Got any suggestions?
We want to hear from you! Send us a message and help improve Slidesgo
Top searches
Trending searches


solar eclipse
25 templates

16 templates

autism awareness
28 templates

12 templates

35 templates

7 templates
Security Presentation templates
Safety is one of the most important things in a community and there are so many people involved in different security bodies to assure that there is no danger around. if you want to speak about security in every way and form possible, we are glad to inform you that you are absolutely safe using these google slides themes & powerpoint templates.
Cyber Security Business Plan
The world is getting increasingly digital. While that’s a boost to connectivity, it comes with risks, especially to online security. Use this free template to introduce your cyber security company’s business plan and objectives!

Premium template
Unlock this template and gain unlimited access
Computer Security Day
We've been using computers every day for years. Even our cell phones are like mini-computers (do we actually use them to make calls?). Even some members of the Slidesgo team are believed to be computers! No, we're just that good, but even us have to make sure our data is...

Cybersecurity Infographics
Use these new infographics to explain all about cybersecurity, one of the main aspects that businesses should take care of in today’s world. Compare items, describe concepts, show steps in a process… Just pick one of the designs—ranging from flat and linear to isometric—and go for it!

Stop Cyber Terrorism Campaign
A campaign against cyber terrorism? Yes, please! Use this slide deck to present everything you've been planning out: a cyber security software, online safety awareness and data protection solution, and detail exactly what funds you have allocated and how you’ve planned your advertising. This template’s design is very cyber-oriented and...

Traffic and Road Safety
When it comes to traffic and road safety, we all have a responsibility to do our part. That's why we're excited to present our Google Slides and PPT template that makes speaking about this topic both informative and entertaining. From eye-catching graphics to creative charts, our template is designed to...

Civil Engineering Safety
Download the Civil Engineering Safety presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides and PowerPoint, is what you...

Digital Citizenship
Download the Digital Citizenship presentation for PowerPoint or Google Slides and start impressing your audience with a creative and original design. Slidesgo templates like this one here offer the possibility to convey a concept, idea or topic in a clear, concise and visual way, by using different graphic resources. You...

Workplace Radiation Safety
Download the Workplace Radiation Safety presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides and PowerPoint, is what you...

Personal Protective Equipment (PPE) at Work
In many workplaces, personal protective equipment (PPE) is crucial to ensure the safety of employees and prevent any accidents or injuries on the job. Safety comes first! So, if a company has hired you to give a speech on PPE, including what it is, why it's essential, and how it...

Workplace Safety in Business
In the business world, it's essential to create a safe and secure work environment to protect employees and prevent accidents and injuries that can cause irreparable damage to workers and the company's reputation. In other words, safety first! If there are any doubts about this topic, make sure to clear...

Health & Safety Meeting
Safety should always come first and foremost, no matter what the topic is about. If you have a good set of recommendations and indications for your next meeting and you want everybody to pay attention to your speech, this template will make your presentation unique.

Safety Rules in Company
Do you dread workplace safety rules reviews and your bored audience who doesn’t pay attention because they’ve heard it all a hundred times before? You’ll be happy to hear that those days are over! This cute, lovingly designed Google Slides and PowerPoint template make you employees smile and pay attention...

Health and Safety Workshop
Feeling overwhelmed about organizing a health and safety workshop? Don't worry, we've got you covered! With our creative template, you'll have all the tools you need to make your next workshop a huge success. Not only does it come fully loaded with interesting illustrations that are directly related to the...

Career Technical Subject for Middle School - 6th Grade: Law, Public Safety, & Security
Give your students a bit of information about how the society they live on is structured and protected. Grab their attention with this creative template full of illustrations of judges, police officers, firemen… and maybe you wake up a passion in them! Year 6 is an optimal time for showing...

Safety and Emergency Preparedness - Health - 8th Grade
Download the Safety and Emergency Preparedness - Health - 8th Grade presentation for PowerPoint or Google Slides. If you’re looking for a way to motivate and engage students who are undergoing significant physical, social, and emotional development, then you can’t go wrong with an educational template designed for Middle School...


Security in Cyberspace: Protecting your Data and Privacy
Download the Security in Cyberspace: Protecting your Data and Privacy presentation for PowerPoint or Google Slides. The world of business encompasses a lot of things! From reports to customer profiles, from brainstorming sessions to sales—there's always something to do or something to analyze. This customizable design, available for Google Slides...

Cybersecurity Agency
We use computers every day—at home, at work, almost anywhere. You need to have your data safe and secure, so if your agency offers cybersecurity services, you can promote them with this template. It catches so much attention thanks to its neon colors and its futuristic appearance. Don't forget to...

Digital Scam Awareness Newsletter
No way! You’re telling us that you have been awarded a prize for being the 10,000th visitor of a website? And you only need to send them a picture of your card to cash it? Unbelievable. We have a better gift for you: this template about digital scamming. Use this...
- Page 1 of 9
New! Make quick presentations with AI
Slidesgo AI presentation maker puts the power of design and creativity in your hands, so you can effortlessly craft stunning slideshows in minutes.

