Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 17 May 2023

A holistic and proactive approach to forecasting cyber threats
- Zaid Almahmoud 1 ,
- Paul D. Yoo 1 ,
- Omar Alhussein 2 ,
- Ilyas Farhat 3 &
- Ernesto Damiani 4 , 5
Scientific Reports volume 13 , Article number: 8049 ( 2023 ) Cite this article
5089 Accesses
6 Citations
2 Altmetric
Metrics details
- Computer science
- Information technology
Traditionally, cyber-attack detection relies on reactive, assistive techniques, where pattern-matching algorithms help human experts to scan system logs and network traffic for known virus or malware signatures. Recent research has introduced effective Machine Learning (ML) models for cyber-attack detection, promising to automate the task of detecting, tracking and blocking malware and intruders. Much less effort has been devoted to cyber-attack prediction, especially beyond the short-term time scale of hours and days. Approaches that can forecast attacks likely to happen in the longer term are desirable, as this gives defenders more time to develop and share defensive actions and tools. Today, long-term predictions of attack waves are mostly based on the subjective perceptiveness of experienced human experts, which can be impaired by the scarcity of cyber-security expertise. This paper introduces a novel ML-based approach that leverages unstructured big data and logs to forecast the trend of cyber-attacks at a large scale, years in advance. To this end, we put forward a framework that utilises a monthly dataset of major cyber incidents in 36 countries over the past 11 years, with new features extracted from three major categories of big data sources, namely the scientific research literature, news, blogs, and tweets. Our framework not only identifies future attack trends in an automated fashion, but also generates a threat cycle that drills down into five key phases that constitute the life cycle of all 42 known cyber threats.
Similar content being viewed by others
Knowledge mining of unstructured information: application to cyber domain
Machine learning partners in criminal networks
A novel hybrid feature selection and ensemble-based machine learning approach for botnet detection
Introduction.
Running a global technology infrastructure in an increasingly de-globalised world raises unprecedented security issues. In the past decade, we have witnessed waves of cyber-attacks that caused major damage to governments, organisations and enterprises, affecting their bottom lines 1 . Nevertheless, cyber-defences remained reactive in nature, involving significant overhead in terms of execution time. This latency is due to the complex pattern-matching operations required to identify the signatures of polymorphic malware 2 , which shows different behaviour each time it is run. More recently, ML-based models were introduced relying on anomaly detection algorithms. Although these models have shown a good capability to detect unknown attacks, they may classify benign behaviour as abnormal 3 , giving rise to a false alarm.
We argue that data availability can enable a proactive defense, acting before a potential threat escalates into an actual incident. Concerning non-cyber threats, including terrorism and military attacks, proactive approaches alleviate, delay, and even prevent incidents from arising in the first place. Massive software programs are available to assess the intention, potential damages, attack methods, and alternative options for a terrorist attack 4 . We claim that cyber-attacks should be no exception, and that nowadays we have the capabilities to carry out proactive, low latency cyber-defenses based on ML 5 .
Indeed, ML models can provide accurate and reliable forecasts. For example, ML models such as AlphaFold2 6 and RoseTTAFold 7 can predict a protein’s three-dimensional structure from its linear sequence. Cyber-security data, however, poses its unique challenges. Cyber-incidents are highly sensitive events and are usually kept confidential since they affect the involved organisations’ reputation. It is often difficult to keep track of these incidents, because they can go unnoticed even by the victim. It is also worth mentioning that pre-processing cyber-security data is challenging, due to characteristics such as lack of structure, diversity in format, and high rates of missing values which distort the findings.
When devising a ML-based method, one can rely on manual feature identification and engineering, or try and learn the features from raw data. In the context of cyber-incidents, there are many factors ( i.e. , potential features) that could lead to the occurrence of an attack. Wars and political conflicts between countries often lead to cyber-warfare 8 , 9 . The number of mentions of a certain attack appearing in scientific articles may correlate well with the actual incident rate. Also, cyber-attacks often take place on holidays, anniversaries and other politically significant dates 5 . Finding the right features out of unstructured big data is one of the key strands of our proposed framework.
The remainder of the paper is structured as follows. The “ Literature review ” section presents an overview of the related work and highlights the research gaps and our contributions. The “ Methods ” section describes the framework design, including the construction of the dataset and the building of the model. The “ Results ” section presents the validation results of our model, the trend analysis and forecast, and a detailed description of the developed threat cycle. Lastly, the “ Discussion ” section offers a critical evaluation of our work, highlighting its strengths and limitations, and provides recommendations for future research.
Literature review
In recent years, the literature has extensively covered different cyber threats across various application domains, and researchers have proposed several solutions to mitigate these threats. In the Social Internet of Vehicles (SIoV), one of the primary concerns is the interception and tampering of sensitive information by attackers 10 . To address this, a secure authentication protocol has been proposed that utilises confidential computing environments to ensure the privacy of vehicle-generated data. Another application domain that has been studied is the privacy of image data, specifically lane images in rural areas 11 . The proposed methodology uses Error Level Analysis (ELA) and artificial neural network (ANN) algorithms to classify lane images as genuine or fake, with the U-Net model for lane detection in bona fide images. The final images are secured using the proxy re-encryption technique with RSA and ECC algorithms, and maintained using fog computing to protect against forgery.
Another application domain that has been studied is the security of Wireless Mesh Networks (WMNs) in the context of the Internet of Things (IoT) 12 . WMNs rely on cooperative forwarding, making them vulnerable to various attacks, including packet drop/modification, badmouthing, on-off, and collusion attacks. To address this, a novel trust mechanism framework has been proposed that differentiates between legitimate and malicious nodes using direct and indirect trust computation. The framework utilises a two-hop mechanism to observe the packet forwarding behaviour of neighbours, and a weighted D-S theory to aggregate recommendations from different nodes. While these solutions have shown promising results in addressing cyber threats, it is important to anticipate the type of threat that may arise to ensure that the solutions can be effectively deployed. By proactively identifying and anticipating cyber threats, organisations can better prepare themselves to protect their systems and data from potential attacks.
While we are relatively successful in detecting and classifying cyber-attacks when they occur 13 , 14 , 15 , there has been a much more limited success in predicting them. Some studies exist on short-term predictive capability 16 , 17 , 18 , 19 , 20 , 21 , 22 , 23 , 24 , 25 , 26 , such as predicting the number or source of attacks to be expected in the next hours or days. The majority of this work performs the prediction in restricted settings ( e.g. , against a specific entity or organisation) where historical data are available 18 , 19 , 25 . Forecasting attack occurrences has been attempted by using statistical methods, especially when parametric data distributions could be assumed 16 , 17 , as well as by using ML models 20 . Other methods adopt a Bayesian setting and build event graphs suitable for estimating the conditional probability of an attack following a given chain of events 21 . Such techniques rely on libraries of predefined attack graphs: they can identify the known attack most likely to happen, but are helpless against never-experienced-before, zero-day attacks.
Other approaches try to identify potential attackers by using network entity reputation and scoring 26 . A small but growing body of research explores the fusion of heterogeneous features (warning signals) to forecast cyber-threats using ML. Warning signs may include the number of mentions of a victim organisation on Twitter 18 , mentions in news articles about the victim entity 19 , and digital traces from dark web hacker forums 20 . Our literature review is summarised in Table 1 .
Forecasting the cyber-threats that will most likely turn into attacks in the medium and long term is of significant importance. It not only gives to cyber-security agencies the time to evaluate the existing defence measures, but also assists them in identifying areas where to develop preventive solutions. Long-term prediction of cyber-threats, however, still relies on the subjective perceptions of human security experts 27 , 28 . Unlike a fully automated procedure based on quantitative metrics, the human-based approach is prone to bias based on scientific or technical interests 29 . Also, quantitative predictions are crucial to scientific objectivity 30 . In summary, we highlight the following research gaps:
Current research primarily focuses on detecting ( i.e. , reactive) rather than predicting cyber-attacks ( i.e. , proactive).
Available predictive methods for cyber-attacks are mostly limited to short-term predictions.
Current predictive methods for cyber-attacks are limited to restricted settings ( e.g. , a particular network or system).
Long-term prediction of cyber-attacks is currently performed by human experts, whose judgement is subjective and prone to bias and disagreement.
Research contributions
Our objective is to fill these research gaps by a proactive, long-term, and holistic approach to attack prediction. The proposed framework gives cyber-security agencies sufficient time to evaluate existing defence measures while also providing objective and accurate representation of the forecast. Our study is aimed at predicting the trend of cyber-attacks up to three years in advance, utilising big data sources and ML techniques. Our ML models are learned from heterogeneous features extracted from massive, unstructured data sources, namely, Hackmageddon 9 , Elsevier 31 , Twitter 32 , and Python APIs 33 . Hackmageddon provides more than 15, 000 records of global cyber-incidents since the year 2011, while Elsevier API offers access to the Scopus database, the largest abstract and citation database of peer-reviewed literature with over 27,000,000 documents 34 . The number of relevant tweets we collected is around 9 million. Our study covers 36 countries and 42 major attack types. The proposed framework not only provides the forecast and categorisation of the threats, but also generates a threat life-cycle model, whose the five key phases underlie the life cycle of all 42 known cyber-threats. The key contribution of this study consists of the following:
A novel dataset is constructed using big unstructured data ( i.e. , Hackmageddon) including news and government advisories, in addition to Elsevier, Twitter, and Python API. The dataset comprises monthly counts of cyber-attacks and other unique features, covering 42 attack types across 36 countries.
Our proactive approach offers long-term forecasting by predicting threats up to 3 years in advance.
Our approach is holistic in nature, as it does not limit itself to specific entities or regions. Instead, it provides projections of attacks across 36 countries situated in diverse parts of the world.
Our approach is completely automated and quantitative, effectively addressing the issue of bias in human predictions and providing a precise forecast.
By analysing past and predicted future data, we have classified threats into four main groups and provided a forecast of 42 attacks until 2025.
The first threat cycle is proposed, which delineates the distinct phases in the life cycle of 42 cyber-attack types.
The framework of forecasting cyber threats
The architecture of our framework for forecasting cyber threats is illustrated in Fig. 1 . As seen in the Data Sources component (l.h.s), to harness all the relevant data and extract meaningful insights, our framework utilises various sources of unstructured data. One of our main sources is Hackmageddon, which includes massive textual data on major cyber-attacks (approx. 15,334 incidents) dating back to July 2011. We refer to the monthly number of attacks in the list as the Number of Incidents (NoI). Also, Elsevier’s Application Programming Interface (API) gives access to a very large corpus of scientific articles and data sets from thousands of sources. Utilising this API, we obtained the Number of Mentions (NoM) ( e.g. , monthly) of each attack that appeared in the scientific publications. This NoM data is of particular importance as it can be used as the ground truth for attack types that do not appear in Hackmageddon. During the preliminary research phase, we examined all the potentially relevant features and noticed that wars/political conflicts are highly correlated to the number of cyber-events. These data were then extracted via Twitter API as Armed Conflict Areas/Wars (ACA). Lastly, as attacks often take place around holidays, Python’s holidays package was used to obtain the number of public holidays per month for each country, which is referred to as Public Holidays (PH).
To ensure the accuracy and quality of Hackmageddon data, we validated it using the statistics from official sources across government, academia, research institutes and technology organisations. For a ransomware example, the Cybersecurity & Infrastructure Security Agency stated in their 2021 trend report that cybersecurity authorities in the United States, Australia, and the United Kingdom observed an increase in sophisticated, high-impact ransomware incidents against critical infrastructure organisations globally 35 . The WannaCry attack in the dataset was also validated with Ghafur et al ’s 1 statement in their article: “WannaCry ransomware attack was a global epidemic that took place in May 2017”.
An example of an entry in the Hackmageddon dataset is shown in Table 2 . Each entry includes the incident date, the description of the attack, the attack type, and the target country. Data pre-processing (Fig. 1 ) focused on noise reduction through imputing missing values ( e.g. , countries), which were often observed in the earlier years. We were able to impute these values from the description column or occasionally, by looking up the entity location using Google.
The textual data were quantified via our Word Frequency Counter (WFC), which counted the number of each attack type per month as in Table 3 . Cumulative Aggregation (CA) obtained the number of attacks for all countries combined and an example of a data entry after transformation includes the month, and the number of attacks against each country (and all countries combined) for each attack type. By adding features such as NoM, ACA, and PH, we ended up having additional features that we appended to the dataset as shown in Table 4 . Our final dataset covers 42 common types of attacks in 36 countries. The full list of attacks is provided in Table 5 . The list of the countries is given in Supplementary Table S1 .
To analyse and investigate the main characteristics of our data, an exploratory analysis was conducted focusing on the visualisation and identification of key patterns such as trend and seasonality, correlated features, missing data and outliers. For seasonal data, we smoothed out the seasonality so that we could identify the trend while removing the noise in the time series 36 . The smoothing type and constants were optimised along with the ML model (see Optimisation for details). We applied Stochastic selection of Features (SoF) to find the subset of features that minimises the prediction error, and compared the univariate against the multivariate approach.
For the modelling, we built a Bayesian encoder-decoder Long Short-Term Memory (B-LSTM) network. B-LSTM models have been proposed to predict “perfect wave” events like the onset of stock market “bear” periods on the basis of multiple warning signs, each having different time dynamics 37 . Encoder-decoder architectures can manage inputs and outputs that both consist of variable-length sequences. The encoder stage encodes a sequence into a fixed-length vector representation (known as the latent representation). The decoder prompts the latent representation to predict a sequence. By applying an efficient latent representation, we train the model to consider all the useful warning information from the input sequence - regardless of its position - and disregard the noise.
Our Bayesian variation of the encoder-decoder LSTM network considers the weights of the model as random variables. This way, we extract epistemic uncertainty via (approximate) Bayesian inference, which quantifies the prediction error due to insufficient information 38 . This is an important parameter, as epistemic uncertainty can be reduced by better intelligence, i.e. , by acquiring more samples and new informative features. Details are provided in “ Bayesian long short-term memory ” section.
Our overall analytical platform learns an operational model for each attack type. Here, we evaluated the model’s performance in predicting the threat trend 36 months in advance. A newly modified symmetric Mean Absolute Percentage Error (M-SMAPE) was devised as the evaluation metric, where we added a penalty term that accounts for the trend direction. More details are provided in the “ Evaluation metrics ” section.
Feature extraction
Below, we provide the details of the process that transforms raw data into numerical features, obtaining the ground truth NoI and the additional features NoM, ACA and PH.
NoI: The number of daily incidents in Hackmageddon was transformed from the purely unstructured daily description of attacks along with the attack and country columns, to the monthly count of incidents for each attack in each country. Within the description, multiple related attacks may appear, which are not necessarily in the attack column. Let \(E_{x_i}\) denote the set of entries during the month \(x_i\) in Hackmageddon dataset. Let \(a_j\) and \(c_k\) denote the j th attack and k th country. Then NoI can be expressed as follows:
where \(Z(a_j,c_k,e)\) is a function that evaluates to 1 if \(a_j\) appears either in the description or in the attack columns of entry e and \(c_k\) appears in the country column of e . Otherwise, the function evaluates to 0. Next, we performed CA to obtain the monthly count of attacks in all countries combined for each attack type as follows:
NoM: We wrote a Python script to query Elsevier API for the number of mentions of each attack during each month 31 . The search covers the title, abstract and keywords of published research papers that are stored in Scopus database 39 . Let \(P_{x_i}\) denote the set of research papers in Scopus published during the month \(x_i\) . Also, let \(W_{p}\) denote the set of words in the title, abstract and keywords of research paper p . Then NoM can be expressed as follows:
where \(U(w,a_j)\) evaluates to 1 if \(w=a_j\) , and to 0 otherwise.
ACA: Using Twitter API in Python 32 , we wrote a query to obtain the number of tweets with keywords related to political conflicts or military attacks associated with each country during each month. The keywords used for each country are summarised in Supplementary Table S2 , representing our query. Formally, let \(T_{x_i}\) denote the set of all tweets during the month \(x_i\) . Then ACA can be expressed as follows:
where \(Q(t,c_k)\) evaluates to 1 if the query in Supplementary Table S2 evaluates to 1 given t and \(c_k\) . Otherwise, it evaluates to 0.
PH: We used the Python holidays library 33 to count the number of days that are considered public holidays in each country during each month. More formally, this can be expressed as follows:
where \(H(d,c_k)\) evaluates to 1 if the day d in the country \(c_k\) is a public holiday, and to 0 otherwise. In ( 4 ) and ( 5 ), CA was used to obtain the count for all countries combined as in ( 2 ).
Data integration
Based on Eqs. ( 1 )–( 5 ), we obtain the following columns for each month:
NoI_C: The number of incidents for each attack type in each country ( \(42 \times 36\) columns) [Hackmageddon].
NoI: The total number of incidents for each attack type (42 columns) [Hackmageddon].
NoM: The number of mentions of each attack type in research articles (42 columns) [Elsevier].
ACA_C: The number of tweets about wars and conflicts related to each country (36 columns) [Twitter].
ACA: The total number of tweets about wars and conflicts (1 column) [Twitter].
PH_C: The number of public holidays in each country (36 columns) [Python].
PH: The total number of public holidays (1 column) [Python].
In the aforementioned list of columns, the name enclosed within square brackets denotes the source of data. By matching and combining these columns, we derive our monthly dataset, wherein each row represents a distinct month. A concrete example can be found in Tables 3 and 4 , which, taken together, constitute a single observation in our dataset. The dataset can be expanded through the inclusion of other monthly features as supplementary columns. Additionally, the dataset may be augmented with further samples as additional monthly records become available. Some suggestions for extending the dataset are provided in the “ Discussion ” section.
Data smoothing
