Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center


CYBER CRIMES: A CASE STUDY OF LEGISLATION IN PAKISTAN IN THE LIGHT OF OTHER JURISDICTIONS

This thesis appraise that cyber legislation has become a constant dilemma of Pakistan. Cyber crimes cause a great loss to national and international business community. Every day more and more digital crimes are being committed, while causing billions of dollar loss to corporations and individuals. Existing legislation does not cope with the advancement of technology. In most of the cases courts fail to find significant proof or suitable legislation to punish the criminals, eventually offenders are released. Extreme demand is emerging from Pakistani society to protect them from cyber crimes and to punish the offenders. So far, Pakistan does not have sufficient legislation to deal with such offenders. First chapter of this research will be based on general concepts of cyber crimes, such as definition, origin of the internet and evolution of it, kinds, jurisdiction issue, cyber crimes in developing and developed countries. Second chapter will be based on role of Pakistan and International community in the cyber world, further the forensic science will also be discussed in this chapter. In third chapter, the legislation of U.S will be compared with Pakistani legislation and at the end of this chapter findings will be given. On the basis of previous chapters recommendations will be given in chapter four. Electronic crimes can only be stopped if existing laws are amended and new legislation is introduced. Therefore, it is important to bring existing legislation conformity with International standards to enable law enforcement agencies to tackle different kind of criminals and bring them before the competent court of justice for punishments.
Related Papers
Marwah Obaid , Muhammad Amir
The growth of internet in Pakistan is exceptional; it reached to the heights of popularity for an ever changing medium of information and communication in a major conservative society. This brings freedom of expression, communication and information across the country which struggled to provide free speech and information access to its people. The internet penetration is increasing very rapidly; it is very important to observe the impact of it on the society; especially when the government is constantly trying to formulate the regulation for controlling the cyber space. A well regulated cyber space leads to the expansion of information technology services speedily. This paper focuses on the prevailing development of governance policies for cyber space and defies among the agencies and information technology venders. Moreover, the case study of national bank of Pakistan and other cyber crime survey shows that a lot of law making is needed in order to reduce the chances of cyber crime.
Pakistan’s Multidisciplinary Journal for Arts & Science
shaharyar sabiri
The study discussed the cyber laws in Pakistan and how these laws are preventing cybercrimes and how much these laws are up to date along with this the study also studied the legality of pirated softwares in Pakistan and internationally. Two research objectives were focused about the pirated softwares and the cyber laws of Pakistan. The study was a systematic review in which 25 articles from journals along with PECA 2016, electronic transition ordinance 2002 and cyber laws dragged in 2007 were reviewed to know the legality of pirated softwares and how these pirated softwares were treated around the globe. Concluded that there was made of laws related to cyber-crimes and up to date technologies in order to cope with the cyber-crimes that were conducted by the use of these modern devices so that the cybercriminals could be arrested and can be punished. All this should be done in order to protect the identity and privacy of the people who are using these technologies. The study concluded that there is a requirement for new laws which are up to date so that these laws can protect the country and its people and their online life so that their privacy and identity cannot be stolen.
SSRN Electronic Journal
Sabahat Akhtar 435-FSL/LLMIL/S21
Assessing the Cybercrime Legislation in Pakistan: a Comparative Study of European Union and Pakistani Cybercrime Laws 63 Pages Posted: 6 Sep 2023 Sabahat Akhtar International Islamic University Date Written: August 29, 2023 Abstract Background: With the recent development in the field of information technology, people are able to communicate in a more efficient way in cyberspace. As this efficient way of communication is used by almost everyone in this era so the interactions and the reasons for these interactions are also increased. In a normal society, disputes arise due to which laws are framed similarly in cyberspace as well these disputes are in large numbers across the world and these need well-framed laws. From this perspective, it is obvious that with the passage of time, the need for laws and proper enforcement mechanisms becomes necessary. For this purpose, the EU has made a number of cybercrime legal frameworks. Method: The research work is aimed at focusing on a comparative study of the cyber Crimes legislation in the European Union and Pakistan. The doctrinal method of research is used to critically analyze the cybercrime laws of the EU and Pakistan. This method is used in legal research to examine laws. The research design for this work is of comparative nature. This research work analyzes the EU legislation which is related to cybersecurity. It mentions all the relevant EU regulations. The second part of this study discusses the kinds of crimes which are committed in cyberspace. The third part of this research work focuses on cybercrimes in Pakistan. It focuses on the relevant cybercrime laws in Pakistan. It also comparatively analyzes the EU cybercrime laws and Pakistani cybercrime laws. It mentions a number of cases in this regard from both regions. Conclusion: It can be observed that there is a presence of lacunas in the smooth delivery of Cyber security in Pakistan as compared to the EU and there are some suggestions for pragmatic solutions to the matter regarding cybersecurity issues faced by Pakistan. This research work has helped in observing the loopholes in the Pakistani legal system. It has observed the ways in which changes in Pakistani legal framework related to cyber laws can be made so that it is in accordance with modern needs of cybersecurity. Systematic review and analysis of this data aims to highlight that updated legislation plays an important role in countering cybercrimes and that legislation should be strengthened, enhanced, and made up to mark the rapid advancement of technology in order to address the rising number of cybercrimes. It concludes that there is a need for more refined and precise cybercrime laws in Pakistan along with the need of staying updated with the changing needs of the time Keywords: Cybercrime laws, Pakistan, UK, Cybersecurity, EU Legislation
Contemporary Challenges of Digital World and Cyber Crime and Management Solutions in the light of Cyber Crime Bill 2016 of Pakistan and Islamic Management Perspective
Rabia Aamir , Dr. Umer Riaz Abbasi
A computer and a network are all that is needed for any criminal activity of cybercrime. A vigorous cybercrime legislation has, therefore, become a necessity in today’s digital age. Many nation-states take great measures to draft the inclusive laws regarding this legislation. The government of Pakistan is also working hard to amend the present laws which pursue to make sure the regulation with regards to the cyber security. Digital technology has many advantages but also has a dark side. Unfortunately, its dark side is paid much heed to which does not sit well with any code of ethics. The existence of Islam in the cyber world has created an opportunity for dialogue besides forming a new method of learning for mental and physical health The Electronic Transactions Ordinance ETO 2002 in the Islamic Republic of Pakistan forbade the illegitimate and unauthorized accessibility towards the information. It preceded the declaration of Prevention of Electronic Crimes Act PECA 2016. The Act lays down the laws for cyber- terrorist crimes which are conducted with the intent of committing terrorism. The penalty for this offense is based on the 14-year term of custody or a charge of Rs 5 million, which makes up to US $47,450. Understanding the Islamic perspective in this regard can be helpful for the betterment of the lives. Islam strictly forbids a spread of fake news through news sourcing which has increasingly become rampant in today’s cyber world which can lead towards malpractices. Thus, this research aims at sharing all the contemporary challenges with regards to the cybercrimes and possible solutions in the light of constitution in Pakistan.
Babar Saeed
The term 'Information Technology' evolved in the 1970s and if we consider a medium or large company providing goods or services, its information technology department will be responsible for storing, protecting, processing, retrieving and transmitting the information. Information Technology (IT) is a wide and varied sector, and is represented in some form in almost all the industries. It is a blend of computers and communication technology where IT professionals perform variety of duties, ranging from development and installation of applications to designing complex computer networks and databases. Although, the term 'Information Technology' is becoming more familiar to the common man some people still wonder, what is information technology? As a concept, it has evolved from the basic usage of computers, internet and processing of information in any industry. In Pakistan use of internet is growing rapidly day by day. It has given rise to new opportunities in every field we can think of – be it entertainment, business, sports or education. It is very much obvious that there are two sides to a coin; Internet also has its own advantages and disadvantages. One of the major disadvantages is Cyber-crime or misuse of Information and Technology– illegal activity committed on the internet. The internet, along with its advantages, which has made the world into a ‘Global Village’ in return, has also exposed us to security risks that come with connecting to a large network. Computers today are being misused for illegal activities like e-mail espionage, credit card fraud, spam, software piracy and so on, which invade our privacy and offend our senses. Criminal activities in the cyberspace are on the rise. In this study we would give suggestions and means with which effective enforcement of Cyber Laws in Pakistan would be implemented.
Kamran Adil
Dr. Ghulam Muhammad Kundi
mohankumar.m kumar
Each crime has its effect particularly on society, country, and the world to the immense degree. By th observation of cybercrime and its wonder, it is uncovered that like previous violations it has severely influenced social existence of people. To comprehend the impact of cybercrime, it is important to consider the effect of two things PC innovation and Web on individuals as cybercrime is most likely starting out of these. This article depicts the distinctions of the Indian point of view and Europe viewpoint in Digital Crimes.
International Journal of Information and Electronics Engineering
Hossein Taji
Journal of Information Engineering and Applications
RELATED PAPERS
8th Intl Conf on Fourier Transform Spectroscopy
Richard Crocombe
Charles Putnam
Aileen CaterSteel
Jurnal Ilmiah Ekonomi Dan Bisnis
Fabricio Piacente
Trends in Genetics
Revista Brasileira de Zootecnia
Mara Cristina Pessoa da Cruz
Revista Textos Linguisticos
Maria Flávia Figueiredo
Proceedings of the Annual International Conference Syiah Kuala University Life Sciences Engineering Chapter
14_ Tri Wahyuni
2016 24th European Signal Processing Conference (EUSIPCO)
Trung Kien Le
Materials Today: Proceedings
chinika dangi
Mehmet Özçelik
European Journal of Organic Chemistry
Hélène Chaumeil
New Journal of Physics
Andrzej Stasiak
Journal of the Royal Society of Medicine
IML Donaldson
Darren Cronshaw
Journal of Clinical Medicine
Leslie Cooper
elsa rahayu
Physics Letters B
Josef Pochodzalla
Journal of Turkish Studies
murat çakırkaya
Revista chilena de neuropsicología
veronica anguita mackay
Revista Brasileira de História & Ciências Sociais
Maria Cristina Bohn Martins
European Journal of Clinical Microbiology & Infectious Diseases
Massimiliano Lanzafame
Annals of Clinical Microbiology and Antimicrobials
Ponmurugan Karuppiah
The International Journal of Prosthodontics
daniel cortes
See More Documents Like This
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
Pakistan and cyber crimes: Problems and preventions
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
‘Chilling pattern’: Pakistani journalists ‘targeted’ by cyber law
At least 23 journalists booked under the country’s draconian cyber-crime law in two years, according to a media rights watchdog.

