole system but often lack security details for specific parts. We discuss some representative examples of the papers we found that explicitly address, propose, or use security architectures such as Vithya Vijayalakshmi and Arockiam ( 2020 ), Witti and Konstantas ( 2018 ) and Pacheco et al. ( 2018 ). Paper Vithya Vijayalakshmi and Arockiam ( 2020 ) discusses an architecture that protects the data security at all the layers of data flow, the transmission of data is essential in this contribution. Paper Witti and Konstantas ( 2018 ) shows architectures in use-cases where they apply and discuss how they are used and the results. Paper Witti and Konstantas ( 2018 ) also explains how architecture can help securing a smart city while preserving citizens’ privacy in that city. A good example of security architecture can be found in paper Pacheco et al. ( 2018 ) by Pacheco et al. ( 2018 ), which proposes a security framework for a smart water system. That paper displays security issues at most of the IoT layers and proposes security algorithms for these issues to make developers consider security early rather than an ad-hoc or afterthought manner.
Answering RQ2.3 What application domains have been addressed by the security patterns and architectures? From Table 2 we see that nine primary studies have presented the application of IoT security patterns/architectures for some specific IoT application domains. The specific IoT application domains can help our analysis in the way they elaborate on the issues and how to mitigate them. Explicitly mentioning IoT application domain has the tendency to show that the patterns can be applied in the domain and can address the requirements in this IoT domain. Some patterns could be more important for some specific domains. For example, for smart city applications, patterns for scalability is important. For e-health, patterns for privacy are important. The primary studies that do explicitly present IoT application domains would address more clearly the IoT-specific requirements or challenges. The domain-specific solutions are created for the domains mentioned, but they may still be applicable in other domains. However, these domains usually take the initiative to incorporate IoT, which explains why these areas have specific solutions before others. We also saw that many of these domain-specific studies had graphical figures describing their contribution to show how they work or the different layers of their architectures.
We consider that domain-specific contributions may not necessarily have a more significant impact on IoT security, but it is better portrayed when having a real case scenario or issue. Both the generic and specific domain contributions cover approximately three security concerns per paper, so they both stand approximately equally strong in security concerns coverage. We believe these domain-specific contributions are getting more attention, but it may still not be a better solution than the general solutions that can apply to more systems or handle more generic issues. It is still good to see more security patterns and architectures in real cases to better grasp the contribution and the issues around these domains.
Table 2 can give us some ideas on any difference in terms of addressing security and privacy concerns between the papers by academic authors and the papers authored by both academia and industry. The joint papers on average cover \(\sim 3,2\) concerns per paper, while the “academic-only” papers on average cover \(\sim 3,3\) concerns per paper. We see that both types of paper cover at least over half of our security concerns on average. To better compare the difference between academic-only papers and joint papers in terms of addressing security and privacy concerns, we visualize the number of papers addressing each concern in Fig. 7 . The first glance at Fig. 7 may give us an impression that the papers from academia have a broader coverage than the joint. This impression makes sense because academic-only papers are nearly three times more than joint papers. However, the number of academic-only papers addressing privacy (15) is five times the number of joint papers addressing privacy (three). Would this comparison imply that privacy (compared to other concerns) has gained more focus in academic-only papers than in industry-oriented papers? On the other hand, the number of academic-only papers addressing availability (eight) is four times the number of joint papers addressing availability (two). Would this comparison imply that availability has also gained more focus in academic-only papers than industry-oriented papers? The data that we have so far is not significant to make any strong statement to answer these questions. As previously mentioned, we do, however, want to highlight joint papers as more practical for industry. If we compare the amounts of academic and joint papers, we see that the number of joint papers is still low. We hope the number of joint papers will grow in the years to come with the current trend.
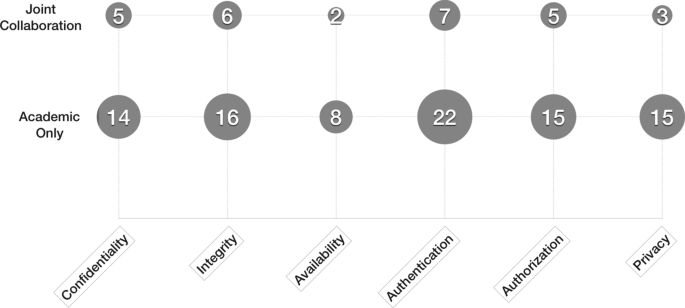
Difference between academic-only and joint papers in terms of security and privacy concerns
In terms of validation, implementation and execution testing, five (Portal et al. 2020 ; Karaarslan et al. 2020 ; Koshy et al. 2020 ; Attia et al. 2019 ; Pacheco et al. 2016 ) out of the nine domain-specific contributions do testing to verify their contribution in some form, while the generic domain contributions have 16 out of 24 papers doing testing, or some form of validation or analysis of a case. These numbers can be found in Table 4 representing “ Categorization of security pattern research ” section and “ IoT architecture ” section and by “testing”, we are referring to item C3 (research implementation/validation). We also see from this table that there are limited number of papers that discuss their purpose with their contribution. Four papers from the domain-specific category and 12 from the general domain category specified their purpose (item C1 ). However for describing their work with figures and diagrams we found 30 contributions (10 specific, 20 general) where in average the domain-specific studies have a higher ratio of including figures (item C2 ).
Table 4 also shows where the primary studies operate in the different layers of the IoT architecture presented in “ IoT architecture ” section. If we look at the numbers from the three-layer IoT architecture point of view, all three layers perception, network, and application have been almost completely covered by the different primary studies. However, the seven-layer IoT World Forum Reference Model of the IoT architecture can offer a closer view. We can see that the studies that explicitly address specific IoT application domains again have a higher average (4,33 layers per contribution) when it comes to layer coverage while general papers display a lower number (2,96 layers per contribution). In total, we see the coverage of 3,3 layers per contribution, which seems a little low considering there are seven layers in the architecture from the World Forum Reference Model (Juxtology 2018 ). In particular, we found that most of the primary studies do not work in all the layers, but rather operate in the Physical Devices and Controller ( L1 ), Connectivity ( L2 ), and Application ( L6 ) layers. There are four layers that have lower coverage in terms of the number of primary studies addressing IoT security challenges in those layers: Edge Computing ( L3 ), and especially, Data Accumulation ( L4 ), Data Abstraction ( L5 ), Collaboration and Processes ( L7 ).
Gaps and limitations (RQ3)
This section gives our answers to the RQ3.1 and RQ3.2 that are supported by the findings presented above. RQ3.1 — What are the current limitations of the IoT security patterns and architectures research? RQ3.2 — What research directions could be recommended for tackling the current limitations? Although there is a spike in the number of primary studies on IoT security patterns and architectures recently as presented in our answer for RQ1.1, our analyses show that IoT security patterns and architectures research is still in its beginning stages. This topic is yet to bloom, both in the industrial and academic universes. There are fundamental gaps and open issues to be handled.
The last decade was only the beginning of research efforts
One of the main limitations is that research on security patterns is still relatively “young” for IoT domain and premature, e.g., in terms of addressing all the different levels of IoT architecture reference model as presented in Table 4 , proper documentation and usage areas, as well as usage examples. Before conducting the review, we expected to see how existing security patterns being applied/adopted for IoT, and even more if new security patterns specific for IoT had emerged. But, based on the results of our review so far, we can say that the last decade has only marked the beginning of the research effort in this direction. The lack of evaluation in use cases or application in case studies as presented in our answer for RQ2.3 is one of the indicators of the premature work in most of the primary studies. Most of the contributions in the primary studies would only be ranked at the low levels (less than level five) in terms of the technology readiness levels (TRL). Footnote 19 We believe that (empirical) evaluations on the application of security patterns in IoT can make a substantial positive impact if more contributed to this research area. Empirical studies can provide more insights for any potential adopters of patterns to create more secure systems, or at least find a proven solution for a common problem.
Security patterns have proven to be very valuable for practitioners, especially non-security experts to adopt and build secure (IT) systems (Schumacher et al. 2013 ; Fernandez-Buglioni 2013 ). We would expect a similar impact of using security patterns in building secure IoT systems. Security patterns can help to mitigate the lack of knowledge from developers without security expertise, who are often under time-to-market pressure and as a result may contribute to more breaches and malicious usage, leading to more catastrophic incidents. Because, security patterns consist of domain-independent time-proven security knowledge, and expertise, they should be helpful, especially for addressing such limitations early in the development of IoT systems. We believe that security patterns can continue to be very valuable for practitioners, especially non-security experts, in building secure IoT systems. It would be even more so with a systematic understanding of different security patterns for addressing the heterogeneity of the IoT domain that our study could be a starting point for more comprehensive IoT domains. In other words, new research efforts could aim at building a catalog of security (and privacy) patterns more specifically and systematically for IoT.
The lack of addressing IoT-specific security and privacy challenges
Compatibility and complexity issues in IoT are other limitations that make security patterns and architectures less practical. An IoT system often makes use of multiple devices connected to a system(s) via a network(s). For example, one device could use a of protocols to communicate between nearby networks and other protocols to communicate with the service provider via IP. The heterogeneity of various communication protocols often used in IoT raises more security issues, which even get worse for complex IoT systems. So far, we have found patterns and architectures for mostly general issues and some specific issues that should work for their stated purposes. However, we have not encountered research that fulfills both types of issues that security patterns and architectures handle. In other words, we have not seen any approach that proposes a (systematic) top-down application of security patterns, first at the architectural level, then to more low-level details for addressing specific challenges in the heterogeneity of IoT, for example sometimes ad-hoc network, and weak links caused by tiny IoT devices.
From the results (see Table 2 ), we found that the quantity of security pattern approaches is less than the number of security architectures for IoT, and way too few compared to the initial numbers of the search results displayed in Fig. 2 . The quantity of existing papers that directly address security patterns for IoT is very low comparing to the explosion of the IoT as estimated by Gartner. Footnote 20 From the papers found, very few had characterized the patterns or architectures accordingly to the taxonomy categorization we constructed or characterized clearly in what layers of the IoT World Forum Reference Model Footnote 21 the contribution tackles (Fig. 8 ). We would, therefore, recommend that further research that should address thoroughly and systematically security pattern aspects for IoT systems.
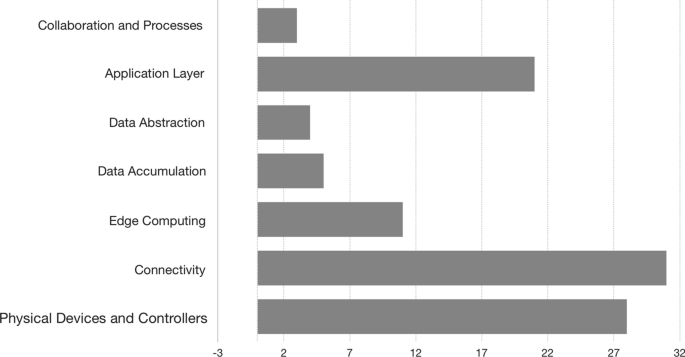
Contributions distributed over the seven layers (Juxtology 2018 )
The status of addressing the top ten most common vulnerabilities within IoT
We also accumulated how the research contributions in the primary studies handle the different issues presented by the OWASP IoT top ten vulnerabilities list (OWASP 2018 ) as shown in Table 5 . This extraction was done to highlight more of this topic’s gaps to see how the existing contributions handle the top ten most common vulnerabilities within IoT (OWASP 2018 ). As we see from the extraction, vulnerabilities such as Insecure Network Services (I2), Insecure Ecosystem Interfaces (I3), and Insecure Data Transfer and Storage (I7) are the most covered vulnerabilities by the contributions. This spread of coverage is fair in terms of what the contributions present. Most of the solutions found are either in the communication part of the system or when interacting with multiple devices/systems. Most of the contributions are also descriptions proposing high-level architectural solutions and not detailing actual (physical) IoT products or devices. The other types of vulnerabilities, such as Weak, Guessable, or Hardcoded Passwords (I1), Insecure Default Settings (I9), Lack of Physical Hardening (I10), and so forth were not visible in the contributions of the primary studies. I2, I3, and I7 are appropriate vulnerabilities that these contributions should mitigate, however Insufficient Privacy Protection (I6) and Lack of Device Management (I8) should be more highlighted due to its natural occurrence within security patterns and architectures.
The need for new security patterns specifically for IoT
Other directions we recommend is to keep up the research on existing patterns and architectures, but also find out new security patterns specifically for IoT. The dominance of academia-only and a few joint collaboration in IoT security pattern research (see our answer to RQ1.3) suggests that there should be even more collaboration between academia and industry. Especially since the IoT market is blossoming and making the industry more aware, there should be approaches that are more practical and closer to the needs in the industry. This research should be both of research nature but should also aim to create an interest for industry and business owners. This way, we can get more test cases, gain more knowledge, and spread awareness around IoT security patterns in general. However, the ultimate goal of promoting IoT security patterns is to make it easier to improve and implement security features early in the development of IoT systems.
Related work
There have been some recent surveys focusing on different aspects of IoT engineering, from the deployment support (Nguyen et al. 2019 ) to actuation conflict management (Lavirotte et al. 2020 ). In Nguyen et al. ( 2019 ), the authors present the state of the art of IoT deployment approaches in which most approaches do not properly support software deployment and orchestration at the tiny IoT device level. Besides, trustworthiness aspects including security were not addressed properly in the existing approaches for IoT systems deployment and orchestration. The new challenges in the IoT domain can also be seen in the physical layer of IoT actuators. The SMS in Lavirotte et al. ( 2020 ) brings attention to the risk of actuation effects to safety and trustworthiness, and analyzes approaches for actuation conflicts management. However, these two recent surveys do not focus on security patterns for IoT.
There exist some other surveys that have addressed IoT security and IoT patterns, but none has systematically, specifically investigated security pattern approaches for IoT. Oracevic et al. ( 2017 ) surveyed IoT security. They want to shed light on this topic and spread awareness, with examples of IoT security solutions. The authors provide different measures on different levels to secure the systems but do not go into details. They also do not offer any form of architectures or patterns to solve common recurring problems for IoT security. Nguyen et al. ( 2015 ) has also reviewed security patterns-based approaches for new systems design and development. However, the reviewed approaches are not specific for IoT systems, which the focus of this work.
Washizaki et al. ( 2020 ) present a collection of papers that either describe IoT architectures or design patterns, or both. They also classify the patterns that are being used in detail as well as in which paper. They present a security column and specify which papers from their study have patterns that cover security. We looked through these papers, but not all of the papers did meet our criteria described in “ Inclusion and exclusion criteria ” section. The papers from Washizaki et al. ( 2020 ) that we analyzed and included as primary studies are Pape and Rannenberg ( 2019 ), Pahl et al. ( 2018 ), Lee and Law ( 2017 )) and Ntuli and Abu-Mahfouz ( 2016 ).
Reinfurt et al. ( 2016 ) give details of IoT patterns by investigating a large number of production-ready IoT offerings to extract recurring proven solution principles into patterns. These patterns show and describe how to help other individuals to understand different aspects of IoT, and also make it easier.
Qanbari et al. ( 2016 ) elaborates on how to design, build, and engineer applications for IoT systems and have created patterns to do these steps in an IoT system. They do not highlight security as one of their focus points, which is our main concern for this paper.
In general, these studies’ results not only address the functional aspects of IoT patterns but also some quality aspects, such as security and development, that we even considered in our work. However, they were not systematically and explicitly conducted to analyze the patterns and architectures for IoT security similar to our work. Note that we have clearly defined the scope of our SLR, which only considered peer-reviewed publications, not white papers from the industry. Thus, our SLR reports state of the art in IoT security pattern research, not including the state of practice in the industry.
Threats to validity
We mainly found the primary studies of this work from the database search process. The search features provided by the five online publication databases are very different from each other. We had to adapt our search string to make use of the provided search features of the publication databases. We tried to use the keywords and built search strings that were not too strict to obtain as many relevant papers as possible. However, it would be impossible to have perfect search strings for the database search process.
There is a possibility that we missed some studies that should have been included in the final set of primary studies. We have tried to mitigate possible missing primary studies of the database search process by the manual search process. While doing snowballing, we saw again some primary studies that we already found from the database search process. Removing the duplicates, we managed to get six more new primary studies that have not been found from the database search process. There were some other relevant papers from snowballing, but they finally did not pass our selection criteria. These few studies may have fulfilled our criteria but may have failed to detail what they did or did not detail enough to include them according to our criteria confidently. We ended our search and selection process in the beginning of December 2020, which means that our review does not completely cover all the publications in 2020, but a major part of them.
The primary studies that passed our selection criteria could still have limitations that make their contributions unreliable or flawed. Because many of the contributions do not have test cases or examples, it can be hard to know if the patterns and architectures do what they are supposed to. It also creates uncertainty regarding how good the patterns preserve or contain the security in already existing systems. To mitigate this risk, we conducted cross-checks between at least two reviewers for some papers in doubt to remove any papers that do not have enough scientific contributions according to our selection criteria.
Conclusions