Register for free and start editing online
Home PowerPoint Templates Business PowerPoint Templates Cybersecurity Presentation Template
Cybersecurity Presentation Template

Are you looking for an interactive presentation template for your cybersecurity seminar? Then try our 100% editable Cybersecurity Presentation Template. This cybersecurity PPT template is a slide deck prepared using customizable elements to discuss various aspects of the importance of cybersecurity. It starts with a title slide, showing imaginative lines to represent how the devices and online surfing are secured with the cybersecurity protocols. All slides have a similar background and a unique dual-shaded color scheme. Next to the title slide , the following slides are for presenting general topics about cybersecurity, such as introduction, key importance points, and threats.
Further, this template provides personalized slides for presenting company or agency details, e.g., why choose us, services, team members, success stories, data protection protocols, and testimonials. We have also added the preset layout for adding pricing plans to subscribe to the company.
In this era, cyber threats are rising with every passing day. Thus, companies always need external parties to manage the impending threats whenever they launch their online services, applications, or products. For that, many agencies have developed teams of experienced ethical hackers and engineers to protect their clients’ products from harmful cyber attacks. This Cybersecurity Presentation Template is specially crafted for such companies to help them display their services and expertise in this field. They can conveniently download and edit this template to present the main highlights of their company and working methodology. The business PowerPoint template can be adapted to the required theme settings by changing the color scheme and graphical elements. The slides are well-designed for adjusting relevant information. For instance, the global footprint slide has an editable map with a guiding chart, and the success story slide has highlighting text boxes to show the keypoints. Likewise, the data protection process slide has a modern flow diagram with icons. So, presenters can edit the placeholder text boxes and create their personalized presentations in a go. Download and edit this template now!
You must be logged in to download this file.
Favorite Add to Collection
Details (13 slides)

Supported Versions:
Subscribe today and get immediate access to download our PowerPoint templates.
Related PowerPoint Templates