Islamabad, Pakistan – At least 23 Pakistani journalists have been “targeted” under the country’s draconian cyber-crime law in the last two years, establishing a “chilling pattern” of using the threat of legal action to silence dissent, a new report by a media rights watchdog says.
Freedom Network, a Pakistan-based group, released its report to coincide with the International Day to End Impunity for Crimes Against Journalists, being marked worldwide on Tuesday.
Keep reading
Tv journalist killed in targeted attack in southern pakistan, pakistani journalist ‘taken off air’ after military outburst, pakistani journalist assaulted in latest press freedom attack, prominent pakistani journalist shot and wounded.
The “crimes” Pakistani journalists were charged with included “bringing the armed forces into disrepute”, “bringing the judiciary into disrepute” and “bringing the intelligence agencies into disrepute”. In at least one case, the journalist was accused of committing “treason”.
The cases under the Pakistan Electronic Crimes Act (PECA, also referred to as the country’s “cyber-crime law”) were often compounded with allegations under the penal code, with criminal cases registered against 13 of the 23 journalists.
At least nine journalists were arrested in connection with those inquiries, with six forced to obtain bail after spending up to 60 days in jail while under investigation.
Pakistan’s vibrant press includes an active television news media landscape, with dozens of channels offering 24/7 live news coverage and news analysis talk shows every evening. There are also dozens of print newspapers and, increasingly, online outlets or YouTube channels being run by journalists.
Increasingly, however, human rights groups and journalists have warned that journalists are facing increased strictures from the authorities not to cover certain topics, particularly allegations of the military’s increasing role in governance and politics.
News television channels that do not abide by the informal rules have seen their signals abruptly censored, newspapers have seen distribution disrupted, and individual journalists have been abducted after filing stories deemed critical of the military.
A 2019 Al Jazeera investigation documented the forms of coercion used to enforce the new code of censorship. Increasingly, the government has used the cyber-crime law as a means of targeting journalists, a 2020 Al Jazeera report found.
Earlier this month, the government expanded ( PDF ) its powers under the cyber-crime law, including a clause that “requires” all internet service providers and social media companies to break encryption and share user data with investigators if so required.
Pakistan’s powerful military has directly ruled the country for roughly half of its 74-year history, and is accused by the political opposition of having rigged the 2018 elections to bring Prime Minister Imran Khan to power. Khan and the military deny the allegations.
International media rights watchdog Reporters Without Borders (known by its French acronym RSF) says that acts of “brazen censorship” and the military’s role influence over the government have “increased dramatically” since Khan came to power.
“After reining in the traditional media, the [military and intelligence services] has set about purging the Internet and social media of content not to its liking,” reads RSF’s country profile for Pakistan.
Pakistan ranked 145 out of 180 countries in RSF’s World Press Freedom Index 2021.
Asad Hashim is Al Jazeera’s digital correspondent in Pakistan. He tweets @AsadHashim.
- EXPRESS NEWS
- URDU E-PAPER
- ENGLISH E-PAPER
- SINDHI E-PAPER
- CRICKET PAKISTAN
- EXPRESS LIVE
- CAMPUS GURU
- EXPRESS ENTERTAINMENT
- FOOD TRIBUNE
Cyber crimes on the rise in Pakistan, worldwide
Minister stresses need to increase number of cyber security experts

With increasing use of technology and online activities, the number of cybercrimes around the globe and in Pakistan is on the rise, which depicts the need to expand the number of cyber security experts in the country, said Federal Minister for Information Technology and Telecommunication Syed Aminul Haque.
Inaugurating a two-day programme titled “Digital Pakistan Cyber Security Hackathon 2021” on Monday, the minister revealed that organisations around the world spent around $20 billion due to cyber attacks last year, which showed the seriousness of the issue.
“Millions of cyber attacks are also being made in Pakistan every day,” he said, adding that Pakistani institutions including important banks and companies had been targeted by cyber attackers.
Citing examples, he revealed that the Federal Board of Revenue’s website was hacked a few weeks ago, which compromised the most important data.
A music streaming website “Patari” was also attacked in June this year and hackers released the data of 257,000 users on the dark web, he said. Last year, K-Electric’s system was hacked and ransom was demanded, he said.
The data of a couple of banks was hacked, but the banks asked customers to change their personal identification number (PIN) codes immediately, which minimised the losses.
The minister said that such attacks showed “how insecure the data of our institutions and consumers is”.
He cautioned that if the institutions still did not follow the instructions of the ministry, then irreparable damages could be done.
Many institutions did not even have cyber security systems, he said, adding that experts should be deployed.
The minister informed the participants that Pakistan’s first cyber security policy, launched in July 2021, explained the mechanism of staying safe from cyber attacks.
The IT ministry had to develop an integrated mechanism so that in case of any cyber attack on public or private institutions it should not only be stopped but retaliated, he added.
“Under Ministry of IT and Telecom’s department of Ignite, this event is a link in the chain through which the ministry wants not only to create awareness among the public about cyber security, but to bring forward creative cyber security experts from across the country,” he said.
The minister invited students of the Information and Communication Technology (ICT) sector and the youth to join the “most important” field of cyber security.
On the occasion, Ignite Chief Executive Officer Asim Shahryar Husain said that the growing importance of cyber security had placed it at number seven among 21 future sustainable technologies with growth projection of $270 billion by 2026.
The event was attended by 266 cyber security experts from different districts of Sindh, who would undergo tests to qualify for the next stage and the successful experts would become part of the Computer Emergency Response Team (CERT) that would be formed by the IT ministry soon.
The purpose of the programme was to train and prepare cyber security experts under the first cyber security policy unveiled by the IT ministry. The programme was launched in Karachi, and later will be organised in Lahore and Islamabad .
Published in The Express Tribune, November 2 nd , 2021.
Like Business on Facebook , follow @TribuneBiz on Twitter to stay informed and join in the conversation.
Comments are moderated and generally will be posted if they are on-topic and not abusive.
For more information, please see our Comments FAQ

Victory for PTI Lawyers: Imran Khan's Toshakhana Sentence Suspended

Israel Launches Deadly Airstrike on Iranian Consulate In Syria

Tragic Loss in Gaza: Foreign Aid Workers Killed in Alleged Israeli Air Strike

The Election Commission Prepares for Pakistan's Senate Elections 2024

5 Times Taylor Swift’s Privacy Was Invaded Before Her Bahamas Vacation with Travis Kelce

IHC Suspends Imran and Bushra Bibi's Toshakhana Conviction

Gaza's Al-Shifa Hospital: Aftermath of Israeli Withdrawal

Former Chief Justice Tassaduq Hussain Jillani Declines Inquiry Commission Leadership.

PTI News: Senate Elections Boycott, Imran Khan’s Adiala Jail Pact, Karachi Rally Announced

29 Year-Old Woman Dies Days After Converting to Islam | Hundreds of Locals Gather for Dubai Funeral

King Charles Makes First Public Appearance Post-Cancer Diagnosis Announcement

Houthi Central Bank Introduces New Currency Coin Amid Yemen's Political Turmoil

Separated couples move courts for family meetings

White House hosts muted Ramazan event as Biden's Israel policy draws anger

Meta facing backlash for allegedly sharing Facebook users' private messages with Netflix

Chinese firm resumes work on Diamer Bhasha dam project

Intel slides as foundry business loss spotlights wide gap with rival TSMC

Spotify to raise prices in some markets, Bloomberg News reports

Makeup Mastery

Revolutionising Runways

From Disorder to Tranquillity: The Art of Minimalist Living
On Express Urdu

اوپن مارکیٹ میں ڈالر کی قدر 280 روپے سے نیچے آگئی

ریکوڈک میں سعودیہ کی جانب سے ایک ارب ڈالر کی سرمایہ کاری کا امکان

بلوم برگ کی پاکستان کی شرح نمو میں دوگنا اضافے کی پیشگوئی

عالمی مقامی مارکیٹوں میں سونے کی قیمت میں اضافہ ہوگیا

پاکستان اسٹاک ایکسچینج میں تاریخی تیزی، انڈیکس بلند ترین سطح عبور کرگیا

6 فرٹیلائزر کمپنیوں کو شوکاز نوٹس

Govt monopoly on vehicle number plates ends

Imran removes Marwat from PTI’s focal roles amidst internal strife

Shawwal moon to likely be sighted on April 9

PIA goes under hammer on June 3

Life in Pakistan is best: Sanam Jung bares all about the realities of life in Texas