We tested multiple smoothing methods and selected the one that resulted in the model with the lowest M-SMAPE during the hyper-parameter optimisation process. The methods we tested include exponential smoothing (ES), double exponential smoothing (DES) and no smoothing (NS). Let \(\alpha \) be the smoothing constant. Then the ES formula is:
where \(D(x_{i})\) denotes the original data at month \(x_{i}\) . For the DES formula, let \(\alpha \) and \(\beta \) be the smoothing constants. We first define the level \(l(x_{i})\) and the trend \(\tau (x_{i})\) as follows:
then, DES is expressed as follows:
The smoothing constants ( \(\alpha \) and \(\beta \) ) in the aforementioned methods are chosen as the predictive results of the ML model that gives the lowest M-SMAPE during the hyper-parameter optimisation process. Supplementary Fig. S5 depicts an example for the DES result.
Bayesian long short-term memory
LSTM is a type of recurrent neural network (RNN) that uses lagged observations to forecast the future time steps 30 . It was introduced as a solution to the so-called vanishing/exploding gradient problem of traditional RNNs 40 , where the partial derivative of the loss function may suddenly approach zero at some point of the training. In LSTM, the input is passed to the network cell, which combines it with the hidden state and cell state values from previous time steps to produce the next states. The hidden state can be thought of as a short-term memory since it stores information from recent periods in a weighted manner. On the other hand, the cell state is meant to remember all the past information from previous intervals and store them in the LSTM cell. The cell state thus represents the long-term memory.
LSTM networks are well-suited for time-series forecasting, due to their proficiency in retaining both long-term and short-term temporal dependencies 41 , 42 . By leveraging their ability to capture these dependencies within cyber-attack data, LSTM networks can effectively recognise recurring patterns in the attack time-series. Moreover, the LSTM model is capable of learning intricate temporal patterns in the data and can uncover inter-correlations between various variables, making it a compelling option for multivariate time-series analysis 43 .
Given a sequence of LSTM cells, each processing a single time-step from the past, the final hidden state is encoded into a fixed-length vector. Then, a decoder uses this vector to forecast future values. Using such architecture, we can map a sequence of time steps to another sequence of time steps, where the number of steps in each sequence can be set as needed. This technique is referred to as encoder-decoder architecture.
Because we have relatively short sequences within our refined data ( e.g. , 129 monthly data points over the period from July 2011 to March 2022), it is crucial to extract the source of uncertainty, known as epistemic uncertainty 44 , which is caused by lack of knowledge. In principle, epistemic uncertainty can be reduced with more knowledge either in the form of new features or more samples. Deterministic (non-stochastic) neural network models are not adequate to this task as they provide point estimates of model parameters. Rather, we utilise a Bayesian framework to capture epistemic uncertainty. Namely, we adopt the Monte Carlo dropout method proposed by Gal et al. 45 , who showed that the use of non-random dropout neurons during ML training (and inference) provides a Bayesian approximation of the deep Gaussian processes. Specifically, during the training of our LSTM encoder-decoder network, we applied the same dropout mask at every time-step (rather than applying a dropout mask randomly from time-step to time-step). This technique, known as recurrent dropout is readily available in Keras 46 . During the inference phase, we run trained model multiple times with recurrent dropout to produce a distribution of predictive results. Such prediction is shown in Fig. 4 .
Figure 2 shows our encoder-decoder B-LSTM architecture. The hidden state and cell state are denoted respectively by \(h_{i}\) and \(C_{i}\) , while the input is denoted by \(X_{i}\) . Here, the length of the input sequence (lag) is a hyper-parameter tuned to produce the optimal model, where the output is a single time-step. The number of cells ( i.e. , the depth of each layer) is tuned as a hyper-parameter in the range between 25 and 200 cells. Moreover, we used one or two layers, tuning the number of layers to each attack type. For the univariate model we used a standard Rectified Linear Unit (ReLU) activation function, while for the multivariate model we used a Leaky ReLU. Standard ReLU computes the function \(f(x)=max(0,x)\) , thresholding the activation at zero. In the multivariate case, zero-thresholding may generate the same ReLU output for many input vectors, making the model convergence slower 47 . With Leaky ReLU, instead of defining ReLU as zero when \(x < 0\) , we introduce a negative slope \(\alpha =0.2\) . Additionally, we used recurrent dropout ( i.e. , arrows in red as shown in Fig. 2 ), where the probability of dropping out is another hyper-parameter that we tune as described above, following Gal’s method 48 . The tuned dropout value is maintained during the testing and prediction as previously mentioned. Once the final hidden vector \(h_{0}\) is produced by the encoder, the Repeat Vector layer is used as an adapter to reshape it from the bi-dimensional output of the encoder ( e.g. , \(h_{0}\) ) to the three-dimensional input expected by the decoder. The decoder processes the input and produces the hidden state, which is then passed to a dense layer to produce the final output.
Each time-step corresponds to a month in our model. Since the model is learnt to predict a single time-step (single month), we use a sliding window during the prediction phase to forecast 36 (monthly) data points. In other words, we predict a single month at each step, and the predicted value is fed back for the prediction of the following month. This concept is illustrated in the table shown in Fig. 2 . Utilising a single time-step in the model’s output minimises the size of the sliding window, which in turn allows for training with as many observations as possible with such limited data.
The difference between the univariate and multivariate B-LSTMs is that the latter carries additional features in each time-step. Thus, instead of passing a scalar input value to the network, we pass a vector of features including the ground truth at each time-step. The model predicts a vector of features as an output, from which we retrieve the ground truth, and use it along with the other predicted features as an input to predict the next time-step.
Evaluation metrics
The evaluation metric SMAPE is a percentage (or relative) error based accuracy measure that judges the prediction performance purely on how far the predicted value is from the actual value 49 . It is expressed by the following formula:
where \(F_{t}\) and \(A_{t}\) denote the predicted and actual values at time t . This metric returns a value between 0% and 100%. Given that our data has zero values in some months ( e.g. , emerging threats), the issue of division by zero may arise, a problem that often emerges when using standard MAPE (Mean Absolute Percentage Error). We find SMAPE to be resilient to this problem, since it has both the actual and predicted values in the denominator.
Recall that our model aims to predict a curve (corresponding to multiple time steps). Using plain SMAPE as the evaluation metric, the “best” model may turn out to be simply a straight line passing through the same points of the fluctuating actual curve. However, this is undesired in our case since our priority is to predict the trend direction (or slope) over its intensity or value at a certain point. We hence add a penalty term to SMAPE that we apply when the height of the predicted curve is relatively smaller than that of the actual curve. This yields the modified SMAPE (M-SMAPE). More formally, let I ( V ) be the height of the curve V , calculated as follows:
where n is the curve width or the number of data points. Let A and F denote the actual and predicted curves. We define M-SMAPE as follows:
where \(\gamma \) is a penalty constant between 0 and 1, and d is another constant \(\ge \) 1. In our experiment, we set \(\gamma \) to 0.3, and d to 3, as we found these to be reasonable values by trial and error. We note that the range of possible values of M-SMAPE is between 0% and (100 + 100 \(\gamma \) )% after this modification. By running multiple experiments we found out that the modified evaluation metric is more suitable for our scenario, and therefore was adopted for the model’s evaluation.
Optimisation
On average, our model was trained on around 67% of the refined data, which is equivalent to approximately 7.2 years. We kept the rest, approximately 33% (3 years + lag period), for validation. These percentages may slightly differ for different attack types depending on the optimal lag period selected.
For hyper-parameter optimisation, we performed a random search with 60 iterations, to obtain the set of features, smoothing methods and constants, and model’s hyper-parameters that results in the model with the lowest M-SMAPE. Random search is a simple and efficient technique for hyper-parameter optimisation, with advantages including efficiency, flexibility, robustness, and scalability. The technique has been studied extensively in the literature and was found to be superior to grid search in many cases 50 . For each set of hyper-parameters, the model was trained using the mean squared error (MSE) as the loss function, and while using ADAM as the optimisation algorithm 51 . Then, the model was validated by forecasting 3 years while using M-SMAPE as the evaluation metric, and the average performance was recorded over 3 different seeds. Once the set of hyper-parameters with the minimum M-SMAPE was obtained, we used it to train the model on the full data, after which we predicted the trend for the next 3 years (until March, 2025).
The first group of hyper-parameters is the subset of features in the case of the multivariate model. Here, we experimented with each of the 3 features separately (NoM, ACA or PH) along with the ground truth (NoI), in addition to the combination of all features. The second group is the smoothing methods and constants. The set of methods includes ES, DES and NS, as previously discussed. The set of values for the smoothing constant \(\alpha \) ranges from 0.05 to 0.7 while the set of values for the smoothing constant \(\beta \) (for DES) ranges from 0.3 to 0.7. Next is the optimisation of the lag period with values that range from 1 to 12 months. This is followed by the model’s hyper-parameters which include the learning rate with values that range from \(6\times 10^{-4}\) to \(1\times 10^{-2}\) , the number of epochs with values between 30 and 200, the number of layers in the range 1 to 2, the number of units in the range 25 to 200, and the recurrent dropout value between 0.2 and 0.5. The range of these values was obtained from the literature and the online code repositories 52 .
Validation and comparative analysis
The results of our model’s validation are provided in Fig. 3 and Table 5 . As shown in Fig. 3 , the predicted data points are well aligned with the ground truth. Our models successfully predicted the next 36 months of all the attacks’ trends with an average M-SMAPE of 0.25. Table 5 summarises the validation results of univariate and multivariate approaches using B-LSTM. The results show that with approximately 69% of all the attack types, the multivariate approach outperformed the univariate approach. As seen in Fig. 3 , the threats that have a consistent increasing or emerging trend seemed to be more suitable for the univariate approach, while threats that have a fluctuating or decreasing trend showed less validation error when using the multivariate approach. The feature of ACA resulted in the best model for 33% of all the attack types, which makes it among the three most informative features that can boost the prediction performance. The PH accounts for 17% of all the attacks followed by NoM that accounts for 12%.
We additionally compared the performance of the proposed model B-LSTM with other models namely LSTM and ARIMA. The comparison covers the univariate and multivariate approaches of LSTM and B-LSTM, with two features in the case of multivariate approach namely NoI and NoM. The comparison is in terms of the Mean Absolute Percentage Error (MAPE) when predicting four common attack types, namely DDoS, Password Attack, Malware, and Ransomware. A comparison table is provided in Supplementary Table S3 . The results illustrate the superiority of the B-LSTM model for most of the attack types.
Trends analysis
The forecast of each attack trend until the end of the first quarter of 2025 is given in Supplementary Figs. S1 – S4 . By visualising the historical data of each attack as well as the prediction for the next three years, we were able to analyse the overall trend of each attack. The attacks generally follow 4 types of trends: (1) rapidly increasing, (2) overall increasing, (3) emerging and (4) decreasing. The names of attacks for each category are provided in Fig. 4 .
The first trend category is the rapidly increasing trend (Fig. 4 a—approximately 40% of the attacks belong to this trend. We can see that the attacks belonging to this category have increased dramatically over the past 11 years. Based on the model’s prediction, some of these attacks will exhibit a steep growth until 2025. Examples include session hijacking, supply chain, account hijacking, zero-day and botnet. Some of the attacks under this category have reached their peak, have recently started stabilising, and will probably remain steady over the next 3 years. Examples include malware, targeted attack, dropper and brute force attack. Some attacks in this category, after a recent increase, are likely to level off in the next coming years. These are password attack, DNS spoofing and vulnerability-related attacks.
The second trend category is the overall increasing trend as seen in Fig. 4 b. Approximately 31% of the attacks seem to follow this trend. The attacks under this category have a slower rate of increase over the years compared to the attacks in the first category, with occasional fluctuations as can be observed in the figure. Although some of the attacks show a slight recent decline ( e.g. , malvertising, keylogger and URL manipulation), malvertising and keylogger are likely to recover and return to a steady state while URL manipulation is projected to continue a smooth decline. Other attacks typical of “cold” cyber-warfare like Advanced Persistent Threats (APT) and rootkits are already recovering from a small drop and will likely to rise to a steady state by 2025. Spyware and data breach have already reached their peak and are predicted to decline in the near future.
Next is the emerging trend as shown in Fig. 4 c. These are the attacks that started to grow significantly after the year 2016, although many of them existed much earlier. In our study, around 17% of the attacks follow this trend. Some attacks have been growing steeply and are predicted to continue this trend until 2025. These are Internet of Things (IoT) device attack and deepfake. Other attacks have also been increasing rapidly since 2016, however, are likely to slow down after 2022. These include ransomware and adversarial attacks. Interestingly, some attacks that emerged after 2016 have already reached the peak and recently started a slight decline ( e.g. , cryptojacking and WannaCry ransomware attack). It is likely that WannaCry will become relatively steady in the coming years, however, cryptojacking will probably continue to decline until 2025 thanks to the rise of proof-of-stake consensus mechanisms 53 .
The fourth and last trend category is the decreasing trend (Fig. 4 d—only 12% of the attacks follow this trend. Some attacks in this category peaked around 2012, and have been slowly decreasing since then ( e.g. , SQL Injection and defacement). The drive-by attack also peaked in 2012, however, had other local peaks in 2016 and 2018, after which it declined noticeably. Cross-site scripting (XSS) and pharming had their peak more recently compared to the other attacks, however, have been smoothly declining since then. All the attacks under this category are predicted to become relatively stable from 2023 onward, however, they are unlikely to disappear in the next 3 years.
The threat cycle
This large-scale analysis involving the historical data and the predictions for the next three years enables us to come up with a generalisable model that traces the evolution and adoption of the threats as they pass through successive stages. These stages are named by the launch, growth, maturity, trough and stability/decline. We refer to this model as The Threat Cycle (or TTC), which is depicted in Fig. 5 . In the launch phase, few incidents start appearing for a short period. This is followed by a sharp increase in terms of the number of incidents, growth and visibility as more and more cyber actors learn and adopt this new attack. Usually, the attacks in the launch phase are likely to have many variants as observed in the case of the WannaCry attack in 2017. At some point, the number of incidents reaches a peak where the attack enters the maturity phase, and the curve becomes steady for a while. Via the trough (when the attack experiences a slight decline as new security measures seem to be very effective), some attacks recover and adapt to the security defences, entering the slope of plateau, while others continue to smoothly decline although they do not completely disappear ( i.e. , slope of decline). It is worth noting that the speed of transition between the different phases may vary significantly between the attacks.
As seen in Fig. 5 , the attacks are placed on the cycle based on the slope of their current trend, while considering their historical trend and prediction. In the trough phase, we can see that the attacks will either follow the slope of plateau or the slope of decline. Based on the predicted trend in the blue zone in Fig. 4 , we were able to indicate the future direction for some of the attacks close to the split point of the trough using different colours (blue or red). Brute force, malvertising, the Distributed Denial-of-Service attack (DDoS), insider threat, WannaCry and phishing are denoted in blue meaning that these are likely on their way to the slope of plateau. In the first three phases, it is usually unclear and difficult to predict whether a particular attack will reach the plateau or decline, thus, denoted in grey.
There are some similarities and differences between TTC and the well-known Gartner hype cycle (GHC) 54 . A standard GHC is shown in a vanishing green colour in Fig. 5 . As TTC is specific to cyber threats, it has a much wider peak compared to GHC. Although both GHC and TTC have a trough phase, the threats decline slightly (while significant drop in GHC) as they exit their maturity phase, after which they recover and move to stability (slope of plateau) or decline.
Many of the attacks in the emerging category are observed in the growth phase. These include IoT device attack, deepfake and data poisoning. While ransomwares (except WannaCry) are in the growth phase, WannaCry already reached the trough, and is predicted to follow the slope of plateau. Adversarial attack has just entered the maturity stage, and cryptojacking is about to enter the trough. Although adversarial attack is generally regarded as a growing threat, interestingly, this machine-based prediction and introspection shows that it is maturing. The majority of the rapidly increasing threats are either in the growth or in the maturity phase. The attacks in the growth phase include session hijacking, supply chain, account hijacking, zero-day and botnet. The attacks in the maturity phase include malware, targeted attack, vulnerability-related attacks and Man-In-The-Middle attack (MITM). Some rapidly increasing attacks such as phishing, brute force, and DDoS are in the trough and are predicted to enter the stability. We also observe that most of the attacks in the category of overall increasing threats have passed the growth phase and are mostly branching to the slope of plateau or the slope of decline, while few are still in the maturity phase ( e.g. , spyware). All of the decreasing threats are on the slope of decline. These include XSS, pharming, drive-by, defacement and SQL injection.
Highlights and limitations
This study presents the development of a ML-based proactive approach for long-term prediction of cyber-attacks offering the ability to communicate effectively with the potential attacks and the relevant security measures in an early stage to plan for the future. This approach can contribute to the prevention of an incident by allowing more time to develop optimal defensive actions/tools in a contested cyberspace. Proactive approaches can also effectively reduce uncertainty when prioritising existing security measures or initiating new security solutions. We argue that cyber-security agencies should prioritise their resources to provide the best possible support in preventing fastest-growing attacks that appear in the launch phase of TTC or the attacks in the categories of the rapidly increasing or emerging trend as in Fig. 4 a and c based on the predictions in the coming years.
In addition, our fully automated approach is promising to overcome the well-known issues of human-based analysis, above all expertise scarcity. Given the absence of the possibility of analysing with human’s subjective bias while following a purely quantitative procedure and data, the resulting predictions are expected to have lower degree of subjectivity, leading to consistencies within the subject. By fully automating this analytic process, the results are reproducible and can potentially be explainable with help of the recent advancements in Explainable Artificial Intelligence.
Thanks to the massive data volume and wide geographic coverage of the data sources we utilised, this study covers every facet of today’s cyber-attack scenario. Our holistic approach performs the long-term prediction on the scale of 36 countries, and is not confined to a specific region. Indeed, cyberspace is limitless, and a cyber-attack on critical infrastructure in one country can affect the continent as a whole or even globally. We argue that our Threat Cycle (TTC) provides a sound basis to awareness of and investment in new security measures that could prevent attacks from taking place. We believe that our tool can enable a collective defence effort by sharing the long-term predictions and trend analysis generated via quantitative processes and data and furthering the analysis of its regional and global impacts.