In this paper, we have presented our systematic review on patterns and architectures for IoT security. After systematically recognizing and reviewing 36 primary studies out of thousands of relevant papers in this domain, we have discovered that there is a slight rise in the number of publications addressing security patterns and architectures in the two recent years. However, our analysis has shown that security patterns are relatively “young” for the IoT domain and we have found more papers with main contributions categorized as architectures rather than patterns. This indicates that more efforts are needed in terms of formalization, proper documentation and adoption. We have not seen any approaches that combine architectural patterns or even IoT security reference architectures with other design patterns. Similarly, we have not seen architectural patterns or IoT security reference architectures referring to any design pattern they would be composed of. This includes patterns at the IoT “weak links”: the network and IoT devices levels. Most of the primary studies do not work in all the seven layers of the IoT World Forum Reference Model for IoT architecture. They mainly operate in the Physical Devices and Controller ( L1 ), Connectivity ( L2 ), and Application ( L6 ) layers. There are four layers that have little coverage in terms of patterns and architectures for addressing IoT security challenges: Edge Computing ( L3 ), Data Accumulation ( L4 ), Data Abstraction ( L5 ), Collaboration and Processes ( L7 ). We also accumulated how the research contributions in the primary studies handle the different issues presented by the OWASP IoT top ten vulnerabilities list.
New IoT systems development should concentrate more on tending to security, which can be improved with progressively relevant security patterns to apply and reuse. In other words, we need to promote the utilization of patterns for IoT security (and privacy) by design. To make security patterns for IoT approaches more viable, we consider the research collaboration between academia and industry is key in this domain. Security patterns in literature can be researched and applied in developing secure IoT systems with industrial context. Vice versa, experiences gained from securing industrial IoT systems can help to improve existing security patterns for IoT, or even new ones can emerge.
Availability of data and materials
All the data of our work is available in Google Drive https://drive.google.com/drive/folders/19CbTTYauf4ijpcSSlN0yySZLz8QIgscJ?usp=sharing .
https://www.idc.com/ .
NIS Directive, https://ec.europa.eu/digital-single-market/en/network-and-information-security-nis-directive .
A. Dasgupta, The Continuum: Big Data, Cloud & Internet of Things, IBM Internet of Things blog, 2017.
Gartner, The Death of IoT Security as You Know It, Gartner, 2017.
https://ieeexplore.ieee.org .
https://dlnext.acm.org .
https://sciencedirect.com/ .
http://apps.webofknowledge.com .
https://scopus.com .
https://www.springer.com .
https://iot-conference.org/iot2020/ .
https://hillside.net/conferences .
https://www.europlop.net/ .
https://conferences.computer.org/iciot/2019/ .
https://dl.acm.org/journal/tiot .
https://ieee-iotj.org/ .
Our search and selection process for the primary studies concluded in December 2020
Our search and selection process covers the period until December 2020.
The use of TRLs in the Horizon 2020 Work Programmes ( https://ec.europa.eu/info/funding-tenders/opportunities/portal/screen/support/faq/2890 ).
Gartner, November 2018 ( https://www.gartner.com/en/newsroom/press-releases/2018-11-07-gartner-identifies-top-10-strategic-iot-technologies-and-trends ).
Juxtology - IoT: Architecture ( https://www.m2mology.com/iot-transformation/iot-world-forum/ ).
Abbreviations
- Internet of Things
Alphand O, Amoretti M, Claeys T, Dall’Asta S, Duda A, Ferrari G, Rousseau F, Tourancheau B, Veltri L, Zanichelli F (2018) IoTChain: a blockchain security architecture for the Internet of Things, vol. 2018-April, pp 1–6. https://doi.org/10.1109/WCNC.2018.8377385
Attia O, Khoufi I, Laouiti A, Adjih C (2019) An IoT-blockchain architecture based on hyperledger framework for healthcare monitoring application. In: 2019 10th IFIP international conference on new technologies, mobility and security (NTMS), pp 1–5. https://doi.org/10.1109/NTMS.2019.8763849
Borgia E, Gomes DG, Lagesse B, Lea RJ, Puccinelli D (2016) Special issue on “internet of things: research challenges and solutions”. Comput Commun 89:1–4
Ciccozzi F, Crnkovic I, Di Ruscio D, Malavolta I, Pelliccione P, Spalazzese R (2017) Model-driven engineering for mission-critical iot systems. IEEE Softw 34(1):46–53
Article Google Scholar
Covington MJ, Carskadden R (2013) Threat implications of the internet of things. In: 2013 5th international conference on cyber conflict (CYCON 2013), pp 1–12
Create-IoT (2018) Deliverable D6.02—Recommendations for commonalities and interoperability profiles of IoT platforms. https://european-iot-pilots.eu/wp-content/uploads/2018/11/D06_02_WP06_H2020_CREATE-IoT_Final.pdf . Accessed 30 Sept 2021
Dhieb N, Ghazzai H, Besbes H, Massoud Y (2020) Scalable and secure architecture for distributed iot systems. In: 2020 IEEE technology engineering management conference (TEMSCON), pp 1–6. https://doi.org/10.1109/TEMSCON47658.2020.9140108
Dougherty C, Sayre K, Seacord RC, Svoboda D, Togashi K (2009) Secure design patterns. Technical report, Carnegie-Mellon Univ Pittsburgh PA Software Engineering Inst
Durresi M, Subashi A, Durresi A, Barolli L, Uchida K (2019) Secure communication architecture for internet of things using smartphones and multi-access edge computing in environment monitoring. J Ambient Intell Humaniz Comput 10(4):1631–1640. https://doi.org/10.1007/s12652-018-0759-6
Federal Trade Commission (1999) How to comply with the privacy of consumer financial information rule of the Gramm-Leach-Bliley Act. https://www.ftc.gov/tips-advice/business-center/guidance/how-comply-privacy-consumer-financial-information-rule-gramm . Accessed 29 Sept 2020
Fernandez-Buglioni E (2013) Security patterns in practice: designing secure architectures using software patterns. Wiley, Hoboken
Google Scholar
Ferry N, Brataas G, Rossini A, Chauvel F, Solberg A (2014) Towards bridging the gap between scalability and elasticity. CLOSER 10:0004975307460751
Fysarakis K, Spanoudakis G, Petroulakis N, Soultatos O, Broring A, Marktscheffel T (2019) Architectural patterns for secure iot orchestrations. In: 2019 Global IoT Summit (GIoTS), pp 1–6. https://doi.org/10.1109/GIOTS.2019.8766425
Gamma E, Helm R, Johnson R, Vlissides JM (1994) Design patterns: elements of reusable object-oriented software, 1st edn. Addison-Wesley Professional, Boston
MATH Google Scholar
Garcia-Morchon O, Keoh SL, Kumar S, Moreno-Sanchez P, Vidal-Meca F, Ziegeldorf JH (2013) Securing the ip-based internet of things with hip and dtls. In: Proceedings of the sixth ACM conference on security and privacy in wireless and mobile networks. WiSec ’13. Association for Computing Machinery, New York, NY, USA, pp 119–124. https://doi.org/10.1145/2462096.2462117
Goncalves F, Macedo J, Nicolau MJ, Santos A (2013) Security architecture for mobile e-health applications in medication control. In: 2013 21st international conference on software, telecommunications and computer networks—(SoftCOM 2013), pp 1–8. https://doi.org/10.1109/SoftCOM.2013.6671901
IEEE SA, S.A. (2018) IEEE draft standard for an architectural framework for the internet of things (IoT). IEEE P2413/D0.4.5, December 2018, pp 1–264
Jerald AV, Rabara SA, Arun Gnana Raj A (2019) Secured architecture for integrated iot enabled smart services. Int J Recent Technol Eng 8(3):7384–7393. https://doi.org/10.35940/ijrte.C6145.098319
Juxtology (2018) IoT: architecture. https://www.m2mology.com/iot-transformation/iot-world-forum/ . Accessed 27 July 2020
Karaarslan E, Karabacak E, Cetinkaya C (2020) Design and implementation of sdn-based secure architecture for iot-lab. In: Hemanth DJ, Kose U (eds) Artificial intelligence and applied mathematics in engineering problems. Springer, Cham, pp 877–885
Chapter Google Scholar
Karmakar KK, Varadharajan V, Nepal S, Tupakula U (2019) SDN enabled secure IoT architecture, pp 581–585. https://www.scopus.com/inward/record.uri?eid=2-s2.0-85066971444&partnerID=40&md5=c0f52e2ce49d38dad5d181190e28e795
Kitchenham BA, Charters S (2007) Guidelines for performing systematic literature reviews in software engineering. Technical Report EBSE 2007-001, Keele University and Durham University Joint Report . https://doi.org/10.1145/2372233.2372235
Kitchenham BA, Budgen D, Brereton OP (2011) Using mapping studies as the basis for further research—a participant-observer case study. Inf Softw Technol 53(6):638–651. https://doi.org/10.1016/j.infsof.2010.12.011 ( Special Section: Best papers from the APSEC )
Koo J, Oh SR, Lee SH, Kim YG (2020) Security architecture for cloud-based command and control system in iot environment. Appl Sci 10:1035. https://doi.org/10.3390/app10031035
Koshy P, Babu S, Manoj BS (2020) Sliding window blockchain architecture for internet of things. IEEE Internet Things J 7(4):3338–3348. https://doi.org/10.1109/JIOT.2020.2967119
Kuhn DR, Hu VC, Polk WT, Chang S-J (2001) NIST SP 800-32, introduction to public key technology and the federal PKI infrastructure. National Institute of Standards & Technology, p 54. https://doi.org/10.6028/NIST.SP.800-32
Lavirotte S, Rocher G, Tigli J, Gonnin T (2020) IoT-based systems actuation conflicts management towards DevOps: a systematic mapping study. In: Proceedings of the 5th international conference on internet of things, big data and security, vol 1. IoTBDS, pp 227–234. SciTePress. https://doi.org/10.5220/0009355102270234 . INSTICC
Lee W, Law P (2017) A case study in applying security design patterns for iot software system. In: 2017 international conference on applied system innovation (ICASI), pp 1162–1165. https://doi.org/10.1109/ICASI.2017.7988402
Lessa dos Santos G, Guimaraes VT, da Cunha Rodrigues G, Granville LZ, Tarouco LMR (2015) A dtls-based security architecture for the internet of things. In: 2015 IEEE symposium on computers and communication (ISCC), pp 809–815. https://doi.org/10.1109/ISCC.2015.7405613
Nguyen PH, Yskout K, Heyman T, Klein J, Scandariato R, Le Traon Y (2015) Sospa: a system of security design patterns for systematically engineering secure systems. In: 2015 ACM/IEEE 18th international conference on model driven engineering languages and systems (MODELS), pp 246–255. https://doi.org/10.1109/MODELS.2015.7338255
Nguyen PH, Kramer M, Klein J, Traon YL (2015) An extensive systematic review on the model-driven development of secure systems. Inf Softw Technol 68:62–81. https://doi.org/10.1016/j.infsof.2015.08.006
Nguyen PH, Ali S, Yue T (2017) Model-based security engineering for cyber-physical systems: a systematic mapping study. Inf Softw Technol 83:116–135. https://doi.org/10.1016/j.infsof.2016.11.004
Nguyen P, Ferry N, Erdogan G, Song H, Lavirotte S, Tigli J, Solberg A (2019) Advances in deployment and orchestration approaches for IoT—a systematic review. In: 2019 IEEE international congress on Internet of Things (ICIOT), pp 53–60. https://doi.org/10.1109/ICIOT.2019.00021
Ntuli N, Abu-Mahfouz A (2016) A simple security architecture for smart water management system. Procedia Comput Sci 83:1164–1169. https://doi.org/10.1016/j.procs.2016.04.239 . The 7th international conference on ambient systems, networks and technologies (ANT 2016)/The 6th international conference on sustainable energy information technology (SEIT-2016)/Affiliated workshops
Office for Civil Rights (2013) Summary of the HIPAA security rule. https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html . Accessed 29 Sept 2020
Oracevic A, Dilek S, Ozdemir S (2017) Security in internet of things: a survey. In: 2017 international symposium on networks, computers and communications (ISNCC), pp 1–6 . https://doi.org/10.1109/ISNCC.2017.8072001
OWASP (2018) Internet of Things (IoT) Top 10 2018. https://owasp.org/www-pdf-archive/OWASP-IoT-Top-10-2018-final.pdf . Accessed 30 Sept 2020
Pacheco J, Ibarra D, Vijay A, Hariri S (2018) IoT security framework for smart water system. In: 2017 IEEE/ACS 14th international conference on computer systems and applications (AICCSA), vol 2017-October, pp 1285–1292. https://doi.org/10.1109/AICCSA.2017.85
Pacheco J, Satam S, Hariri S, Grijalva C, Berkenbrock H (2016) IoT security development framework for building trustworthy smart car services, pp 237–242. https://doi.org/10.1109/ISI.2016.7745481
Pacheco J, Tunc C, Hariri S (2019) Security framework for IoT cloud services, vol 2018-November . https://doi.org/10.1109/AICCSA.2018.8612808
Pahl C, Ioini NE, Helmer S, Lee B (2018) An architecture pattern for trusted orchestration in iot edge clouds. In: 2018 third international conference on fog and mobile edge computing (FMEC), pp 63–70. https://doi.org/10.1109/FMEC.2018.8364046
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes. In: Stern J (ed) Advances in cryptology—EUROCRYPT ’99. Springer, Berlin, Heidelberg, pp 223–238
Pape S, Rannenberg K (2019) Applying privacy patterns to the internet of things’ (iot) architecture. Mobile Netw Appl 24(3):925–933. https://doi.org/10.1007/s11036-018-1148-2
Park C (2020) Security architecture for secure multicast coap applications. IEEE Internet Things J 7(4):3441–3452. https://doi.org/10.1109/JIOT.2020.2970175
Perera C, Barhamgi M, Bandara AK, Ajmal M, Price B, Nuseibeh B (2020) Designing privacy-aware internet of things applications. Inf Sci 512:238–257. https://doi.org/10.1016/j.ins.2019.09.061
Petersen K, Vakkalanka S, Kuzniarz L (2015) Guidelines for conducting systematic mapping studies in software engineering: an update. Inf Softw Technol 64:1–18
Petroulakis NE, Lakka E, Sakic E, Kulkarni V, Fysarakis K, Somarakis I, Serra J, Sanabria-Russo L, Pau D, Falchetto M, Presenza D, Marktscheffel T, Ramantas K, Mekikis P, Ciechomski L, Waledzik K (2019) Semiotics architectural framework: End-to-end security, connectivity and interoperability for industrial iot. In: 2019 Global IoT Summit (GIoTS), pp 1–6. https://doi.org/10.1109/GIOTS.2019.8766399
Porambage P, Ylianttila M, Schmitt C, Kumar P, Gurtov A, Vasilakos AV (2016) The quest for privacy in the internet of things. IEEE Cloud Comput 3(2):36–45
Portal G, de Matos E, Hessel F (2020) An edge decentralized security architecture for industrial iot applications. In: 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), pp 1–6. https://doi.org/10.1109/WF-IoT48130.2020.9221176
Qanbari S, Pezeshki S, Raisi R, Mahdizadeh S, Rahimzadeh R, Behinaein N, Mahmoudi F, Ayoubzadeh S, Fazlali P, Roshani K, Yaghini A, Amiri M, Farivarmoheb A, Zamani A, Dustdar S (2016) IoT design patterns: computational constructs to design, build and engineer edge applications. In: 2016 IEEE first international conference on Internet-of-Things design and implementation (IoTDI), pp 277–282. https://doi.org/10.1109/IoTDI.2015.18
Rajmohan T, Nguyen PH, Ferry N (2020) Research landscape of patterns and architectures for iot security: a systematic review. In: 2020 46th Euromicro conference on software engineering and advanced applications (SEAA), pp 463–470. https://doi.org/10.1109/SEAA51224.2020.00079
Reinfurt L, Breitenbücher U, Falkenthal M, Leymann F, Riegg A (2016) Internet of things patterns. In: Proceedings of the 21st European conference on pattern languages of programs. EuroPlop ’16. ACM, New York, NY, USA. https://doi.org/10.1145/3011784.3011789
Richa E (2021) Iot: security issues and challenges. In: Senjyu T, Mahalle PN, Perumal T, Joshi A (eds) Information and communication technology for intelligent systems. Springer, Singapore, pp 87–96
Robles Enciso A, Zarca A, Garcia Carrillo D, Hernandez-Ramos J, Bernal Bernabe J, Skarmeta A, Matheu Garcia SN (2020) Security architecture for defining and enforcing security profiles in dlt/sdn-based iot systems. Sensors 20:1882. https://doi.org/10.3390/s20071882
Roman R, Najera P, Lopez J (2011) Securing the internet of things. Computer 44(9):51–58
Ross R, McEvilley M, Oren J (2016) NIST SP 800-160, systems security engineering considerations for a multidisciplinary approach in the engineering of trustworthy secure systems. National Institute of Standards & Technology, p 243. https://doi.org/10.6028/NIST.SP.800-160v1
Schmidt DC, Buschmann F (2003) Patterns, frameworks, and middleware: their synergistic relationships. In: 25th international conference on software engineering, 2003. Proceedings, pp 694–704
Schneier B (2017) Iot security: what’s plan b? IEEE Secur Privacy 15(05):96. https://doi.org/10.1109/MSP.2017.3681066
Schumacher M, Fernandez-Buglioni E, Hybertson D, Buschmann F, Sommerlad P (2013) Security patterns: integrating security and systems engineering. Wiley, Hoboken
Schuß M, Iber J, Dobaj J, Kreiner C, Boano CA, Römer K (2018) Iot device security the hard(ware) way. In: Proceedings of the 23rd European conference on pattern languages of programs. EuroPLoP ’18. ACM, New York, NY, USA, pp 20–1204. https://doi.org/10.1145/3282308.3282329
Steel C, Nagappan R (2006) Core security patterns: best practices and strategies for J2EE”, web services, and identity management. Pearson Education, London
Syed MH, Fernandez EB, Moreno J (2018) A misuse pattern for ddos in the iot. In: Proceedings of the 23rd European conference on pattern languages of programs. EuroPLoP ’18. ACM, New York, NY, USA, pp 34–1345. https://doi.org/10.1145/3282308.3282343
Tiburski RT, Moratelli CR, Johann SF, Neves MV, Matos ED, Amaral LA, Hessel F (2019) Lightweight security architecture based on embedded virtualization and trust mechanisms for iot edge devices. IEEE Commun Mag 57(2):67–73. https://doi.org/10.1109/MCOM.2018.1701047
Tran NK, Sheng QZ, Babar MA, Yao L (2017) Searching the web of things: state of the art, challenges, and solutions. ACM Comput Surv (CSUR) 50(4):55
Ur-Rehman O, Zivic N (2015) Secure design patterns for security in smart metering systems. In: 2015 IEEE European modelling symposium (EMS), pp 278–283. https://doi.org/10.1109/EMS.2015.49
Vijayakumaran C, Senthil M, Manickavasagam B (2020) A reliable next generation cyber security architecture for industrial internet of things environment. Int J Electr Comput Eng: IJECE 10:387. https://doi.org/10.11591/ijece.v10i1.pp387-395
Vithya Vijayalakshmi A, Arockiam L (2020) A secured architecture for iot healthcare system. In: Pandian AP, Senjyu T, Islam SMS, Wang H (eds) Proceeding of the international conference on computer networks, big data and IoT (ICCBI-2018). Springer, Cham, pp 904–911
Vučinić M, Tourancheau B, Rousseau F, Duda A, Damon L, Guizzetti R (2015) Oscar: object security architecture for the internet of things. Ad Hoc Netw 32:3–16. https://doi.org/10.1016/j.adhoc.2014.12.005 ( Internet of Things security and privacy: design methods and optimization )
Washizaki H, Ogata S, Hazeyama A, Okubo T, Fernandez EB, Yoshioka N (2020) Landscape of architecture and design patterns for iot systems. In: IEEE Internet of Things Journal 2020 (early Access), p 1. https://doi.org/10.1109/JIOT.2020.3003528
Washizaki H, Xia T, Kamata N, Fukazawa Y, Kanuka H, Yamaoto D, Yoshino M, Okubo T, Ogata S, Kaiya H, Kato T, Hazeyama A, Tanaka T, Yoshioka N, Priyalakshmi G (2018) Taxonomy and literature survey of security pattern research. In: 2018 IEEE conference on application, information and network security (AINS), pp 87–92. https://doi.org/10.1109/AINS.2018.8631465
Williams-Grut O (2018) Hackers once stole a casino’s high-roller database through a thermometer in the lobby fish tank. https://www.businessinsider.com/hackers-stole-a-casinos-database-through-a-thermometer-in-the-lobby-fish-tank-2018-4?r=US&IR=T . Accessed 20 Aug 2020
Witti M, Konstantas D (2018) A secure and privacy-preserving internet of things framework for smart city. In: Proceedings of the 6th international conference on information technology: IoT and smart city. ICIT 2018. Association for Computing Machinery, New York, NY, USA, pp 145–150. https://doi.org/10.1145/3301551.3301607
Wohlin C (2014) Guidelines for snowballing in systematic literature studies and a replication in software engineering. In: Proceedings of the 18th international conference on evaluation and assessment in software engineering. ACM, p 38
Wright M (2020) Default passwords banned for smart devices as part of hacking crackdown. https://www.telegraph.co.uk/news/2020/01/27/default-passwords-banned-smart-devices-part-hacking-crackdown/ . Accessed 20 June 2020
Yampolskiy M, Horvath P, Koutsoukos XD, Xue Y, Sztipanovits J (2013) Taxonomy for description of cross-domain attacks on cps. In: Proceedings of the 2nd ACM international conference on high confidence networked systems. HiCoNS ’13. Association for Computing Machinery, New York, NY, USA, pp 135–142. https://doi.org/10.1145/2461446.2461465
Ye F, Qian Y (2017) A security architecture for networked Internet of Things devices, vol 2018-January, pp 1–6. https://doi.org/10.1109/GLOCOM.2017.8254021
Yskout K, Heyman T, Scandariato R, Joosen W (2006) A system of security patterns. CW Reports. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.142.4538
Zhang J, Jin H, Gong L, Cao J, Gu Z (2019) Overview of IoT security architecture, pp 338–345. https://doi.org/10.1109/DSC.2019.00058
Zhu X, Badr Y (2018) Fog computing security architecture for the internet of things using blockchain-based social networks. In: 2018 IEEE international conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), pp 1361–1366
Download references
Acknowledgements
The research leading to these results has partially received funding from the European Commission's H2020 Programme under the grant agreement numbers 958363 (Dat4.ZERO), and 958357 (InterQ).
Author information
Authors and affiliations.
Capgemini, Oslo, Norway
Tanusan Rajmohan
SINTEF, Oslo, Norway
Phu H. Nguyen
Université Côte d’Azur, I3S/INRIA Kairos, Sophia Antipolis, France
Nicolas Ferry
You can also search for this author in PubMed Google Scholar
Contributions
All authors contributed to all the steps of conducting this work and writing this manuscript. All the authors read and approved the final manuscript.
Corresponding author
Correspondence to Phu H. Nguyen .
Ethics declarations
Ethics approval and consent to participate.
Not applicable.
Consent for publication
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.

Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Rajmohan, T., Nguyen, P.H. & Ferry, N. A decade of research on patterns and architectures for IoT security. Cybersecurity 5 , 2 (2022). https://doi.org/10.1186/s42400-021-00104-7
Download citation
Received : 30 April 2021
Accepted : 17 November 2021
Published : 05 January 2022
DOI : https://doi.org/10.1186/s42400-021-00104-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Architecture
- How It Works
- PhD thesis writing
- Master thesis writing
- Bachelor thesis writing
- Dissertation writing service
- Dissertation abstract writing
- Thesis proposal writing
- Thesis editing service
- Thesis proofreading service
- Thesis formatting service
- Coursework writing service
- Research paper writing service
- Architecture thesis writing
- Computer science thesis writing
- Engineering thesis writing
- History thesis writing
- MBA thesis writing
- Nursing dissertation writing
- Psychology dissertation writing
- Sociology thesis writing
- Statistics dissertation writing
- Buy dissertation online
- Write my dissertation
- Cheap thesis
- Cheap dissertation
- Custom dissertation
- Dissertation help
- Pay for thesis
- Pay for dissertation
- Senior thesis
- Write my thesis
128 High Quality Cybersecurity Research Topics Ideas List

The internet is a global village full of different people. Some people have malicious motives. Once they stumble upon your sensitive data, they will use it to harass you. This also occurs in social media accounts. You may post something and then get some bad or hurtful comments.
That’s a form of cyberbullying that is not acceptable. Therefore, you need to be careful when dealing with people on the internet. Also, try to reduce the data that you expose on your different user profiles. A person may even steal your online identity in a blink of an eye.
Case Situations To Write Cybersecurity Research Paper
Thereby cybersecurity comes in with the motive of defending computers, servers, mobiles, electronic systems, networks, and much more from those malicious attacks. You may need to write a cybersecurity research paper for:
Your final paper, project, thesis, or dissertation. When you are proposing a new strategy to use in your company to prevent cyber-attacks. When you want to bring into light some vulnerabilities being ignored. When you want to do more research and get a better understanding of harassment on the internet.
How To Write Cybersecurity Research Paper
This is the procedure you can use when writing a research paper.
Consult your professor – You will first need to get insights from your professor or teacher on the best way to go about it. You can provide a list of topics you may want to write on for his approval. Brainstorm – Discuss with some like-minded people the best cybersecurity topics to try. You need to be careful to ensure that you choose a topic that you can easily do. Research – Once you settle on a good topic, you can start your research on books, scholarly articles, documentaries, and films to get legit information on your cybersecurity research topic. Jot them down as a draft. Start your paper – Once you are settled with the research, you can use your draft to write a viable research paper. Ensure you follow the right procedure. Proofread the work – Once you are satisfied with your work, consider proofreading it before submitting it.
If you don’t feel like writing research paper yourself, you can get cheap dissertation help from our experts.
Cybersecurity Research Topics
When in high school or college, you need to strive to get good grades. You can use any of these cybersecurity research topics for your paper. Just ensure to do enough research on the concepts.
- The significance of a firewall in the protection of the network.
- Discuss the process of authentication.
- The loss and restoration of data.
- The best data encryption algorithms.
- The best methods to protect your network.
- Evaluate digital piracy and security.
- The significance of social engineering.
- The significance of software updates in devices.
- The major causes of cybersecurity.
- The safety of biometrics.
- The worst cases of IoT hacking.
Cybersecurity Research Paper Topics
Cybersecurity is wide and inexhaustible. Each day, cybercrime are occurring, leading to research on better ways to protect ourselves online. You can use any of these topics for your research paper or project.
- The advantages and disadvantages of unified user profiles.
- The relation between bots and cybersecurity.
- The major cybersecurity vulnerabilities.
- Evaluate digital piracy and its effects on creativity.
- How has automotive hacking grown over the years?
- Evaluate ethical hacking.
- Evolution of phishing over time.
- The best antivirus software currently being used.
- The trends in cybersecurity technology.
- How biometrics is helping in cybersecurity?
- The occurrence of cybersecurity in spoofing.
Cybersecurity Research Topics For Research Papers
Are you in the IT profession? Have you done your project yet? Then you can consider using any of these cybersecurity research topics. They are all ideal and based on current matters.
- The rise of identity theft on the internet.
- Why are more people getting into computer forensics?
- The major threats found using digital forensic techniques.
- The best VPNs in the world that will hide your IP on the internet.
- The disadvantages of exposure of your IP address to the public.
- The major A.I. security systems.
- The centralization of data storage.
- How to identify malicious activity on your devices.
- The safety of a network.
- The applications of network segmentation.
- The major challenges in IT risk management.
PhD Research Topics In Cybersecurity
Are you currently doing your Ph.D.? You can use any of these cybersecurity topics for your paper. They are all based on current matters. There are available resources that you can use to get data.
- The best approach for connected autonomous vehicles.
- The best methods for cognitive cybersecurity.
- The most innovative methods being used to determine the viability of deep learning based on the cybersecurity log analytics system.
- The significance of not sharing sensitive data on social media networks.
- Evaluate cookies on privacy.
- The different types of hackers.
- The disadvantages of Wi-Fi hacking apps on mobile phones.
- The major cyber-attack concepts.
- The best way to develop credible internet security software.
- How to scan malware on your pc.
- Evaluate twitter’s access control policy.
Research Topics In Cybersecurity
You can use any of these research topics in cybersecurity for your papers. You can derive data from some other scholarly articles, documentaries, films, and books. Information about cybersecurity gets updated daily.
- The attack of ransomware.
- The effects of RSA on any network’s security.
- The significance of cloud security.
- How do data leaks occur on mobile apps?
- The effects of a black hole on a network system.
- The significance of applications logging.
- How to detect malicious activities on Google Play apps.
- The best way to check security protocols.
- How does network security deal with cybercrime?
- The network security monitoring process.
- The dangers and flaws of the internet.
Best Research Topics In Cybersecurity
How confident are you about your knowledge of cybersecurity? Then you can consider using any of these topics to test your knowledge capacity. Give it your best to get top grades.
- Initiatives that can be taken to check the growth of cyber hackers.
- The difference between white and black hat hackers.
- How does network intrusion occur and its prevention?
- The authentication processes.
- The most common vulnerabilities.
- The different types of cybercrime.
- The major pandemics caused by cyber viruses.
- The significance of software updates and patches.
- The common laws against cybercrime in the world.
- The best way to suppress the ransomware attack rate.
- The significance of a keylogger.
Hot Topics Cybersecurity Research
These are some of the hottest topics in cybersecurity. You just need to find an ideal topic, do research, jot down the points, and start your research paper.
- The best way to ensure you are safe when downloading files on the internet.
- The best device synchronization and protection methods.
- How can you detect bots on the internet?
- The relation between internet cookies with cybersecurity.
- How are IOS-based apps less prone to ransomware attacks?
- Is it possible for computer hardware to face a cyber-attack?
- The algorithms of data encryption.
- The significance of investing in a strong anti-malware.
- How do encrypting viruses work?
- How do the reverse engineering and vulnerabilities analysis work?
Great Topics For Cybersecurity Research Papers
There are a lot of vulnerabilities on the internet. These great topics for cybersecurity can make you more knowledgeable about the current trends.
- Risk management in computing.
- The most common causes of a data breach in the 21 st
- The best way to protect your device and synchronize the data.
- The significance of computer forensics in the current digital era.
- The major implications of ethical hacking.
- The motivations behind cybercrimes like identity theft.
- The major components of IT and data governance.
- The most secure user authentication methods.
- The threats of digital piracy.
- The significance of device synchronization.
Cybersecurity And Law Research Topics
Did you know that certain laws govern cybersecurity? Then you can use these cybersecurity and law research topics to get a deeper understanding.
- Data and cybersecurity in IoT.
- The correlation between big data analysis with IoT.
- Evaluate Software Defined Network.
- The best tools for excellent email security.
- How to prevent cybercrimes.
- How do phishing scams occur?
- The significance of using strong passwords.
- The worst data breaches of all time.
- How do malicious people use other people’s identities to their benefit?
- How to remove malware from a computer.
Research Topics On Cybersecurity
There are different internet vulnerabilities in the world. Thereby, you can use these research topics on cybersecurity to understand how your security can be compromised on the internet.
- Evaluate botnets in the current world.
- Evaluate a brute force attack.
- The risks of connecting your device to a public wireless network.
- How to secure removable media.
- The occurrence of credit card fraud.
- The most recent cloud security threats.
- The significance of implementing multifactor authentication.
- How is online slandering a cybercrime?
- Email sender spoofing process.
- Stress is caused by periodic cyberbullying.
Cybersecurity Research Topic
Have you ever faced any cyber-attack? How was the experience? These are great topics that can help you become more knowledgeable.
- How to protect yourself from cyberbullying.
- The best security measures to input on Windows, macOS, and Linux.
- How dangerous is cyberstalking?
- Can cyber harassment be termed a crime?
- The major dangers of public Wi-Fi networks.
- Is it possible to identify a phishing attack?
- The best mobile protection methods on your smartphone.
- Malware and how it occurs.
- The best practices to secure your Home Wi-Fi.
- The advantages and disadvantages of antivirus software.
Topic On Cybersecurity
As a student, you need to up your game, to ensure you provide custom work that your teacher or professor will be happy about. Just try any of these topics on cybersecurity.
- The endpoint attacks on devices.
- The dangers posed by tracking cookies.
- The role of backups on your device’s data.
- Evaluate security patches.
- Is it important to read the software terms and conditions?
- Are there any malicious apps on the Google Play Store and Apple Store?
- Evaluate SQL injection attacks.
- The best way to keep your personal information safe.
- The vulnerabilities found in multifactor authentication.
- How to protect your computer.
- How to authenticate on your devices.
Paper Writing Assistance In Cybersecurity Research Paper
Are you busy and wondering how you will do your research paper, project, or thesis? Look no further, you can pay for dissertation and be sure to get perfect result. You just need to order by choosing a topic of your preference and buy it at a cheap price.
You don’t have to worry about not meeting the deadline. With us, you will be sorted. All the best in your research paper.