Govt okays expensive $500m ADB loan

The perils of social media

Pakistan’s standing in the world

Man is nothing but his thoughts

An Israel-Hezbollah war — outcomes and implications

Erosion of merit in Pakistan: the hows and whys

Seeking perfection?
- Life & Style
- Prayer Timing Pakistan
- Ramazan Calendar Pakistan
- Weather Forecast Pakistan
- Online Advertising
- Subscribe to the Paper
- Style Guide
- Privacy Policy
- Code of ethics
This material may not be published, broadcast, rewritten, redistributed or derived from. Unless otherwise stated, all content is copyrighted © 2024 The Express Tribune.
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Springer Nature - PMC COVID-19 Collection

Artificial Intelligence Implementation to Counteract Cybercrimes Against Children in Pakistan
Saadia anwar pasha.
1 Department of Mass Communication, Allama Iqbal Open University, Islamabad, Pakistan
2 Allama Iqbal Open University, Islamabad, Pakistan
Riadh Jeljeli
3 College of Communication and Media, Al Ain University, Al Ain, United Arab Emirates
Increased internet usage also enhances cyberattacks, particularly in a developing country like Pakistan. These cybercrimes are common against children, demanding the implementation of automated systems and models to detect and counteract these crimes. By keeping in view the growing importance of AI-enabled cybersecurity systems, this article provides insights regarding implementing the relevant systems and models to counteract cybercrimes against children in Pakistan. The researchers reviewed current studies witnessing the performance, reliability, and results of AI implementation in different countries to relate their possible potential further to detect, takedown, and trace online violence against children effectively. Findings showed that AI-enabled software, i.e., Spotlight, SomeBuddy, Google AI Tool, etc., and models such as DAPHNE, iCOP toolkit, and PrevBOT can identify and takedown any indecent activity against children. Besides, detecting the perpetrators’ URLs, domains, and personal emails can further help the children resume internet usage in a healthy online environment. Thus, it is concluded that the internet technology is also creating vectors for abuse and exploitation against children. Harnessing powerful technology, i.e., AI, to analyze and manage the data can also enrich investigative functions. Towards this, local government and law enforcement agencies should resort to suggested tools that may identify even keywords and images. Further, the researchers have provided policy recommendations and discussed the limitations accordingly.
Introduction
There is a wealth of opportunities for the users on the internet. However, today, when from financial assets to one’s personal information is available on the internet, data preservation, privacy, and security are some of the major concerns, increasing the need for cybersecurity as comparatively more effective and strong (Bhatele et al., 2019 ). For instance, individuals saving their bank account details and residential information in their online cloud storage account are more vulnerable to cyber threats indicating an inevitable need to increase their cyber security. Cyber security creates and sustains the integrity, availability, and confidentiality of the users’ data without compromising any private information. In this regard, the contemporary trends in internet usage and adoption raise several concerns regarding a sudden confrontation with cybercrimes. However, the role of artificial intelligence in counteracting these cyber crimes is prominent, providing several instant solutions to the law enforcement agencies (Newman, 2019 ). As noted by Coole et al. ( 2021 ), using artificial intelligence in the cyber system provides several benefits for operational security systems. For example, artificial intelligence helps increase the speed and probability of cybercrimes’ detection, reduces operator fatigue, and assists security personnel for providing more attention where needed. Besides, Artificial Intelligence also helps reduce the cost at the management level, supports the decision-making process, provides effective interventions to counteract the internal threats, and directs resource allocation.
Similarly, an ever-increasing number of cybercrimes against children is a thought-provoking phenomenon. As noted by Kumar ( 2021 ), children are the most vulnerable component of our society that can be easily manipulated and exploited. Especially today, when the internet offers greater accessibility and ease of use, targeting a child has become common. Especially after 2019, the number of cyber violence against children has increased 400 times more, raising questions regarding the credibility of the internet as a safe place for children (Durkin, 2017 ). Consequently, increasing internet usage among children without knowing the potential threats is considerable. We cannot deny malicious activities on different online platforms that require one single click, leading to adverse outcomes for the users and children (Alhumaid et al., 2021 ).
Particularly, cybercrimes against children in developing countries are another major concern that requires serious consideration. For example, Federal Intelligence Agency (FIA) Pakistan reported daily 266 cybercrimes against children, mainly including child pornography and harassment, in the country. Still, most cybercrimes against children remained unreported due to children’s lack of understanding about the incident and parents’ neglect (Child Welfare Information Gateway, 2006 ; Global Human Rights Defence, 2021a ). Yet, these increased cybercrimes against children can be counteracted by cyber security systems accompanied by artificial intelligence. Emerging technologies such as cloud computing, internet banking, and others can use artificial intelligence, which can also be applied to control cybercrimes against children (Chandra, 2019 ). Vilks ( 2019 ) further argued that AI-based cyber security not only identifies any criminal activity but also helps determine crimes against children. Countries, where cyber security is adopted and accompanied by Artificial Intelligence, are comparatively more vigilant to identify and counteract the relevant activities.
Thus, by keeping in view the number of cybercrimes against children in Pakistan, this article focuses on highlighting and addressing the online incidents against children and potential ways to avoid them. In the first section, the researchers have discussed the importance of Artificial Intelligence in dealing with cybercrimes in general and cybercrimes against children in particular. The second section discusses the most common cybercrimes against children worldwide and in Pakistan. The following section will also involve literature discussing how and to what extent Artificial Intelligence can help identify relevant crimes. The third section involves a general discussion and suggestions for implementing AI-based systems to identify and deal with the cybercrimes against Pakistani children. Finally, conclusions are made in the fourth chapter, and study limitations are discussed accordingly.
Cybercrimes Against Children
Online emotional abuse and cyberbullying happen when someone resorts to online technology to target, harass, threaten, or cause psychological harm. As today, smart devices are adopted and owned even by children, they often confront this harassment besides psychological trauma. Several cases of cyberbullying involve posting personal information and photos of a child, sharing other content that may harm the child and their reputation. Fake accounts pretending to be someone are also found to harm and target a child, causing emotional damage and bullying (Kidshealth.org, 2020 ). A report represented by Ipos Global Advisor conducted a study in 28 countries to investigate cyberbullying against children. Results revealed that the reports of cyberbullying have tremendously increased after 2011. Among the selected countries, 54% of South African children reported cyber-bullying against them. However, 65% of children from Latin America also reported cyberbullying, indicating increased cyber violence against them (Jarno & November, 2020 ).
However, despite online bullying and emotional abuse being common against children, sexual crimes are comparatively more prevalent (Katz, 2020 ). An investigative team by Europol led by the Te Tari Taiwhenua Department of Internal Affairs started interrogation against cyber-crimes against children in Croatia, Hungary, Austria, Czechia, Canada, Spain, USA, Greece, Australia, UK, and Slovenia. In 2019, the team found many users utilizing different online platforms to distribute and exchange images and videos containing explicit sexual and sadistic activities with children and infants. The team acquired 32 GB of files, leading to the international opening of approximately 836 cases (EUROPOL, 2022 ). Notably, the team encountered almost 90,000 international accounts, arrested 46 suspects in New Zealand, and more than 100 individuals were also arrested across the Europe. In two of the cases in Hungary and Austria, the suspects were molesting their own children, who were 6 and 8 years old, which were later safeguarded. Another case in Spain involved a suspect possessing child pornographic material and sharing sexual content with adults without their knowledge and consent (EUROPOL, 2022 ).
Similarly, a mixed-method study in Sri Lanka revealed that 28% of children had experienced some kind of online violence against them. More specifically, irrespective of gender, 27% of children reported receiving indecent images. However, the number of female children (29%) receiving the relevant images remained higher than that of male children (27%), while 27% of children also reported facing cyberbullying and extortion, and 20% reported that their indecent images were being shared on the internet (SavetheChildren.net, 2020 ) (Table (Table1 1 ).
Reports concerning cybercrimes against children worldwide and in Pakistan
Cybercrimes Against Children in Pakistan
Children are the most vulnerable sections of society and are easily exploited in the cyber world due to a lack of maturity level. It is observed that besides bullying and emotional abuse, sexual exploitation of children is prevailing at many online platforms. The offenders chat online with young children by wrongly stating/representing their age and lure them towards sex. With the latest technology, it has become easy for criminals to contact children (Lewczuk et al., 2021 ).
Violence against children is a burning issue in Pakistan like other countries. For example, in 2020, a total of 2,960 cases were recorded, indicating a 4% increase compared to 2019 only in Punjab province. These cases involved physical and sexual violence, leading to even life-threatening situations for the victims. 51% of victims were females, and 49% were male children in these cases (AIN, 2021 ). However, these cases only indicate violence in the non-virtual environment, indicating a lack of research and consideration towards online violence against children in the country. Notably, today there are 61.34 million internet users in Pakistan. The number of internet users significantly increased from 2020 to 2021 by 11 million due to the COVID-19 outbreak. These internet users comprise almost 27% of the total population, indicating a significant number of youngsters below 16 years old. As a result, children often confront several cybercrimes, including cyberbullying, online violence, and harassment (DigitalPakistan, 2021 ). In 2019, Pakistan’s Human Rights Minister, Dr. Shireen Mazari declared that today Pakistan is one of the most prominent countries to produce and disseminate child pornography. Other crimes such as identity theft, stalking, and online harassment also prevail against children in Pakistan (Global Human Rights Defence, 2021b ).
Cybercrimes against Pakistani children are primarily seen in terms of child sexual abuse and pornography. During the past few years, young internet users in Pakistan have widely experienced cyber-bullying, sextortion, and revenge porn (Global Human Rights Defence, 2021 ). One of the prominent incidents of online violence against children in Pakistan can be traced back to 2015 when the local authorities found a wing regulating online child pornography for commercial purposes in Hussain Khanwala village, Kasur, Pakistan. Further reports revealed more than 285 children were sexually abused for pornography and silenced by their parents through fear and threats (Jalil, 2018 ). Police also recovered over 400 pornographic videos of young boys engaging in on-camera sexual acts with the adults (Zehra Abid, 2019 ).