Zero-day attacks exploit a previously unknown vulnerability before the developer has had a chance to release a patch or fix for the problem 55 . Zero-day attacks are particularly dangerous because they can be used to target even the most secure systems and go undetected for extended periods of time. As a result, these attacks can cause significant damage to an organisation’s reputation, financial well-being, and customer trust. Our approach takes the existing research on using ML in the field of zero-day attacks to another level, offering a more proactive solution. By leveraging the power of deep neural networks to analyse complex, high-dimensional data, our approach can help agencies to prepare ahead of time, in-order to prevent the zero-day attack from happening at the first place, a problem that there is no existing fix for it despite our ability to detect it. Our results in Fig. 4 a suggest that zero-day attack is likely to continue a steep growth until 2025. If we know this information, we can proactively invest on solutions to prevent it or slow down its rise in the future, since after all, the ML detection approaches may not be alone sufficient to reduce its effect.
A limitation of our approach is its reliance on a restricted dataset that encompasses data since 2011 only. This is due to the challenges we encountered in accessing confidential and sensitive information. Extending the prediction phase requires the model to make predictions further into the future, where there may be more variability and uncertainty. This could lead to a decrease in prediction accuracy, especially if the underlying data patterns change over time or if there are unforeseen external factors that affect the data. While not always the case, this uncertainty is highlighted by the results of the Bayesian model itself as it expresses this uncertainty through the increase of the confidence interval over time (Fig. 3 a and b). Despite incorporating the Bayesian model to tackle the epistemic uncertainty, our model could benefit substantially from additional data to acquire a comprehensive understanding of past patterns, ultimately improving its capacity to forecast long-term trends. Moreover, an augmented dataset would allow ample opportunity for testing, providing greater confidence in the model’s resilience and capability to generalise.
Further enhancements can be made to the dataset by including pivotal dates (such as anniversaries of political events and war declarations) as a feature, specifically those that experience a high frequency of cyber-attacks. Additionally, augmenting the dataset with digital traces that reflect the attackers’ intentions and motivations obtained from the dark web would be valuable. Other informative features could facilitate short-term prediction, specifically to forecast the on-set of each attack.
Future work
Moving forward, future research can focus on augmenting the dataset with additional samples and informative features to enhance the model’s performance and its ability to forecast the trend in the longer-term. Also, the work opens a new area of research that focuses on prognosticating the disparity between the trend of cyber-attacks and the associated technological solutions and other variables, with the aim of guiding research investment decisions. Subsequently, TTC could be improved by adopting another curve model that can visualise the current development of relevant security measures. The threat trend categories (Fig. 4 ) and TTC (Fig. 5 ) show how attacks will be visible in the next three years and more, however, we do not know where the relevant security measures will be. For example, data poisoning is an AI-targeted adversarial attack that attempts to manipulate the training dataset to control the prediction behaviour of a machine-learned model. From the scientific literature data ( e.g. , Scopus), we could analyse the published articles studying the data poisoning problem and identify the relevant keywords of these articles ( e.g. , Reject on Negative Impact (RONI) and Probability of Sufficiency (PS)). RONI and PS are typical methods used for detecting poisonous data by evaluating the effect of individual data points on the performance of the trained model. Likewise, the features that are informative, discriminating or uncertainty-reducing for knowing how the relevant security measures evolve exist within such online sources in the form of author’s keywords, number of citations, research funding, number of publications, etc .
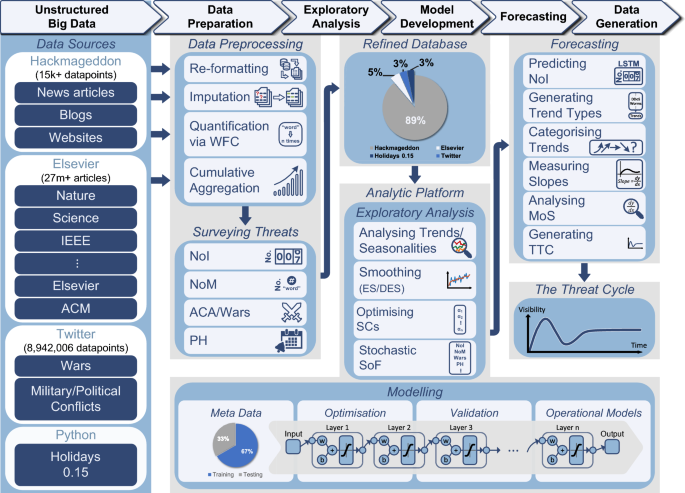
The workflow and architecture of forecasting cyber threats. The ground truth of Number of Incidents (NoI) was extracted from Hackmageddon which has over 15,000 daily records of cyber incidents worldwide over the past 11 years. Additional features were obtained including the Number of Mentions (NoM) of each attack in the scientific literature using Elsevier API which gives access to over 27 million documents. The number of tweets about Armed Conflict Areas/Wars (ACA) was also obtained using Twitter API for each country, with a total of approximately 9 million tweets. Finally, the number of Public Holidays (PH) in each country was obtained using the holidays library in Python. The data preparation phase includes data re-formatting, imputation and quantification using Word Frequency Counter (WFC) to obtain the monthly occurrence of attacks per country and Cumulative Aggregation (CA) to obtain the sum for all countries. The monthly NoM, ACA and PHs were quantified and aggregated using CA. The numerical features were then combined and stored in the refined database. The percentages in the refined database are based on the contribution of each data source. In the exploratory analysis phase, the analytic platform analyses the trend and performs data smoothing using Exponential Smoothing (ES), Double Exponential Smoothing (DES) and No Smoothing (NS). The smoothing methods and Smoothing Constants (SCs) were chosen for each attack followed by the Stochastic Selection of Features (SoF). In the model development phase, the meta data was partitioned into approximately 67% for training and 33% for testing. The models were learned using the encoder-decoder architecture of the Bayesian Long Short-Term Memory (B-LSTM). The optimisation component finds the set of hyper-parameters that minimises the error (i.e., M-SMAPE), which is then used for learning the operational models. In the forecasting phase, we used the operational models to predict the next three years’ NoIs. Analysing the predicted data, trend types were identified and attacks were categorised into four different trends. The slope of each attack was then measured and the Magnitude of Slope (MoS) was analysed. The final output is The Threat Cycle (TTC) illustrating the attacks trend, status, and direction in the next 3 years.
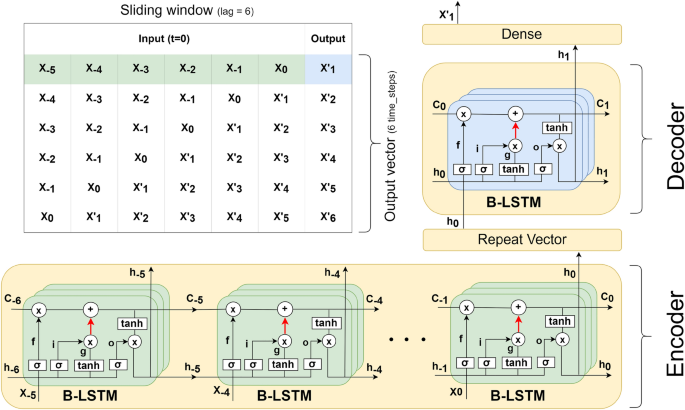
The encoder-decoder architecture of Bayesian Long Short-Term Memory (B-LSTM). \(X_{i}\) stands for the input at time-step i . \(h_{i}\) stands for the hidden state, which stores information from the recent time steps (short-term). \(C_{i}\) stands for the cell state, which stores all processed information from the past (long-term). The number of input time steps in the encoder is a variable tuned as a hyper-parameter, while the output in the decoder is a single time-step. The depth and number of layers are another set of hyper-parameters tuned during the model optimisation. The red arrows indicate a recurrent dropout maintained during the testing and prediction. The figure shows an example for an input with time lag=6 and a single layer. The final hidden state \(h_{0}\) produced by the encoder is passed to the Repeat Vector layer to convert it from 2 dimensional output to 3 dimensional input as expected by the decoder. The decoder processes the input and produces the final hidden state \(h_{1}\) . This hidden state is finally passed to a dense layer to produce the output. The table illustrates the concept of sliding window method used to forecast multiple time steps during the testing and prediction (i.e., using the output at a time-step as an input to forecast the next time-step). Using this concept, we can predict as many time steps as needed. In the table, an output vector of 6 time steps was predicted.
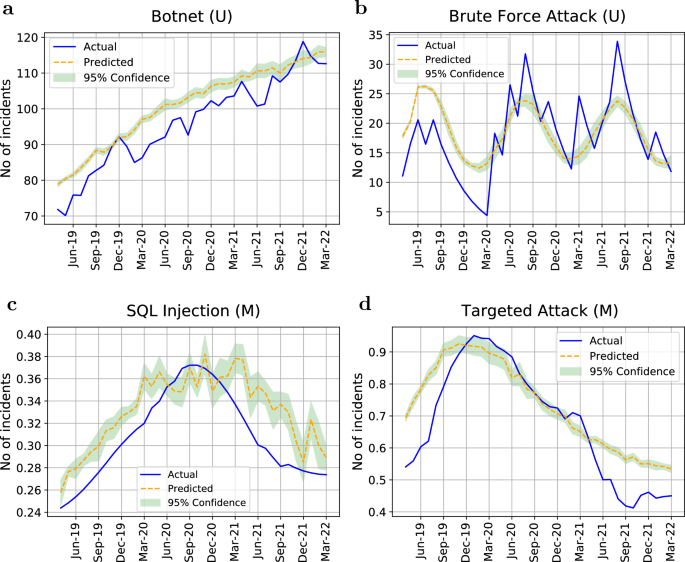
The B-LSTM validation results of predicting the number of attacks from April, 2019 to March, 2022. (U) indicates an univariate model while (M) indicates a multivariate model. ( a ) Botnet attack with M-SMAPE=0.03. ( b ) Brute force attack with M-SMAPE=0.13. ( c ) SQL injection attack with M-SMAPE=0.04 using the feature of NoM. ( d ) Targeted attack with M-SMAPE=0.06 using the feature of NoM. Y axis is normalised in the case of multivariate models to account for the different ranges of feature values.
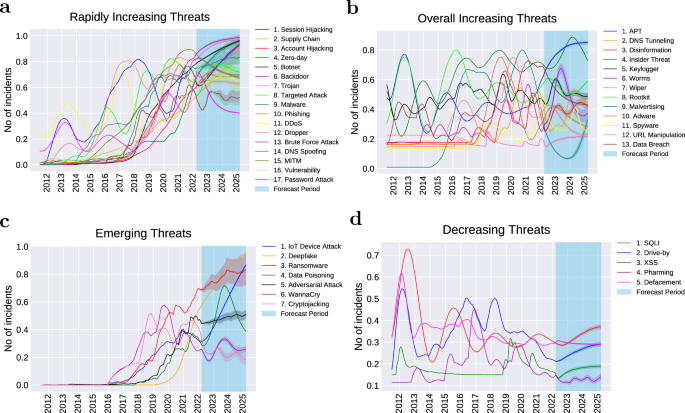
A bird’s eye view of threat trend categories. The period of the trend plots is between July, 2011 and March, 2025, with the period between April, 2022 and March, 2025 forecasted using B-LSTM. ( a ) Among rapidly increasing threats, as observed in the forecast period, some threats are predicted to continue a sharp increase until 2025 while others will probably level off. ( b ) Threats under this category have overall been increasing while fluctuating over the past 11 years. Recently, some of the overall increasing threats slightly declined however many of those are likely to recover and level off by 2025. ( c ) Emerging threats that began to appear and grow sharply after the year 2016, and are expected to continue growing at this increasing rate, while others are likely to slow down or stabilise by 2025. ( d ) Decreasing threats that peaked in the earlier years and have slowly been declining since then. This decreasing group are likely to level off however probably will not disappear in the coming 3 years. The Y axis is normalised to account for the different ranges of values across different attacks. The 95% confidence interval is shown for each threat prediction.
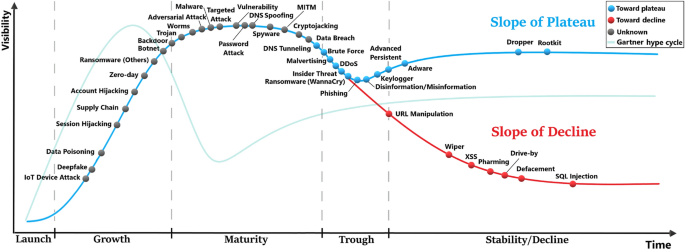
The threat cycle (TTC). The attacks go through 5 stages, namely, launch, growth, maturity trough, and stability/decline. A standard Gartner hype cycle (GHC) is shown with a vanishing green colour for a comparison to TTC. Both GHC and TTC have a peak, however, TTC’s peak is much wider with a slightly less steep curve during the growth stage. Some attacks in TTC do not recover after the trough and slide into the slope of decline. TTC captures the state of each attack in 2022, where the colour of each attack indicates which slope it would follow (e.g., plateau or decreasing) based on the predictive results until 2025. Within the trough stage, the attacks (in blue dot) are likely to arrive at the slope of plateau by 2025. The attacks (in red dot) will probably be on the slope of decline by 2025. The attacks with unknown final destination are coloured in grey.
Data availability
As requested by the journal, the data used in this paper is available to editors and reviewers upon request. The data will be made publicly available and can be accessed at the following link after the paper is published. https://github.com/zaidalmahmoud/Cyber-threat-forecast .
Ghafur, S. et al. A retrospective impact analysis of the wannacry cyberattack on the NHS. NPJ Digit. Med. 2 , 1–7 (2019).
Article Google Scholar
Alrzini, J. R. S. & Pennington, D. A review of polymorphic malware detection techniques. Int. J. Adv. Res. Eng. Technol. 11 , 1238–1247 (2020).
Google Scholar
Lazarevic, A., Ertoz, L., Kumar, V., Ozgur, A. & Srivastava, J. A comparative study of anomaly detection schemes in network intrusion detection. In: Proceedings of the 2003 SIAM International Conference on Data Mining , 25–36 (SIAM, 2003).
Kebir, O., Nouaouri, I., Rejeb, L. & Said, L. B. Atipreta: An analytical model for time-dependent prediction of terrorist attacks. Int. J. Appl. Math. Comput. Sci. 32 , 495–510 (2022).
MATH Google Scholar
Anticipating cyber attacks: There’s no abbottabad in cyber space. Infosecurity Magazine https://www.infosecurity-magazine.com/white-papers/anticipating-cyber-attacks (2015).
Jumper, J. et al. Highly accurate protein structure prediction with alphafold. Nature 596 , 583–589 (2021).
Article ADS CAS PubMed PubMed Central Google Scholar
Baek, M. et al. Accurate prediction of protein structures and interactions using a three-track neural network. Science 373 , 871–876 (2021).
Gibney, E. et al. Where is russia’s cyberwar? researchers decipher its strategy. Nature 603 , 775–776 (2022).
Article ADS CAS PubMed Google Scholar
Passeri, P. Hackmageddon data set. Hackmageddon https://www.hackmageddon.com (2022).
Chen, C.-M. et al. A provably secure key transfer protocol for the fog-enabled social internet of vehicles based on a confidential computing environment. Veh. Commun. 39 , 100567 (2023).
Nagasree, Y. et al. Preserving privacy of classified authentic satellite lane imagery using proxy re-encryption and UAV technologies. Drones 7 , 53 (2023).
Kavitha, A. et al. Security in IoT mesh networks based on trust similarity. IEEE Access 10 , 121712–121724 (2022).
Salih, A., Zeebaree, S. T., Ameen, S., Alkhyyat, A. & Shukur, H. M A survey on the role of artificial intelligence, machine learning and deep learning for cybersecurity attack detection. In: 2021 7th International Engineering Conference “Research and Innovation amid Global Pandemic” (IEC) , 61–66 (IEEE, 2021).
Ren, K., Zeng, Y., Cao, Z. & Zhang, Y. Id-rdrl: A deep reinforcement learning-based feature selection intrusion detection model. Sci. Rep. 12 , 1–18 (2022).
Liu, X. & Liu, J. Malicious traffic detection combined deep neural network with hierarchical attention mechanism. Sci. Rep. 11 , 1–15 (2021).
Werner, G., Yang, S. & McConky, K. Time series forecasting of cyber attack intensity. In Proceedings of the 12th Annual Conference on Cyber and Information Security Research , 1–3 (2017).
Werner, G., Yang, S. & McConky, K. Leveraging intra-day temporal variations to predict daily cyberattack activity. In 2018 IEEE International Conference on Intelligence and Security Informatics (ISI) , 58–63 (IEEE, 2018).
Okutan, A., Yang, S. J., McConky, K. & Werner, G. Capture: cyberattack forecasting using non-stationary features with time lags. In 2019 IEEE Conference on Communications and Network Security (CNS) , 205–213 (IEEE, 2019).
Munkhdorj, B. & Yuji, S. Cyber attack prediction using social data analysis. J. High Speed Netw. 23 , 109–135 (2017).
Goyal, P. et al. Discovering signals from web sources to predict cyber attacks. arXiv preprint arXiv:1806.03342 (2018).
Qin, X. & Lee, W. Attack plan recognition and prediction using causal networks. In 20th Annual Computer Security Applications Conference , 370–379 (IEEE, 2004).
Husák, M. & Kašpar, J. Aida framework: real-time correlation and prediction of intrusion detection alerts. In: Proceedings of the 14th international conference on availability, reliability and security , 1–8 (2019).
Liu, Y. et al. Cloudy with a chance of breach: Forecasting cyber security incidents. In: 24th USENIX Security Symposium (USENIX Security 15) , 1009–1024 (2015).
Malik, J. et al. Hybrid deep learning: An efficient reconnaissance and surveillance detection mechanism in sdn. IEEE Access 8 , 134695–134706 (2020).
Bilge, L., Han, Y. & Dell’Amico, M. Riskteller: Predicting the risk of cyber incidents. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security , 1299–1311 (2017).
Husák, M., Bartoš, V., Sokol, P. & Gajdoš, A. Predictive methods in cyber defense: Current experience and research challenges. Futur. Gener. Comput. Syst. 115 , 517–530 (2021).
Stephens, G. Cybercrime in the year 2025. Futurist 42 , 32 (2008).
Adamov, A. & Carlsson, A. The state of ransomware. Trends and mitigation techniques. In EWDTS , 1–8 (2017).
Shoufan, A. & Damiani, E. On inter-rater reliability of information security experts. J. Inf. Secur. Appl. 37 , 101–111 (2017).
Cha, Y.-O. & Hao, Y. The dawn of metamaterial engineering predicted via hyperdimensional keyword pool and memory learning. Adv. Opt. Mater. 10 , 2102444 (2022).
Article CAS Google Scholar
Elsevier research products apis. Elsevier Developer Portal https://dev.elsevier.com (2022).
Twitter api v2. Developer Platform https://developer.twitter.com/en/docs/twitter-api (2022).
holidays 0.15. PyPI. The Python Package Index https://pypi.org/project/holidays/ (2022).
Visser, M., van Eck, N. J. & Waltman, L. Large-scale comparison of bibliographic data sources: Scopus, web of science, dimensions, crossref, and microsoft academic. Quant. Sci. Stud. 2 , 20–41 (2021).
2021 trends show increased globalized threat of ransomware. Cybersecurity and Infrastructure Security Agency https://www.cisa.gov/uscert/ncas/alerts/aa22-040a (2022).
Lai, K. K., Yu, L., Wang, S. & Huang, W. Hybridizing exponential smoothing and neural network for financial time series predication. In International Conference on Computational Science , 493–500 (Springer, 2006).
Huang, B., Ding, Q., Sun, G. & Li, H. Stock prediction based on Bayesian-lstm. In Proceedings of the 2018 10th International Conference on Machine Learning and Computing , 128–133 (2018).
Mae, Y., Kumagai, W. & Kanamori, T. Uncertainty propagation for dropout-based Bayesian neural networks. Neural Netw. 144 , 394–406 (2021).
Article PubMed Google Scholar
Scopus preview. Scopus https://www.scopus.com/home.uri (2022).
Jia, P., Chen, H., Zhang, L. & Han, D. Attention-lstm based prediction model for aircraft 4-d trajectory. Sci. Rep. 12 (2022).
Chandra, R., Goyal, S. & Gupta, R. Evaluation of deep learning models for multi-step ahead time series prediction. IEEE Access 9 , 83105–83123 (2021).
Gers, F. A., Schmidhuber, J. & Cummins, F. Learning to forget: Continual prediction with lstm. Neural Comput. 12 , 2451–2471 (2000).
Article CAS PubMed Google Scholar
Sagheer, A. & Kotb, M. Unsupervised pre-training of a deep lstm-based stacked autoencoder for multivariate time series forecasting problems. Sci. Rep. 9 , 1–16 (2019).
Article ADS Google Scholar
Swiler, L. P., Paez, T. L. & Mayes, R. L. Epistemic uncertainty quantification tutorial. In Proceedings of the 27th International Modal Analysis Conference (2009).
Gal, Y. & Ghahramani, Z. Dropout as a bayesian approximation: Representing model uncertainty in deep learning. arXiv preprint arXiv:1506.02142v6 (2016).
Chollet, F. Deep Learning with Python , 2 edn. (Manning Publications, 2017).
Xu, J., Li, Z., Du, B., Zhang, M. & Liu, J. Reluplex made more practical: Leaky relu. In 2020 IEEE Symposium on Computers and Communications (ISCC) , 1–7 (IEEE, 2020).
Gal, Y., Hron, J. & Kendall, A. Concrete dropout. Adv. Neural Inf. Process. Syst. 30 (2017).
Shcherbakov, M. V. et al. A survey of forecast error measures. World Appl. Sci. J. 24 , 171–176 (2013).
Bergstra, J. & Bengio, Y. Random search for hyper-parameter optimization. J. Mach. Learn. Res. 13 (2012).
Kingma, D. P. & Ba, J. Adam: A method for stochastic optimization. arXiv preprint arXiv:1412.6980 (2014).
Krizhevsky, A., Sutskever, I. & Hinton, G. E. Imagenet classification with deep convolutional neural networks. Commun. ACM 60 , 84–90 (2017).
Shifferaw, Y. & Lemma, S. Limitations of proof of stake algorithm in blockchain: A review. Zede J. 39 , 81–95 (2021).
Dedehayir, O. & Steinert, M. The hype cycle model: A review and future directions. Technol. Forecast. Soc. Chang. 108 , 28–41 (2016).
Abri, F., Siami-Namini, S., Khanghah, M. A., Soltani, F. M. & Namin, A. S. Can machine/deep learning classifiers detect zero-day malware with high accuracy?. In 2019 IEEE International Conference on Big Data (Big Data) , 3252–3259 (IEEE, 2019).
Download references
Acknowledgements
The authors are grateful to the DASA’s machine learning team for their invaluable discussions and feedback, and special thanks to the EBTIC, British Telecom’s (BT) cyber security team for their constructive criticism on this work.
Author information
Authors and affiliations.
Department of Computer Science and Information Systems, University of London, Birkbeck College, London, United Kingdom
Zaid Almahmoud & Paul D. Yoo
Huawei Technologies Canada, Ottawa, Canada
Omar Alhussein
Department of Electrical and Computer Engineering, University of Waterloo, Waterloo, Canada
Ilyas Farhat
Department of Computer Science, Università degli Studi di Milano, Milan, Italy
Ernesto Damiani
Center for Cyber-Physical Systems (C2PS), Khalifa University, Abu Dhabi, United Arab Emirates
You can also search for this author in PubMed Google Scholar
Contributions
Z.A., P.D.Y, I.F., and E.D. were in charge of the framework design and theoretical analysis of the trend analysis and TTC. Z.A., O.A., and P.D.Y. contributed to the B-LSTM design and experiments. O.A. proposed the concepts of B-LSTM. All of the authors contributed to the discussion of the framework design and experiments, and the writing of this paper. P.D.Y. proposed the big data approach and supervised the whole project.
Corresponding author
Correspondence to Paul D. Yoo .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary information., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Almahmoud, Z., Yoo, P.D., Alhussein, O. et al. A holistic and proactive approach to forecasting cyber threats. Sci Rep 13 , 8049 (2023). https://doi.org/10.1038/s41598-023-35198-1
Download citation
Received : 21 December 2022
Accepted : 14 May 2023
Published : 17 May 2023
DOI : https://doi.org/10.1038/s41598-023-35198-1
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Integrating ai-driven threat intelligence and forecasting in the cyber security exercise content generation lifecycle.
- Alexandros Zacharis
- Vasilios Katos
- Constantinos Patsakis
International Journal of Information Security (2024)
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing: AI and Robotics newsletter — what matters in AI and robotics research, free to your inbox weekly.
- Search Menu
- Editor's Choice
- Author Guidelines
- Submission Site
- Open Access
- About Journal of Cybersecurity
- Editorial Board
- Advertising and Corporate Services
- Journals Career Network
- Self-Archiving Policy
- Journals on Oxford Academic
- Books on Oxford Academic