Company Profile Overview PowerPoint Template

Business Profile PowerPoint Template

Creative Agency Company Profile PowerPoint Template

Black & Red Business Pitch Deck Template for PowerPoint
Check out our new Consent management feature here
- Case Studies
- Book a Demo
Understanding Secure Protocols: A Comprehensive Guide
Learn everything you need to know about secure protocols in this comprehensive guide.
Secure protocols play a vital role in ensuring the security and integrity of data transmitted over the internet. In this comprehensive guide, we will explore everything you need to know about secure protocols, from their basics to their implementation.
Introduction to Secure Protocols
Secure protocols are a set of rules and procedures that determine how data is securely transmitted between two or more parties over a network. They provide a secure channel for communication, protecting sensitive information from interception and unauthorized access.
When it comes to the world of technology and the vastness of the internet, security is of utmost importance. With the increasing number of cyber threats and the constant evolution of hacking techniques, it has become necessary to establish secure protocols. These protocols act as a shield, ensuring that data is transmitted safely and securely.
What are Secure Protocols?
Secure protocols are a combination of cryptographic algorithms and protocols designed to establish secure connections and protect data transmitted over a network. They ensure that data is encrypted, authenticated, and delivered to the intended recipient without being tampered with or intercepted by malicious entities.
Imagine a scenario where you are sending an important document over the internet. Without secure protocols, your document could be intercepted by hackers who can manipulate the data or steal sensitive information. However, with the implementation of secure protocols, your document is encrypted and protected, making it nearly impossible for anyone to tamper with it.
The Importance of Secure Protocols
The importance of secure protocols cannot be overstated in today's digital landscape where cyber threats are rampant. By implementing secure protocols, organizations can safeguard their digital assets, including sensitive customer information and confidential business data.
Organizations, both big and small, handle vast amounts of data on a daily basis. This data may include personal information, financial records, or trade secrets. Without secure protocols, this data is vulnerable to attacks from cybercriminals who are constantly looking for opportunities to exploit weaknesses in security systems.
By implementing secure protocols, organizations can ensure that their data remains secure and protected. This not only helps in maintaining the trust of customers and clients but also prevents potential financial losses and reputational damage that can occur as a result of a security breach.
Moreover, secure protocols also play a crucial role in enabling secure online transactions. Whether it is online shopping, banking, or any other form of electronic transaction, secure protocols ensure that sensitive information such as credit card details or login credentials are transmitted securely, without the risk of being intercepted or misused.
In conclusion, secure protocols are an essential component of today's digital world. They provide a layer of protection that is necessary to safeguard sensitive information and maintain the integrity of data transmitted over networks. By understanding the importance of secure protocols and implementing them effectively, organizations can mitigate the risks associated with cyber threats and ensure a secure digital environment for all.
The Evolution of Secure Protocols
Secure protocols have come a long way since their inception. Let's take a brief look at their history and explore modern developments.
A Brief History of Secure Protocols
Secure protocols have been around for decades, evolving to meet the increasing demand for secure communication. The advent of protocols like Secure Sockets Layer (SSL) and Transport Layer Security (TLS) paved the way for secure online transactions and secure communication channels.
Back in the early days of the internet, security was not a major concern. However, as more and more people started using the internet for various purposes, including online banking and e-commerce, the need for secure protocols became apparent. This led to the development of SSL in the mid-1990s, which provided a secure layer for transmitting sensitive information over the internet.
SSL quickly gained popularity and became the standard protocol for securing online transactions. It provided encryption and authentication mechanisms, ensuring that data transmitted between a web server and a client remained confidential and tamper-proof. With SSL, users could feel more confident about sharing their personal and financial information online.
As technology advanced and new security threats emerged, SSL was replaced by TLS, which offered enhanced security features. TLS introduced stronger encryption algorithms and improved authentication mechanisms, making it even more difficult for malicious actors to intercept and manipulate data during transmission.
Modern Developments in Secure Protocols
In recent years, there have been significant advancements in secure protocol technology. New protocols and standards have emerged to address the ever-evolving security threats on the internet.
One notable development is the emergence of the Datagram Transport Layer Security (DTLS) protocol. DTLS is a variation of TLS specifically designed for securing datagram-based applications, such as real-time communication and video streaming. It ensures that data transmitted over unreliable networks, such as the internet, remains secure and intact.
Another significant development is the adoption of the HTTP Secure (HTTPS) protocol as the standard for secure web communication. HTTPS combines the HTTP protocol with SSL or TLS to provide encrypted and authenticated communication between web servers and clients. This not only protects sensitive information but also ensures the integrity of web content, preventing unauthorized modification by attackers.
Furthermore, the Internet Engineering Task Force (IETF) has been actively working on developing new secure protocols and improving existing ones. They have introduced protocols like QUIC (Quick UDP Internet Connections) and TLS 1.3, which aim to enhance the performance and security of internet communication.
QUIC, for example, is designed to reduce latency and improve the speed of web communication. It achieves this by combining the functionalities of multiple protocols, including encryption, congestion control, and error correction, into a single efficient protocol.
TLS 1.3, on the other hand, focuses on improving the security of TLS by removing outdated cryptographic algorithms and implementing stronger encryption mechanisms. It also introduces features like zero-round trip time resumption, which further enhances the performance of secure communication.
In conclusion, secure protocols have evolved significantly over the years to meet the growing demand for secure communication on the internet. From the early days of SSL to the modern developments in protocols like DTLS, HTTPS, QUIC, and TLS 1.3, continuous efforts are being made to ensure that data transmitted over the internet remains confidential, authenticated, and tamper-proof.
Types of Secure Protocols
When it comes to securing communication between web browsers and servers, there are several commonly used secure protocols that play a crucial role. Let's explore these protocols and delve into their specific use cases.
Secure Sockets Layer (SSL)
SSL, which stands for Secure Sockets Layer, is a widely adopted protocol that serves as a cornerstone for securing communication on the internet. Its primary purpose is to establish a secure and encrypted connection between web browsers and servers, ensuring the confidentiality and integrity of transmitted data.
With SSL, sensitive information such as credit card numbers, login credentials, and personal details can be transmitted securely over the internet. It accomplishes this by encrypting the data, making it virtually impossible for unauthorized individuals to intercept and decipher.
Moreover, SSL provides authentication mechanisms that enable web browsers to verify the identity of the server they are communicating with. This prevents malicious attackers from impersonating legitimate websites and stealing sensitive information.
Transport Layer Security (TLS)
Transport Layer Security, commonly known as TLS, is the successor to SSL and has become the industry standard for securing various internet protocols. It offers enhanced security features and improved compatibility with modern cryptographic algorithms.
One of the significant advantages of TLS is its versatility. While SSL primarily focuses on securing web browsing, TLS can be employed to secure a wide range of applications and services. It is commonly used to protect email communication, instant messaging platforms, and virtual private networks (VPNs).
By utilizing TLS, organizations can ensure that sensitive information transmitted through these channels remains confidential and tamper-proof. This is particularly important in today's digital landscape, where cyber threats continue to evolve and pose significant risks to individuals and businesses.
Secure Shell (SSH)
Secure Shell, abbreviated as SSH, is a protocol that provides secure remote access and secure file transfers between systems. It offers a robust alternative to traditional remote access methods, such as Telnet and FTP, which transmit data in plain text and are susceptible to eavesdropping and tampering.
When using SSH, communication between the client and server is encrypted, ensuring the confidentiality and integrity of sensitive information. This is particularly crucial when accessing remote systems over untrusted networks, such as the internet.
In addition to secure remote access, SSH also facilitates secure file transfers. It allows users to securely transfer files between systems, preventing unauthorized individuals from intercepting or modifying the transferred data.
SSH has become an essential tool for system administrators, enabling them to manage remote servers securely and efficiently. It has found widespread adoption in various industries, including IT, finance, and telecommunications.
How Secure Protocols Work
The Role of Encryption in Secure Protocols
Encryption is at the heart of secure protocols. It transforms plaintext data into an unintelligible form, making it unreadable to anyone who doesn't have the decryption key. Through encryption, secure protocols ensure confidentiality and protect the privacy of transmitted data.
The Process of Authentication
Authentication is a critical component of secure protocols. It verifies the identity of the parties involved in the communication process, ensuring that data is exchanged only with trusted entities. Authentication prevents unauthorized access and protects against impersonation attacks.
Ensuring Data Integrity
Data integrity is crucial to secure protocols. It verifies that the transmitted data remains unchanged and untampered during communication. By using cryptographic hash functions and integrity checks, secure protocols can identify any modifications to the data and discard tampered or corrupted information.
Implementing Secure Protocols
Implementing secure protocols requires careful consideration to ensure the appropriate choice and successful implementation. Let's explore the factors involved.
Choosing the Right Secure Protocol
Choosing the right secure protocol depends on the specific use case and requirements. Factors such as encryption strength, compatibility, and support for the desired functionality should be considered when selecting a secure protocol.
Steps to Implement Secure Protocols
Implementing secure protocols involves several steps, including setting up certificates, configuring encryption parameters, and testing the security of the implementation. It is essential to follow best practices and guidelines provided by the protocol's documentation.
Common Challenges and Solutions
Implementing secure protocols can present challenges, such as compatibility issues, maintenance complexities, and the need for continuous monitoring. However, employing robust security measures, keeping the protocols up to date, and regularly reviewing the implementation can address these challenges effectively.
By understanding secure protocols and their significance in today's digital landscape, organizations can establish secure communication channels, protect sensitive data, and mitigate the ever-growing threats posed by cybercriminals.