In 2020, Federal Intelligence Agency (FIA) witnessed a potential increase in online harassment against children, including child pornography. According to the records, Federal Intelligence Agency (FIA) registered 260 complaints daily, reaching 94,500 complaints by the end of 2020. These crimes involve identity theft, online blackmailing, defamation, and child pornography (Global Human Rights Defence, 2021 ). According to Kasim Abbasi ( 2021 ), the accumulative ratio of cyber violence against children and in general indicates several types of crimes causing physical and psychological harm to the young users. Fake profiles, online blackmailing, defamation, sharing, receiving, and recording child pornography and other have enormously increased in Pakistan.
Artificial Intelligence in Crime Detection in General Context
Artificial intelligence is an important field of computer sciences that, e.g., bots, imitate human intellect. In other words, robots mimic human intellect in a digital environment as they contain smart algorithms making an evaluation based on the provided information. Artificial intelligence plays a significant role in almost every industry, including communication, cybersecurity, and forensics (Dupont et al., 2021 ). Today, when internet usage is increasing globally, users are more vulnerable to cyber-attacks. Cyber-criminals are always searching for new ways to harm people, steal their data, and put their lives at stake. As a result, it is impossible to overlook these cyber-crimes leading to strong cyber-security adoption among them (Thuy & Hieu, 2020 ). According to Caldwell et al. ( 2020 ), the internet provides us with various entertainment, information, communication, and educational opportunities; threats posed by cyber-crimes further endanger these new opportunities.
Consequently, cyber-security, including new approaches, i.e., Artificial Intelligence, has become an integral consideration for everyone. Here Thuy and Hieu ( 2020 ) further argued that cyber-criminals could contact and invade from any geographical region, identify personal information, defraud us financially, or harm our reputation. In such a situation, Rehnström ( 2021 ) suggested implementing Machine Learning and Artificial Intelligence as critical approaches to combat the cyber-crimes. For instance, Artificial Intelligence analyzed the trends in cybercrimes and prevention in the past. The importance of Artificial Intelligence can be determined by the fact that it can also work with the conventional security systems hand in hand (Rigano, 2019 ). Today, emerging security systems across the globe are attaining different ideas from several cyber events and utilizing them to identify threats, i.e., phishing and malware attacks. Podoletz ( 2022 ) noted that artificial intelligence automatically detects all the cyber threats or data breaches, which further alerts the systems to strengthen the cyber-security and counteract any potential invasion. As Rouhollahi ( 2021 ) argued, whatever form the Artificial Intelligence takes, technology will provide in-depth details of an event and ensure security against such incidents.
AI-Enabled Approaches to Counteract Cybercrimes Against Children in Pakistan
As system models have a potential to counteract online crimes against children, still, many ask how AI can help mitigate online violence against children. As a result, software developers and providers are providing influential AI applications that can thwart online crimes against children (Coole et al., 2021 ) in Pakistan. It is notable that, the intelligent agent system represents a small part of an entire AI system, known as computational intelligence (CI). Computational intelligence (CI) involves some strong yet different nature inspired capabilities, i.e., Fuzzy Logic, Swarm Intelligence, Artificial Immune System, Machine Learning, and Neural Networks (Dilek, 2017 ). These approaches facilitate the decision-making particularly, when the cybersecurity of internet users is required. When we say “Nature Inspired Immune System,” we mean that the AI technology that can imitate the natural immune system, focused on counteracting the crimes as having abilities such as detection, memorization, process, and classify the information (Dilek, 2017 ). Thus, the following are some relevant AI-enabled systems that not only detect the cybercrimes against children but also provide a pathway to counteract them:
- Child Safe AI
Child Safe AI is one of the pioneering AI-based platforms that monitor web content, particularly child abuse-based material, ensuring reduced child abuse in the online environment. The US law enforcement agencies also deploy Child Safe AI, which actively gathers signals regarding exploitative activities or material from the online environment. The relevant system also assists many organizations by continuously monitoring and evaluating the online material, i.e., images, videos, chats, and other content (Nolan & Brodowski, 2019 ).
- 2. Spotlight
Developed by Thorn, Spotlight is a digital identifier of online crimes against children, especially child trafficking and child sexual abuse. This technology uses predictive analytics to detect the relevant activities and victims. According to Oriel ( 2022 ), Spotlight identifies the activities and victims of child sexual abuse and online trafficking by data obtained from escort websites and sex advertisements. Like Child Safe AI, Spotlight is also used by the US Federal Department to detect child trafficking activities. It is also notable that, Spotlight has helped to detect and solve more than 14,874 cases of online child trafficking during the past 4 years.
- 3. AI technology by UNICRI
According to the United Nations Secretary-General Antonio Guterres, the combined efforts to counteract online crimes can protect children and ensure peace for all. AI technology by the United Nations Interregional Crime and Justice and Research Institute (UNICRI) uses Robotics and Artificial Intelligence for the law enforcement (particularly to identify and locate the long-missing children) (UNICRI, 2020a ). Besides, it also helps to detect child and human trafficking sites and activities and identify illicit online pornographic material (UNICRI, 2020b ). However, despite UNICRI is using Robotics and AI, still, the relevant technology is not much used (Oriel, 2022 ). According to UNICRI, employing Artificial Intelligence to ensure online safety for children also requires regular monitoring and updating the relevant system. Besides, incorporating AI technology is important due to the fact that, during the after the COVID-19 outbreak, internet usage among children increased further leading to an increased cases of online crimes against children. As a part of definitive emerging technologies today, artificial intelligence not only detects the crimes, but also monitor what a human eye, sometimes, cannot detect (UNICRI, 2021 ).
- 4. Google’s AI Tool
Technology giant Google introduced an AI toolkit to counteract online crimes against children. This AI toolkit involved image processing through Deep Neural Networks that further helped the non-governmental organizations and investigators to detect the audio and video content based on child sexual abuse. The relevant AI toolkit also assists the classifiers in monitoring the offenders by detecting the content not identified by child sexual abuse material (Hunt et al., 2020 ). According to Detrick, the Artificial Intelligence-enabled tool by Google can help the reviewers to scan and identify more than 700% indecent material of children available online. Notably, Google’s AI Tool is available free of cost; however, it needs human moderators to carefully evaluate the indecent images and other types of content by hand, needing human efficiency and effort as aiding intelligent systems for the crime detection (Detrick, 2018 ).
Thorn developed Safer as one of the leading AI companies, able to detect 99% of cybercrimes against children. With the help of Safer, an online platform can detect, remove, and block the sources and platforms used for cybercrimes against children. Safer had previously taken down more than 100,000 relevant files in its beta phase, and more improvements are yet to come (Gray et al., 2016 ). Safer provides the following services:
- Image Hash Matching creates perpetual and cryptographic hashes to match them with the previous child sexual abuse containing material, mainly to detect the indecent images of children.
- CSAM Image Classifier helps classify whether an image is consistent with the content that involves child sexual abuse.
- Video Hash Matching, like Image Hash Matching, also produces perpetual and cryptographic hashes to match them with the previous child sexual abuse containing material, mainly to detect the indecent images of children.
- 6. Griffeye
According to UK Home Office ( 2015 ), Griffeye uses different computer vision and recognition tools such as facial recognition to scan and detect the images based on the parameters of age and nudity. Griffeye is also adopted and implemented by US federal agencies to counteract any online activities against children (GRIFFEYE, 2018 ). According to the official Griffeye platform, online crimes against children can be traced through three resources: Analyze DI Pro software that can be used by individuals to import, process, and review the complex information regarding indecent images and videos of children available online. Analyze CS Operations involves group efforts facilitating crime detection. More specifically, teams using Analyze CS Operations are provided with digital base for analyzing and reviewing the relevant material. Finally, Analyze CS Enterprise facilitates the organizations in resuming ongoing interrogations regarding cybercrimes against children. The Analyze CS Enterprise is based on a dynamic repository to examine and identify the suspicious information over time (Digital Forensics, 2021 ).
- 7. SomeBuddy
Another important AI-enabled software, “SomeBuddy,” was created and designed by UNICEF to protect children using the internet for socialization, education, and entertainment. SomeBuddy as a “First-aid” platform helps and facilitates children report cyberbullying and harassment (UNICEF, 2019 ). It involves a strong combination of human supervision and Artificial Intelligence (AI) to detect and categorize the type of harassment, providing them with the most suitable recommendations concerning the current step. According to UNICEF ( 2019 ), the primary objective of SomeBuddy is to provide psychological and legal support to the children facing any challenging situation in cyberspace. Besides, it also spreads awareness among children to effectively identify and counteract any potential crime. According to CrimeDetector, initially, SomeBuddy adopted a virtual assistant interface; however, the developers found the chatbots as ineffective due to their broader conversational nature. Thus, SomeBuddy adopted simple yet automated approach to provide the users with more time to elaborate the obtained data. The relevant design output aided improving and streamlining the intake functions (CrimeDetector, 2019 ). Besides, SomeBuddy also stresses the legal experts across the globe to thoroughly review the obtained information, especially “false positives” and “false negatives” (CrimeDetector, 2019 ) (Table (Table2 2 ).
AI-enabled approaches and models to counteract cybercrimes against children
DAPHNE: Detecting Grooming in Online Social Media
Online crimes against children, especially sharing and possessing indecent images of children, have become common today. Besides, interacting with online child abusers and sextortion is also prevailing. Exposure to online criminals, especially pedophiles, is of greater concern, demanding strong consideration from the technology developers and online law-making authorities. In this regard, classified supervisors using independent feature types such as content, polarity, semantic frames, n-gram, and psycholinguistics can help counteract cybercrimes, particularly online child grooming (Peersman, 2017 ). Rigano ( 2019 ) proposed that the merged features can also help to counteract the online child grooming.
The study conducted by Cano et al. ( 2014 ) further proposed generating binary classifiers to detect the child grooming attempts on social media as the researchers used stage-labeled sentences (i.e., approach stages section, grooming, trust development) that were labeled as the positive set while the sentences labeled as “other” were the negative set. The researchers further suggested using a stage classifier with a unigram of words approach and a tenfold cross-validation five-trial setting. In their work, Cano and their colleagues emphasized upon the characterization of the predators’ online behavior, including sentiment polarity, syntactical content, discourse patterns, psycholinguistics, and a bag of words (BOW). Further, for the characterization process, the researchers provided a framework (see Fig. 1 ). In the framework proposed by Cano et al. ( 2014 ), the first step involves extracting predators’ communication patterns from the PJ chat log. In the second phase, the identifier pre-processes these conversation lines. Then, each conversation is represented in the feature extraction, following the information-gaining approach. Further, the researchers also designed a vector machine for the experiment as a supervised discriminative model.