Editors-in-Chief
Tyler Moore
About the journal
Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …
Latest articles

Call for Papers: Workshop on the Economics of Information Security
Journal of Cybersecurity is inviting submissions to a new special issue from the workshop on the economics of information security. Authors whose papers appeared at the workshop are invited to submit a revised version to the journal.

Call for Papers
Journal of Cybersecurity is soliciting papers for a special collection on the philosophy of information security. This collection will explore research at the intersection of philosophy, information security, and philosophy of science.
Find out more

Submit your paper
Join the conversation moving the science of security forward. Visit our Instructions to Authors for more information about how to submit your manuscript.

High-Impact Research Collection
Explore a collection of recently published high-impact research in the Journal of Cybersecurity .
Browse the collection here

Email alerts
Register to receive table of contents email alerts as soon as new issues of Journal of Cybersecurity are published online.

Read and Publish deals
Authors interested in publishing in Journal of Cybersecurity may be able to publish their paper Open Access using funds available through their institution’s agreement with OUP.
Find out if your institution is participating
Related Titles

Affiliations
- Online ISSN 2057-2093
- Print ISSN 2057-2085
- Copyright © 2024 Oxford University Press
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Institutional account management
- Rights and permissions
- Get help with access
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.
- Request Demo
Cybersecurity Trends 2023: Latest Research & Key Risk Contributors
Cybersecurity risk is evolving in novel ways, with growing potential to cause significant economic disruption and financial losses as attackers become more sophisticated and businesses become more interconnected. Recent analysis from Moody’s highlights the risk: $22 trillion in global rated debt has “High” or “Very High” cyber risk exposure.
What are the major cybersecurity trends for 2023? How can security leaders adapt their programs and increase their levels of preparedness? How will financial markets incorporate cyber risk into investment and credit decisions?
Download this webinar to hear insights from Moody’s analysts and Bitsight’s cyber risk experts as they discuss their latest research and look ahead to 2023:
- Key takeaways regarding the latest Moody’s research featuring Bitsight data, including factors contributing to increased cyber risk in markets, sectors, and regions with the highest cyber risk levels
- Future of ransomware attacks
- Potential impact of new cybersecurity regulations like the Securities and Exchange Commission’s cyber incident disclosure requirements
- Evolution of cyber insurance
- Quantifying losses from cyber incidents

View Your Webinar
- Company Email
- Company Name
- Job Role - Select - Architecture/Engineering Audit/Compliance Board/General Counsel Consulting Cyber Brokerage Finance Human Resources Information Security Information Technology Marketing/Sales Network/Systems Operations Other Press/Media Procurement Risk Management Student Underwriting
- Job Level - Select - Board Level C - Level VP - Level Director - Level Manager - Level Specialist/Technician Other Consultant Administrator

ICT: Cyber Security and Applications
Proceedings of ICTCS 2023, Volume 3
- Conference proceedings
- © 2024
- Amit Joshi 0 ,
- Mufti Mahmud 1 ,
- Roshan G. Ragel 2 ,
- S. Kartik 3
Global Knowledge Research Foundation, Ahmedabad, India
You can also search for this editor in PubMed Google Scholar
Nottingham Trent University, Nottingham, UK
University of peradeniya, delthota, sri lanka, department of cse, sns college of technology, coimbatore, india.
- Presents high-quality research in the field of information and communication technology
- Features the outcomes of ICTCS 2023, held in Jaipur, India
- Serves as a reference resource for researchers and practitioners in academia and industry
Part of the book series: Lecture Notes in Networks and Systems (LNNS, volume 916)
Included in the following conference series:
- ICTCS: International Conference on Information and Communication Technology for Competitive Strategies
Conference proceedings info: ICTCS 2022.
This is a preview of subscription content, log in via an institution to check access.
Access this book
- Available as EPUB and PDF
- Read on any device
- Instant download
- Own it forever
- Compact, lightweight edition
- Dispatched in 3 to 5 business days
- Free shipping worldwide - see info
Tax calculation will be finalised at checkout
Other ways to access
Licence this eBook for your library
Institutional subscriptions
Table of contents (40 papers)
Front matter, scalability analysis of molecular dynamics simulation using namd on ampere-based dense gpu supercomputer.
- Nisha Agrawal, Abhishek Das, Manish Modani
Digital Muhadathah : Framework Model Development for Digital Arabic Language Learning
- Aminudin Hehsan, Miftachul Huda, Mahsun Mahsun, Asrori Asrori, Muhammad Hambal Shafwan, Din Muhammad Zakariya et al.
Proficient Exam Monitoring System Using Deep Learning Techniques
- Priya N. Parkhi, Amna Patel, Dhruvraj Solanki, Himesh Ganwani, Manav Anandani
Object Detection in Rainy Images Based on Multi-stage Image Deraining Network
- V. S. Vishnu, Philomina Simon
ApnaMarket.NFT: Empowering Art and Collectibles in the NFT Marketplace
- Padma Adane, Viresh Dhawan, Harsh Singh, Atharva Baheti
Smart Homes of Tomorrow: IoT-Enabled Lifestyle Enhancements
- Priyanka Patel, Krishna Gevariya, Rency Kapadia
Human Activity Recognition Using Supervised Machine Learning Classifiers
- Kazi Azizuddin, Premal Patel, Chintan Shah
Application of Deep Learning in Detection and Classification
- P. K. Muhammad Suarim, Meeradevi, B. J. Sowmya, Prathik Boppudi, Vivek Ranjan, Yashraj Verma et al.
Gesture-Based Alphabet Detection and Scoring Using OpenCV and Tesseract-OCR
- Karan Chopra, S. Shanthi Therese
Sign-Kiosk: A Real-Time Virtual Assistant
- Srushti Sujit, Anchala Balaraj, M. S. Pavan Kumar, A. Sagar, M. Anuradha
A Graph-Based Strategy for Intrusion Detection in Connected Vehicles
- M. S. Sreelekshmi, S. Aji
Correlation Analysis Between INR-USD Exchange Rates and Public Sentiments Using Twitter
- Gargee Dorle, Varsha Pimprale
Improving Farm Yield Through Agent-Based Modelling
- Dattatraya Adane, Anand Upadhyaya, Mayank Pandey, Yash Dhoot