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Comment * Error message
Name * Error message
Email * Error message
Save my name, email, and website in this browser for the next time I comment.
As Putin continues killing civilians, bombing kindergartens, and threatening WWIII, Ukraine fights for the world's peaceful future.
Ukraine Live Updates
Articles on Internet security
Displaying 1 - 20 of 37 articles.

Five things South Africa must do to combat cybercrime
Basie von Solms , University of Johannesburg

RMIT attack underlines need to train all uni staff in cyber safety
Abu Barkat ullah , University of Canberra and Mohiuddin Ahmed , Edith Cowan University

Cyberattacks are on the rise amid work from home – how to protect your business
Michael Parent , Simon Fraser University

Can I still be hacked with 2FA enabled?
David Tuffley , Griffith University

Trump’s attempts to ban TikTok and other Chinese tech undermine global democracy
Philip Mai , Toronto Metropolitan University

Quantum internet: the next global network is already being laid
Harun Šiljak , Trinity College Dublin

Data lakes: where big businesses dump their excess data, and hackers have a field day
Mohiuddin Ahmed , Edith Cowan University

Is your VPN secure?
Mohammad Taha Khan , University of Illinois Chicago and Narseo Vallina-Rodriguez , University of California, Berkeley

The quiet threat inside ‘internet of things’ devices
Charles T. Harry , University of Maryland

30 years ago, the world’s first cyberattack set the stage for modern cybersecurity challenges
Scott Shackelford , Indiana University

Explainer: how internet routers work and why you should keep them secure
Nicholas Patterson , Deakin University
Happy 10th birthday iPhone, the nearest thing to a secure pocket computer
Keith Martin , Royal Holloway University of London and Kenny Paterson , Royal Holloway University of London

Could your kettle bring down the internet?
Ansgar Koene , University of Nottingham and Derek McAuley , University of Nottingham

By attacking DNS, hackers can bring down many websites for the price of one
Rob Miles , University of Hull

Is someone watching you online? The security risks of the Internet of Things
Patryk Szewczyk , Edith Cowan University and Nikolai Hampton , Edith Cowan University

Four things you should be doing to protect yourself from cyberattack
Robert Potter , The University of Queensland

Australia could become a leader in cybersecurity research
Alex Zelinsky , Defence Science and Technology Organisation ; Andrew Goldsmith , Flinders University ; Craig Valli , Edith Cowan University ; Jodi Steel , Data61 ; Liz Sonenberg , The University of Melbourne ; Sven Rogge , UNSW Sydney , and Vijay Varadharajan , Macquarie University

Seven easy steps to keep viruses from your devices
Mary Adedayo , University of Pretoria

Doxxing, swatting and the new trends in online harassment
Andrew Quodling , Queensland University of Technology

Roar of China’s ‘Great Cannon’ heard across the internet
Tim Stevens , King's College London
Related Topics
- Cyberattacks
- Cybersecurity
- Internet of Things
- Online privacy
- Online security
- Surveillance
Top contributors
Senior Lecturer in Networking, The Open University
Senior Lecturer in Applied Ethics & CyberSecurity, Griffith University
Senior Lecturer of Computing and Security, Edith Cowan University
Senior Lecturer in Sociology, University of Tasmania
Honorary Lecturer in Sociology, Australian National University
Professor of Digital Economy, University of Nottingham
Professor of Physics, UNSW Sydney
Professor of Cybersecurity, School of Computer Science and Informatics, De Montfort University
Director of ECU Security Research Institute, Edith Cowan University
Professor, Dalhousie University
Professor, Information Security Group, Royal Holloway University of London
Matthew Flinders Distinguished Emeritus Professor, Flinders University
Doctoral researcher investigating governance of social media platforms, Queensland University of Technology
Associate Professor – Information & Communication Technology (ICT), CQUniversity Australia
Reader in International Security Security, King's College London
- X (Twitter)
- Unfollow topic Follow topic
A List of 181 Hot Cyber Security Topics for Research [2024]
Your computer stores your memories, contacts, and study-related materials. It’s probably one of your most valuable items. But how often do you think about its safety?
Our specialists will write a custom essay specially for you!
Cyber security is something that can help you with this. Simply put, it prevents digital attacks so that no one can access your data. Do you want to write a research paper related to the modern challenges of cyberspace? This article has all you need. In here, you’ll find:
- An overview of cyber security’s research areas.
- A selection of compelling cyber security research topics.
And don’t hesitate to contact our custom writing team in case you need any assistance!
- 🔝 Top 10 Topics
- ✅ Research Areas
- ⭐ Top 10 Cybersecurity Topics
- 🔒 Technology Security Topics
- 🖥️ Cybercrime Topics
- ⚖️ Cyber Law & Ethics Topics
🔍 References
🔝 top 10 cyber security topics.
- How does malware work?
- The principle of zero trust access
- 3 phases of application security
- Should removable media be encrypted?
- The importance of network security
- The importance of end-user education
- Cloud security posture management
- Do biometrics ensure security of IPhones?
- Can strong passwords protect information?
- Is security in critical infrastructure important?
✅ Cyber Security Topics & Research Areas
Cyber security is a vast, constantly evolving field. Its research takes place in many areas. Among them are:

- Safe quantum and space communications . Progress in quantum technologies and space travel calls for extra layers of protection.
- Data privacy. If someone’s personal information falls into the wrong hands, the consequences can be dire. That’s why research in this area focuses on encryption techniques.
- (Inter)national cyberethics, criminology, and law. This branch analyzes how international legal frameworks work online.
- AI and IoT security . We spend more and more of our daily lives online. Additionally, our reliance on AI increases. This scientific field strives to ensure a safe continuation of this path.
As you can see, cyber security extends in various exciting directions that you can explore. Naturally, every paper needs a cover page. We know that it’s one of the more annoying parts, so it’s not a bad thing to use a title page generator for your research paper . Now, let’s move on to our cyber topics list.
⭐ Top 10 Cybersecurity Topics 2024
- Is removable media a threat?
- Blockchain security vulnerabilities
- Why should you avoid public Wi-Fi?
- How to prevent phishing attacks
- Physical security measures in banks
- Security breaches of remote working
- How does two-factor authentication work?
- How to prevent social engineering attacks
- Cybersecurity standards for automotive
- Privacy settings of social media accounts
🔒 Computer Security Topics to Research
Safe computer and network usage is crucial. It concerns not only business but also individuals. Security programs and systems ensure this protection. Explore them with one of our topics:
Just in 1 hour! We will write you a plagiarism-free paper in hardly more than 1 hour
- How do companies avoid sending out confidential information ? Sending an email to the wrong person has happened to the best of us. But what happens if the message’s contents were classified? For your paper, you can find out what technologies can prevent such slip-ups.
- What are the best ways to detect malicious activity ? Any organization’s website gets plenty of daily traffic. People log in, browse, and interact with each other. Among all of them, it might be easy for an intruder to slip in.
- Internet censorship: classified information leaks . China takes internet censorship to the next level. Its comprehensive protection policies gave the system the nickname Great Firewall of China . Discuss this technology in your essay.
- Encrypted viruses as the plague of the century . Antivirus programs are installed on almost every computer. They prevent malicious code from tampering with your data. In your paper, you can conduct a comparison of several such programs.
- What are the pros and cons of various cryptographic methods? Data privacy is becoming more and more critical. That’s why leading messaging services frequently advertise with their encryption technologies .
- What makes blockchain secure ? This technique allows anonymity and decentralization when working with cryptocurrencies . How does it work? What risks are associated with it?
- What are the advantages of SIEM ? Security Incident and Event Management helps organizations detect and handle security threats. Your essay can focus on its relevance for businesses.
- What are the signs of phishing attempts?
- Discuss unified cyber security standards in healthcare .
- Compare and contrast various forms of data extraction techniques.
- What do computers need protocols for?
- Debate the significance of frequent system updates for data security .
- What methods does HTTPS use that make it more secure than HTTP?
- The role of prime numbers in cryptography .
- What are public key certificates , and why are they useful?
- What does a VPN do?
- Are wireless internet connections less secure than LAN ones? If so, why?
- How do authentication processes work?
- What can you do with IP addresses?
- Explain the technology of unlocking your phone via facial recognition vs. your fingerprint.
- How do you prevent intrusion attempts in networks ?
- What makes Telnet vulnerable?
- What are the phases of a Trojan horse attack?
- Compare the encryption technologies of various social networks.
- Asymmetric vs. symmetric algorithms.
- How can a person reach maximum security in the computer networking world ?
- Discuss autoencoders and reveal how they work.
💾 Information Security Topics to Research
Information security’s goal is to protect the transmission and storage of data. On top of that, network security topics are at the forefront of infosec research. If you’re looking for inspiration on the subject, check out these ideas.
- What are the mechanics of password protection ? Passwords are a simple tool to ensure confidentiality. What do users and developers need to keep in mind when handling passwords?
- What are the safest ways to ensure data integrity ? Everybody wants their data to be intact. Accidental or malicious modifications of data can have dire consequences for organizations and individuals. Explore ways to avoid it.
- How can one establish non-repudiation? Non-repudiation proves the validity of your data. It’s essential in legal cases and cyber security .
- How did the advent of these new technologies impact information security ? Mobile networks have changed the way we access information. On a smartphone , everything is permanently available at your fingertips. What adverse consequences did these technologies bring?
- How do big corporations ensure that their database environment stays conflict-free? We expect our computers to always run fast and without errors. For institutions such as hospitals, a smooth workflow is vital. Discuss how it can be achieved.
- Describe solid access control methods for organizations. In a company, employees need access to different things. This means that not everyone should have an admin account. How should we control access to information ?
- Medical device cyber security. For maximum safety, it’s best to employ several measures. Protection on the hard- and software side is just a part of it. What are some other means of security?
- Write an argumentative essay on why a career in information security doesn’t require a degree.
- Pros and cons of various infosec certificates.
- Cybersecurity in cruise ship industry
- The influence of remote work on a businesses’ infosec network .
- What should everyone be aware of when it comes to safeguarding private information?
- Select a company and calculate how much budget they should allocate on cyber security.
- What are the dangers of public Wi-Fi networks ?
- How secure are cloud services ?
- Apple vs. Microsoft : whose systems offer better security?
- Why is it important to remove a USB flash drive safely?
- Is it possible to create an unguessable password?
- Intranet security : best practices.
- Does the use of biometrics increase security?
- Face recognition vs. a simple code: what are the safest locking options for smartphones ?
- How do you recover data from a broken hard drive?
- Discuss the functions and risks of cookies and cache files.
- Online privacy regulations in the US and China.
- Physical components of infosec .
- Debate security concerns regarding electronic health records .
- What are unified user profiles, and what makes them potentially risky?
🖥️ Cybercrime Topics for a Research Paper
Knowledge is one of today’s most valuable assets. Because of this, cybercrimes usually target the extraction of information. This practice can have devastating effects. Do you want to learn more about the virtual world’s dark side? This section is for you.
- Give an overview of the various types of cybercrimes today . Cybercriminals are becoming more and more inventive. It’s not easy to keep up with the new threats appearing every day. What threats are currently the most prominent?
- How does cryptojacking work, and why is it problematic? Cryptocurrency’s value explosion has made people greedy. Countries such as Iceland have become a haven for datamining. Explore these issues in your essay.
- Analyze the success rate of email frauds . You’ve probably seen irrelevant ads in your spam folder before. They often sound so silly it’s hard to believe they work. Yet, unfortunately, many people become victims of such scams.
- How did the WannaCry malware work? WannaCry was ransomware that caused global trouble in 2017. It led to financial losses in the billions. What made it so dangerous and hard to stop?
- Give famous examples of cybercrimes that targeted people instead of money . Not all cybercrimes want to generate profit. Sometimes, the reasons are political or personal. Explore several instances of such crimes in your essay. How did they pan out?