Identification and characterization of the child grooming phases (Cano et al., 2014 )
iCOP: Identifying New CSAM on P2P Networks
The severity of online crimes against children demands a proliferation of monitoring and detection technology. A study by Aiello and McFarland ( 2014 ) proposed a toolkit, iCOP, to identify online child abuse material on P2P networks. However, before discussing and proposing the iCOP toolkit, the researchers proposed a classification approach that involves specialized vocabulary and n-grams to share child abuse material on P2P networks. Both specialized vocabulary and n-grams can automatically identify the child abuse material from the millions of files shared online. Further, a potential video and image classification approach using multiple and multimodal feature descriptions leads to a strong identification of child abuse material on online platforms.
Similarly, the above-discussed approaches are merged into an iCOP toolkit to counteract the child abuse-based online material further. As shown in Fig. 2 , the proposed toolkit has two primary components, including the P2P Engine and iCOP Analysis Engine (Pupillo & Fantin, 2021 ). The P2P Engine helps to monitor the online traffic on the P2P networks. This P2P Engine supports traffic monitoring on Gnutella. However, other monitors can also plug in to increase their monitoring ability. This P2P Engine gathers information such as URLs, IP addresses, hash values, metadata, and filenames when the user is seen sharing the file. The latter is thus important to detect the originator and receiver of the child abuse-based content file.

iCOP toolkit (Aiello & McFarland, 2014 )
The PrevBOT Concept
According to Kumar ( 2021 ), online crimes against children are proliferating today. To counteract these concerns, there is a need to establish an intelligence crime detection system. Further, Sunde and Sunde proposed PrevBOT concept commonly used by law enforcement authorities. PrevBOT was first conceptualized after the Sweetie 2.0 that can monitor open conversations and communicate automatically through chat rooms. Besides, monitoring and interacting through chatrooms, PrevBOT contains the characteristics of machine learning and forensic linguistics influenced by AiBA technology (Schermer et al., 2019 ). PrevBOT also enabled to predict and compute the details important for highlighting the preventive measures against online child sexual abuse in particular. Figure 3 illustrates the graphical model regarding PrevBOT to classify Problem Persons (PP) and Problematic Spaces (PS).

Model regarding PrevBOT to classify Problem Persons (PP) and Problematic Spaces (PS)
According to Sunde and Sunde, PrevBOT is based on the Machine Learning algorithms and generates computations and predictions regarding the information consistent to online crimes against children. The output is statements, i.e., “carry a degree of uncertainty.” Notably, the PrevBOT has two primary objectives: to classify the Problematic Persons and to classify the Problematic Spaces (Sunde & Sunde, 2021 ). For example, when a chatroom is flagged as Problematic Space, PrevBOT predicts whether the behavior of individual(s) is suspicious (Problematic Persons (PS)). Further, PrevBOT uses a series of questions to classify and detect the problematic chat and behaviors through other different tactics. For example, at one stage, it uses “Linguistics Fingerprints” to compare pre-existing conversations with the new conversations. By using different techniques, PrevBOT facilitates reliable investigations for identifying the suspicious behaviors in chatrooms even if the persons are known to the police from previous cases of cybercrimes against children (Finch & Ryckman, 2020 ).