- Cyber Security Protocols
- Popular Categories
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories
Powerpoint Templates and Google slides for Cyber Security Protocols
Save your time and attract your audience with our fully editable ppt templates and slides..
Item 2281 to 2340 of 2637 total items

- You're currently reading page 39

Presenting this set of slides with name Case Study For Cyber Security Services Ppt Powerpoint Presentation Icon. This is a one stage process. The stages in this process are Problem, Our Solution . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting this set of slides with name Client Testimonials For Cyber Security Organization R81 Ppt Powerpoint Gallery. This is a two stage process. The stages in this process are Client Testimonials For Cyber Security Organization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting this set of slides with name Client Testimonials For Cyber Security Organization R82 Ppt Powerpoint Presentation. This is a three stage process. The stages in this process are Client Testimonials For Cyber Security Organization. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
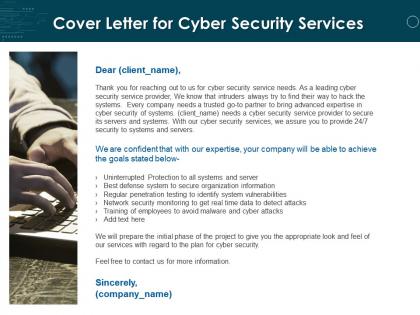
Presenting this set of slides with name Cover Letter For Cyber Security Services Ppt Powerpoint Presentation Visuals. The topics discussed in these slides are Cover Letter For Cyber Security Services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Presenting this set of slides with name Icons Slide For Cyber Security Organization Ppt Powerpoint Presentation Model. The topics discussed in these slides are Icons. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting this set of slides with name Mode Of Communication For Cyber Security Services Ppt Powerpoint Presentation Styles. The topics discussed in these slides are Communicate Medium, Review Sessions, Emails, Description. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting this set of slides with name Next Steps For Cyber Security Services Ppt Powerpoint Presentation Summary. This is a one stage process. The stages in this process are Next Steps For Cyber Security Services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
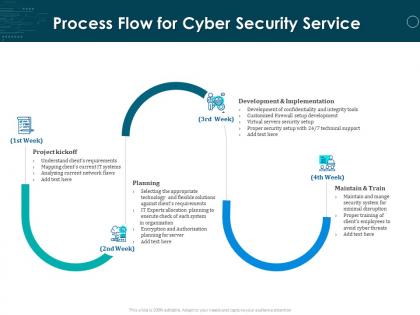
Presenting this set of slides with name Process Flow For Cyber Security Service Ppt Powerpoint Presentation Files. This is a three stage process. The stages in this process are Project Kickoff, Planning, Development And Implementation, Maintain And Train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
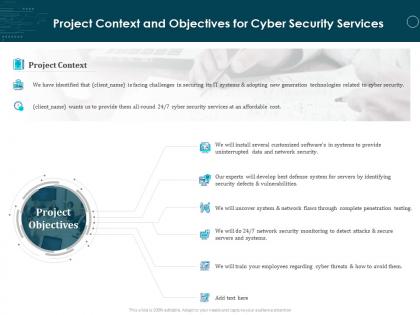
Presenting this set of slides with name Project Context And Objectives For Cyber Security Services Ppt Powerpoint Styles. The topics discussed in these slides are Project Context, Project Objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Presenting this set of slides with name Roadmap For Cyber Security Services Ppt Powerpoint Presentation Ideas. This is a five stage process. The stages in this process are Roadmap For Cyber Security Services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting this set of slides with name Statement Of Work And Contract For Cyber Security Services Ppt Powerpoint Pictures. This is a one stage process. The stages in this process are Services Rendered, Mutual Cooperation, Terms Of Payment, Plans Cancellation, Confidentiality. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Presenting this set of slides with name Timeframe For Cyber Security Services Ppt Powerpoint Presentation Infographic Template. This is a four stage process. The stages in this process are Project Kickoff, Planning, Development And Implementation, Results. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Presenting this set of slides with name Timeline For Cyber Security Services Ppt Powerpoint Presentation Portfolio. This is a five stage process. The stages in this process are Timeline For Cyber Security Services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Presenting this set of slides with name Why Us For Cyber Security Services Ppt Powerpoint Presentation Slides. This is a one stage process. The stages in this process are Why Us For Cyber Security Services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
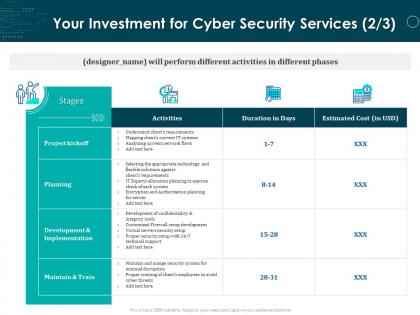
Presenting this set of slides with name Your Investment For Cyber Security Services Activities Ppt Powerpoint Slides. The topics discussed in these slides are Project Kickoff, Planning, Development And Implementation, Maintain And Train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Presenting this set of slides with name Incident Management Process Cyber Security Ppt Powerpoint Presentation Infographics Show Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Incident Management Process Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
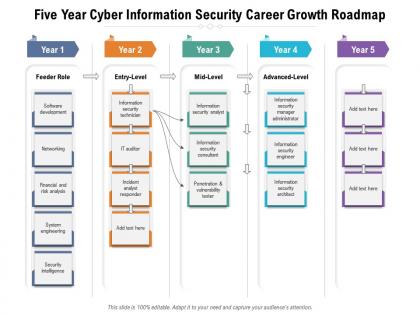
Presenting Five Year Cyber Information Security Career Growth Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
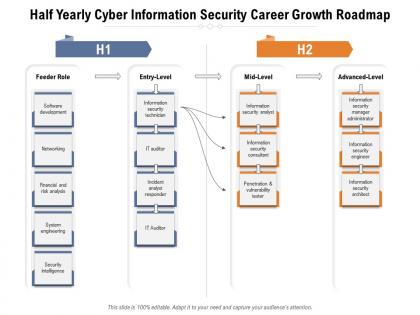
Presenting Half Yearly Cyber Information Security Career Growth Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
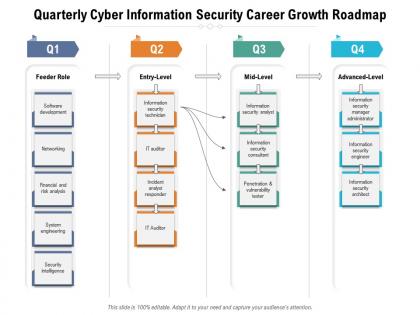
Presenting Quarterly Cyber Information Security Career Growth Roadmap PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
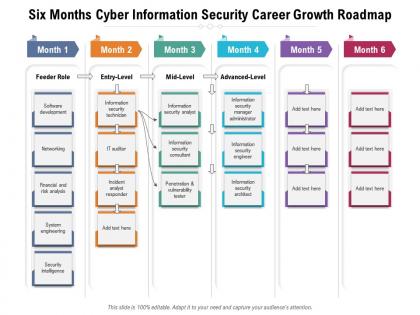
Presenting Six Months Cyber Information Security Career Growth Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
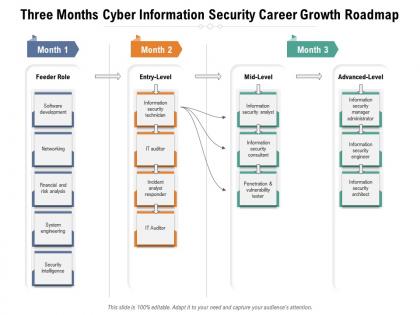
Presenting Three Months Cyber Information Security Career Growth Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
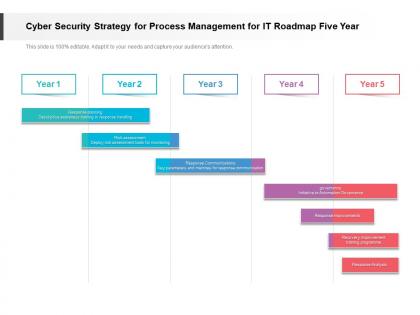
Presenting Cyber Security Strategy For Process Management For IT Roadmap Five Year PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
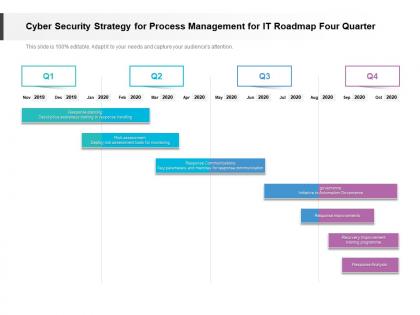
Presenting Cyber Security Strategy For Process Management For IT Roadmap Four Quarter PowerPoint Template. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements.
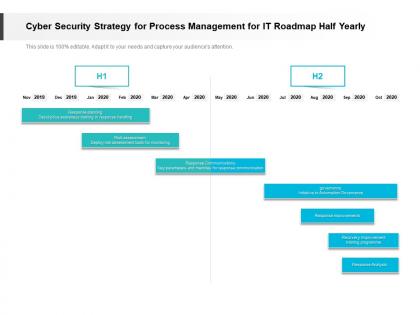
Presenting Cyber Security Strategy For Process Management For IT Roadmap Half Yearly PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
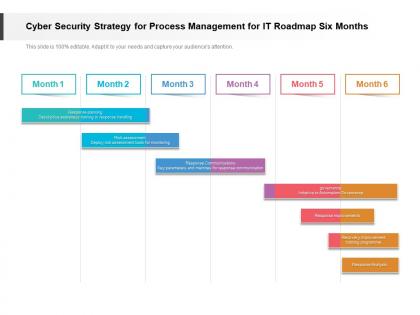
Presenting Cyber Security Strategy For Process Management For IT Roadmap Six Months PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
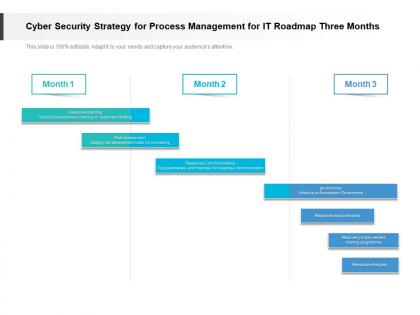
Presenting Cyber Security Strategy For Process Management For IT Roadmap Three Months PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.