- Analyze the implications of the Cyberpunk 2077 leak. The game’s bugs and issues made many people angry. Shortly after its flop, hackers released developer CD Projekt Red’s source codes. What far-reaching consequences could this have?
- Why do hackers commit identity theft? Social media has made it easy to steal identities . Many like to display their lives online. In your paper, research what happens to the victims of identity thefts.
- Should governments punish cybercrimes like real-life crimes?
- How does ransomware work?
- Describe the phases of a DDoS attack.
- What cybercrime cases led to changes in the legislature ?
- Track the evolution of online scams.
- Online grooming: how to protect children from predators.
- Are cybercrimes “gateway crimes” that lead to real-life misbehavior?
- What are man-in-the-middle attacks?
- Big data and the rise of internet crimes.
- Are cybercrimes more dangerous to society than they are to corporations?
- Is the internet increasing the likelihood of adolescents engaging in illegal activities?
- Do the downsides of cyberlife outweigh its positives?
- Is constantly checking your crush’s Facebook page cyberstalking?
- How do you recognize your online date is a scam?
- Describe what happens during a Brute Force attack.
- What’s the difference between pharming and phishing?
- The Lehman Bank cybercrimes
- Should the punishments for cybercriminals be harsher than they are now?
- Compare various types of fraud methods .
- How do you mitigate a denial-of-service attack?
🕵️ Topics for a Research Paper on Hacking
Blinking screens and flashing lines of code: the movie industry makes hacking look fascinating. But what actually happens when someone breaks into another person’s computer’s system? Write a paper about it and find out! The following prompts allow you to dive deeper into the subject.
- Is it vital to keep shutting down online movie streaming sites? Many websites offer free movie streaming. If one of their domains gets closed down, they just open another one. Are they a threat to the industry that must be stopped? Or should cyber law enforcement rather focus on more serious crimes?
- Explore the ethical side of whistleblowing. WikiLeaks is a platform for whistleblowers. Its founder, Julian Assange, has been under arrest for a long time. Should whistleblowing be a crime? Why or why not?
- How did Kevin Mitnick’s actions contribute to the American cyber legislature? Mitnick was one of the US’s first most notorious hackers. He claimed to have broken into NORAD’s system. What were the consequences?
- Examine how GhostNet operates. GhostNet is a large organization attacking governments. Its discovery in 2009 led to a major scandal.
- Describe how an SQL injection attack unfolds. Injection attacks target SQL databases and libraries. This way, hackers gain unauthorized access to data.
- What political consequences did the attack on The Interview imply? In 2014, hackers threatened to attack theaters that showed The Interview . As a result, Sony only showed the movie online and in limited releases.
- Write about cross-site request forgery attacks. Every website tells you that logging out is a crucial step. But what can happen if you don’t do it?
- What is “Anonymous,” and what do they do?
- Is it permissible to hack a system to raise awareness of its vulnerabilities?
- Investigate the origins of the hacking culture .
- How did industrial espionage evolve into hacking?
- Is piracy destroying the music and movie industries ?
- Explain the term “cyberwarfare.”
- Contrast different types of hacking .
- Connections between political protests and hacking.
- Is it possible to create an encryption that can’t be hacked?
- The role of hackers in modern warfare .
- Can hacking be ethical?
- Who or what are white hat hackers ?
- Discuss what various types of hackers do.
- Is jailbreaking a crime?
- How does hacking a phone differ from hacking a computer?
- Is hacking your personal home devices problematic?
- What is clickjacking?
- Why would hackers target newspapers ?
- Examine the consequences society would have to bear if a hacker targeted the state.
- Compare and analyze different hacking collectives.
⚖️ Topics on Cyber Law & Ethics to Look Into
Virtual life needs rules just like the real one does. The online world brings a different set of values and issues to the table. And, naturally, cyberlife has a legal framework. That’s where researching cyber law and ethics comes into play.
- Is it ethical that governments can always access their citizens’ data? In some countries, online platforms for personal information are standard. From medical exams to debts , everything is available with a click. The system is inarguably convenient. But what about its downsides?
- Is it still morally permissible to use Spotify ? Spotify has made listening to music more accessible than ever. However, artists only receive a tiny fraction of the company’s profits. Discuss the implications of this fact.
- Should internet forums require users to display their real names? Online harassment is a widespread problem. Nicknames hide the identities of ordinary users as well as perpetrators. Can the mandatory use of real names change the situation?
- Analyze online gaming behavior from a psychological standpoint. If one wants to play online games, one needs to have a thick skin. The community can be harsh. You can dedicate your paper to exploring these behaviors. Or you might want to ponder what game publishers can do to reduce hate speech.
- What type of restrictions should sellers implement to prevent domain speculation? Some people buy domains hoping that they will sell them later for more money. This practice makes registering a new website trickier.
- Does the internet need regulations to make adult content less visible? Every computer without parental control can access pornographic websites. Most of them don’t require registration . Their contents can be disturbing, and their ads can appear anywhere. What can be done about it?
- What are cyber laws still missing in America? The US has established many laws to regulate internet usage. Select the most significant ones and explain their relevance.
- Why should cyber ethics be different from real-world norms?
- Are there instances in which illegal downloading is justified?
- The rule of law in real life vs. in cyberspace.
- Does the internet need a government?
- What is cyber terrorism, and what makes it dangerous?
- Who is responsible for online misbehavior?
- How binding are netiquettes?
- What did the implementation of the GDPR change?
- Compare and contrast Indian vs. Venezuelan internet regulations.
- What does the CLOUD entail?
- How should law enforcement adapt to online technologies?
- AI applications : ethical limits and possibilities.
- Discuss trending topics in cyber law of the past ten years.
- Should schools teach online etiquette?
- Does internet anonymity bring out the worst in people?
- Is data privacy more important than convenience and centralization?
- Debate whether bitcoins could become the currency of the future.
- How can online consumers protect themselves from fraud ?
- Is buying from websites like eBay and Craigslist more ethical than buying from other online marketplaces?
- Present RSF’s Minecraft library and discuss its moral implications.
🖱️ Cyberbullying Topics for Essays and Papers
On the web, everyone can remain anonymous. With this added comfort, bullying rises to another level. It’s a serious issue that’s getting more and more problematic. Cyber security measures can alleviate the burden. Do you want to address the problem? Have a look at our cyberbullying topics below.
Receive a plagiarism-free paper tailored to your instructions. Cut 20% off your first order!
- Cyberbullying prevention in online learning environments . Online classes increase the possibility of cyberbullying. What can teachers do to watch out for their students?
- What makes online emotional abuse particularly difficult to bear? Bullying doesn’t necessarily have to be physical to hurt. Statistics show increased suicide rates among students who were harassed online. Explore the reasons behind this phenomenon.
- How can victims of identity theft reclaim their lives? Identity theft leads not only to mental distress. Thieves also have access to credit card information and other essential assets.
- What are the best methods to stay safe online? When surfing the internet, one always has to be on one’s toes. Avoiding harassment and bullying is a particularly challenging task.
- How can parents monitor their children’s behavior on the web? Children are particularly vulnerable online. They might enter dangerous online relationships with strangers if they feel lonely. They are also more susceptible to scams. What can parents do to protect them?
- Cyberbullying among university students. Online abuse in such websites is very common. Everyone can be a potential target, regardless of age or gender. Discuss whether the structure of social networks helps to spread cyberbullying.
- What societal factors contribute to online bullying? Not everyone who uses the internet becomes an abuser. It’s possible to establish several psychological characteristics of cyberbullies. Explore them in your paper.
- Define how cyberbullying differs from in-person harassment .
- Establish a link between feminism and the fight against cyberstalking .
- The emotional consequences of physical vs. verbal abuse.
- The effects of cyberbullying and academics.
- Short vs. long-term mental health effects of internet bullying .
- What are the most widespread means of cyberbullying ?
- Should people who want to play video games online get over the fact that the community is toxic?
- Is defending the freedom of speech more important than preventing the spread of hate speech?
- Reasons and consequences of Amanda Todd’s suicide.
- The dangers of pro-ana/-mia communities for adolescents.
- What are effective strategies to cope with online harassment ?
- Would cyber communism decrease bullying?
- How enhanced cyber security measures can help reduce abuse.
- The importance of parental control mechanisms on children’s computers.
- Traditional vs. cyberbullying in children.
- Do image-heavy websites such as Tumblr and Instagram affect one’s mental state similarly to active abuse?
- What kind of people does cyber abuse affect the most, and why?
- Analyze how the stalker uses the internet in Netflix’s series You .
- Catfishing: effects and solutions.
Thanks for reading through our article. If you found it helpful, consider sharing it with your friends. We wish you good luck with your project!
Further reading:
- 220 Best Science and Technology Essay Topics to Write About
- 204 Research Topics on Technology & Computer Science
- A List of 580 Interesting Research Topics [2024 Edition]
- A List of 179 Problem Solution Essay Topics & Questions
- 193 Interesting Proposal Essay Topics and Ideas
- 226 Research Topics on Criminal Justice & Criminology
- What Is Cybersecurity?: Cisco
- Cyber Security: Research Areas: The University of Queensland, Australia
- Cybersecurity: National Institute of Standards and Technology
- What Is Information Security?: CSO Online
- Articles on Cyber Ethics: The Conversation
- What Is Cybercrime?: Kaspersky
- Types of Cybercrime and How to Protect Yourself Against Them: Security Traits
- Hacking: Computing: Encyclopedia Britannica
- Hacking News: Science Daily
- Cyberbullying and Cybersecurity: How Are They Connected?: AT&T
- Cyberbullying: What Is It and How to Stop It: UNICEF
- Current Awareness: Cyberlaw Decoded: Florida State University
- Share to Facebook
- Share to Twitter
- Share to LinkedIn
- Share to email

Have you ever wondered why everyone has a unique set of character traits? What is the connection between brain function and people’s behavior? How do we memorize things or make decisions? These are quite intriguing and puzzling questions, right? A science that will answer them is psychology. It’s a multi-faceted...
![research paper topics about internet security Student Exchange Program (Flex) Essay Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/student-exchange-program-284x153.jpg)
Participating in a student exchange program is a perfect opportunity to visit different countries during your college years. You can discover more about other cultures and learn a new language or two. If you have a chance to take part in such a foreign exchange, don’t miss it. Keep in...

How can you define America? If you’ve ever asked yourself this question, studying US history will help you find the answer. This article will help you dive deeper into this versatile subject. Here, you will find: Early and modern US history topics to write about. We’ve also got topics for...
![research paper topics about internet security 380 Powerful Women’s Rights & Feminism Topics [2024]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Womens-Rights-284x153.jpg)
Are you looking for perfect feminist topics? Then you’ve come to the right place. With our help, you can be sure to craft a great essay. Here, you can find feminist topics for discussion, feminism research topics and other ideas and questions for students. Some people think all feminists hate...

If you have an assignment in politics, look no further—this article will help you ace your paper. Here, you will find a list of unique political topics to write about compiled by our custom writing team. But that’s not all of it! Keep reading if you want to: See how to tackle political essay topics in your paper; Choose a topic that will be interesting for you to research; Refresh your knowledge of essential political concepts. Now, without further ado, let’s get started! Below, you’ll find political topics and questions for your task. 🔝 Top 10...

It’s not a secret that our health largely depends on nutrition. A balanced and wholesome diet improves our immune system. It lowers the risk of getting sick and makes us more productive. But if we don’t eat right, our overall well-being and performance worsen. You see, nutrition topics are more...

A presentation is a speech in which you explain a topic to an audience. It usually includes visuals done in a program such as PowerPoint. Teachers in schools and in colleges love to assign presentations for various reasons: It requires students to put their knowledge into practice.It teaches them how...

In modern societies, people do everything to live peacefully. Still, tensions often arise. We call them social issues when they start negatively impacting a specific group of people. Poverty, discrimination, and addiction are examples of such problems. We need to confront them to ensure equal treatment for everyone.

There are many ways to define popular culture. Here’s one of them: pop culture includes mainstream preferences in society within a specific time frame. It covers fashion, music, language, and even food. Pop culture is always evolving, engaging in new trends, and leaving the old ones behind.
![research paper topics about internet security 500 Sociology Questions and Topics [Examples & Tips]](https://custom-writing.org/blog/wp-content/uploads/2021/01/Sociology-Questions-284x153.jpg)
Sociology is a study that focuses on people’s interactions. It looks at structures and changes in social life. Any situation involving people can become a topic of sociology. This article is designed to help high school and college students with sociology assignments. Whether you’re writing an essay, creating a presentation,...

Controversial issues are the ones that evoke a variety of opinions. They often cause heated debates. And, as you can guess, controversial research topics are not easy to handle. Luckily, we’ve got you covered. This article will: help you pick a controversial question for your essay;provide you a list of...

Plates break when you drop them. Glasses help you see better. Have you ever wondered why? Physics has the answer. It studies the observable as well as invisible aspects of nature. An essential part of this is examining the structure and interactions of matter.
Security Management Research Paper Topics