Discussion and Policy Recommendations
Fundamentally, the role and integration of information communication technology in our society limit access to counteract every single cyberattack. Talking particularly about the cybercrimes against children, the magnitude of these crimes is increasing in Pakistan. An algorithm-based system can help not only to counteract the crime but also aid in determining both previous and recent patterns in cybercrimes. The data used to modify and upgrade these systems is based on factual reports, defining the most considerable patterns of crimes especially against children (Global Information Security, 2019 ).
The empirical resources, available today, indicate that there are several approaches to identify and counteract cybercrimes against children. For instance, Neural Networks as an integral part of Intrusion Detection System can be used to detect the spam material and also to conduct the forensic investigations (EPCAT, 2021 ). According to Yadav and their colleagues, the ability of Artificial Intelligence to process huge amount of information cannot be denied. For example, a law enforcement team identifies suspects and has to go through the files saved into their computer systems. In such a situation, the investigation team will need human force to scrutinize all the content one by one that will be time-consuming, further threatening the investigators interest in the case. However, using Artificial Intelligence-enabled tools and approaches will not only help them to improve and speedup their investigations but also help to counteract the potential crimes in the future (Yadav & Husain, 2018 ). According to Pupillo and Fantin ( 2021 ), major platforms such as Facebook, YouTube, Tiktok, and others use Artificial Intelligence to identify and takedown the relevant activities. In many cases, tracing the criminals by recognizing their URLs also remained prominent as the relevant content was directly reported to the law enforcement agencies, leading to an instant detention and punishments.
Thus, to mitigate these cybercrimes, the Federal Intelligence Agency (FIA) Pakistan has created a special wing named “Cyber Crime Wing” (CCW) (Zia UL Islam et al., 2019 ). This Cyber Crime Wing was established under the laws that were designed under the Prevention of Electronic Crimes Act (PPECA) 2016, which criminalizes online violence against children with a punishment of a fine of up to five million rupees or 7 years of imprisonment or both. Victims can directly access the Cyber Crime Wing (CCW) through email or phone calls to lodge their complaints, ensuring an effective strategy to deal with the cyberattacks against children (AIN, 2021 ). However, these Cyber Crime Wing (CCW) and other bodies lack any prominent technological approach (Coole et al., 2021 ; Zia UL Islam et al., 2019 ) to automatically detect and takedown content and activities indicating a loophole in the cybersecurity systems. For this purpose, this article tends to provide some recommendations to the government, law enforcement authorities, and software providers in Pakistan, including:
- The trend of using Artificial Intelligence to counteract cybercrimes against children is increasing, and Pakistan’s criminal justice authorities should also consider them (Velasco, 2022 ). The local government should grant sufficient funds and training to the law enforcement agencies, especially Cyber Crime Wing.
- It is notable that, although cybercrimes against online users is a punishable crime in Pakistan, yet no practical policy is given to specify these crimes against children. In this regard, it is important to create a national Artificial Intelligence strategy to create a primary framework to implement it for both public and private sector law enforcement organizations with a potential focus on children welfare and their rights (Global Information Security, 2019 ).
- The suggested softwares and models should be deployed and also identify suspicious activities through the suggested software models (See Gray et al., 2016 ; Podoletz, 2022 ; UNESCO, 2019 ). For this purpose, professionally trained individuals should be recruited.
- Creating additional task forces to counteract cybercrimes against children may also coordinate with the Artificial Intelligence-enabled system. The relevant coordination may help identify the suspicious activities and content and help the task force to take instant action (Erokhina & Letuta, 2020 ).
- Deploying models like PrevBOT, DAPHNE and iCOP to identify and counteract the stages of grooming in a cyber environment require skilled agents (Aiello & McFarland, 2014 ; Charalambous et al., 2016 ; Peersman, 2017 ). Software providers should recruit skilled and experienced individuals for deployment purposes so that they may also keep the systems updated.
- Efficiently deploying network tools already used by UNICEF (Walker, 2019 ) and other concerned bodies can help investigators gather information about the host servers and URLs. Investigators with vigilance and prior experience in detecting and takedown any indecent activity can also help gather information about the user, website owner, and host country. If the concerned authorities use an AI-enabled system, improved forensic tools can further assist in identifying the email and URL information leading to easy detention of the cybercriminals (Charalambous et al., 2016 ).
- The government of Pakistan can take an example of incorporating AI in counteracting online crimes against children by the Australian Police Department. Introducing “AiLecs” is trained to identify the suspicious activities, particularly, the content showing any indecent activity against children. It is notable that, the AI cannot be fully influential yet when the algorithms work as expected, cybercrimes against children can be counteracted (Panda Media Center, 2022 ).
The rise of cybercrimes against children in Pakistan further questions the credibility and use of online platforms among children. These crimes also threaten children’s life-long well-being as the relevant crimes are also evolving. Anonymity and accessibility are two prominent features that further halt a direct identification of the criminals and their origins. However, where technology has facilitated criminals, it also enables forensics and principal investigators to identify and takedown cyberattacks in the better possible way.
Deploying technology, updating existing cybersecurity systems, and using Artificial Intelligence (AI) besides human force can further help to counteract these crimes. As technology evolves, communication and interactivity are enhanced from conventional platforms to computers and now smart devices. Children are becoming increasingly vulnerable to sexual abuse, bullying, and emotional violence in online environments. Today, the rise of internet technology is also creating vectors for abuse and exploitation against children. Harnessing powerful technology, i.e., AI, to analyze and manage the data can also enrich investigative functions. Towards this, local government and law enforcement agencies should resort to suggested tools that may identify even keywords and images.
Limitations and Contributions
This study highlights an important area of interest which is formally underrepresented in the Pakistani scenario. Despite increasing cybercrimes against children in the country, deploying technology-assisted defense and identification systems is still under debate. The current study will not only provide an idea regarding AI’s significance in counteracting cybercrimes against children but also proposes potential technological systems and models with practical evidence from the other regions. However, certain limitations are considered in the current research. First, this study lacks any primary data that narrow down its scope. Second, the researchers have highlighted some selective softwares and models. Finally, the third limitation involves the lack of data sufficiently witnessing cyberattacks in the Pakistani scenario. Yet, this study is a heads-up call for the government, law enforcement agencies, and policymakers, further filling the gap in the existing literature.
Declarations
The authors declare no competing interests.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Contributor Information
Saadia Anwar Pasha, Email: [email protected] .
Sana Ali, Email: moc.liamtoh@0991oel_anas .
Riadh Jeljeli, Email: [email protected] .
- Aiello LM, McFarland D. Detecting child grooming behaviour patterns on social media. Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) 2014; 8851 (-):16. doi: 10.1007/978-3-319-13734-6. [ CrossRef ] [ Google Scholar ]
- Alhumaid K, Habes M, Salloum SA. Examining the factors influencing the mobile learning usage during COVID-19 pandemic: An integrated SEM-ANN method. IEEE Access. 2021; 9 (July):102567–102578. doi: 10.1109/ACCESS.2021.3097753. [ CrossRef ] [ Google Scholar ]
- AIN. (2021). Violence against children continues unabated in Pakistan’s Punjab province . https://www.aninews.in/news/world/asia/violence-against-children-continues-unabated-in-pakistans-punjab-province20210621041438/#:~:text=Atotalnumberof2%2C960,49percentwereboys
- Bhatele, K. R., Shrivastava, H., & Kumari, N. (2019). The role of artificial intelligence in cyber security . January , 170–192. 10.4018/978-1-5225-8241-0.ch009