Presenting this set of slides with name Project Context And Objectives For Cyber Security Services Ppt File Topics. This is a one stage process. The stages in this process are Project Context, Project Objectives . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Presenting this set of slides with name Cyber Security Attack Scenarios Ppt Powerpoint Presentation Layouts Clipart Images Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Attack Scenarios to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Cyber Security Training Employees Ppt Show Designs Download Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cyber Security Training Employees to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Cyber Security Service Offerings Ppt Powerpoint Presentation Inspiration Show Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Service Offerings to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Pros Cons Cyber Security Ppt Powerpoint Presentation Summary Mockup Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Pros Cons Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Technologies Used Cyber Security Ppt Powerpoint Presentation Professional Skills Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Technologies Used Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Offensive Defensive Cyber Security Ppt Powerpoint Presentation Visual Aids Slides Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Offensive Defensive Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Templates act as productivity boosters as they help in getting more work done in a lesser time frame. They are also great design frameworks with everything pre designed. This An Open Door With Hands Holding Guns Surrounded By Words Like Cyber Crime Stolen Identity Virus Phishing Security is one such layout that can help you meet your goals and expectations in no time. It will provide you with great design elements that are suitable for any scenario consulting marketing sales personal agenda or any other. Not only this but this template layout will help you navigate the most important ideas and streamline your way of presenting. With everything pre laden and fully equipped this design is an absolute steal. The high resolution graphics and images used will empower your message and catch the audiences attention in minutes thereby helping you deliver inspiring presentations. The biggest advantage of this template is that it can be manipulated as per your business understanding. So feel free to adjust it to your terms and conditions once you click on the download button.
Presenting this set of slides with name Control System Cyber Security Ppt Powerpoint Presentation Portfolio Example Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Control System Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Presenting this set of slides with name Cyber Security Industrial Control Ppt Powerpoint Presentation Slides Influencers Cpb. This is an editable Powerpoint seven stages graphic that deals with topics like Cyber Security Industrial Control to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Cyber Security Audit Checklist Ppt Powerpoint Presentation Gallery Visual Aids Cpb. This is an editable Powerpoint two stages graphic that deals with topics like Cyber Security Audit Checklist to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Cyber Security Dashboard Template Ppt Powerpoint Presentation Infographics Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Dashboard Template to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Cyber Security Issues Business Ppt Powerpoint Presentation Model Slide Portrait. This is an editable Powerpoint five stages graphic that deals with topics like Cyber Security Issues Business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Presenting this set of slides with name Threat Intelligence Cyber Security Ppt Powerpoint Presentation Layouts Show Cpb. This is an editable Powerpoint seven stages graphic that deals with topics like Threat Intelligence Cyber Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Presenting this set of slides with name Small Business Cyber Security Statistics Ppt Powerpoint Presentation Example Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Small Business Cyber Security Statistics to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Presenting this set of slides with name Cyber Security Logo With Gear Wheel. This is a three stage process. The stages in this process are Cyber Security Logo With Gear Wheel. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
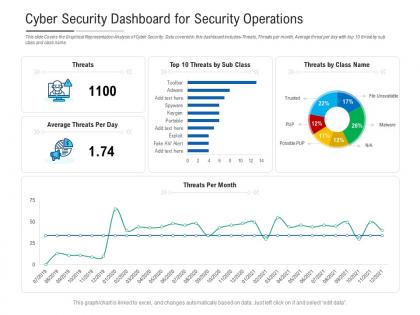
This slide Covers the Graphical Representation Analysis of Cyber Security. Data covered in this dashboard snapshot includes Threats, Threats per month, Average threat per day with top 10 threat by sub class and class name. This is a Cyber Security Dashboard Snapshot For Security Operations Powerpoint Template drafted with a diverse set of graphics, that can be reformulated and edited as per your needs and requirements. Just download it in your system and make use of it in PowerPoint or Google Slides, depending upon your presentation preferences.
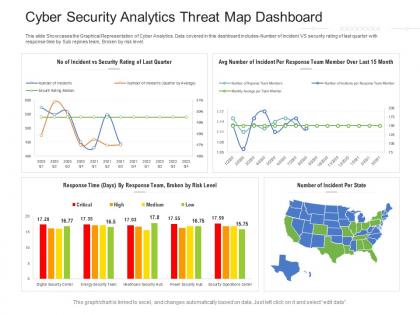
This slide Showcases the Graphical Representation of Cyber Analytics. Data covered in this dashboard includes Number of incident VS security rating of last quarter with response time by Sub repines team, Broken by risk level. This is a Cyber Security Analytics Threat Map Dashboard Powerpoint Template featuring in built editable components to add your personal touches. Tailor this template as per your liking and display it on a widescreen or standard screen, the choice is yours.
Presenting our Cyber Security Education Awareness Ppt Powerpoint Presentation Portfolio Visuals Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cyber Security Education Awareness This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
Presenting Cyber Security Vs Data Science Ppt Powerpoint Presentation Styles Backgrounds Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Vs Data Science. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
This is our 8 Steps Circle Of Internal Audit And Cyber Security Infographic Template designed in PowerPoint, however, you can also access it in Google Slides. It comes in two aspect ratios standard and widescreen, with fully editable visual content.