A Recommendation System for Food Tourism
- Dattatraya S. Adane, Himanshu Shahu, Parshva Choradia, Ritesh Yadav
Working of the Tesseract OCR on Different Fonts of Gujarati Language
- Kartik Joshi, Harshal Arolkar
Exploring Innovations for Streamlining Orphan Adoption: Harnessing Blockchain and Decentralized Solutions—A Survey and Comprehensive Framework
- Deepali Patil, Aabha Patil, Aarti Puthran, Nilesh Marathe, Surekha Janrao, Hezal Lopes
Encryption + Watermarking: A Duo Approach for Secure Image Communication in Transform Domain
- R. Sivaraman, D. Yasvanthira Sri, R. Subashini, B. Vinizia, C. Lakshmi
Animal Detection in Wildlife Conservation Using Deep Learning
- B. Senbagam, S. Bharathi
Real-Time Groundwater Monitoring Using IoT Sensors for Sustainable Resource Management
- M. Sowndharya, S. Duraisamy
Other volumes
Information and communication technology for competitive strategies (ictcs 2022).
- Information and Communication Technology
- Big Data and Data Mining
- Sensor Networks and Embedded System
- Human Computer Interaction
- E-governance
- ICTCS 2023 Proceedings
About this book
This book contains best selected research papers presented at ICTCS 2023: Eighth International Conference on Information and Communication Technology for Competitive Strategies. The conference will be held in Jaipur, India during 8 – 9 December 2023. The book covers state-of-the-art as well as emerging topics pertaining to ICT and effective strategies for its implementation for engineering and managerial applications. This book contains papers mainly focused on ICT for computation, algorithms and data analytics and IT security. The work is presented in three volumes.
Editors and Affiliations
Mufti Mahmud
Roshan G. Ragel
About the editors
Dr. Amit Joshi is currently the Director of Global Knowledge Research Foundation, also an Entrepreneur Researcher who has completed his Masters and research in the areas of cloud computing and cryptography in medical imaging. Dr. Joshi has an experience of around 10 years in academic and industry in prestigious organizations. Dr. Joshi is an active member of ACM, IEEE, CSI, AMIE, IACSIT-Singapore, IDES, ACEEE, NPA and many other professional societies. Currently, Dr. Joshi is the International Chair of InterYIT at International Federation of Information Processing (IFIP, Austria), He has presented and published more than 50 papers in national and international journals/conferences of IEEE and ACM. Dr. Joshi has also edited more than 40 books which are published by Springer, ACM and other reputed publishers. Dr. Joshi has also organized more than 50national and international conferences and programs in association withACM, Springer, IEEE to name a few across different countries including India, UK, Europe, USA, Canada, Thailand, Egypt and many more.
Dr. Mufti Mahmud is an Associate Professor of Cognitive Computing at the Computer Science Department of Nottingham Trent University (NTU), UK. He has been the recipient of the top 2% cited scientists worldwide in computer science (since 2020), the NTU VC Outstanding Research Award 2021, and the Marie-Curie postdoctoral fellowship. Dr Mahmud is a member of the university shadow executive team shadowing the pro-vice-chancellor (research and innovation), coordinator of the Computer Science and Informatics research excellence framework unit of assessment at NTU, the group leader of the cognitive computing & brain informatics research group and the deputy group leader of the Interactive Systems research group at NTU. His research portfolio consists of GBP 4.0 million grant capture with expertise that includes brain informatics, computational intelligence, applied data analysis, and big data technologies focusing on healthcare applications. In these fields, he has published over 320 peer-reviewed articles. Dr Mahmud has been the General Chair of the Brain Informatics Conference 2020, 2021, and 2022; founding chair of the Applied Intelligence and Informatics conference since 2021; Trends in Electronics and Health Informatics 2022; International Symposium of Green Technologies and Applications 2023; chair of the IEEE CICARE symposium since 2017 and was the local organising chair of the IEEE WCCI 2020. He will serve as one of the General Chairs of the 31st edition of the ICONIP conference to be held in Auckland (NZ) in 2024. He is the Big Data Analytics Section Editor of Cognitive Computation, the Regional Editor (Europe) of the Brain Informatics journal, and an Associate Editor of the Frontiers in Neuroscience. He is the chief editor of the Applied Intelligence and Informatics (Springer-Nature) and Smart Healthcare Systems: From Data to Knowledge (CRC Press) book series. Currently, Dr Mahmud is serving as the Chair of the Intelligent System Application and Brain Informatics Technical Committees of the IEEE Computational Intelligence Society (CIS), a member of the IEEE CIS Task Force on Intelligence Systems for Health, the Publications Chair of the IEEE UK and Ireland Industry Applications Chapter, and the Project Liaison Officer of the IEEE UK and Ireland SIGHT Committee, and the Secretary of the IEEE UK and Ireland CIS Chapter. Dr. Roshan Ragel is a full professor in Computer Engineering at the University of Peradeniya, Sri Lanka. He is a skilled university lecturer and researcher with a doctorate in computer science and engineering and a passion for teaching, research and administration. His research interest is in the areas of fault-tolerant and dependable computing, accelerated and high-performance computing, wearable computing and synthesis of secure and reliable embedded processors.Prof. Ragel received his PhD in Computer Science and Engineering from the University of New South Wales, Australia in 2007 and his BSc in Engineering from the University of Peradeniya, Sri Lanka in 2001. He was appointed a Senior Lecturer in Computer Engineering at the University of Peradeniya December 2007 and a full professor since October 2017. Prof. Ragel has co-authored about 150 peer-reviewed articles in topics including Micro- Architectural Support for Reliability and Security in Embedded Processors (SoC), Internet of Things (IoT), Side-Channel Attacks and Countermeasures, Application Specific Processor Design, High-Performance Computing such as Hardware/Software Acceleration of Bioinformatics Algorithms, Wearable Computing, Format-Preserving Digitisation and OCR of Local Language Text, and Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHAs) in the Context of Mobile Applications. He has won several best paper awards in conference papers, the most prolific Sri Lankan author award from Elsevier Research in 2017 and the Presidential award for scientific publication in Sri Lanka in 2018. He was a visiting research scholar at the UNSW, Sydney a few times and UIUC, Illinois once. He is a Senior Member of the IEEE and the IEEE Computer Society.
Dr. S. Karthik is presently Professor & Dean in the Department of Computer Science & Engineering, SNS College of Technology, affiliated to Anna University- Chennai, Tamil Nadu, India. He received the M.E and PhD degree from Anna University, Chennai. His research interests include network security, big data, cloud computing, web services and wireless systems. In particular, he is currently working in a research group developing new Internet security architectures and active defence systems against DDoS attacks. Dr. S.Karthik published more than 200 papers in refereed international journals and 125 papers in conferences and has been involved in many international conferences as Technical Chair and tutorial presenter. He is an active member of IEEE, ISTE, IAENG, IACSIT and Indian Computer Society.
Bibliographic Information
Book Title : ICT: Cyber Security and Applications
Book Subtitle : Proceedings of ICTCS 2023, Volume 3
Editors : Amit Joshi, Mufti Mahmud, Roshan G. Ragel, S. Kartik
Series Title : Lecture Notes in Networks and Systems
DOI : https://doi.org/10.1007/978-981-97-0744-7
Publisher : Springer Singapore
eBook Packages : Engineering , Engineering (R0)
Copyright Information : The Editor(s) (if applicable) and The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd. 2024
Softcover ISBN : 978-981-97-0743-0 Published: 14 May 2024
eBook ISBN : 978-981-97-0744-7 Published: 13 May 2024
Series ISSN : 2367-3370
Series E-ISSN : 2367-3389
Edition Number : 1
Number of Pages : XX, 501
Number of Illustrations : 72 b/w illustrations, 189 illustrations in colour
Topics : Communications Engineering, Networks , Science and Technology Studies , Systems and Data Security , Computational Intelligence , Artificial Intelligence
- Publish with us
Policies and ethics
- Find a journal
- Track your research
Mobile Menu Overlay
The White House 1600 Pennsylvania Ave NW Washington, DC 20500
Fact Sheet: 2024 Report on the Cybersecurity Posture of the United States
May 7, 2024
Read the full report here
Today, the Office of the National Cyber Director (ONCD) released the 2024 Report on the Cybersecurity Posture of the United States . This first-of-its-kind report provides important updates on how the nation is addressing the challenges and opportunities we face in cyberspace.
Over the past year, U.S. national cybersecurity posture improved, driven by steady progress towards the 2023 National Cybersecurity Strategy’s (NCS) vision of a defensible, resilient, and values-aligned digital ecosystem. Achieving this vision requires two fundamental shifts in how we allocate roles, responsibilities, and resources in cyberspace by (1) rebalancing the responsibility to defend cyberspace away from end users and to the most capable and best-positioned actors in the public and private sectors, and (2) realigning incentives to favor long-term investments in future resilience.
The Administration has successfully begun implementation of the NCS Implementation Plan (NCSIP), which coordinates actions by departments and agencies across the Federal Government to make the President’s affirmative vision a reality. In NCSIP Version 1, the Federal Government was responsible for completing 36 initiatives by the second quarter of 2024. 33 of these 36 (92%) initiatives were completed on time and three remain underway. An additional 33 NCSIP Version 1 initiatives have completion dates over the next two years and are on track. Congress has provided essential support to the implementation process by empowering departments and agencies with necessary authorities and resources.
The Administration has also released Version 2 of the NCSIP , which complements the findings of this report and outlines the next phase of action necessary to implement the President’s Strategy and further improve U.S. national cybersecurity posture.
The Strategic Environment
In 2023, the strategic environment was characterized by complexity , interconnectivity , and competition . Continued progress in digital communications, advanced computing, quantum information science, data storage and processing, and other critical and emerging technologies are rapidly increasing the complexity of our economy and society. These technologies also connect people around the world, enable the proliferation of cyber-physical systems, and create new dependencies between critical infrastructure and essential services across every sector.
As this landscape evolves, malicious state and non-state actors are exploiting its seams with growing capability and strategic purpose, continuing to aggressively conduct malicious cyber activity that threatens U.S. national security, public safety, and economic prosperity. Critical infrastructure across the United States has been held at risk by the People’s Republic of China and other adversaries who threaten essential services and public safety in service of their geopolitical ambitions. Ransomware groups have built a business model around targeting schools, hospitals, small businesses, and many others ill-equipped to defend themselves.
Five trends, in addition to enduring cybersecurity challenges, drove change in the strategic environment in 2023:
- Evolving Risks to Critical Infrastructure : Nation-state adversaries demonstrated a growing willingness to use cyber capabilities to compromise and hold at risk critical infrastructure systems and assets with no inherent espionage value, in order to further their broader strategic objectives.
- Ransomware : Ransomware remained a persistent threat to national security, public safety, and economic prosperity, and ransomware groups continued to develop sophisticated strategies to evade or circumvent defensive and disruptive measures designed to frustrate their activities.
- Supply Chain Exploitation : Complex and interconnected supply chains for software and other information technology and services enabled malicious actors to compromise victims at scale.
- Commercial Spyware : There was a growing market for sophisticated and invasive cyber-surveillance tools sold to nation-state actors by private vendors to access electronic devices remotely, monitor and extract their content, and manipulate their components without the knowledge or consent of the devices’ users.
- Artificial Intelligence : Artificial intelligence is one of the most powerful, publicly accessible technologies of our time, and its continued evolution in 2023 presented opportunities and challenges for cyber risk management at scale.
Current Efforts
ONCD coordinates the implementation of national cyber policy and strategy, including the NCS, by driving new actions and uplifting and connecting work underway. Actions taken by the Federal Government during the period covered by this report include:
- Establishing and Using Cyber Requirements to Protect Critical Infrastructure , including through the development and harmonization of regulatory requirements in multiple critical infrastructure sectors.
- Enhancing Federal Cooperation and Partnerships to better support cyber defenders, including by increasing operational collaboration, improving Sector Risk Management Agency capacity, and integrating Federal cyber defense capabilities.
- Improving Incident Preparedness and Response by rapidly sharing threat information, prioritizing support to victims, and reviewing significant incidents and campaigns to derive lessons learned.
- Disrupting and Degrading Adversary Activity using all tools of national power, resulting in coordinated, high-impact disruption campaigns against a wide range of malicious cyber actors.
- Defending Federal Networks at speed and scale, including by integrating Zero Trust Architecture principles across the Federal enterprise, modernizing legacy technology systems, and expanding the use of shared services.
- Strengthening the National Cyber Workforce , including through the promulgation of a National Cyber Workforce and Education Strategy (NCWES) and engagement with workers, employers, students, and educators across the country.
- Advancing Software Security to Produce Safer Products and Services , including by advancing Secure by Design principles, Software Bills of Material, and memory-safe programming languages.
- Enabling a Digital Economy that Empowers and Protects Consumers , including by launching a U.S. Cyber Trust Mark certification and labeling program and by promoting competition and accountability across the technology industry.
- Investing in Resilient Next-Generation Technologies across the clean energy economy, issuing an executive order to guide Federal efforts related to artificial intelligence, and addressing security challenges present in the technical foundations of the Internet.
- Managing Risks to Data Security and Privacy by enabling safe, data-rich cross-border commerce and promoting the development of privacy-enhancing technologies.
- Enhancing Resilience Across the Globe by building coalitions of like-minded nations to provide support to victims of ransomware and other cyberattacks, align national policy, and promote secure and resilient global supply chains.
- Advancing a Rights-Respecting Digital Ecosystem by advancing an affirmative vision of an open, free, global, interoperable, reliable, accessible, and secure Internet; combatting the proliferation and misuse of digital technologies like commercial spyware; and shaping emerging technologies to align with democratic values and human rights.
Future Outlook
In 2024 and beyond, the Federal Government will build on accomplishments of the past year, continue to implement the NCS and NCWES, and adapt its approach to address emergent challenges and opportunities presented by an evolving strategic landscape. NCSIP Version 2 outlines 31 new initiatives that build on shared accomplishments of the past year and establish specific lines of effort to realize the vision set out in the President’s NCS.
Read the full National Cybersecurity Strategy Implementation Plan 2.0 here
Stay Connected
We'll be in touch with the latest information on how President Biden and his administration are working for the American people, as well as ways you can get involved and help our country build back better.
Opt in to send and receive text messages from President Biden.

Cybersecurity Award 2023
Call for nominations.
About the Award
The Cybersecurity Award is presented to authors whose work represents outstanding and groundbreaking research in all essential aspects of cybersecurity. The award will be bestowed upon three distinguished papers focused on the following perspectives:
Track A--- Best Theoretical Research Paper Track B--- Best Practical Research Paper Track C--- Best Machine Learning and Security Paper
Every winning paper will receive USD 1500 as the prize with a statue and certificate to commemorate.
Scope
All paper written in the area of cybersecurity is eligible for nomination. Please note that your paper must have appeared in a refereed journal, conference, or workshop with proceedings published from January 1, 2022, until December 31, 2022.
Your paper shall cover at least one of the following aspects:
• Cryptography and its applications • Network and critical infrastructure security • Hardware security • Software and system security • Cybersecurity data analytics • Data-driven security and measurement studies • Adversarial reasoning • Malware analysis • Privacy-enhancing technologies and anonymity • IoT Security • AI Security
Submission Guidelines
Your nomination shall be directly sent to [email protected] with the following contents:
• Full paper (Word or PDF format preferred) • Official publication site of the paper • The track you prefer (only one track can be chosen per paper) • Anything else you feel necessary to note
Schedule
January Call for nomination opened *All nominations must be submitted by April 10, 2023. May Online voting open June Review period July Award recipients are notified; selections announced August-the end of 2023 ‘ Cybersecurity ’s salon event’
Reviewing Process and Instructions
Firstly, the nominations will go through online voting publicly. Those with higher votes will be considered in the final assessment of winning papers. You are welcome to tell your friends and support your submission.
The second round of selection will be done by the Awards Committee and up to three papers will be awarded.
ONLY authors of the awarded papers will be notified via email. And the authors of these papers will be invited to present in the seminar on ‘ Cybersecurity ’s salon event’. Besides, an extended paper of your winning paper will be invited to publish in the journal Cybersecurity .
Previous Winner
In 2022, the award was given to the following two papers. Let’s celebrate the winners mentioned below to get a taste of what to expect for the Cybersecurity Award 2023:
Best Practical Paper --- Robert Buhren, Hans-Niklas Jacob, Thilo Krachenfels, and Jean-Pierre Seifert. 2021. One Glitch to Rule Them All: Fault Injection Attacks Against AMD's Secure Encrypted Virtualization. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security (CCS '21). Association for Computing Machinery, New York, NY, USA, 2875–2889. Best Machine Learning and Security Paper --- Xuezixiang Li, Yu Qu, and Heng Yin. 2021. PalmTree: Learning an Assembly Language Model for Instruction Embedding. In Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security (CCS '21). Association for Computing Machinery, New York, NY, USA, 3236–3251