- Caldwell M, Andrews JTA, Tanay T, Griffin LD. AI-enabled future crime. Crime Science. 2020; 9 (1):1–13. doi: 10.1186/s40163-020-00123-8. [ CrossRef ] [ Google Scholar ]
- Cano AE, Fernandez M, Alani H. Detecting child grooming behaviour patterns on social media. Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics) 2014; 8851 :412–427. doi: 10.1007/978-3-319-13734-6_30. [ CrossRef ] [ Google Scholar ]
- Chandra M. Reduction of cyber crimes by effective use of artificial intelligence techniques. International Journal of Recent Technology and Engineering (IJRTE) 2019; 4 :8643–8645. doi: 10.35940/ijrte.D8566.118419. [ CrossRef ] [ Google Scholar ]
- Charalambous E, Kavallieros D, Brewster B, Leventakis G, Koutras N, Papalexandratos G. Combatting cybercrime and sexual exploitation of children: An open source toolkit. Open Source Intelligence Investigation. 2016 doi: 10.1007/978-3-319-47671-1. [ CrossRef ] [ Google Scholar ]
- Child Welfare Information Gateway. (2006). Child abuse and neglect what is child abuse and neglect? https://tedibear.ecu.edu/wp-content/pv-uploads/sites/189/2019/07/Child-Abuse-and-Neglect.pdf
- Coole, M., Evans, D., & Medbury, J. (2021). Artificial intelligence in security: Opportunities and implications .
- CrimeDetector. (2019). SomeBuddy . 1–14.
- Detrick, H. (2018). Google’s new AI tool to fight child sexual abuse will help reviewers scan 700% more material . https://fortune.com/2018/09/04/google-child-sexual-abuse-prevention-ai-tool/
- Digital Forensics. (2021). Griffeye . https://www.dataexpert.eu/products/digital-forensics-griffeye/
- DigitalPakistan. (2021). Digital 2021: Pakistan . https://datareportal.com/reports/digital-2021-pakistan
- Dilek S. Applications of Artificial Intelligence Techniques to Combating Cyber Crimes: A Review. 2017; 6 (1):21–39. [ Google Scholar ]
- Dupont B, Stevens Y, Westermann H, Joyce M. Artificial intelligence in the context of crime and criminal justice. SSRN Electronic Journal. 2021 doi: 10.2139/ssrn.3857367. [ CrossRef ] [ Google Scholar ]
- Durkin, K. F. (2017). Encyclopedia of cyber behavior . January 2012 . 10.4018/978-1-4666-0315-8.ch066
- EPCAT. (2021). The role of artificial intelligence in protecting children in the digital space . https://ecpat.org/ai-digitalspace/
- Erokhina, E. V, & Letuta, T. V. (2020). Juvenile cybersecurity and artificial intelligence system . 156 (Iscde), 607–611.
- EUROPOL. (2022). 146 children worldwide saved in an operation targeting child abuse online . https://www.europol.europa.eu/media-press/newsroom/news/146-children-worldwide-saved-in-operation-targeting-child-abuse-online
- Finch, A., & Ryckman, L. (2020). Strategies to prevent online sexual abuse of children: A systematic review of the literature protocol . March , 1–7.
- Global Human Rights Defence. (2021a). Cybercrime towards children in Pakistan . https://ghrd.org/cybercrime-towards-children-in-pakistan/
- Global Human Rights Defence. (2021b). Cybercrime towards children in Pakistan . https://ghrd.org/cybercrime-towards-children-in-pakistan/#:~:text=Young people between the ages,from over 160 countries worldwide.
- Global Information Security. (2019). Global information society watch 2019 artificial intelligence:
- Gray, J., Pesevska, D. J., Sethi, D., Gonzalez, M. D. R., & Yon, Y. (2016). Handbook on developing national action plans to prevent child maltreatment. World Health Organization . http://www.euro.who.int/__data/assets/pdf_file/0019/329500/Child-maltreatment-PAP-handbook.pdf
- GRIFFEYE. (2018). Analyze DI Pro: Powerful software for your digital media investigations . 30–31.
- Hunt, X., Tomlinson, M., Sikander, S., Skeen, S., Marlow, M., du Toit, S., & Eisner, M. (2020). Artificial intelligence, big data, and mHealth: The frontiers of the prevention of violence against children. Frontiers in Artificial Intelligence , 3 (October). 10.3389/frai.2020.543305 [ PMC free article ] [ PubMed ]
- Jalil, X. (2018). Is something wrong with Kasur? https://www.dawn.com/news/1384248
- Jarno, K., & November, T. (2020). Cyberbullying, an overlooked and ever growing danger to the development of children . November , 1–23.
- Kasim Abbasi. (2021). Cybercrime increases by 83pc in three years . https://www.thenews.com.pk/print/884453-cybercrime-increases-by-83pc-in-three-years
- Katz, A. (2020). Vulnerable children in a digital world .
- Kidshealth.org. (2020). Cyberbullying . https://kidshealth.org/en/parents/cyberbullying.html
- Kumar, S. (2021). Crime against children in cyber world . January .
- Lewczuk K, Wójcik A, Gola M. Increase in the prevalence of online pornography use: Objective data analysis from the period between 2004 and 2016 in Poland. Archives of Sexual Behavior. 2021 doi: 10.1007/s10508-021-02090-w. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Newman, J. C. (2019). Toward AI security: Global aspirations for a more resilient future . 1–89. https://cltc.berkeley.edu/wp-content/uploads/2019/02/CLTC_Cussins_Toward_AI_Security.pdf
- Nolan, C., & Brodowski, M. L. (2019). Emerging practices in the prevention of child abuse and neglect .
- Oriel, A. (2022). Top 8 AI technologies to mitigate child abuse and child trafficking . https://www.analyticsinsight.net/top-8-ai-technologies-mitigate-child-abuse-child-trafficking/
- Panda Media Center. (2022). Australian police develop a new AI tool to combat child abuse . https://www.pandasecurity.com/en/mediacenter/technology/police-ai-abuse/
- Peersman, C. (2017). Using AI for supporting cybercrime investigations .
- Podoletz L. We have to talk about emotional AI and crime. AI and Society. 2022; 0123456789 (-):-. doi: 10.1007/s00146-022-01435-w. [ CrossRef ] [ Google Scholar ]
- Pupillo, L., & Fantin, S. (2021). Artificial intelligence and cybersecurity .
- Rehnström, F. (2021). How capable is artificial intelligence (AI) in crime prediction and prevention? https://www.diva-portal.org/smash/get/diva2:1581808/FULLTEXT01.pdf
- Rigano C. Intelligence to address criminal. National Institute of Justice. 2019; 3 (280):1–10. [ Google Scholar ]
- Rouhollahi, Z. (2021). Towards artificial intelligence enabled financial crime detection .
- SavetheChildren.net. (2020). Online violence against children in Sri Lanka: A national research on incidence, nature and scope contents . https://srilanka.savethechildren.net/sites/srilanka.savethechildren.net/files/OnlineViolenceAgainstChildreninSriLanka.pdf
- Schermer, B. W., Georgieva, I., Hof, S. V. D., & Koops, B.-J. (2019). Legal aspects of Sweetie 2.0 . https://research.tilburguniversity.edu/en/publications/legal-aspects-of-sweetie-20-2
- Sunde, N., & Sunde, I. M. (2021). Article fagfellevurdert conceptualizing an AI-based police robot for preventing online child sexual exploitation and abuse: July . 10.18261/issn.2703-7045-2021-02-01
- Thuy, N. X., & Hieu, N. D. (2020). Developing artificial intelligence in fighting, preventing and combating the digital business crimes . 115 (Insyma), 447–450. 10.2991/aebmr.k.200127.090
- UK Home Office. (2015). The Child Abuse Image Database (CAID) . November , 1–5. https://www.gov.uk/government/uploads/system/uploads/attachment_data/file/478006/4817_CAID_Booklet_v13_online4.pdf
- UNESCO. (2019). Child online safety: Minimizing the risk of violence, abuse and exploitation online .
- UNICEF. (2019). SomeBuddy . 1–14.
- UNICRI. (2020a). Artificial intelligence and robotics for law enforcement . https://unicri.it/artificial-intelligence-and-robotics-law-enforcement
- UNICRI. (2020b). The new age of technology . https://unicri.it/topics/ai_robotics
- UNICRI. (2021). A high-level side-event to the 76th session of the United Nations general assembly . https://unicri.it/index.php/News/Child-Sexual-Exploitation-Online-Side-event-UNGA76
- Velasco, C. (2022). Cybercrime and artificial intelligence. An overview of the work of international organizations on criminal justice and the international applicable instruments. ERA Forum , 23 (1), 109–126. 10.1007/s12027-022-00702-z
- Vilks, A. (2019). Cybercrime and sexual exploitation of children in e-environment in the context of strengthening urban and rural security . 01010 .
- Walker, S. (2019). A guide to the UN cybercrime debate . March .
- Yadav, S., & Husain, M. S. (2018). Application of artificial intelligence in fighting against cyber crimes: A review Available Online at www.ijarcs.info Application of artificial intelligence in fighting against cyber crimes: A review . April 2020 .
- Zehra Abid. (2019). In Pakistan’s Kasur, child rapes and killings continue unabated | Child rights | Al Jazeera . https://www.aljazeera.com/features/2019/10/28/in-pakistans-kasur-child-rapes-and-killings-continue-unabated
- Zia UL Islam, Khan, M. A., & Zubair, M. (2019). Cybercrime and Pakistan. Global Political Review , IV (II), 12–19. 10.31703/gpr.2019(iv-ii).02
- The first place to go when you need to know.
- Map connected infrastructure to get ahead of threats.
- Discover and monitor lookalike domains with unmatched speed and coverage.
- Integrate DomainTools data with SIEM, SOAR, and other tools.
- The world’s largest Passive DNS intelligence solution.
- Unlock the power of 13+ years of historical passive DNS data, updated in real time.
- The “on-premise” version of DNSDB API resulting in the fastest response time, unlimited query volume, and total query privacy.
- Regular expression search across every label of a fully qualified domain name and select RData.
- If it’s happening online, you’ll know.