Security management research paper topics are a critical area of study for management students looking to explore the complex world of safeguarding organizational assets. Security management covers various facets, including information security, physical security, risk management, compliance, and more. The study of security management is increasingly relevant in our technology-driven world. Research within this field equips students with the knowledge to protect an organization’s information and physical resources, and the skills to respond to rapidly evolving security threats. This page provides a comprehensive list of research topics to assist students in selecting a subject that aligns with their interests and the current industry demands. The following sections will provide an in-depth look into various security management research topics, organized into ten categories with ten subjects each. Additionally, this page will offer insights into how to choose and write about these topics, along with an overview of iResearchNet’s customized writing services for those who seek professional assistance.
100 Security Management Research Paper Topics
The field of security management is as vast as it is vital in today’s global landscape. From protecting information systems to ensuring the physical safety of assets, security management plays a central role in the smooth operation of organizations across various sectors. As we dive into this comprehensive list of security management research paper topics, students will find a plethora of subjects that are both challenging and relevant. The topics are divided into ten distinct categories, each focusing on a different aspect of security management.
Academic Writing, Editing, Proofreading, And Problem Solving Services
Get 10% off with 24start discount code.
- Role of Encryption in Data Protection
- Security Protocols in Wireless Networks
- Cloud Security Management Strategies
- Biometric Security Measures
- Ethical Hacking and Defense Strategies
- Security Risks in Internet of Things (IoT)
- Mobile Application Security
- Compliance with GDPR and Other Regulations
- Social Engineering Attacks and Prevention
- Virtual Private Networks (VPNs) and Security
- Designing Secure Buildings and Facilities
- Access Control Systems and Technologies
- Surveillance and Monitoring Techniques
- Security Personnel Training and Management
- Risk Assessment for Physical Threats
- Vehicle Security and Fleet Management
- Maritime Security Protocols
- Security Measures for Public Events
- Emergency Response and Evacuation Planning
- Integration of Technology in Physical Security
- Enterprise Risk Management Strategies
- Security Policies and Compliance Auditing
- Regulatory Compliance in Different Industries
- Risk Mitigation and Disaster Recovery Planning
- Cyber Insurance and Risk Transfer
- Security Awareness and Training Programs
- Third-party Vendor Risk Management
- Financial Risk Management in Security Operations
- Implementing ISO Security Standards
- Privacy Policies and Consumer Protection
- Cyber Threat Intelligence and Analysis
- Intrusion Detection Systems and Firewalls
- Secure Software Development Lifecycle
- Incident Response and Crisis Management
- Security Considerations in E-commerce
- Protecting Against Ransomware and Malware
- Security in Social Networking Sites
- Cybersecurity in Critical Infrastructure
- Mobile Device Security in the Workplace
- Privacy vs. Security in Cyber Law
- Role of CISO (Chief Information Security Officer)
- Security Leadership and Governance
- Insider Threat Management and Mitigation
- Security Culture and Employee Behavior
- Contractual and Legal Aspects of Security
- Intellectual Property Protection
- Security Metrics and Performance Indicators
- Outsourcing Security Services
- Security Budgeting and Financial Management
- Integrating Security with Business Strategy
- Terrorism and Counterterrorism Strategies
- Security Intelligence and Law Enforcement
- Border Control and Immigration Security
- Cyber Warfare and State-sponsored Attacks
- Protection of Critical National Infrastructure
- Emergency Preparedness and Response
- Security Considerations in International Relations
- Humanitarian Security and Crisis Management
- Nuclear Security and Non-proliferation
- Global Maritime Security Issues
- Security in Hospitals and Healthcare Facilities
- Patient Data Privacy and HIPAA Compliance
- Medical Device and IoT Security
- Emergency Medical Services and Security
- Security Measures for Mental Health Facilities
- Pharmaceutical Supply Chain Security
- Bioterrorism and Public Health Security
- Security Education for Healthcare Professionals
- Medical Records Security and Management
- Telemedicine and Remote Healthcare Security
- Security Considerations in Online Retail
- Fraud Detection and Prevention Strategies
- Payment Security and PCI Compliance
- Inventory Security and Loss Prevention
- Consumer Trust and Brand Protection
- E-commerce Regulations and Compliance
- Security in Omnichannel Retailing
- Secure Customer Experience Design
- Mobile Commerce Security
- Retail Surveillance and Anti-shoplifting Techniques
- Campus Safety and Security Measures
- Cybersecurity Education and Curriculum
- Student Data Privacy and Protection
- Security in Online Learning Platforms
- Intellectual Property Rights in Academia
- Emergency Response Plans for Educational Institutions
- School Transportation Security
- Security Measures for Laboratories and Research Facilities
- Ethical Guidelines in Academic Research
- Security Considerations in International Student Exchange
- Artificial Intelligence in Security
- Quantum Computing and Cryptography
- Security Implications of 5G Technology
- Sustainable and Green Security Practices
- Human Factors in Security Design
- Blockchain for Security Applications
- Virtual and Augmented Reality Security
- Security in Autonomous Vehicles
- Integration of Smart Technologies in Security
- Ethical Considerations in Emerging Security Technologies
Security management is an ever-evolving field, reacting to both technological advancements and global socio-political changes. The above categories and topics encompass a broad spectrum of the security management domain. This comprehensive list is designed to inspire students and guide them towards a research paper that not only interests them but also contributes to the growing body of knowledge in security management. By exploring these topics, students will have the opportunity to deepen their understanding of current issues and become part of the ongoing conversation in this vital area of study.
Security Management and the Range of Research Paper Topics
Introduction to security management.
Security management has increasingly become a central concern for organizations, governments, and individuals in our interconnected and technologically driven world. Its primary focus is on safeguarding assets, information, and people by assessing risks and implementing strategies to mitigate potential threats. From the micro-level of individual privacy protection to the macro-level of national security, the concepts and practices within this field permeate almost every aspect of our daily lives. This article delves into the fundamental aspects of security management and explores the extensive range of research paper topics it offers.
Key Principles and Concepts in Security Management
- Risk Assessment and Mitigation: At the core of security management lies the process of identifying, evaluating, and minimizing risks. It involves recognizing potential vulnerabilities, assessing the likelihood of threats, and implementing measures to reduce the potential impact.
- Compliance and Regulation: Security management is also heavily influenced by various laws, regulations, and industry standards. Whether it’s GDPR for data protection or HIPAA for healthcare, compliance with these regulations is essential to avoid legal consequences.
- Physical and Cyber Security: Security management encompasses both the physical and digital realms. Physical security focuses on protecting tangible assets, such as buildings and equipment, while cyber security emphasizes safeguarding digital information.
- Human Factors: People are often considered the weakest link in security. Training, awareness, and a robust security culture are crucial in ensuring that employees and stakeholders understand and adhere to security protocols.
- Technology and Innovation: With the advent of new technologies like AI, blockchain, and IoT, security management must continuously evolve to address the unique challenges and opportunities they present.
- Global Perspectives: In a globally connected world, security management must consider international laws, cross-border data flows, and the unique risks associated with different geographical regions.
- Ethics and Social Responsibility: Ethical considerations in security management include respecting individual privacy, transparency in surveillance, and social responsibility in using technology for security purposes.
Range and Depth of Research Paper Topics
Given the complexity and multidimensionality of security management, the range of research paper topics in this field is vast. The following sections provide an insight into the various dimensions that can be explored:
- Information Security Management: Research can focus on encryption, authentication, intrusion detection, or explore the psychological aspects of social engineering attacks.
- Physical Security Management: Topics may include architectural design for security, biometrics, or the balance between security and convenience in access controls.
- Organizational Security Management: This includes leadership and governance in security, insider threats, and the alignment of security strategies with business goals.
- Global and National Security Management: Areas to explore here include counterterrorism strategies, cybersecurity policies among nations, or human rights considerations in security protocols.
- Retail and E-commerce Security Management: From payment security to fraud detection, this area explores the unique challenges in the retail and online shopping environment.
- Emerging Trends in Security Management: This invites research into the future of security management, considering technological advancements, emerging threats, and the ethical implications of new tools and techniques.
Security management is an intricate field that intertwines technological, human, organizational, and societal aspects. It continues to evolve in response to the rapidly changing global landscape marked by technological innovation, geopolitical shifts, and emerging threats. The range of research paper topics in security management reflects this diversity and offers a wealth of opportunities for students to engage with cutting-edge issues.
The ongoing development of this field requires fresh insights, innovative thinking, and a commitment to understanding the underlying principles that govern security management. By delving into any of the areas outlined above, students can contribute to this exciting and ever-changing field. Whether exploring traditional aspects like risk management or venturing into the realms of AI and blockchain, the possibilities for research are as broad and varied as the field itself.
This article provides a foundational understanding of security management and serves as a springboard for further exploration. It’s a gateway to a myriad of research avenues, each offering a unique perspective and challenge, all united by the common goal of enhancing the security and safety of our interconnected world.
How to Choose Security Management Research Paper Topics
Selecting a topic for a research paper in the field of security management is a crucial step that sets the tone for the entire research process. The breadth and depth of this field offer a wide array of possibilities, making the choice both exciting and somewhat daunting. The topic must be relevant, engaging, unique, and, most importantly, aligned with the researcher’s interests and the academic requirements. This section provides a comprehensive guide on how to choose the perfect security management research paper topic, with 10 actionable tips to simplify the process.
- Identify Your Interests: Begin by exploring areas within security management that truly intrigue you. Whether it’s cyber threats, risk management, or physical security measures, your passion for the subject will drive a more engaging research process.
- Understand the Scope: Security management spans across various sectors such as IT, healthcare, retail, and more. Assess the scope of your paper to determine which sector aligns best with your academic needs and professional goals.
- Consider the Relevance: Choose a topic that is pertinent to current trends and challenges in security management. Researching emerging threats or innovative technologies can lead to more compelling findings.
- Assess Available Resources: Ensure that there is enough accessible information and research material on the chosen topic. A topic too obscure might lead to difficulties in finding supporting evidence and data.
- Consult with Your Advisor or Mentor: An experienced academic advisor or mentor can provide valuable insights into the feasibility and potential of various topics, helping you make an informed decision.
- Balance Complexity and Manageability: Selecting a topic that is too broad can be overwhelming, while a narrow topic might lack depth. Striking the right balance ensures that you can comprehensively cover the subject within the stipulated word count and time frame.
- Consider Ethical Implications: Especially in a field like security management, ethical considerations must be at the forefront. Any topic involving human subjects, privacy concerns, or potentially sensitive information should be approached with caution and integrity.
- Align with Learning Objectives: Reflect on the specific learning outcomes of your course or program, and choose a topic that aligns with these objectives. It ensures that your research contributes to your overall academic development.
- Evaluate Potential Contributions: Think about what new insights or perspectives your research could offer to the field of security management. Choosing a topic that allows you to make a meaningful contribution can be more satisfying and impactful.
- Experiment with Preliminary Research: Before finalizing a topic, conduct some preliminary research to gauge the existing literature and potential research gaps. It can help refine your focus and provide a clearer direction.
Choosing a research paper topic in security management is a multifaceted process that requires thoughtful consideration of various factors. By following the tips outlined above, you can navigate through the complexities of this task and select a topic that resonates with your interests, aligns with academic goals, and contributes to the broader field of security management. Remember, a well-chosen topic is the foundation upon which a successful research paper is built. It’s the starting point that leads to a journey filled with discovery, analysis, and intellectual growth. Make this choice wisely, and let it be a gateway to an engaging and rewarding research experience.
How to Write a Security Management Research Paper
A. introductory paragraph.
Writing a research paper on security management requires more than just a keen interest in the subject; it demands a systematic approach, adherence to academic standards, and the ability to synthesize complex information. Security management, with its multifaceted nature encompassing physical security, cybersecurity, risk assessment, and more, offers an exciting but challenging landscape for research. In this section, we will delve into a step-by-step guide comprising 10 vital tips on how to write an effective security management research paper. These tips aim to guide you through the research, planning, writing, and revision stages, ensuring a coherent and impactful paper.
- Choose the Right Topic: Guidance: Reflect on your interests, the current trends in the field, and the available resources. Consult with mentors and refer to the previous section for more insights into selecting the perfect topic.
- Conduct Thorough Research: Guidance: Use reliable sources like academic journals, books, and reputable online resources. Gather diverse viewpoints on the topic and keep track of the sources for citation.
- Develop a Strong Thesis Statement: Guidance: The thesis should encapsulate the main argument or focus of your paper. It should be clear, concise, and specific, providing a roadmap for the reader.
- Create an Outline: Guidance: Outline the main sections, including introduction, literature review, methodology, findings, discussion, conclusion, and references. An organized structure helps maintain coherence and logical flow.
- Write a Compelling Introduction: Guidance: Begin with a hook that grabs the reader’s attention, provide background information, and conclude with the thesis statement. The introduction sets the stage for the entire paper.
- Employ the Appropriate Methodology: Guidance: Choose the research methods that align with your research question and objectives. Explain the rationale behind your choices, ensuring that they adhere to ethical standards.
- Analyze Findings and Discuss Implications: Guidance: Present your research findings in a clear and unbiased manner. Discuss the implications of the results in the context of the existing literature and real-world applications.
- Conclude with Insight: Guidance: Summarize the main findings, restate the thesis in the context of the research, and discuss the potential limitations and future research directions. The conclusion should leave the reader with something to ponder.
- Adhere to Academic Formatting: Guidance: Follow the specific formatting guidelines required by your institution or the style guide (APA, MLA, etc.). Pay attention to citations, references, headings, and overall presentation.
- Revise and Proofread: Guidance: Allocate ample time for revising content, structure, and language. Use tools or seek help from peers or professionals for proofreading to ensure grammatical accuracy and clarity.
Writing a security management research paper is a rigorous and intellectually stimulating endeavor that requires meticulous planning, research, and execution. The tips provided in this guide are meant to facilitate a well-structured and insightful paper that adheres to academic excellence. By following these guidelines, you not only develop a comprehensive understanding of security management but also contribute valuable insights to this evolving field. Remember, writing is a process of exploration, articulation, and refinement. Embrace the challenge, learn from the journey, and take pride in the scholarly contribution you make through your research paper on security management.
iResearchNet’s Custom Research Paper Services
In the complex world of security management, crafting a top-notch research paper can be a daunting task. The landscape of security management is multifaceted, encompassing areas such as cybersecurity, risk analysis, policy development, physical security, and much more. For students juggling multiple responsibilities, producing a quality research paper on these intricate subjects may seem nearly impossible. That’s where iResearchNet comes into play. Offering tailor-made solutions to your academic needs, iResearchNet is your go-to service for custom security management research papers. Below are the features that make iResearchNet the ideal choice for your academic success.
- Expert Degree-Holding Writers: At iResearchNet, we employ writers who not only hold advanced degrees but also have extensive experience in security management. Their expertise ensures that your paper is insightful, well-researched, and academically sound.
- Custom Written Works: Every research paper is crafted from scratch, tailored to your specific needs, guidelines, and preferences. Our writers work closely with you to understand your vision, making the paper uniquely yours.
- In-Depth Research: Our team engages in thorough research, using reputable sources and cutting-edge methodologies. This diligent approach guarantees a comprehensive understanding of the subject and a well-rounded paper.
- Custom Formatting: Adhering to academic standards is crucial, and our writers are skilled in various formatting styles. Whether APA, MLA, Chicago/Turabian, or Harvard, your paper will be formatted to perfection.
- Top Quality: Quality is at the core of our services. From the initial draft to the final submission, we maintain the highest standards of excellence, ensuring that your paper stands out.
- Customized Solutions: We recognize that each student’s needs are unique. Hence, our solutions are not one-size-fits-all but are customized to meet your specific requirements, timelines, and academic level.
- Flexible Pricing: Quality doesn’t have to break the bank. Our pricing structure is designed to be affordable and flexible, providing various options to fit different budgets.
- Short Deadlines: Whether you’re facing a last-minute crunch or planning ahead, our writers can accommodate tight deadlines. Even within as short as 3 hours, we deliver without compromising on quality.
- Timely Delivery: Your time is valuable, and we respect that. Our commitment to timely delivery ensures that you receive your paper well before the deadline, giving you ample time for review.
- 24/7 Support: Questions or concerns? Our support team is available around the clock. With 24/7 assistance, you can rest assured that help is always just a click away.
- Absolute Privacy: Your privacy is our priority. We employ stringent security measures to protect your personal information. With iResearchNet, your details are safe, secure, and confidential.
- Easy Order Tracking: With our user-friendly tracking system, you can easily monitor the progress of your order. Stay updated, provide feedback, and enjoy a smooth and transparent process.
- Money Back Guarantee: Your satisfaction is our goal. If, for any reason, our services do not meet your expectations, our money-back guarantee ensures that you are not at a loss.
iResearchNet’s custom security management research paper services are more than just a promise; they are a commitment to excellence, convenience, and integrity. Our blend of expert writers, personalized solutions, quality assurance, and robust support makes us the preferred choice for students across the globe. Dive into the world of security management without the stress of paper writing, knowing that iResearchNet has got your back. Embark on your academic journey with confidence and trust in a partner who understands your needs and shares your pursuit of excellence. With iResearchNet, you’re not just ordering a paper; you’re investing in your future.
Secure Your Academic Success Today
Are you feeling overwhelmed with the prospect of writing your security management research paper? Perhaps you’re struggling to find the right topic, or the research is becoming a tedious task? You don’t have to go through this alone. With iResearchNet’s specialized writing services, all your academic challenges can be turned into opportunities for success.
What sets iResearchNet apart from other writing services is not just our expertise and quality but our understanding of students’ needs. We know that every research paper is not just a task but a step towards your future career in security management. That’s why we invest our best resources to make sure your paper is nothing short of perfect. Our expert writers, meticulous research, and dedication to your satisfaction are all geared towards one goal – helping you excel.
We don’t just write papers; we create opportunities for learning and growth. When you choose iResearchNet, you’re not only receiving a top-notch research paper but also gaining access to a treasure trove of knowledge in security management. With our 24/7 support, flexible pricing, and customizable solutions, your success is no longer a distant dream but a tangible reality.
Take the step towards a brighter academic future. Don’t let the burden of research and writing hold you back from achieving your best. Click the button below to place your order and begin a collaborative journey with iResearchNet. With our secure and user-friendly platform, ordering your custom security management research paper is just a few clicks away. Empower yourself with the right partner, and let iResearchNet pave the way to your academic success.
ORDER HIGH QUALITY CUSTOM PAPER

A Study of Cyber Security Issues and Challenges
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
A Review on the Security of the Internet of Things: Challenges and Solutions
- Published: 06 March 2021
- Volume 119 , pages 2603–2637, ( 2021 )
Cite this article
- Oludare Isaac Abiodun 1 , 2 ,
- Esther Omolara Abiodun ORCID: orcid.org/0000-0002-7801-2541 1 ,
- Moatsum Alawida 1 ,
- Rami S. Alkhawaldeh 3 &
- Humaira Arshad 4
3290 Accesses
43 Citations
Explore all metrics
The Internet of Things (IoT) has emerged as a modern wave of Internet technologies that promises great transformation of life in areas such as smart health, smart cities, smart homes, intelligent transport, amongst others. However, security often serves as a critical reason for the widespread adoption of any innovation. While the IoT has increased business productivity and enriched diverse areas of life over the years, the world is yet to see a methodical revolution of its humongous application and transformation given its ubiquity and highly interconnected global network structure. The main culprit for such lapses is principally attributed to security and privacy issues which have been widely discussed in research articles and reviews but remain largely unaddressed in the literature. Hence, this paper provides a state-of-the-art review of IoT security and its challenges. It overviews technical and legal solutions that are useful to private, organizational, and governmental enterprises. The study encompasses the review and security analysis of IoT’s evolution and revolution, IoT security assessments, requirements, current research challenges in security and much more. Consequently, it offers potential solutions to address the security challenges discussed and further present open research issues, research gaps, opportunities, future development, and recommendations. This overview is intended to serve as a knowledgebase that will proffer novel foresight to guide users and administrators in positioning themselves and their organizations in a manner that is consistent with their overall objectives, mission, and vision for remarkable outcomes. Likewise, interested scholars and researchers can explore topics and directions from the study in providing better solutions to the numerous problems in IoT security.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Internet of Things (IoT) Security Challenges and Solutions: A Systematic Literature Review