For enquiries call:
+1-469-442-0620

60+ Latest Cyber Security Research Topics in 2024
Home Blog Security 60+ Latest Cyber Security Research Topics in 2024
The concept of cybersecurity refers to cracking the security mechanisms that break in dynamic environments. Implementing Cyber Security Project topics and cybersecurity thesis topics helps overcome attacks and take mitigation approaches to security risks and threats in real-time. Undoubtedly, it focuses on events injected into the system, data, and the whole network to attack/disturb it.
The network can be attacked in various ways, including Distributed DoS, Knowledge Disruptions, Computer Viruses / Worms, and many more. Cyber-attacks are still rising, and more are waiting to harm their targeted systems and networks. Detecting Intrusions in cybersecurity has become challenging due to their Intelligence Performance. Therefore, it may negatively affect data integrity, privacy, availability, and security.
This article aims to demonstrate the most current Cyber Security Topics for Projects and areas of research currently lacking. We will talk about cyber security research questions, cyber security topics for the project, latest research titles about cyber security.
.jpg&w=3840&q=75)
List of Trending Cyber Security Research Topics in 2024
Digital technology has revolutionized how all businesses, large or small, work, and even governments manage their day-to-day activities, requiring organizations, corporations, and government agencies to utilize computerized systems. To protect data against online attacks or unauthorized access, cybersecurity is a priority. There are many Cyber Security Courses online where you can learn about these topics. With the rapid development of technology comes an equally rapid shift in Cyber Security Research Topics and cybersecurity trends, as data breaches, ransomware, and hacks become almost routine news items. In 2024, these will be the top cybersecurity trends.
A. Exciting Mobile Cyber Security Research Paper Topics
- The significance of continuous user authentication on mobile gadgets.
- The efficacy of different mobile security approaches.
- Detecting mobile phone hacking.
- Assessing the threat of using portable devices to access banking services.
- Cybersecurity and mobile applications.
- The vulnerabilities in wireless mobile data exchange.
- The rise of mobile malware.
- The evolution of Android malware.
- How to know you’ve been hacked on mobile.
- The impact of mobile gadgets on cybersecurity.
B. Top Computer and Software Security Topics to Research
- Learn algorithms for data encryption
- Concept of risk management security
- How to develop the best Internet security software
- What are Encrypting Viruses- How does it work?
- How does a Ransomware attack work?
- Scanning of malware on your PC
- Infiltrating a Mac OS X operating system
- What are the effects of RSA on network security ?
- How do encrypting viruses work?
- DDoS attacks on IoT devices
C. Trending Information Security Research Topics
- Why should people avoid sharing their details on Facebook?
- What is the importance of unified user profiles?
- Discuss Cookies and Privacy
- White hat and black hat hackers
- What are the most secure methods for ensuring data integrity?
- Talk about the implications of Wi-Fi hacking apps on mobile phones
- Analyze the data breaches in 2024
- Discuss digital piracy in 2024
- critical cyber-attack concepts
- Social engineering and its importance
D. Current Network Security Research Topics
- Data storage centralization
- Identify Malicious activity on a computer system.
- Firewall
- Importance of keeping updated Software
- wireless sensor network
- What are the effects of ad-hoc networks
- How can a company network be safe?
- What are Network segmentation and its applications?
- Discuss Data Loss Prevention systems
- Discuss various methods for establishing secure algorithms in a network.
- Talk about two-factor authentication
E. Best Data Security Research Topics
- Importance of backup and recovery
- Benefits of logging for applications
- Understand physical data security
- Importance of Cloud Security
- In computing, the relationship between privacy and data security
- Talk about data leaks in mobile apps
- Discuss the effects of a black hole on a network system.
F. Important Application Security Research Topics
- Detect Malicious Activity on Google Play Apps
- Dangers of XSS attacks on apps
- Discuss SQL injection attacks.
- Insecure Deserialization Effect
- Check Security protocols
G. Cybersecurity Law & Ethics Research Topics
- Strict cybersecurity laws in China
- Importance of the Cybersecurity Information Sharing Act.
- USA, UK, and other countries' cybersecurity laws
- Discuss The Pipeline Security Act in the United States
H. Recent Cyberbullying Topics
- Protecting your Online Identity and Reputation
- Online Safety
- Sexual Harassment and Sexual Bullying
- Dealing with Bullying
- Stress Center for Teens
I. Operational Security Topics
- Identify sensitive data
- Identify possible threats
- Analyze security threats and vulnerabilities
- Appraise the threat level and vulnerability risk
- Devise a plan to mitigate the threats
J. Cybercrime Topics for a Research Paper
- Crime Prevention.
- Criminal Specialization.
- Drug Courts.
- Criminal Courts.
- Criminal Justice Ethics.
- Capital Punishment.
- Community Corrections.
- Criminal Law.
Cyber Security Future Research Topics
- Developing more effective methods for detecting and responding to cyber attacks
- Investigating the role of social media in cyber security
- Examining the impact of cloud computing on cyber security
- Investigating the security implications of the Internet of Things
- Studying the effectiveness of current cyber security measures
- Identifying new cyber security threats and vulnerabilities
- Developing more effective cyber security policies
- Examining the ethical implications of cyber security
Cyber Security Topics For Research Paper
- Cyber security threats and vulnerabilities
- Cyber security incident response and management
- Cyber security risk management
- Cyber security awareness and training
- Cyber security controls and countermeasures
- Cyber security governance
- Cyber security standards
- Cyber security insurance
- Cyber security and the law
- The future of cyber security
5 Current Research Topics in Cybersecurity
Below are the latest 5 cybersecurity research topics. They are:
- Artificial Intelligence
- Digital Supply Chains
- Internet of Things
- State-Sponsored Attacks
- Working From Home
Research Area in Cyber Security
The field of cyber security is extensive and constantly evolving. Its research covers a wide range of subjects, including:
- Quantum & Space
- Data Privacy
- Criminology & Law
- AI & IoT Security
- RFID Security
- Authorisation Infrastructure
- Digital Forensics
- Autonomous Security
- Social Influence on Social Networks
How to Choose the Best Research Topics in Cyber Security
A good cybersecurity assignment heading is a skill that not everyone has, and unfortunately, not everyone has one. You might have your teacher provide you with the topics, or you might be asked to come up with your own. If you want more research topics, you can take references from Certified Ethical Hacker Certification, where you will get more hints on new topics. If you don't know where to start, here are some tips. Follow them to create compelling cybersecurity assignment topics.
1. Brainstorm
In order to select the most appropriate heading for your cybersecurity assignment, you first need to brainstorm ideas. What specific matter do you wish to explore? In this case, come up with relevant topics about the subject and select those relevant to your issue when you use our list of topics. You can also go to cyber security-oriented websites to get some ideas. Using any blog post on the internet can prove helpful if you intend to write a research paper on security threats in 2024. Creating a brainstorming list with all the keywords and cybersecurity concepts you wish to discuss is another great way to start. Once that's done, pick the topics you feel most comfortable handling. Keep in mind to stay away from common topics as much as possible.
2. Understanding the Background
In order to write a cybersecurity assignment, you need to identify two or three research paper topics. Obtain the necessary resources and review them to gain background information on your heading. This will also allow you to learn new terminologies that can be used in your title to enhance it.
3. Write a Single Topic
Make sure the subject of your cybersecurity research paper doesn't fall into either extreme. Make sure the title is neither too narrow nor too broad. Topics on either extreme will be challenging to research and write about.
4. Be Flexible
There is no rule to say that the title you choose is permanent. It is perfectly okay to change your research paper topic along the way. For example, if you find another topic on this list to better suit your research paper, consider swapping it out.
The Layout of Cybersecurity Research Guidance
It is undeniable that usability is one of cybersecurity's most important social issues today. Increasingly, security features have become standard components of our digital environment, which pervade our lives and require both novices and experts to use them. Supported by confidentiality, integrity, and availability concerns, security features have become essential components of our digital environment.
In order to make security features easily accessible to a wider population, these functions need to be highly usable. This is especially true in this context because poor usability typically translates into the inadequate application of cybersecurity tools and functionality, resulting in their limited effectiveness.
Writing Tips from Expert
Additionally, a well-planned action plan and a set of useful tools are essential for delving into Cyber Security Research Topics. Not only do these topics present a vast realm of knowledge and potential innovation, but they also have paramount importance in today's digital age. Addressing the challenges and nuances of these research areas will contribute significantly to the global cybersecurity landscape, ensuring safer digital environments for all. It's crucial to approach these topics with diligence and an open mind to uncover groundbreaking insights.
- Before you begin writing your research paper, make sure you understand the assignment.
- Your Research Paper Should Have an Engaging Topic
- Find reputable sources by doing a little research
- Precisely state your thesis on cybersecurity
- A rough outline should be developed
- Finish your paper by writing a draft
- Make sure that your bibliography is formatted correctly and cites your sources.
Discover the Power of ITIL 4 Foundation - Unleash the Potential of Your Business with this Cost-Effective Solution. Boost Efficiency, Streamline Processes, and Stay Ahead of the Competition. Learn More!
Studies in the literature have identified and recommended guidelines and recommendations for addressing security usability problems to provide highly usable security. The purpose of such papers is to consolidate existing design guidelines and define an initial core list that can be used for future reference in the field of Cyber Security Research Topics.
The researcher takes advantage of the opportunity to provide an up-to-date analysis of cybersecurity usability issues and evaluation techniques applied so far. As a result of this research paper, researchers and practitioners interested in cybersecurity systems who value human and social design elements are likely to find it useful. You can find KnowledgeHut’s Cyber Security courses online and take maximum advantage of them.
Frequently Asked Questions (FAQs)
Businesses and individuals are changing how they handle cybersecurity as technology changes rapidly - from cloud-based services to new IoT devices.
Ideally, you should have read many papers and know their structure, what information they contain, and so on if you want to write something of interest to others.
The field of cyber security is extensive and constantly evolving. Its research covers various subjects, including Quantum & Space, Data Privacy, Criminology & Law, and AI & IoT Security.
Inmates having the right to work, transportation of concealed weapons, rape and violence in prison, verdicts on plea agreements, rehab versus reform, and how reliable are eyewitnesses?

Mrinal Prakash
I am a B.Tech Student who blogs about various topics on cyber security and is specialized in web application security
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cyber Security Batches & Dates
The future of cybersecurity