Presenting our well-structured Government Web Portal For Citizens Services. The topics discussed in this slide are Government Web Portal For Citizens Services. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
Presenting our set of slides with Shopping Web Portal For Online Purchases. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Shopping Web Portal For Online Purchases.
Presenting our set of slides with Web Portal For Providing Job Vacancies Alerts. This exhibits information on two stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Portal For Providing Job Vacancies Alerts.
Introducing our premium set of slides with Web Portal Requires Username And Password For Login. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Web Portal Requires Username And Password For Login. So download instantly and tailor it with your information.
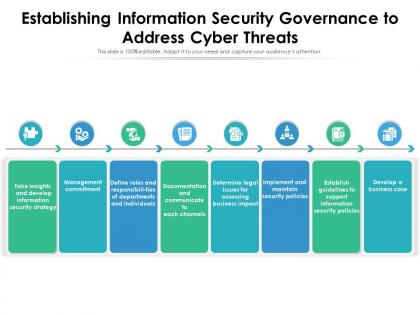
Introducing our premium set of slides with name Establishing Information Security Governance To Address Cyber Threats. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Management Commitment, Documentation And Communicate, Develop A Business Case, Implement And Maintain Security Policies, Security Strategy. So download instantly and tailor it with your information.
Presenting Data Science Cyber Security Ppt Powerpoint Presentation Outline Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Science Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting Data Science Cyber Security Ppt Powerpoint Presentation Slides Picture Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Science Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.

Presenting our Cyber Security Deep Learning Ppt Powerpoint Presentation Portfolio Model Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Deep Learning This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
Presenting Cyber Security Financial Services Ppt Powerpoint Presentation Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Financial Services. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting Cyber Security Team Ppt Powerpoint Presentation Gallery Show Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase eight stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Team. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting Aviation Cyber Security Ppt Powerpoint Presentation Icon Images Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Aviation Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
Presenting our Cyber Security Organizational Structure Ppt Powerpoint Presentation Ideas Visual Aids Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Organizational Structure This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
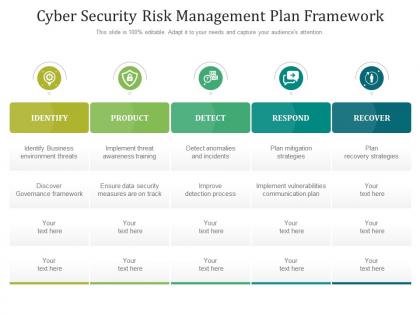
Introducing our Cyber Security Risk Management Plan Framework set of slides. The topics discussed in these slides are Management, Framework, Business. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.