Security in the Internet of Things: Recent Challenges and Solutions

Research Challenges in the Internet of Things (IoTs)
Code availability.
This article contains no source code.
Availability of Data and Material
This article contains no data or material other than the articles used for the review and which have been referenced.
International Data Corporation. (2019). The Growth in Connected IoT Devices Is Expected to Generate 79.4ZB of Data in 2025, According to a New IDC Forecast. Retrieved October 06, 2020, from https://www.idc.com/getdoc.jsp?containerId=prUS45213219 .
Schneier, B. (2017). IoT security: What’s plan B? IEEE Security & Privacy, 5, 96–96.
Article Google Scholar
Sicari, S., Cappiello, C., De Pellegrini, F., Miorandi, D., & Coen-Porisini, A. (2016). A security-and quality-aware system architecture for Internet of Things. Information Systems Frontiers, 18 (4), 665–677.
Sadeghi, A.-R., Wachsmann, C., & Waidner, M. (2015). Security and privacy challenges in industrial internet of things. In Proceedings of the 52nd annual design automation conference on—DAC ’15 (pp. 1–6).
Hadnagy, C. (2010). Social engineering: The art of human hacking . Wiley.
Google Scholar
Alhalafi, N., & Veeraraghavan, P. (2019). Privacy and security challenges and solutions in IOT: A review. In IOP conference series: Earth and environmental science (Vol. 322, No. 1, pp. 012013). IOP Publishing.
Alaba, F. A., Othman, M., Hashem, I. A. T., & Alotaibi, F. (2017). Internet of Things security: A survey. Journal of Network and Computer Applications, 88, 10–28.
Khan, M. A., & Salah, K. (2018). IoT security: Review, blockchain solutions, and open challenges. Future Generation Computer Systems, 82, 395–411.
Granjal, J., Monteiro, E., & Silva, J. S. (2015). Security for the internet of things: A survey of existing protocols and open research issues. IEEE Communications Surveys & Tutorials, 17 (3), 1294–1312.
Alrajeh, N. A., & Lloret, J. (2013). Intrusion detection systems based on artificial intelligence techniques in wireless sensor networks. International Journal of Distributed Sensor Networks, 9 (10), 351047.
Abduvaliyev, A., Pathan, A. S. K., Zhou, J., Roman, R., & Wong, W. C. (2013). On the vital areas of intrusion detection systems in wireless sensor networks. IEEE Communications Surveys & Tutorials, 15 (3), 1223–1237.
Sicari, S., Rizzardi, A., Grieco, L. A., & Coen-Porisini, A. (2015). Security, privacy and trust in Internet of Things: The road ahead. Computer networks, 76, 146–164.
Zhou, J., Cao, Z., Dong, X., & Vasilakos, A. V. (2017). Security and privacy for cloud-based IoT: Challenges. IEEE Communications Magazine, 55 (1), 26–33.
Yi, S., Qin, Z., & Li, Q. (2015). Security and privacy issues of fog computing: A survey. In International conference on wireless algorithms, systems, and applications (pp. 685–695). Springer, Cham.
Mukherjee, M., Matam, R., Shu, L., Maglaras, L., Ferrag, M. A., Choudhury, N., & Kumar, V. (2017). Security and privacy in fog computing: Challenges. IEEE Access, 5, 19293–19304.
Roman, R., Lopez, J., & Mambo, M. (2018). Mobile edge computing, fog et al.: A survey and analysis of security threats and challenges. Future Generation Computer Systems, 78, 680–698.
Barrow, P., Kumari, R., & Manjula, R. (2016). Security in Cloud computing for service delivery models: Challenges and solutions. Journal of Engineering Research and Applications , 6 (4), 76–85.
Hepsiba, C. L., & Sathiaseelan, J. G. R. (2016). Security issues in service models of cloud computing. International Journal of Computer Science and Mobile Computing, 5 (3), 610–615.
Subashini, S., & Kavitha, V. (2011). A survey on security issues in service delivery models of cloud computing. Journal of Network and Computer Applications, 34 (1), 1–11.
Hassija, V., Chamola, V., Saxena, V., Jain, D., Goyal, P., & Sikdar, B. (2019). A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access, 7, 82721–82743.
Ammar, M., Russello, G., & Crispo, B. (2018). Internet of Things: A survey on the security of IoT frameworks. Journal of Information Security and Applications, 38, 8–27.
Li, S., Da Xu, L., & Zhao, S. (2015). The internet of things: A survey. Information Systems Frontiers, 17 (2), 243–259.
Kamin, D. A. (2017). Exploring security, privacy, and reliability strategies to enable the adoption of IoT . Minneapolis, MN, United States of America: Walden University.
Prasad, A. V. (Ed.). (2017). Exploring the convergence of big data and the internet of things (Vol. 13, pp. 1–23). IGI Global.
Waraga, O. A., Bettayeb, M., Nasir, Q., & Talib, M. A. (2020). Design and implementation of automated IoT security testbed. Computers & Security, 88, 101648.
Davis, G. (2018). 2020: Life with 50 billion connected devices. In 2018 IEEE international conference on consumer electronics (ICCE) (pp. 1–1). IEEE.
Saha, H. N., Mandal, A., & Sinha, A. (2017). Recent trends in the Internet of Things. In 2017 IEEE 7th annual computing and communication workshop and conference (CCWC) (pp. 1–4). IEEE.
Nordrum, A. (2016). The internet of fewer things [news]. IEEE Spectrum, 53 (10), 12–13.
Chase, J. (2013). The evolution of the internet of things. Texas Instruments, 1, 1–7.
Yinbiao, S., Lee, K., Lanctot, P., Jianbin, F., Hao, H., Chow, B., & Desbenoit, J. P. (2014). Internet of things: Wireless sensor networks. White Paper, International Electrotechnical Commission , http://www.iec . ch, 11.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012). Security in the internet of things: A review. In 2012 international conference on computer science and electronics engineering (Vol. 3, pp. 648–651). IEEE.
Banafa, A. (2019). Three major challenges facing IoT. IEEE Internet of Things Newsletter , 4 (3), 12–23.
Pham, C., Lim, Y., & Tan, Y. (2016). Management architecture for heterogeneous IoT devices in home network. In 2016 IEEE 5th Global Conference on Consumer Electronics (pp. 1–5). IEEE.
Van den Abeele, F., Hoebeke, J., Moerman, I., & Demeester, P. (2015). Integration of heterogeneous devices and communication models via the cloud in the constrained internet of things. International Journal of Distributed Sensor Networks, 11 (10), 683425.
Vargas, D. C. Y., & Salvador, C. E. P. (2016). Smart IoT gateway for heterogeneous devices interoperability. IEEE Latin America Transactions, 14 (8), 3900–3906.
Rose, K., Eldridge, S., & Chapin, L. (2015). The internet of things: An overview. The Internet Society (ISOC) , 80 , 1–50.
Stergiou, C., Psannis, K. E., Kim, B. G., & Gupta, B. (2018). Secure integration of IoT and cloud computing. Future Generation Computer Systems, 78, 964–975.
Iqbal, M. A., Olaleye, O. G., & Bayoumi, M. A. (2017). A review on internet of things (IoT): Security and privacy requirements and the solution approaches. Global Journal of Computer Science and Technology , 16 (2), 1–11.
Yan, Z., Zhang, P., & Vasilakos, A. V. (2014). A survey on trust management for internet of things. Journal of Network and Computer Applications, 42, 120–134.
Ahlgren, B., Hidell, M., & Ngai, E. C. H. (2016). Internet of things for smart cities: Interoperability and open data. IEEE Internet Computing, 20 (6), 52–56.
Alansari, Z., Anuar, N. B., Kamsin, A., Belgaum, M. R., Alshaer, J., Soomro, S., & Miraz, M. H. (2018). Internet of things: Infrastructure, architecture, security and privacy. In 2018 International conference on computing, electronics & communications engineering (iCCECE) (pp. 150–155). IEEE.
Qiu, T., Chen, N., Li, K., Atiquzzaman, M., & Zhao, W. (2018). How can heterogeneous Internet of Things build our future: A Survey. IEEE Communications Surveys & Tutorials, 20 (3), 2011–2027.
Bao, F., Chen, R., Chang, M., & Cho, J. H. (2012). Hierarchical trust management for wireless sensor networks and its applications to trust-based routing and intrusion detection. IEEE transactions on network and service management, 9 (2), 169–183.
Kumarage, H., Khalil, I., Tari, Z., & Zomaya, A. (2013). Distributed anomaly detection for industrial wireless sensor networks based on fuzzy data modelling. Journal of Parallel and Distributed Computing, 73 (6), 790–806.
Duc, A. N., Jabangwe, R., Paul, P., & Abrahamsson, P. (2017). Security challenges in IoT development: A software engineering perspective. In Proceedings of the XP2017 scientific workshops (pp. 1–5).
Barrera, D., Molloy, I., & Huang, H. (2018). Standardizing IoT network security policy enforcement. In Workshop on decentralized IoT security and standards (DISS) (Vol. 2018, p. 6).
Andrea, I., Chrysostomou, C., and Hadjichristofi, G. (2016). Internet of Things: Security vulnerabilities and challenges. In Proceedings—IEEE symposium on computers and communications (pp. 180–187).
Lee, H., Lee, D., Moon, J., Jung, J., Kang, D., Kim, H., & Won, D. (2018). An improved anonymous authentication scheme for roaming in ubiquitous networks. PLoS ONE, 13 (3), e0193366.
Saleem, J., Hammoudeh, M., Raza, U., Adebisi, B., & Ande, R. (2018). IoT standardisation: Challenges, perspectives and solution. In Proceedings of the 2nd International Conference on Future Networks and Distributed Systems (pp. 1–9).
Coulter, R., & Pan, L. (2018). Intelligent agents defending for an IoT world: A review. Computers & Security, 73, 439–458.
Hossain, M. M., Fotouhi, M., & Hasan, R. (2015). Towards an analysis of security issues, challenges, and open problems in the internet of things. IEEE World Congress on Services , 21–28.
Abomhara, M., & Køien, G. M. (2014). Security and privacy in the Internet of Things: Current status and open issues. In 2014 international conference on privacy and security in mobile systems (PRISMS) (pp. 1–8). IEEE.
Roman, R., Najera, P., & Lopez, J. (2011). Securing the internet of things. Computer, 44 (9), 51–58.
Lee, J. (2018). Collective attestation for manageable IoT environments. Applied Sciences, 8 (12), 2652.
Chaudhry, S. A., Naqvi, H., Mahmood, K., Ahmad, H. F., & Khan, M. K. (2017). An improved remote user authentication scheme using elliptic curve cryptography. Wireless Personal Communications, 96 (4), 5355–5373.
Mahmood, Z., Ning, H., & Ghafoor, A. (2016). Lightweight two-level session key management for end user authentication in Internet of Things. In 2016 IEEE international conference on internet of things (iThings) and IEEE Green computing and communications (GreenCom) and IEEE Cyber , Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData) (pp. 323–327). IEEE.
Zhang, C., & Green, R. (2015). Communication security in internet of thing: Preventive measure and avoid DDoS attack over IoT network. In Proceedings of the 18th symposium on communications & networking (pp. 8–15).
Zhang, Z. K., Cho, M. C. Y., & Shieh, S. (2015). Emerging security threats and countermeasures in IoT. In Proceedings of the 10th ACM symposium on information, computer and communications security (pp. 1–6).
Henze, M., Hummen, R., & Wehrle, K. (2013). The cloud needs cross-layer data handling annotations. In 2013 IEEE security and privacy workshops (pp. 18–22). IEEE.
Phung, P. H., Truong, H. L., & Yasoju, D. T. (2017). P4SINC-an execution policy framework for IoT services in the edge. In 2017 IEEE international congress on internet of things (ICIOT) (pp. 137–142). IEEE.
Yu, T., Sekar, V., Seshan, S., Agarwal, Y., and Xu, C. (2015). Handling a trillion (unfixable) flaws on a billion devices. In Proceedings of the 14th ACM workshop on hot topics in networks — HotNets-XIV (pp. 1–7). ACM Press.
Misra, S., Gupta, A., Krishna, P. V., Agarwal, H., & Obaidat, M. S. (2012). An adaptive learning approach for fault-tolerant routing in Internet of Things. In 2012 IEEE wireless communications and networking conference (WCNC) (pp. 815–819). IEEE.
Kumar, S. A., Vealey, T., and Srivastava, H. (2016). Security in Internet of Things: Challenges, solutions and future directions. In 49th Hawaii international conference on system sciences (HICSS) (pp. 5772–5781). IEEE.
Nguyen, K. T., Laurent, M., & Oualha, N. (2015). Survey on secure communication protocols for the Internet of Things. Ad Hoc Networks, 32, 17–31.
Karlsson, J., Dooley, L. S., & Pulkkis, G. (2018). Secure routing for MANET connected Internet of Things systems. In 2018 IEEE 6th international conference on future internet of things and cloud (FiCloud) (pp. 114–119). IEEE.
Airehrour, D., Gutierrez, J., & Ray, S. K. (2016). Secure routing for internet of things: A survey. Journal of Network and Computer Applications, 66, 198.
Bhardwaj, K., Miranda, J. C., & Gavrilovska, A. (2018). Towards iot-ddos prevention using edge computing. In {USENIX} workshop on hot topics in edge computing (HotEdge 18).
Razzak, F. (2012). Spamming the Internet of Things: A possibility and its probable solution. Procedia Computer Science, 10, 658–665.
Zamfiroiu, A., Iancu, B., Boja, C., Georgescu, T., & Cartas, C. (2019). IoT Architectures for Critical Infrastructures Protection. In European conference on cyber warfare and security (pp. 613–XII). Academic Conferences International Limited.
Vasilomanolakis, E., Daubert, J., Luthra, M., Gazis, V., Wiesmaier, A., & Kikiras, P. (2015). On the security and privacy of Internet of Things architectures and systems. In 2015 International workshop on secure internet of things (SIoT) (pp. 49–57). IEEE.
Kozlov, D., Veijalainen, J., & Ali, Y. (2012). Security and privacy threats in IoT architectures. In BODYNETS (pp. 256–262).
Porras, J., Khakurel, J., Knutas, A., & Pänkäläinen, J. (2018). Security challenges and solutions in the internet of things. Nordic and Baltic Journal of Information and Communications Technologies, 2018 (1), 177–206.
Arias, O., Rahman, F., Tehranipoor, M., & Jin, Y. (2018). Device attestation: Past, present, and future. In 2018 Design, automation & test in europe conference & exhibition (DATE) (pp. 473–478). IEEE.
Moon, Y. H., & Jeon, Y. S. (2016). Cooperative remote attestation for IoT swarms. In 2016 International conference on information and communication technology convergence (ICTC) (pp. 1233–1235). IEEE.
Carpent, X., Rattanavipanon, N., & Tsudik, G. (2018). Remote attestation of iot devices via smarm: Shuffled measurements against roving malware. In 2018 IEEE international symposium on hardware oriented security and trust (HOST) (pp. 9–16). IEEE.
Carpent, X., Eldefrawy, K., Rattanavipanon, N., Sadeghi, A. R., & Tsudik, G. (2018). Reconciling remote attestation and safety-critical operation on simple iot devices. In 2018 55th ACM/ESDA/IEEE design automation conference (DAC) (pp. 1–6). IEEE.
Carpent, X., Rattanavipanon, N., & Tsudik, G. (2018). Remote attestation via self-measurement. ACM Transactions on Design Automation of Electronic Systems (TODAES), 24 (1), 1–15.
Perumal, T., Datta, S. K., & Bonnet, C. (2015). IoT device management framework for smart home scenarios. In 2015 IEEE 4th global conference on consumer electronics (GCCE) (pp. 54–55). IEEE.
Malina, L., Hajny, J., Fujdiak, R., & Hosek, J. (2016). On perspective of security and privacy-preserving solutions in the internet of things. Computer Networks, 102, 83–95.
Malina, L., Srivastava, G., Dzurenda, P., Hajny, J., & Fujdiak, R. (2019). A secure publish/subscribe protocol for internet of things. In Proceedings of the 14th international conference on availability, reliability and security (pp. 1–10).
Singh, D., Tripathi, G., & Jara, A. J. (2014). A survey of Internet-of-Things: Future vision, architecture, challenges and services. In 2014 IEEE world forum on Internet of Things (WF-IoT) (pp. 287–292). IEEE.
Abiodun, E. O., Jantan, A., Abiodun, O. I., & Arshad, H. (2020). Reinforcing the security of instant messaging systems using an enhanced honey encryption scheme: The case of WhatsApp. Wireless Personal Communications, 112, 1–24.
Omolara, A. E., Jantan, A., Abiodun, O. I., Dada, K. V., Arshad, H., & Emmanuel, E. (2019). A deception model robust to eavesdropping over communication for social network systems. IEEE Access, 7, 100881–100898.
Benazzouz, Y., Munilla, C., Günalp, O., Gallissot, M., & Gürgen, L. (2014). Sharing user IoT devices in the cloud. In 2014 IEEE world forum on internet of things (WF-IoT) (pp. 373–374). IEEE.
Massonet, P., Naqvi, S., Ponsard, C., Latanicki, J., Rochwerger, B., & Villari, M. (2011). A monitoring and audit logging architecture for data location compliance in federated cloud infrastructures. In 2011 IEEE international symposium on parallel and distributed processing workshops and PhD forum (pp. 1510–1517). IEEE
Sunyaev, A., & Schneider, S. (2013). Cloud services certification. Communications of the ACM, 56 (2), 33–36.
Kunz, T., Selzer, A., & Waldmann, U. (2014). Automatic data protection certificates for cloud-services based on secure logging. In Trusted cloud computing (pp. 59–75). Springer, Cham.
Muñoz, A., & Maña, A. (2013). Bridging the gap between software certification and trusted computing for securing cloud computing. In 2013 IEEE ninth world congress on services (pp. 103–110). IEEE.
Sharma, T., Bambenek, J. C., & Bashir, M. (2020). Preserving privacy in cyber-physical-social systems: An anonymity and access control approach. CEUR WS, 25 (30), 16–30.
Ning, H., & Liu, H. (2012). Cyber-physical-social based security architecture for future internet of things. Advances in Internet of Things, 2 (01), 1.
Thampi, S. M., Pérez, G. M., Westphall, C. B., Hu, J., Fan, C. I., & Mármol, F. G. (Eds.). (2017). Security in Computing and Communications: 5th International Symposium , SSCC 2017, Manipal, India, September 13–16, 2017, Proceedings (Vol. 746). Springer.
Vučinić, M., Tourancheau, B., Rousseau, F., Duda, A., Damon, L., & Guizzetti, R. (2015). OSCAR: Object security architecture for the Internet of Things. Ad Hoc Networks, 32, 3–16.
Bose, P., Gąsieniec, L. A., Römer, K., & Wattenhofer, R. (Eds.). (2015). Algorithms for Sensor Systems: 11th International Symposium on Algorithms and Experiments for Wireless Sensor Networks, Algosensors 2015, Patras, Greece, September 17–18, 2015, Revised Selected Papers (Vol. 9536). Springer.
Coetzee, L., Oosthuizen, D., & Mkhize, B. (2018). An analysis of CoAP as transport in an Internet of Things environment. In 2018 IST-Africa week conference (IST-Africa) (pp. Page-1). IEEE.
Rahman, R. A., & Shah, B. (2016). Security analysis of IoT protocols: A focus in CoAP. In 2016 3rd MEC international conference on big data and smart city (ICBDSC) (pp. 1–7). IEEE.
Chen, X. (2014). Constrained application protocol for internet of things . Retrieved January 3, 2021, from https://www.cse.wustl.edu/~jain/cse574-14/ftp/coap .
Qureshi, M. A., & Munir, A. (2020). PUF-IPA: A PUF-based identity preserving protocol for internet of things authentication. In 2020 IEEE 17th annual consumer communications & networking conference (CCNC) (pp. 1–7). IEEE.
Yilmaz, Y., Gunn, S. R., & Halak, B. (2018). Lightweight PUF-based authentication protocol for IoT devices. In 2018 IEEE 3rd international verification and security workshop (IVSW) (pp. 38–43). IEEE.
Abdul-Ghani, H. A., & Konstantas, D. (2019). A comprehensive study of security and privacy guidelines, threats, and countermeasures: An IoT perspective. Journal of Sensor and Actuator Networks, 8 (2), 22.
Raza, S. (2013). Lightweight security solutions for the internet of things (Doctoral dissertation, Mälardalen University, Västerås, Sweden).
Mazurczyk, W., & Szczypiorski, K. (2014). Advances in digital media security and right management. Multimedia Systems , 20 (2), 102–103.
Zhou, L., & Chao, H. C. (2011). Multimedia traffic security architecture for the internet of things. IEEE Network, 25 (3), 35–40.
Joshi, J. B., Shyu, M., Chen, S. C., Aref, W., & Ghafoor, A. (2008). A multimedia-based threat management and information security framework. In Multimedia technologies: Concepts, methodologies, tools, and applications (pp. 509–526). IGI Global.
Sadek, I., Rehman, S. U., Codjo, J., & Abdulrazak, B. (2019). Privacy and security of IoT based healthcare systems: Concerns, solutions, and recommendations. In International conference on smart homes and health telematics (pp. 3–17). Springer, Cham.
Download references
This paper was partially supported by the Center for Cyber Safety and Education, Internal Revenue segregated fund of (ISC) 2 , Code. EIN: 45–2405127 via the (ISC)2 graduate cybersecurity scholarship award, 311 Park Place Blvd. Suite 610 Clearwater, FL 33759, USA.
Author information
Authors and affiliations.
School of Computer Science, University Sains Malaysia, George Town, Penang, Malaysia
Oludare Isaac Abiodun, Esther Omolara Abiodun & Moatsum Alawida
Department of Computer Science, Bingham University, New Karu, Nasarawa State, Nigeria
Oludare Isaac Abiodun
Department of Computer Information Systems, The University of Jordan, Aqaba, 77110, Jordan
Rami S. Alkhawaldeh
The Islamia University of Bahawalpur, Bahawalpur, Pakistan
Humaira Arshad
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Esther Omolara Abiodun .
Ethics declarations
Conflict of interest.
All authors declare that there are no conflicting interests of whatsoever.
Human and Animal’s Rights
This article does not contain any studies with human participants or animals performed by any of the authors .
Informed Consent
Informed consent was not required in this article as no human or animals were involved.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Abiodun, O.I., Abiodun, E.O., Alawida, M. et al. A Review on the Security of the Internet of Things: Challenges and Solutions. Wireless Pers Commun 119 , 2603–2637 (2021). https://doi.org/10.1007/s11277-021-08348-9
Download citation
Accepted : 19 February 2021
Published : 06 March 2021
Issue Date : August 2021
DOI : https://doi.org/10.1007/s11277-021-08348-9
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Internet of things (IoT)
- Security and privacy challenges in the internet of things
- Solutions to IoT security and privacy challenges
- IoT research gaps
- Future development in the IoT
- Find a journal
- Publish with us
- Track your research
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
- We're Hiring!
- Help Center
Internet Security
- Most Cited Papers
- Most Downloaded Papers
- Newest Papers
- Save to Library
- Last »
- Network Security Follow Following
- Information Security Follow Following
- Internet and web security Follow Following
- Computer Security Follow Following
- World Wide Web Follow Following
- Software Security Follow Following
- Internet Governance Follow Following
- Cyber Security Follow Following
- Evarist Galois Follow Following
- Analytical Functions Follow Following
Enter the email address you signed up with and we'll email you a reset link.
- Academia.edu Publishing
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024