With TikTok in the hands of 170 million Americans, cybersecurity expert Amy Zegart says it’s time to talk about consequences. Foreign access to all that data on so many Americans is a national security threat, she asserts.
For those as concerned as she, Zegart has good news and bad. The government has gotten better at fighting cyberthreats, but artificial intelligence is making things very complicated, very fast. The US needs to adapt quickly to keep pace, Zegart tells host Russ Altman on this episode of Stanford Engineering’s The Future of Everything podcast.
Listen on your favorite podcast platform:
Related : Amy Zegart , senior fellow at The Hoover Institution, Freeman Spogli Institute for International Studies (FSI), and Stanford Institute for Human Centered Artificial Intellligence (HAI)
[00:00:00] Amy Zegart: What we really need to pursue much more seriously is developing independent capacity. Developing the talent, developing the compute that, I know at Stanford's been really pushing this idea of a national AI, research resource. That's fancy talk for compute power so that independent researchers can ask hard questions, uh, and do the kind of analysis that, that needs to be done.
[00:00:27] I think we need to be investing much more in that. Compute is a strategic national asset like oil. And the government should be investing orders of magnitude more and making that available.
[00:00:44] Russ Altman: This is Stanford Engineering's The Future of Everything podcast, and I'm your host, Russ Altman. If you're enjoying the show or if it's helping you in any way, please consider sharing it with friends, family, and colleagues. Personal recommendations are one of the best ways to spread the news about the podcast.
[00:00:59] Today, Amy Zegart from Stanford University will tell us about cybersecurity and AI. How have things changed in the last three or four years since she was last a guest on The Future of Everything? It's the future of cybersecurity.
[00:01:13] Before we get started, a quick reminder that if you're enjoying this show, please consider sharing it with friends and family. Personal recommendations really do work in growing the podcast audience and improving the podcast.
[00:01:31] Cybersecurity is a huge issue for the United States. Computers are one of the battlefields where the next big conflicts are and will be waged. Specifically, we focus on four countries that are the source of lots of cyber attacks. These include Russia, China, North Korea, and Iran. Intelligence is complicated, and it's gotten more complicated in the last few years with the rise of AI.
[00:01:55] Now, disinformation can be generated and spread more quickly and more realistic looking. Amy Zegart is a senior fellow at the Hoover Institute, the Freeman Spogli Institute for International Affairs, and the Institute for Human Centered AI at Stanford University. She's an expert in cybersecurity. She's written several books and she's an advisor to the nation.
[00:02:17] She's going to tell us that AI has accelerated the work of both the good guys trying to combat cyber warfare and cyber attacks, as well as, unfortunately, the bad guys who are making the attacks. However, things are looking better and there's reason to be optimistic. Amy, you're a return visitor to The Future of Everything.
[00:02:37] It's a great honor for me. You can decide if it's an honor for you or not. Last time we discussed cyber security and you said something very memorable, which is that the cyber security world is moving at light speed and the government is moving at government speed. Now in the interim, since you were last on the show, there's this thing called AI that has just exploded. ChatGPT and many other technologies. Has that changed the situation? Is the government able to respond faster? Are the cyber attacks able to come faster? Both, neither. Where are we these days with respect to the relative strengths of the government and of the cyber attackers?
[00:03:18] Amy Zegart: Well, Russ, thanks for starting me off with such a softball question. It's really an honor to be back with you too. It's a complicated question. There's good news and bad news. Let me start with the good news. Government has matured. So part of the challenge, as you know, of dealing with cyber is do we have capacity in the government to understand and coordinate and work with the private sector?
[00:03:40] That's gotten a lot better. So we have the creation of the National Cyber Director. That office has matured. There's a state department ambassador at large for cyber. That's a really important component to it. Um, secondly, there are SEC regulations now.
[00:03:55] Russ Altman: Wow.
[00:03:55] Amy Zegart: So there's an incentive for corporate boards to pay much more attention to cyber security. And when the incentives are aligned, of course, companies pay more money for cybersecurity, do a lot more investing in cybersecurity. So that, those SEC rules have kicked in. And I think that's important to bear in mind.
[00:04:12] Russ Altman: Can you, just to take, just to dive down, why would the SEC, why does the SEC even regulate that? I'm a little bit surprised. I think of them as regulating, you know, disclosures about the company and the financials and all that kind of stuff, monopolies, where does cybersecurity come into their kind of purview?
[00:04:28] Amy Zegart: I think there's a sense that it's a question of governance and it's not, the SEC regulations aren't dictating specific cybersecurity actions, but they are incentivizing processes. So corporate directors are held responsible for oversight of cybersecurity. And that's then catalyzed a whole bunch of other things, you know, regular reporting and in private and public companies as well.
[00:04:53] Russ Altman: And it's not the case that the companies would have been independently motivated not to be attacked, not to have ransomware? I'm just surprised that we needed to tell them this.
[00:05:02] Amy Zegart: Well, many companies are incentivized. When you think about financial services, for example, they've invested an enormous amount of money in their cyber security, and they know they need to. But many companies think that cyber security is really for the big guys. Cyber security is for the sexy industries. Remember Home Depot? When Home Depot got hacked?
[00:05:20] Russ Altman: Yes.
[00:05:20] Amy Zegart: Right? Their defense was, we just sell hammers. Why are we a victim of cyber attacks? So, when you think about,
[00:05:27] Russ Altman: Now the bad guys know about my wheelbarrow.
[00:05:30] Amy Zegart: Exactly. So when you think about the cyber attack surface, it's everywhere. So you really want to incentivize all companies to spend more money and pay more attention to cybersecurity. I think that's,
[00:05:41] Russ Altman: Sorry, I interrupted you on that because I was just surprised. Keep going. Yeah.
[00:05:44] Amy Zegart: So that's the plus side of the ledger. The negative side of the ledger, and you asked about AI, is AI makes everything more complicated and faster. So is AI being used to automate cybersecurity on the defensive side? Yes. Is AI used to automate offensive attacks against cybersecurity defenses? Yes.
[00:06:04] So it sort of washes out. It's good news and bad news on that side. But let me add one other, uh, depressing wrinkle to the story, which is, of course, what are the attackers thinking? What are their capabilities? And what are their intentions? And there, the picture is bad. So I want to read to you the intelligence threat assessment, the annual intelligence threat assessment that was just delivered last month by the Director of National Intelligence to Congress. And this is about China. This is what the intelligence community’s assessment said.
[00:06:38] If Beijing believed that a major conflict with the United States were imminent it would consider aggressive cyber operations against U.S. critical infrastructure, by the way, that means just about everything, and military assets. It goes on to say, designed to induce societal panic.
[00:07:02] What they're saying is, it's not just if a war breaks out, if China believes conflict is imminent, they're already in our systems. And they have an incentive and an interest in attacking. So the bad guys are out there. Just because they haven't attacked us yet, doesn't mean they won't. So when you think about nation states with real cyber capabilities, China, Russia, Iran, North Korea, they're out there and they have not been defeated on the cyber landscape.
[00:07:30] Russ Altman: I'm glad you mentioned our favorite four countries because, uh, because I wanted to ask you, are they, are there, I'm suspecting that their interests are not precisely aligned and that they all have a different kind of, uh, piece of the game in mind. So you just kind of described how China might be thinking of it as a defensive slash offensive, basically a weapon for a potential, uh, conflict with the U.S., is that the same kind of thinking that Russia is doing? Or are they just, they seem more random? That's why I ask, because they seem more random in their attacks.
[00:08:04] Amy Zegart: There are different flavors of their interests, right? So Russia is really focused on the disinformation space. So think about foreign election interference. So the Russians really like that space, uh, fomenting, uh, you know, exacerbating polarization in the United States. By the way, the Chinese are trying to do that too. The Iranians too, but Russia is the A team. That's, they're really good at that. The North Koreans want to steal. Right? So they're trying to steal everything they can in cyberspace. When you think about ransomware, I think primarily North Koreans, Russians too.
[00:08:35] Russ Altman: Okay.
[00:08:35] Amy Zegart: But they're really in it for the money. The Iranians have sort of a vengeful attitude towards cyber attacks. So you'll see cyber attacks against, um, particular targets like casinos, right? And they're very vengeful, uh, in there, like specifically targeting, uh, you know, assets that are owned by people that say things that they don't like.
[00:08:58] Now that's a broad simplification of the differences between these four countries, but they're all very capable cyber adversaries. Uh, and those capabilities are growing over time. So it's a cat and mouse defense offense game.
[00:09:13] Russ Altman: And can you update us on the issue of Russia? What have we learned from the Russian Ukrainian conflict? Has Russia, uh, have they been successful in kind of as part of their to include the cyber security or have the Ukrainians successfully fended them off? And are we learning anything by watching this conflict? Are we learning anything that could be useful to us in combating the Russians?
[00:09:37] Amy Zegart: So yes and yes.
[00:09:38] Russ Altman: Okay, good.
[00:09:39] Amy Zegart: Yes. Um, I think the narrative of the Russian cyber attacks against Ukraine at the start of the war turns out to be not quite right. You'll remember at the start of the war, the big question was, how come they didn't do more in cyberspace? They actually did do a lot in cyberspace, we now know, right?
[00:09:58] They attacked Viasat, so this is a pretty significant cyber attack. And they tried to do a lot more. Why didn't they succeed is the question, is the more important question. Part of the answer we now know is that United States Cyber Command was helping the Ukrainians weeks before the Russian attack.
[00:10:18] And so this was about moving critical digital assets to safer, uh, configurations. This was about fending off attacks. This was about working side by side with the Ukrainians to try to mitigate the risk of a cyber sort of first strike that would really take them out. And so we know a lot more now that's been revealed publicly about U.S. Cyber Command's role there.
[00:10:40] The other thing I think that we learned is that cyber attacks in an ongoing conflict are actually really hard to pull off, right? So it's one thing to initiate an attack at the start of a conflict where you're planning to go in.
[00:10:53] Russ Altman: The surprise.
[00:10:54] Amy Zegart: But then sustaining that level of activity and adapting to the threat landscape turns out to be much harder.
[00:11:03] Russ Altman: Really interesting. Okay. So, um, all right. So you gave a great answer to my initial question. And the answer is that the cyber guys have gotten faster. The government is a little bit, is more on board and presumably is getting faster. Um, what about a domestic? I know that you've spent a lot of time thinking about, uh, global threats. Um, I think you also think about internal, um, domestic threats. Um, Is that true?
[00:11:29] Amy Zegart: Not so much. I worry about things coming from outside the United States, not inside the United States.
[00:11:35] Russ Altman: Okay. So tell me about, um, have they gotten, so misinformation, I want to talk about misinformation. Um, you already alluded to it as especially like messing up elections. Uh, and generally it's an attempt to create chaos. Is that how I should think about it?
[00:11:52] Amy Zegart: So it depends. So let's just talk a little bit about terminology. So misinformation is information that is wrong, but people are mistakenly sending it around, right? So this is your crazy uncle sending things that he may think may be true, but are actually not true.
[00:12:08] So disinformation is a deliberate effort by somebody to spread something that they know to be false. We have both problems. People spreading things that are patently false, but they don't know they're false and they go viral. And then nefarious actors, domestic and foreign, that are knowingly spreading information that is false.
[00:12:28] And in that category, right, there are a variety of motives, but from a foreign adversary perspective, it is to fray the bonds of democratic societies that bring us together. Anything that gets you and me to fight with each other about what's true or what's not, or what we believe in and, um, what our values are in conflict benefits these adversaries.
[00:12:50] Russ Altman: Yeah. So, and I've heard that. And so, you know, as you may be aware, Uh, there is a lot of splits in the U.S. right now, politically, and it makes me wonder when you say things like what you just said, um, is some of that manufactured not from deeply held beliefs of the two sides. Uh, but from external sources, and that would actually, in a funny way, be a hopeful thing, because it might imply that we actually have a chance to resolve some of these divides if we could kind of get the noise from the, uh, external pertur, perturbators out, but I don't know if that's too Pollyanna.
[00:13:25] I'm sure it is too Pollyannaish. So how should I think about when I look at the political divides in the U.S.? Do we have a sense for how much is that created from external sources and how much is in some sense? Like real, or is that not even a question that makes sense?
[00:13:39] Amy Zegart: I think it's a great question. I don't think we know the answer. It's so hard to unravel what are the roots of, uh, the particular information that's being spread. Now there are researchers that are trying to do this, but that they're caught in the political maw as well, right? Seen as either censoring or favoring one side or the other. It's a really hard thing to unwind.
[00:14:00] And of course our adversaries are getting better at it and hiding their tracks. So you think back to, you know, Russia's early efforts to interfere with a presidential election. And, uh, we may have talked about this in the last time I came on. You know, you could easily trace it back after the fact to Facebook groups that were created by Prigozhin in St. Petersburg in an office with trolls that, you know, came to work nine to five and they masqueraded as Americans trying to get followers and getting Americans to be pitted against each other. Not just online, but in real life, right? On the streets of Texas, protesting against each other, all fomented by the Kremlin.
[00:14:40] Now it's a lot harder. And, you know, you think about TikTok, for example, the Chinese don't need the Russian playbook, which is utilize American platforms against ourselves. They have their own platform. Directly into the hands of forty percent of Americans, which is why there's been this whole bruhaha about banning TikTok or forcing a sale of TikTok. It is a legitimate national security concern.
[00:15:04] Russ Altman: Great. Okay. Now there's something juicy and meaty we can talk about. So there are these big tech companies and uh, TikTok is a great example because I have graduate students who are ready to hit the streets in protest if, uh, if TikTok is shut down, because it evidently has become a huge part of their life. Um, so talk to me about your perception of the real risks of TikTok, uh, versus kind of manufactured political rhetoric that you think is not so beefy.
[00:15:35] Amy Zegart: So I will say, and I mentioned this to General Nakasone when he was the head of Cyber Command and the National Security Agency, that, um, we were talking about our kids, I said, you know, I have a college daughter, and she runs her team's TikTok page, right?
[00:15:47] Russ Altman: Right, exactly. There you go.
[00:15:49] Amy Zegart: How do you, and you know, and I had to send a note to the parents saying, hey, if you want to know what your kids are up to on TikTok, uh, you can take a look, but I have to tell you it's a national security threat.
[00:16:00] Russ Altman: Oh my god. Oh, what a great message that would have been to get.
[00:16:03] Amy Zegart: So it was a bit of an awkward position to be in. So yes, I hear what you're saying, particularly young people, they get their news from TikTok. TikTok is a very big part of their life. So why do we care so much?
[00:16:15] Russ Altman: They'll ask me, what's email? What's Instagram? Facebook is for my grandmother. It's all about TikTok. And they also say, just be, sorry to interrupt you. They also say, and these are my technical students, my computer science, or they say that we don't know how their algorithm works, but it is light years better than all the other algorithms in terms of putting things in front of me that I find interesting.
[00:16:37] Amy Zegart: Yeah. And by the way, that's one of the reasons China may not want to actually divest TikTok to an American buyer because they don't want that IP, that algorithm to be in foreign hands.
[00:16:49] Russ Altman: Yes, it seems to be magically good.
[00:16:50] Amy Zegart: So this dilemma, the U.S. is trying to force a sale. China doesn't want to sell. It's going to be very interesting to see what happens.
[00:16:57] But back to your question about what's the real national security concern about TikTok? There are several. Number one, access to data. So TikTok executives have been saying, no, no, no, no, no. There's a firewall between American data and Chinese access to the data. That is not true. Right? We know empirically that is not true.
[00:17:17] So data on a hundred and seventy million Americans can be accessible by Chinese owners of this company. And we know the national security law in China mandates that companies turn over data when asked.
[00:17:31] Russ Altman: Is this data generated within the app or is this even other stuff on your phone that can be grabbed?
[00:17:37] Amy Zegart: That I don't know.
[00:17:39] Russ Altman: Okay, but it's at least what I'm watching on TikTok, what I'm typing into TikTok, maybe where I am, if there's geolocation. I don't know if there's geolocation on TikTok.
[00:17:48] Amy Zegart: So let me put it to you this way, Russ. Imagine the U.S. government had the ability to reach into the phones of forty percent of citizens in China. And know with the algorithm what gets their attention, what they like and what they don't. How much would we pay to have that kind of access to the populace of a foreign country?
[00:18:10] Russ Altman: And that's what they have.
[00:18:11] Amy Zegart: That's what they have, right? That's what our kids and your students have. So that's issue number one is access to the data.
[00:18:19] Number two is influence. So it doesn't have to be a heavy handed, the Chinese Communist Party is great kind of TikTok algorithm, right? Where you're, you know, the viewers or my daughter is suddenly watching this. It can be things at the margin, right? You probably saw the story about Osama Bin Laden really had legitimate grievances when he masterminded the nine eleven attack.
[00:18:42] Just horrifying things. But on TikTok, this messaging went viral. Now, I don't know whether this was deliberately put there, right, by, in a deliberate effort by a foreign adversary, but you can see how ideas, if a government wanted to influence opinion on issues, uh, it would be pretty easy to do.
[00:19:03] Russ Altman: Yeah, and your point is a really good one, that these can be nudges and not bludgeons.
[00:19:07] Amy Zegart: Right.
[00:19:08] Russ Altman: And actually nudges are probably more insidious and difficult to find and are way less detectable.
[00:19:15] Amy Zegart: That's a better way of putting it than what I just said. Yes.
[00:19:17] Russ Altman: This is The Future of Everything. I'm Russ Altman. We'll have more with Amy Zegart next.
[00:19:36] Welcome back to The Future of Everything. I'm Russ Altman, your host, and I'm speaking with Amy Zegart from Stanford University.
[00:19:42] In the last segment, Amy described to us some of the changes that have happened since we last spoke with her in cybersecurity threat assessment and also response. In this segment, we're going to talk about the role of corporations. They have more compute power, not only more than academics. In many cases, they have more than the government has to use in building AI tools. This has created new challenges for regulation and for collaboration between industry and government and academics.
[00:20:11] Amy, to start off this segment, I wanted to ask you about the role of corporations. We talked about it a tiny bit when we're talking about the SEC regulations, but there are these big tech companies that are really holding AI and controlling AI. What is the role of the corporation in national security these days?
[00:20:28] Amy Zegart: Well Russ, the role of the corporation is totally different than it was when we were growing up. So it used to be that innovations were invented in the government and then they became commercialized, right? You think about the internet started that way, or GPS satellites. And now the script has flipped. So now innovations, and we see this with large language models, are being invented outside of the government, and the government has to figure out not only what to do about that in the private sector, but how to bring those capabilities into the government itself.
[00:20:57] That's a new world for them. We're in a world right now where a handful of companies really dwarf the capacity of the government or universities to, uh, to compete and understand these large language models.
[00:21:12] Russ Altman: And there is no way that me and my friends could have built ChatGPT. We don't have a tenth of the compute power we would need.
[00:21:21] Amy Zegart: And I think Russ, many people don't know that, right? So the orders of magnitude of compute power, right? So how much more compute power does OpenAI have than Stanford, for example? I mean, you know, it's, you know, you probably don't have,
[00:21:37] Russ Altman: It's ten to a hundred, it's a hundred X. It's a hundred X.
[00:21:40] Amy Zegart: So I was trying to find a specific number cause I'm writing about this now. And I saw an announcement that Princeton is buying, is very excited, that they're buying three hundred NVIDIA chips by the end of the year. Meta is expected to have three hundred and fifty thousand, right? So,
[00:21:59] Russ Altman: So it's a thousand X. I was off by an order of magnitude. You're right.
[00:22:03] Amy Zegart: And so what that means is that these companies are not just at the forefront of innovating, they're grading their own homework, right? Because how do you know what's safe? How do you know what potential risks there are? What kinds of questions do you need to ask? They're deciding those things largely by themselves, and that's never a good setup. I would say that, but I also want to emphasize that we don't want to impede innovation.
[00:22:26] So the question is, how do you strike the right balance between mitigating harms from these AI models. And how do you make sure that we're allowing the private sector leaders in this space, and they are all American at this moment, to continue innovating in ways that help, you know, there's so many positive benefits to these models as well. So we don't want to impede that either.
[00:22:47] Russ Altman: So what is the approach? I mean, is it now requiring government to have some kind of super awkward type of conversations that it's not used to having where it's kind of, it has to be a little bit more humble, perhaps, and come to the companies and say, hey, could we work together?
[00:23:04] I mean, first of all, I presume that they're a part of the national security infrastructure. We would want to use many of those technologies to combat, uh, threats. On the other hand, um, they're not under the control of the government and they might say things like, who's going to pay for that? Or, you know, how much should the license that the government pays us, how much should that cost? And so, how far are we at figuring out how this new dance should be danced?
[00:23:30] Amy Zegart: Well, you know, we just talked about cyber and how long it took to sort of get the maturation of cyber organization in the U.S. government. We're on day one for AI. So we are not far along at all. Yes, there are awkward conversations. You can see them on television when Sam Altman goes to testify before Congress. You know, many members of Congress are learning how to spell AI. So we have a, we have an expertise challenge there too. So at one point I counted the number of members of Congress that had engineering degrees. I think it was in 2020.
[00:24:00] You will be unsurprised to know more than half the Senate had law degrees. And there were, I think, three engineers. Which is actually more than I thought there would be. So that's part of the challenge too, is, you know, ordinary folks don't know enough to be able to ask the right oversight questions.
[00:24:16] Russ Altman: So here's overly optimistic Russ's next question. Did we learn from cyber so many lessons that AI is going to be easier? Based on the cyber experience, or are we basically starting from scratch?
[00:24:28] Amy Zegart: I think I'm trying to be optimistic. I'm trying to get your optimism, Russ. Yes, we have learned some lessons. You can see efforts early on at conversation, both on the private sector side. They know they've got this powerful technology and they're concerned about the risks. I don't want to overstate.
[00:24:45] Russ Altman: They want to be patriots to some degree, I would guess, slash hope.
[00:24:49] Amy Zegart: And they know that what they have has great promise and also great peril and trying to harness the upside while mitigating the downside is in everybody's interest.
[00:24:58] So those conversations are happening. We don't have the Edward Snowden problem. So you remember in 2013, former NSA contractor revealed highly classified programs, and it really sowed distrust, deep distrust between companies here in the Valley and the government. We don't have that right now.
[00:25:15] Thanks to Xi Jinping and Vladimir Putin there's a joint concern about authoritarians in the world and the bad they can do. So that's good. We have learned from that, but you know, there is this question of what do we do, given that there's just this capacity differential between talent and compute and algorithms and a handful of companies and what everybody else can do.
[00:25:38] And I think we have three options. One is regulation. I'm concerned about that because you can really, you know, uh, throw the baby out with the bath water. Two is do nothing, let them grade their own homework. That concerns me too. What happens if, uh, people violate OpenAI's rules in the presidential election? They, they go to OpenAI jail, right? I mean, it's voluntary compliance.
[00:25:59] Russ Altman: No chat for you.
[00:26:01] Amy Zegart: So that's the world we're in right now. And then the third option, I think this is what we really need to pursue much more seriously is developing independent capacity. Developing the talent, developing the compute thing.
[00:26:15] I know Stanford's been really pushing this idea of a national AI research resource. That's fancy talk for compute power so that independent researchers can ask hard questions, uh, and do the kind of analysis that, that needs to be done. I think we need to be investing much more in that. Compute is a strategic national asset like oil and the government should be investing orders of magnitude more and making that available.
[00:26:44] Russ Altman: You know, as a biomedical researcher, I'm very aware of this because whenever, for example, the drug industry gets out ahead of NIH researchers, the NIH has a history, and I've seen this several times in my career, of making huge investments to try to level the playing field so that academic can kind of not really compete with the pharmaceutical industry. But do things at the same scale.
[00:27:05] And I'm somewhat surprised to not have seen a government scale, uh, AI resource that's as big as Facebook's or OpenAIs or Anthropics or, it's just surprising because the government can definitely afford it. Yes, it's expensive, but you know, the government has a bigger budget than Facebook even and so it's just surprising and maybe we'll see this.
[00:27:27] Um, let me just ask you, you mentioned about regulation. I'm sure you have opinions about the Europeans. As you know, the Europeans have been very aggressive at um, kind of AI and data protections. What's your take on that in terms of the security implications? Is that a model that the U.S. should seriously look at? Or do you have concerns about how they've approached it?
[00:27:47] Amy Zegart: I understand where they're coming from, and the Europeans share our values. And so I think that the impetus, I understand. I think their hearts in the right place, but I don't think it's a coincidence that the leading AI companies in the world are not coming out of Europe.
[00:28:01] They're coming out of the United States. Our, you know, wild west approach to innovation, hands off regulation is both a feature and a bug, right? It is what is fostering this innovation explosion that we've had for a long time. But it also means that we have a harder time mitigating the harms. So what I think is most promising and what the Europeans have done, two things.
[00:28:26] One is starting an international conversation about norms. That's really important. Ultimately, I think that we also need a serious bilateral conversation about AI guardrails between the U.S. and China. Things like AI and nuclear command and control, AI and financial system security, things where we have mutual interests, we need to have that.
[00:28:48] But the multilateral approach is important, too, for building norms about what's acceptable and what isn't. The second thing the Europeans are doing is the UK has really taken the lead on their AI Safety Institute. Independent capacity building to really understand what the risks of this technology could be.
[00:29:06] Now it's a beginning, it's not an end. The United States is behind. We're behind in our organization. We're behind in our funding compared to the Brits. And as you probably know, now there's conversation about how can we join our efforts together. And I think that's very promising.
[00:29:21] Russ Altman: Great. So to finish up. How is AI going to help intelligence? Like, I know that the bad guys might use AI as well, but what are some of the ways, like, kind of tangible ways that we should be excited about AI helping increase our security and safety?
[00:29:36] Amy Zegart: So, I do think there is some good news of the potential of AI. So, it can help intelligence in a number of ways.
[00:29:43] First, you have to think about intelligence isn't really about secrets, it's about insight. So the question is, how can analysts sitting inside the Central Intelligence Agency better develop insight about what's going on around the world? Well, what can AI do? AI can do pattern recognition at scale and speeds that humans cannot.
[00:30:02] So you think about an analyst, there was actually an experiment done several years ago by the National Geospatial Intelligence Agency. And they had a human team and an AI team looking at identifying surface to air missile sites over a huge swath of territory. The humans and the algorithms did the, had the same level of accuracy, ninety percent accuracy, but the AI did it eighty times faster.
[00:30:28] What does that mean? Now you're freeing up the human analysts to do things that only humans can do well, like thinking about intention. What does the adversary intend to do with those surface to air?
[00:30:40] Russ Altman: Why are they pointing in that direction?
[00:30:42] Amy Zegart: Why are they pointing in that direction? Yeah. So, so incredible efficiency gains, right?
[00:30:46] Pattern recognition. That's thing one. Thing two is AI can help find needles in haystacks. Much better than humans can pouring over images or pouring over data. And the third thing that AI can do, is AI can derive insight from the haystacks themselves. So I think about in your world, AI, um, accelerating scientific discovery, the new antibiotic at MIT, that's finding insight from mounds and mounds of data, all the haystacks, connections that humans didn't even know existed. AI can help with that.
[00:31:23] Russ Altman: Thanks to Amy Zegart, that was The Future of Cybersecurity. Thanks for tuning into this episode. With over 250 episodes in our archive, you have instant access to an extensive array of fascinating discussions on the future of pretty much everything. Please remember to hit follow in the app that you're listening to now.
[00:31:41] This will guarantee that you never miss out on the future of anything. You can connect with me on x or twitter @rbaltman. You can connect with Stanford Engineering @stanfordeng.