IMAGES
VIDEO
COMMENTS
You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Security Patch Management Process Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience.
Global Data Security Encryption Cyber Security Illustration. This coloured PowerPoint Illustration provides a visually appealing representation of global data security. It is perfect for presentations and other documents to illustrate the importance of protecting data across the world. Slide 1 of 6.
Flaticon. Slidesgo. Wepik. Videvo. We assure you that your presentation will be a success thanks to these Google Slides and PPT templates on security. Free Easy to edit Professional.
This cybersecurity PPT template is a slide deck prepared using customizable elements to discuss various aspects of the importance of cybersecurity. It starts with a title slide, showing imaginative lines to represent how the devices and online surfing are secured with the cybersecurity protocols. All slides have a similar background and a ...
It has an image of a big key is the main focus of this background. 6. Cybercrime Prevention - Free Cyber Security PPT Template. If you want to create a cyber security PowerPoint strategy, this is a great option. It includes an image of a shield or security logo is part of this background.
Modern Developments in Secure Protocols. In recent years, there have been significant advancements in secure protocol technology. New protocols and standards have emerged to address the ever-evolving security threats on the internet. One notable development is the emergence of the Datagram Transport Layer Security (DTLS) protocol.
3. Antivirus and Anti-malwarе Softwarе: Antivirus and anti-malwarе softwarе dеtеct and rеmovе malicious softwarе from computеr systеms, such as virusеs, worms, and spywarе. 4. Encryption: Encryption is thе procеss of transforming data into a sеcurе form that is unrеadablе to unauthorizеd individuals. 5.
Modelling and Analysing of Security Protocol: Lecture 1. Introductions to Modelling Protocols. Tom Chothia. CWI. This Course This course will primarily teaching you: How to design your own secure communication protocols. How to analyse protocols and look for faults. How to use automatic tools to help you do this.
Slide 1: Get started. Slide 1 is designed to be the call-to-attention slide. It needs to be sparse and simply identify the topics you'll cover in the following slides. It should signal that the presentation will include information about business execution, strategy, external developments and risk position, and set the scene at a high level.
Chapter 11Security Protocols Network Security Threats. Network Security • The combination of low-cost powerful computing and high-performance networks is a two-edged sword: • Many powerful new services and applications are enabled • But computer systems and networks become highly susceptible to a wide variety of security threats ...
Below you'll see thumbnail sized previews of the title slides of a few of our 105 best network security templates for PowerPoint and Google Slides. The text you'll see in in those slides is just example text. The network security-related image or video you'll see in the background of each title slide is designed to help you set the stage ...
Network security protocols.pptx. Nov 26, 2023 •. 1 like • 38 views. S. SamyLacheheub. A presentation includes all network security protocols and the threats on our network. Data & Analytics. 1 of 19. Network security protocols.pptx - Download as a PDF or view online for free.
A well-designed incident response plan can be the crucial differentiator that enables an organization to quickly contain the damage from an incident and rapidly recover normal business operations. Companies developing their incident response plans should follow these steps. Step 1. Create a policy.
6 Types of Network Security Protocols. Network protocols are used to carry different types of data over the network. For example, HTTP is used for web traffic, while DNS is used to convert domain names to IP addresses. However, many of the network protocols used by the modern Internet are insecure, lacking encryption, authentication, or data ...
Security Protocols that Protect the Presentation Layer Data encryption and decryption happen at the presentation layer, making sure the recipient can access and use the information. Because of its importance, there are various types of cyber-attacks that seek to compromise the security and privacy of the data before it gets encrypted.
Template 1: Complete Network Security. Enhance your network security strategy with our comprehensive Network Security PowerPoint Presentation Slides. This visually engaging deck covers essential topics, including risk assessment, mitigation strategies, benefits of network security, and automation's role. It provides a checklist, a 30-60-90-day ...
Internet Security Protocols Chapters 5. Outline • Security protocols at various layers (esp., L2TP) • IP Security protocol (IPsec). Security protocolsfor the TCP/IP networks • To provide security over a network connection, typically cryptographical mechanisms are applied. • When data (d) is sent from the sender (S) to the receiver (R), the following must be provided ...
Presentation Transcript. CS 155 May 26, 2005 Security Protocols John Mitchell. Topics • Application layer protocols (review) • Kerberos, SSL/TLS • Network layer security • IPsec Some details: key management techniques • 802.11 • Mobility • Secure network infrastructure • DNSsec • Sender authentication for spam prevention ...
Maryam Nawaz, the Chief Minister of Pakistan's Punjab province,on Friday said that Chinese nationals living in Pakistan get "resentful" when they are asked to follow security protocols.
Presentation Transcript. Security Protocols. What We Know • A bit about the history of cryptography • The key distribution problem • Distinction between symmetric and public key cryptography • Some basic and not-so-basic symmetric schemes • Lots of number theory • A little about pseudo-random number generation • Several public key ...
Presenting this set of slides with name Mode Of Communication For Cyber Security Services Ppt Powerpoint Presentation Styles. The topics discussed in these slides are Communicate Medium, Review Sessions, Emails, Description. This is a completely editable PowerPoint presentation and is available for immediate download.