Published: 8 April 2024 Contributors: Gregg Lindemulder, Amber Forrest
Open-source intelligence (OSINT) is the process of gathering and analyzing publicly available information to assess threats, make decisions or answer specific questions.
Many organizations use OSINT as a cybersecurity tool to help gauge security risks and identify vulnerabilities in their IT systems. Cybercriminals and hackers also use OSINT techniques for social engineering , phishing and exposing targets for cyberattacks.
Beyond cybersecurity, other disciplines such as law enforcement, national security, marketing, journalism and academic research may also make use of open-source intelligence.
As far back as World War II, highly trained agents in the intelligence community have monitored open-source information such as radio broadcasts, newspapers and market fluctuations. Today, given the number and variety of easily accessible data sources, nearly anyone can participate in open-source intelligence gathering.
Some of the public sources from which OSINT researchers collect data points include:
Internet search engines such as Google, DuckDuckGo, Yahoo, Bing and Yandex.
Print and online news media including newspapers, magazines and news sites.
Social media accounts on platforms such as Facebook, X, Instagram and LinkedIn.
Online forums, blogs and Internet Relay Chats (IRC).
The dark web , an encrypted area of the internet that is not indexed by search engines.
Online directories of phone numbers, email addresses and physical addresses.
Public records including births, deaths, court documents and business filings.
Government records such as meeting transcripts, budgets, speeches and press releases issued by local, state and federal/national governments.
Academic research including papers, theses and journals.
Technical data such as IP addresses, APIs , open ports and web page metadata.
However, before data collection from OSINT sources begin, a clear objective should be established. For example, security professionals who use OSINT first determine which insights they seek to uncover, and which public data will yield the desired results.
After the public information is collected, it must then be processed to filter out unnecessary or redundant data. Security teams can then analyze the refined data and create an actionable intelligence report.
Threat actors often use OSINT to uncover sensitive information they can leverage to exploit vulnerabilities in computer networks.
This may include personal details about an organization’s employees, partners and vendors that are easily accessible on social media and company websites. Or technical information such as credentials, security gaps or encryption keys that may appear in the source code of web pages or cloud applications. There are also public websites that publish compromising information such as stolen logins and passwords from data breaches.
Cybercriminals are able to use this public data for a variety of nefarious purposes.
For example, they could use personal information from social networks to create tailored phishing emails that convince readers to click on a malicious link. Or conduct a Google search with specific commands that reveal security weaknesses in a web application, a practice called “Google dorking.” They may also evade detection during a hacking attempt after reviewing a company’s public assets that describe their cybersecurity defense strategies.
For these reasons, many organizations conduct OSINT assessments of the public sources of information related to their systems, applications and human resources.
The findings can be used to locate unauthorized leaks of proprietary or sensitive data, evaluate information security, and identify vulnerabilities such as unpatched software, misconfigurations or open ports. Organizations may also conduct penetration testing of their systems and networks using the same OSINT data that are publicly accessible by cybercriminals and hackers.
Often, the information collected during an OSINT assessment is combined with non-public data to create a more comprehensive threat intelligence report. Frequent updates to OSINT cybersecurity assessments can help organizations mitigate the risk of data breaches, ransomware, malware and other cyberattacks.
Because of the vast amount of public information available, it is often impractical to manually collect, sort and analyze OSINT data. Specialized open-source intelligence tools can help manage and automate data tasks for a variety of OSINT use cases.
Some OSINT analysis tools use artificial intelligence and machine learning to detect which information is valuable and relevant, and which is insignificant or unrelated. Among the more popular OSINT tools are:
Osintframework.com (link resides outside ibm.com) – An extensive directory of free, online OSINT tools and resources hosted on the developer platform GitHub. Both hackers and cybersecurity professionals can use this directory as a starting point to drill down into the specific functionality they seek in an OSINT tool.
Maltego (link resides outside ibm.com) – A real-time data mining solution for Windows, Mac and Linux platforms that provides graphic representations of data patterns and connections. With its ability to profile and track the online activities of individuals, this tool can be useful to both cybersecurity professionals and threat actors.
Spiderfoot (link resides outside ibm.com) – A data source integration tool for information such as email addresses, phone numbers, IP addresses, subdomains and more. Ethical hackers may use this resource to investigate publicly available information that could pose a threat to an organization or an individual.
Shodan (link resides outside ibm.com) – A search engine for internet-connected devices that can also provide information on metadata and open ports. Because this tool can identify security vulnerabilities for millions of devices, it can be useful to both cybersecurity professionals and cybercriminals.
Babel X (link resides outside ibm.com) – A multilingual, AI-enabled search tool capable of searching the world wide web and dark web in more than 200 languages. Security teams within an organization may use this tool to search for sensitive or proprietary information that may be posted on the dark web or in a foreign country.
Metasploit (link resides outside ibm.com) – A penetration testing tool that can identify security vulnerabilities in networks, systems and applications. Both cybersecurity professionals and hackers find value in this tool because it can expose the specific weaknesses that may enable a successful cyberattack.
Redefine SIEM to unleash analyst potential and outpace adversaries with speed, scale and accuracy. QRadar SIEM helps maximize your security team’s productivity by providing a unified experience across all SOC tools, with integrated, advanced AI and automation capabilities.
Leverage our team of world-class intelligence analysts to secure your environment. Gain insights into the latest threats and techniques from malware reverse engineering, dark web research, and vulnerability tracking.
Detect cyberattacks fast with IBM QRadar SIEM's near real-time threat detection.
Get actionable insights to help you understand how threat actors are waging attacks—and how to proactively protect your organization.
Understand how penetration testing helps organizations uncover critical security vulnerabilities in their applications, networks, devices and other assets.
Discover how security analysts create threat intelligence by analyzing and correlating raw information to help mitigate and prevent cyberattacks before they occur.
Cybersecurity threats are becoming more advanced and more persistent, and demanding more effort by security analysts to sift through countless alerts and incidents. IBM Security QRadar SIEM helps you remediate threats faster while maintaining your bottom line. QRadar SIEM prioritizes high-fidelity alerts to help you catch threats that others simply miss.

IMAGES
VIDEO
COMMENTS
Cyber Security Research Topics. Cyber Security Research Topics are as follows: The role of machine learning in detecting cyber threats. The impact of cloud computing on cyber security. Cyber warfare and its effects on national security. The rise of ransomware attacks and their prevention methods.
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the ...
In 2024, these will be the top cybersecurity trends. A) Exciting Mobile Cyber Security Research Paper Topics. The significance of continuous user authentication on mobile gadgets. The efficacy of different mobile security approaches. Detecting mobile phone hacking.
Depending on the amount of data, the extent of the damage caused by a data breach can be significant, with the average cost being USD 392 million Footnote 1 (IBM Security 2020). This research paper reviews the existing literature and open data sources related to cybersecurity and cyber risk, focusing on the datasets used to improve academic ...
If you're still unsure about how to find a quality research topic, check out our Research Topic Kickstarter service, which is the perfect starting point for developing a unique, well-justified research topic. A comprehensive list of cybersecurity-related research topics. Includes 100% free access to a webinar and research topic evaluator.
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on INTERNET SECURITY. Find methods information, sources, references or conduct a literature review on ...
Artificial intelligence (AI) is one of the key technologies of the Fourth Industrial Revolution (or Industry 4.0), which can be used for the protection of Internet-connected systems from cyber threats, attacks, damage, or unauthorized access. To intelligently solve today's various cybersecurity issues, popular AI techniques involving machine learning and deep learning methods, the concept of ...
The emergence of the Internet of Things (IoT) technology has brought about tremendous possibilities, but at the same time, it has opened up new vulnerabilities and attack vectors that could compromise the confidentiality, integrity, and availability of connected systems. Developing a secure IoT ecosystem is a daunting challenge that requires a systematic and holistic approach to identify and ...
From thousands of candidate papers initially found in our search process, we have systematically distinguished and analyzed thirty-six (36) papers that have been peer-reviewed and published around patterns and architectures for IoT security and privacy in the last decade (January 2010-December 2020).
CNN model provides the highest accuracy of 98.42 with multiclass class. The study shows that DL techniques can be effectively used in cybersecurity applications. Future research areas are being elaborated, including the potential research topics to improve several DL methodologies for cybersecurity applications.
This study aims to uncover the challenges of Internet governing bodies to inform a trajectory for better cybersecurity governance and policy formulation. ... reviewed papers focused on varied issues and overlaps. The power-driven nature of the numerous Internet governing bodies against 14 (20%) of the total included studies calling for some ...
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on INFORMATION SECURITY. Find methods information, sources, references or conduct a literature review on ...
The methodology adopted in this paper is a review of papers with keywords network security, network attacks and threats and network security measures. The aim of this paper is to critically review ...
The best way to develop credible internet security software. How to scan malware on your pc. Evaluate twitter's access control policy. Research Topics In Cybersecurity. You can use any of these research topics in cybersecurity for your papers. You can derive data from some other scholarly articles, documentaries, films, and books.
Browse Internet security news, research and analysis from The Conversation Internet security - News, Research and Analysis - The Conversation - page 1 Menu Close
204 Research Topics on Technology & Computer Science. A List of 580 Interesting Research Topics [2024 Edition] A List of 179 Problem Solution Essay Topics & Questions. 193 Interesting Proposal Essay Topics and Ideas. 226 Research Topics on Criminal Justice & Criminology.
Increasing complexity in and interconnectivity between technologies and systems (e.g., cloud computing, Internet of Things (IoT), fog and edge computing) can complicate data processing and security requirements. Thus, in this paper we review existing literature survey articles focusing on cloud, fog and edge computing platforms and infrastructures. We then present the result of a systematic ...
Research paper. A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments ... Cyberspace coverage is a broad topic. In the following article, we will review the main types of cyber security. ... Distributed network security framework of energy internet based on Internet of Things. Sustain. Energy ...
Abstract. In the recent past, Internet of Things (IoT) has been a focus of. research. With the great potential of IoT, there comes many types of issues and. challenges. Security is one of the main ...
Security management research paper topics are a critical area of study for management students looking to explore the complex world of safeguarding organizational assets. Security management covers various facets, including information security, physical security, risk management, compliance, and more. The study of security management is increasingly relevant in our technology-driven world.
Life has reached a stage where we cannot live without internet enabled technology. New devices and services are being invented continuously with the evolution of new technologies to improve our day-to-day lifestyle. At the same time, this opens many security vulnerabilities. There is a necessity for following proper security measures. Cybercrime may happen to any device/service at any time ...
The Internet of Things (IoT) has emerged as a modern wave of Internet technologies that promises great transformation of life in areas such as smart health, smart cities, smart homes, intelligent transport, amongst others. However, security often serves as a critical reason for the widespread adoption of any innovation. While the IoT has increased business productivity and enriched diverse ...
This paper presents security of Internet of things. In the Internet of Things vision, every physical object has a virtual component that can produce and consume services Such extreme interconnection will bring unprecedented convenience and economy, but it will also require novel approaches to ensure its safe and ethical use.
Many organizations use OSINT as a cybersecurity tool to help gauge security risks and identify vulnerabilities in their IT systems. Cybercriminals and hackers also use OSINT techniques for social engineering, phishing and exposing targets for cyberattacks.. Beyond cybersecurity, other disciplines such as law enforcement, national security, marketing, journalism and academic research may also ...