Regenerating worms have genetic control over their algal partners

Understanding how racism and emotion impact affordable housing support

Meet the robot that learned to sauté shrimp
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
- Home Products
- Small Business 1-49 employees
- Medium Business 50-999 employees
- Enterprise 1000+ employees
Every third cyber incident was due to ransomware, Kaspersky reports
Ransomware remains a formidable cybersecurity threat, impacting organizations and individuals globally. with the rise of targeted ransomware groups, kaspersky's latest research uncovers a concerning trend: every third cyber incident in 2023 was attributed to ransomware attacks. as the world prepares to observe international anti-ransomware day on may 12, kaspersky releases a comprehensive analysis of the current ransomware landscape. delving into major events, emerging trends, and actionable recommendations, the report sheds light on the evolving nature of ransomware threats and their implications for cybersecurity..
Kaspersky's research, spanning the years 2022 and 2023, reveals a worrisome escalation in targeted ransomware groups. The data indicates a staggering 30% global increase in the number of these groups compared to 2022, accompanied by a 71% surge in known victims of their attacks. Unlike random assaults, these targeted groups set their sights on governments, prominent organizations, and specific individuals within enterprises. With cybercriminals orchestrating sophisticated and extensive attacks, the threat to cybersecurity grows ever more pronounced.
In 2023, Lockbit 3.0 emerged as the most prevalent ransomware, leveraging a builder leak in 2022 to spawn custom variants targeting organizations worldwide. BlackCat/ALPHV ranked second, until December 2023, when a collaborative effort by the FBI and other agencies disrupted its operations. However, BlackCat quickly rebounded, underscoring the resilience of ransomware groups. Third on the list was Cl0p, which breached the managed file transfer system MoveIt, impacting over 2.5 thousand organizations by December 2023, according to New Zealand security firm Emsisoft.
Kaspersky's threat research identifies several noteworthy ransomware families, including BlackHunt, Rhysida, Akira, Mallox, and 3AM. Moreover, as the ransomware landscape evolves, smaller and more elusive groups are emerging, posing new challenges for law enforcement. The rise of Ransomware-as-a-Service (RaaS) platforms further complicates the cybersecurity landscape, emphasizing the need for proactive measures.
Kaspersky's incident response team notes that ransomware incidents accounted for every third cybersecurity incident in 2023. Attacks via contractors and service providers have emerged as prominent vectors, facilitating large-scale assaults with alarming efficiency. Overall, ransomware groups demonstrate a sophisticated understanding of network vulnerabilities and utilize a variety of tools and techniques to achieve their objectives. The use of well-known security tools, exploitation of public-facing vulnerabilities, and exploitation of native Windows commands highlight the need for robust cybersecurity measures to defend against ransomware attacks and domain takeovers.
“The escalating financial toll of ransomware attacks underscores the urgent need for governments to elevate cybersecurity strategies. As ransomware-as-a-service proliferates and cybercriminals execute increasingly sophisticated assaults, the threat to cybersecurity becomes more acute. Ransomware strikes persist as a formidable menace, infiltrating critical sectors and preying on small businesses indiscriminately. To combat this pervasive threat, it's imperative for individuals and organizations to fortify their defenses with robust cybersecurity measures. Deploying solutions such as Kaspersky Endpoint Security and embracing Managed Detection and Response (MDR) capabilities are pivotal steps in safeguarding against evolving ransomware threats,” commented Dmitry Galov, head of research center, Kaspersky’s GReAT.
Read the full report on the state of ransomware at Securelist.com.
On May 12, which is Anti-Ransomware Day , Kaspersky encourages organizations to follow these best practices that help safeguard your organization against ransomware:
- Always keep software updated on all the devices you use to prevent attackers from exploiting vulnerabilities and infiltrating your network.
- Focus your defense strategy on detecting lateral movements and data exfiltration to the internet. Pay special attention to outgoing traffic to detect cybercriminals’ connections to your network. Set up offline backups that intruders cannot tamper with. Make sure you can access them quickly when needed or in an emergency.
- Enable ransomware protection for all endpoints. There is a free Kaspersky Anti-Ransomware Tool for Business that shields computers and servers from ransomware and other types of malware, prevents exploits and is compatible with already installed security solutions.
- Install anti-APT and EDR solutions, enabling capabilities for advanced threat discovery and detection, investigation and timely remediation of incidents. Provide your SOC team with access to the latest threat intelligence and regularly upskill them with professional training. All of the above is available within Kaspersky Expert Security framework .
- Use the latest Threat Intelligence information to stay aware of actual TTPs used by threat actors.
- To protect the company against a wide range of threats, use solutions from Kaspersky Next product line that provide real-time protection, threat visibility, investigation and response capabilities of EDR and XDR for organizations of any size and industry. Depending on your current needs and available resources, you can choose the most relevant product tier and easily migrate to another one if your cybersecurity requirements are changing.
- To learn about the TTPs of the most influential ransomware groups, download our "The hateful eight" report .
Related Articles Virus News
Global mobile banking malware grows 32 percent in 2023.
We use cookies to make your experience of our websites better. By using and further navigating this website you accept this. Detailed information about the use of cookies on this website is available by clicking on more information .

Cost of living help and a future made in Australia
Strengthening medicare and the care economy.
Building a better health system than improves outcomes
Print or save page
On this page
High‑quality health services through Medicare
Boosting access to essential health services
Building a better healthcare system
The Government is investing $2.8 billion to continue its commitment to strengthen Medicare. This includes the $1.2 billion package to address pressures facing the health system, which provides:
- $882.2 million to support older Australians avoid hospital admission, be discharged from hospital earlier and improve their transition out of hospital to other appropriate care.
- $227 million to deliver a further 29 Medicare Urgent Care Clinics and boost support for regional and remote clinics. This will increase the total number of clinics across Australia to 87. Since commencing last year, existing clinics have already provided almost 400,000 bulk‑billed visits.
- $90 million to address health workforce shortages by making it simpler and quicker for international health practitioners to work in Australia.

Rohan’s daughter Zoya has been off school with a runny nose and a cough. By 6pm, she is lethargic and has a fever.
Rohan is concerned because his regular GP is now closed. Instead of waiting for hours at the emergency department, he takes Zoya to a Medicare Urgent Care Clinic, without having to make an appointment.
During the bulk billed visit, Zoya is diagnosed with an infection by the doctor and prescribed appropriate medication. Rohan and Zoya leave within an hour of arrival. Zoya makes a full recovery.
Improving health outcomes
Almost half of Australians live with a chronic condition. This Budget will provide $141.1 million for research and services for people living with chronic conditions, including bowel and skin cancer, diabetes and dementia.
To improve health outcomes, the Government is providing:
- Support for Australians to enjoy healthier, more active lives by investing $132.7 million in sport participation and performance programs.
- $825.7 million to ensure Australians can continue to access testing for and vaccinations against COVID‑19. The Government is also ensuring continued access to oral antiviral medicines on the Pharmaceutical Benefits Scheme.
- $41.6 million over two years to continue funding for alcohol and other drug treatment and support services, including the Good Sports alcohol management program for community sporting clubs.
The Government is allocating an additional $411.6 million (for a total $1.6 billion over 13 years) through the Medical Research Future Fund to continue existing research and introduce two new research missions for low‑survival cancers and reducing health inequities.
Improving access to medicines
The Government is investing $3.4 billion for new and amended listings to the Pharmaceutical Benefits Scheme, which means eligible patients can save on treatment costs.
By expanding the Closing the Gap Pharmaceutical Benefits Scheme Co‑payment Program, eligible First Nations patients will have free or cheaper access to all Pharmaceutical Benefits Scheme medicines.
Australians will benefit from $141.1 million to support and expand the National Immunisation Program.
Mental health support
The Government’s $888.1 million mental health package over eight years will help people get the care they need, while relieving pressure on the Better Access initiative and making it easier to access services.
A free, low‑intensity digital service will be established to address the gap for people with mild mental health concerns. From 1 January 2026, Australians will be able to access the service without a referral and receive timely, high‑quality mental health support. Once fully established, 150,000 people are expected to make use of this service each year.
The Government is improving access to free mental health services through a network of walk‑in Medicare Mental Health Centres, built on the established Head to Health network. The upgraded national network of 61 Medicare Mental Health Centres will open by 30 June 2026. They will provide clinical services for adults with moderate‑to‑severe mental health needs.
For Australians with complex mental health needs, funding will be provided for Primary Health Networks to partner with GPs to deliver multidisciplinary, wraparound support services and care coordination.
Improving the aged care system
Providing quality care
The Budget provides $2.2 billion to deliver aged care reforms and continue implementing recommendations from the Royal Commission into Aged Care Quality and Safety.
The new Aged Care Act will put the rights and needs of older people at the centre of the aged care system. The new Act will provide the framework for fundamental change within the aged care sector.
More Home Care Packages
The Government is investing $531.4 million to release an additional 24,100 Home Care Packages in 2024–25. This will help reduce average wait times and enable people to age at home if they prefer to do so.
Improving aged care regulation
Funding of $110.9 million over four years will support an increase in the Aged Care Quality and Safety Commission’s regulatory capabilities.
The Government is investing $1.2 billion in critical digital systems to support the introduction of the new Aged Care Act and contemporary IT systems.
The My Aged Care Contact Centre will receive $37 million to reduce call‑waiting times for people seeking information and access to aged care.
Higher wages for aged care workers
The Government has committed to fund the Fair Work Commission decision to increase the award wage for direct and indirect aged care workers once the final determination is made. This will build on the $11.3 billion already allocated to support the interim 15 per cent wage increase for aged care workers.
The Government is providing $87.2 million for workforce initiatives to attract nurses and other workers into aged care.
Reforming the disability sector
Better and more sustainable services
Getting the National Disability Insurance Scheme (NDIS) back on track
A further $468.7 million is being provided to support people with disability and get the NDIS back on track. This includes:
- $214 million over two years to fight fraud and to co‑design NDIS reforms with people with disability, announced earlier this year
- $160.7 million to upgrade the NDIS Quality and Safeguards Commission’s information technology
- $45.5 million to establish a NDIS Evidence Advisory Committee
- $20 million to start consultation and design on reforms to help NDIS participants and people with disability navigate services.
This builds on $732.9 million provided in the 2023–24 Budget.
In December 2023, National Cabinet agreed to work together to improve the experience of participants and restore the original intent of the Scheme to support people with permanent and significant disability, within a broader ecosystem of supports. This builds on an earlier decision by National Cabinet to ensure Scheme sustainability and achieve an 8 per cent growth target by 1 July 2026, with further moderation as the NDIS matures.
Improving employment for people with disability
A $227.6 million investment will support a new specialised disability employment program to replace the existing Disability Employment Services program by 1 July 2025. This includes a modern digital platform for providers and participants. These reforms will support more people with disability into sustainable work, through a program with greater flexibility, increased individual supports, and better service quality. Eligibility will be expanded to include volunteers outside the income support system and those with less than eight hours per week work capacity.
Delivering essential services
Investing in reliability and security
Strengthening resourcing for Services Australia
The Government is delivering safer and more efficient government services for all Australians.
A $1.8 billion provision will support delivery of customer and payment services. This includes funding for frontline and service delivery staff to manage claims, respond to natural disasters and improve the cyber security environment. The Government is providing $314.1 million over two years to strengthen safety and security at Services Australia centres.
The Government is investing $580.3 million over four years and $139.6 million per year ongoing to sustain the myGov platform and identify potential enhancements. A further $50 million will improve usability, safety and security of the myGov platform and ensure Services Australia can support people to protect their information and privacy.
Strengthening the Australian Taxation Office (ATO) against fraud
There will be $187.4 million to better protect taxpayer data and Commonwealth revenue against fraudulent attacks on the tax and superannuation systems. Funding will upgrade the ATO’s information and communications technologies and increase fraud prevention capabilities to manage increasing risk, prevent revenue loss, and support victims of fraud and cyber crime.
Looking after our veterans
Veterans’ claims processing is prioritised with an additional $186 million for staffing resources and $8.4 million to improve case management and protect against cyber risk. The Government will provide $222 million to harmonise veterans’ compensation and rehabilitation legislation.
A further $48.4 million will be available for Veterans’ Home Care and Community Nursing programs and $10.2 million to provide access to funded medical treatment for ill and injured veterans while their claims for liability are processed.
Back to top

IMAGES
VIDEO
COMMENTS
Volume 97, September 2023, 101804. ... The article is a full research paper (i.e., not a presentation or supplement to a poster). ... Cyber supply chain security. Cyber supply chain security requires a secure integrated network between the incoming and outgoing chain's subsystems. Therefore, it is essential to understand and predict threats ...
The survey focuses on recent research and developments in the field, highlighting the most promising applications of AI and ML in cybersecurity, such as intrusion detection and response, malware detection, and network security (Aneja et al., Citation 2023). Additionally, the survey covers the current challenges and open research questions in ...
cyber risk remains a challenge for organizational leaders. The 2023 Global Cybersecurity Outlook report presents the results from this year's study of cybersecurity and business leaders' perspectives on leading cyber issues and examines how they affect organizations around the world. Key findings include:
Traditionally, cyber-attack detection relies on reactive, assistive techniques, where pattern-matching algorithms help human experts to scan system logs and network traffic for known virus or ...
Journal of Cybersecurity | 9 | 1 | January 2023. Skip to Main Content. Advertisement. Journals. Books. Search Menu; ... Research Papers. ... A close look at a systematic method for analyzing sets of security advice. David Barrera and others. Journal of Cybersecurity, Volume 9, Issue 1, 2023, ...
About the journal. Journal of Cybersecurity publishes accessible articles describing original research in the inherently interdisciplinary world of computer, systems, and information security …. Find out more. The simple economics of an external shock to a bug bounty platform. The cybersecurity of fairy tales.
In an era where digital risks are continuously evolving, this report will serve as an indispensable resource for decision-makers seeking to fortify their cybersecurity defenses and stay ahead of the curve. Costigan, Sean S. and Ni Thuama, Rois, The State of Cyber Resilience 2023 (November 10, 2023). Red Sift | November 2023, Available at SSRN ...
The journal publishes research articles and reviews in the areas including, but not limited to: • Cryptography and its applications. • Network and critical infrastructure security. • Hardware security. • Software and system security. • Cybersecurity data analytics. • Data-driven security and measurement studies. • Adversarial ...
Developing a secure IoT ecosystem is a daunting challenge that requires a systematic and holistic approach to identify and mitigate potential security threats. Cybersecurity research considerations play a critical role in this regard, as they provide the foundation for designing and implementing security measures that can address emerging risks.
Cybersecurity is a significant concern for businesses worldwide, as cybercriminals target business data and system resources. Cyber threat intelligence (CTI) enhances organizational cybersecurity resilience by obtaining, processing, evaluating, and disseminating information about potential risks and opportunities inside the cyber domain. This research investigates how companies can employ CTI ...
Study of smart grid cyber-security, examining architectures, communication networks, cyber-attacks, countermeasure techniques, and challenges. Smart Grid (SG) technology utilizes advanced network communication and monitoring technologies to manage and regulate electricity generation and transport. However, this increased reliance on technology ...
These trends support the need for balance between people, process and technology, in order to successfully reduce cybersecurity risk.. Human-centric security design prioritizes the role of employee experience — rather than technical considerations alone — across the controls management life cycle. Drawing upon the behavioral sciences, user-experience (UX) and related disciplines, it helps ...
Cybercrime is estimated to have cost the global economy just under USD 1 trillion in 2020, indicating an increase of more than 50% since 2018. With the average cyber insurance claim rising from USD 145,000 in 2019 to USD 359,000 in 2020, there is a growing necessity for better cyber information sources, standardised databases, mandatory reporting and public awareness. This research analyses ...
A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the ...
Cybersecurity Trends 2023: Latest Research & Key Risk Contributors. Cybersecurity risk is evolving in novel ways, with growing potential to cause significant economic disruption and financial losses as attackers become more sophisticated and businesses become more interconnected. Recent analysis from Moody's highlights the risk: $22 trillion ...
Cyber Security is a blend of innovative headways, process cycles and practices. The goal of cyber security is to ensure protection of applications, networks, PCs, and critical information from attack. ... This paper reviews research work done in cybersecurity including the types of cybersecurity. The paper also discusses threats and prevention ...
This book contains best selected research papers presented at ICTCS 2023: Eighth International Conference on Information and Communication Technology for Competitive Strategies. The conference will be held in Jaipur, India during 8 - 9 December 2023. The book covers state-of-the-art as well as emerging topics pertaining to ICT and effective ...
Briefing Room. Press Release. May 7, 2024. Read the full report here. Today, the Office of the National Cyber Director (ONCD) released the 2024 Report on the Cybersecurity Posture of the United ...
The 2023 Cloud Security Report is a comprehensive study based on an extensive survey conducted among 351 cybersecurity professionals in the European Union (EU). By analyzing the latest trends in cloud adoption, identifying prevalent security challenges, and highlighting best practices, this report provides
In 2022, the award was given to the following two papers. Let's celebrate the winners mentioned below to get a taste of what to expect for the Cybersecurity Award 2023: Best Practical Paper --- Robert Buhren, Hans-Niklas Jacob, Thilo Krachenfels, and Jean-Pierre Seifert. 2021.
Here is a list of research ideas along with the cyber security research areas, tips to choose the best topic from experts and more. For enquiries call: +1-469-442-0620. For enquiries call: +1-469-442-0620. All Courses. ... A. Exciting Mobile Cyber Security Research Paper Topics. The significance of continuous user authentication on mobile gadgets.
An expert in cybersecurity surveys a rapidly evolving world where technology is racing ahead of our ability to manage it, posing risks to our national security. With TikTok in the hands of 170 million Americans, cybersecurity expert Amy Zegart says it's time to talk about consequences. Foreign access to all that data on so many Americans is a ...
Read all the papers in 2023 IEEE 10th International Conference on Cyber Security and Cloud Computing (CSCloud)/2023 IEEE 9th International Conference on Edge Co IEEE Account. Change Username/Password; Update Address; Purchase Details. Payment Options; Order History ...
Ransomware remains a formidable cybersecurity threat, impacting organizations and individuals globally. With the rise of targeted ransomware groups, Kaspersky's latest research uncovers a concerning trend: every third cyber incident in 2023 was attributed to ransomware attacks. As the world prepares to observe International Anti-ransomware Day on May 12, Kaspersky releases a comprehensive ...
The ABA TechReport 2023 pairs data from the 2023 Legal Technology Survey Report, which surveyed practicing attorneys, with analysis, observations, and predictions from experts in the legal technology field. This Cybersecurity TechReport is a partial summarization of the detailed responses contained in the 60 plus page volume.
This paper provides a thorough literature review of maritime cyber-risks and the maritime cyber-security policy framework, focusing on the concept of seaworthiness. Policy instruments in force, do not focus on cyber-threats, and the industry addresses relevant challenges, with recommendations and expertise from third parties. Moreover, increased digitization of operations, as well as the ...
I.C.S. College, Khed, Ratnagri. Abstract: In the current world that is run by technology and network connections, it is crucial to know what cyber security is. and to be able to use it effectively ...
This Budget will provide $141.1 million for research and services for people living with chronic conditions, including bowel and skin cancer, diabetes and dementia. ... This builds on $732.9 million provided in the 2023-24 Budget. ... respond to natural disasters and improve the cyber security environment. The Government is providing $314.1 ...