- Daily risk-scored domain list and targeted feeds.
- Predictive risk scoring and infrastructure profiling.
- Integrations
- Enhance threat hunting and domain alerts in your preferred SIEM.
- Create event playbooks and take targeted action with our leading domain intelligence.
- Uncover actor infrastructure and profile threats in your preferred platform.
- Transform threat data into intelligence with top security vendor partnerships.
- VAR’s, Distributors, MSSP’s and System Integrators can grow revenue and improve margins.
- Cyber Product and Service companies can quickly advance and differentiate your solution.
- Cyber Technology Companies enhance and expand your capabilities.
- See the Internet. Identify risk.
- Gain the early upper hand on emerging campaigns.
- Make unknown threats known before they do damage.
- Defend your brand and reputation.
- Discover “who is” behind attacks and threats.
- Build homegrown or third-party security applications with the world’s best Internet intelligence.
- Strengthening cybersecurity resilience across government systems.
- Increasing the financial sector’s resilience against attacks.
- Bolstering protection and defenses for PII and PHI.
- Helping defenders of the high-tech attack surface.
- Safeguarding against data breaches, consumer-based attacks, phishing, BEC, and other threats.
- Meet our exceptional executive team of experts and industry leaders.
- Join our team to collaborate with exceptional people who are dedicated to protecting the Internet.
- Access the latest DomainTools news and press coverage.
- We’re here to help with product info, pricing, and current and future account services.
- Resource Center
- Explore our library of thought leadership articles and insights.
- Watch live and on-demand cybersecurity training from the DomainTools team.
- Stream informative and exclusive episodes of DomainTools “Breaking Badness” podcast.
- Discover the real-world impact of DomainTools DNS intelligence.
- Navigate DomainTools features effortlessly with our comprehensive guides.
- Access everything you need, including endpoint, response formats, sample queries, and product service levels.
- Explore our in-depth Frequently Asked Questions by category to get the answers you need.
- Featured DomainTools Reports The DomainTools Report: Spring 2023 Edition Read More
- Support and Learning
- Request a Demo
The Resurgence of the “Manipulaters” Team - Breaking HeartSenders
Share this entry.
- Share on Facebook
- Share on Twitter
- Share on Linkedin
- Share by Mail
The Pakistan-based “Manipulaters” (their corruption of the word “manipulators”) represent a notorious and, in some respects, pioneering cybercrime empire. The Manipulaters have a decade-long history of selling phishing kits, spamming services, and malware. This history spans dozens of cybercrime marketplaces and the malicious domains associated with them are measured in the tens of thousands. The Manipulaters have enabled countless attacks against enterprises and customers; most security teams at Fortune 100 companies have encountered their deployed phishing kits or received spam from their mailers.
Nearly nine years ago, Brian Krebs released research on the Manipulaters Team , a fraud group that tricked people into giving up usernames and passwords via fake bank and e-commerce sites. Since then, the Manipulaters claimed to be turning over a new leaf–righting their wrongs and refraining from running large fraud schemes.
In 2021, Krebs reviewed the social media postings from the Manipulaters which showed they were prospering, while rather poorly hiding their activities behind a software development firm in Lahore that secretly enabled an entire generation of spammers and scammers.
In late 2023, our researchers stumbled upon a set of domains that linked back to their organization. That triggered the subsequent investigation into the historical domain and host records that unearthed that the Manipulaters have profited for more than a decade by selling vast quantities of phishing kits, commodity malware and spamming services, and more – eventually expanding into selling web domains, both for their own use as well as resale to other criminals. Coincidentally, in early 2024 and apropos of nothing, the Manipulaters reached out directly to Krebs asking for his removal of previous stories on their exploits.
Though lacking the technical sophistication many other large cybercrime vendors have, their most notable characteristic is being one of the earliest phishing-focused cybercrime marketplaces to horizontally integrate their business model while also spreading their operations across several separately branded shops. Unfortunately for them, another notable characteristic is a history of severe operational security inconsistencies.
Using a combination of domain-related data and open-source intelligence (OSINT) techniques, DomainTools Research identified dozens of Manipulaters cybercrime marketplaces that show a threat actor group that represents a growing concern. This concern is not limited to innocent consumers and enterprises; a series of operational security failures call into question the integrity of their criminal enterprise and may even suggest some of their customers are also targets. Ironically, the most significant risk to Manipulaters’ customers might be the Manipulaters themselves.
This piece explores both facets of this prolific, but perhaps enigmatically flawed, group.
The Role of Cybercrime Marketplaces
Cybercrime marketplaces serve a foundational role in the underground economy. These marketplaces exist primarily as a storefront for cybercrime service offerings but can also become de facto communities. Such communities can enable cybercrime in several ways, including driving innovation by associating cybercrime with financial reward, refining new techniques and methods that benefit members of the group, and lowering the technical barriers to entry to cybercrime by providing tools developed by others. Importantly, removing technical barriers to entry also increases the addressable market such cybercrime marketplaces cater to.
Marketing Apparatus
What the Manipulaters lack in technical sophistication, they make up for in scale and scope. Whereas other cybercrime groups seek to build an iconic brand, the Manipulaters prefer to deploy dozens of cybercrime shops using different names. This strategy is likely based on several motivating factors, including:
- Spreading risk across many domains makes the takedown of a single domain less operationally disruptive and may help avoid law enforcement scrutiny by appearing small.
- Operating several brands allows for reputation laundering if a customer accuses them of being a scam or offering low-quality products.
- Saturating the underground economy with seemingly disparate products and services that make new entrants less likely to compete.
The Long Road to Now
The Manipulaters are rapidly expanding operations following a period of relative inactivity after journalist Brian Krebs identified several of their members . This expansion appears to focus more on spamming tools and sender services, likely because of the overabundance of phishing kits and the relative ease of cloning them is less profitable than a services model.
Evidence suggests that new members have joined and at least one early member of the Manipulaters left the group. They appear to have a physical presence in Pakistan, including Lahore, Fatehpur, Karachi, and Faisalabad.
The Manipulaters have a long history of selling phishing kits, account checkers, proxy and RDP access, “bulletproof” hosting, and forged identity documents. Regarding software applications, they often rebrand or cobble together existing tools. Their priority now appears to be selling spam services.
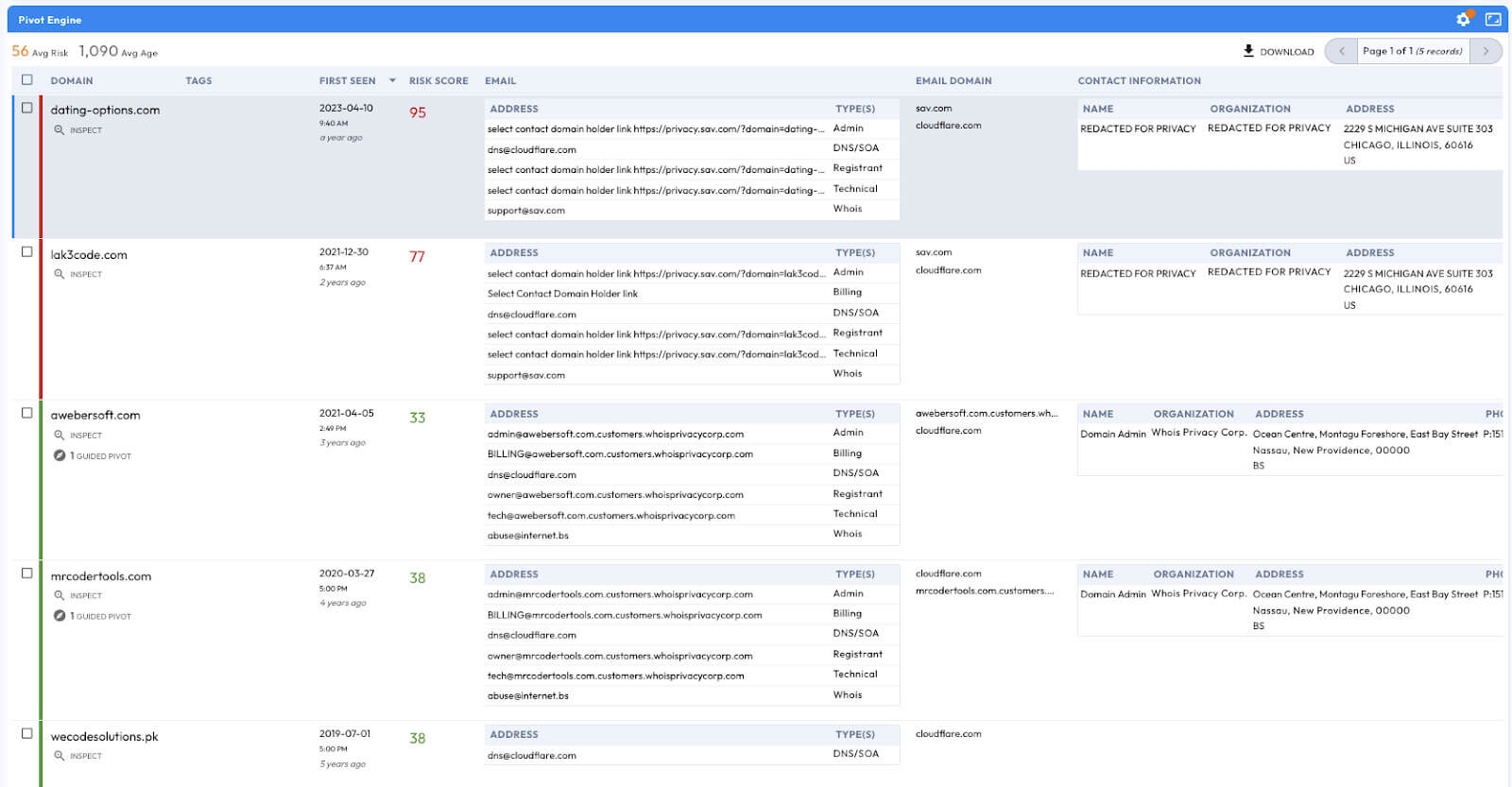
The domain wecodesolutions[.]pk is closely associated with the Manipulaters. This domain proves useful in collecting additional domains associated with the host 191.101.164[.]254 (Figure 1). Two domains are of particular interest:
lak3code[.]com
The interface shown in Figure 2 resembles one featured in an advertisement for “Office 365 Private Page with Antibot” posted on heartsender[.]com, another Manipulaters storefront (Figure 3). The ad includes a list of features used in modern phishing campaigns combined with a management panel.
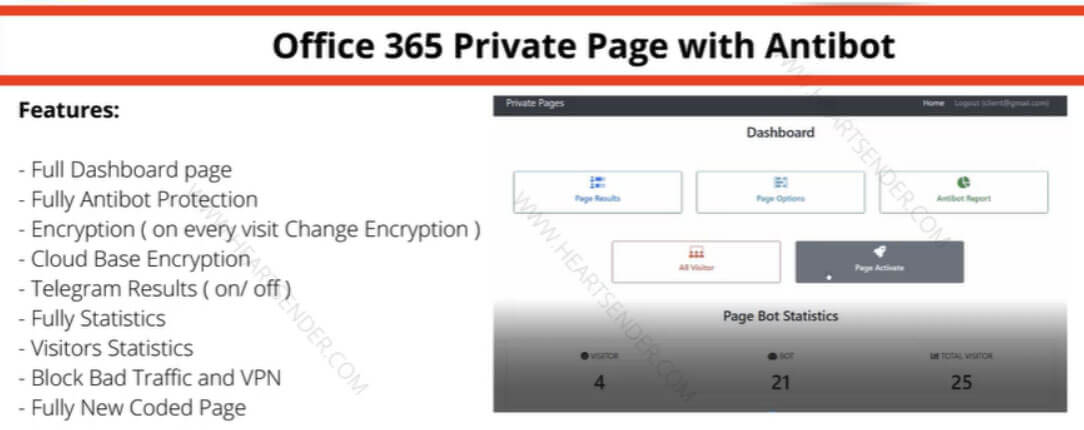
mrcodertools[.]com
The path /web/site/login appended to the domain mrcodertools[.]com reveals a management panel named “HeartSender” that resembles the one found at lak3code[.]com/web/site/login (Figure 4). Several menu items are notable: user requests, announcements, advertisements, and user feedback. Most of these pages require an authenticated user to access them. Some, however, do not.
The “Advertisements” screen contains a data table with more than 10,700 rows. Each entry includes a specific software product the Manipulaters sell (Figure 5). This panel may also represent part of the apparatus the Manipulaters use to manage customers and promote their services.
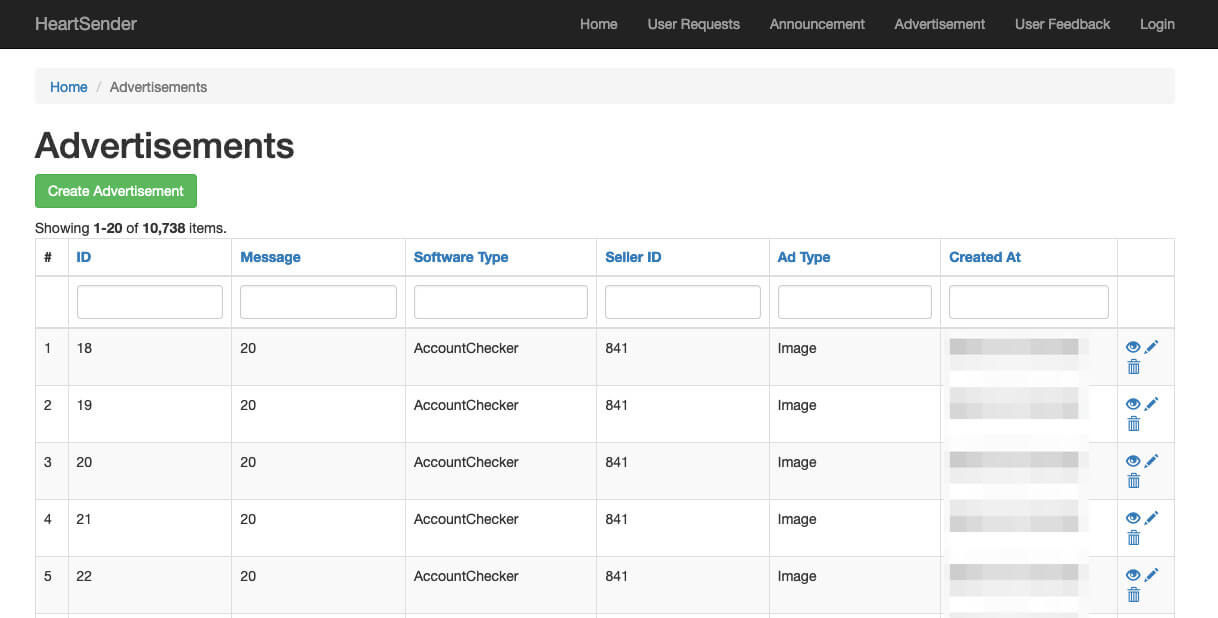
The “Create Advertisement” page is similarly accessible by an unauthenticated user. The dropdown menu for the field “Software Type” reveals the names of several products: HeartSender, FudSender, ClaySender, InboxXploiter, XploiterEmailVerifier, D29Sender, and AccountChecker (Figure 6). These product names proved helpful.
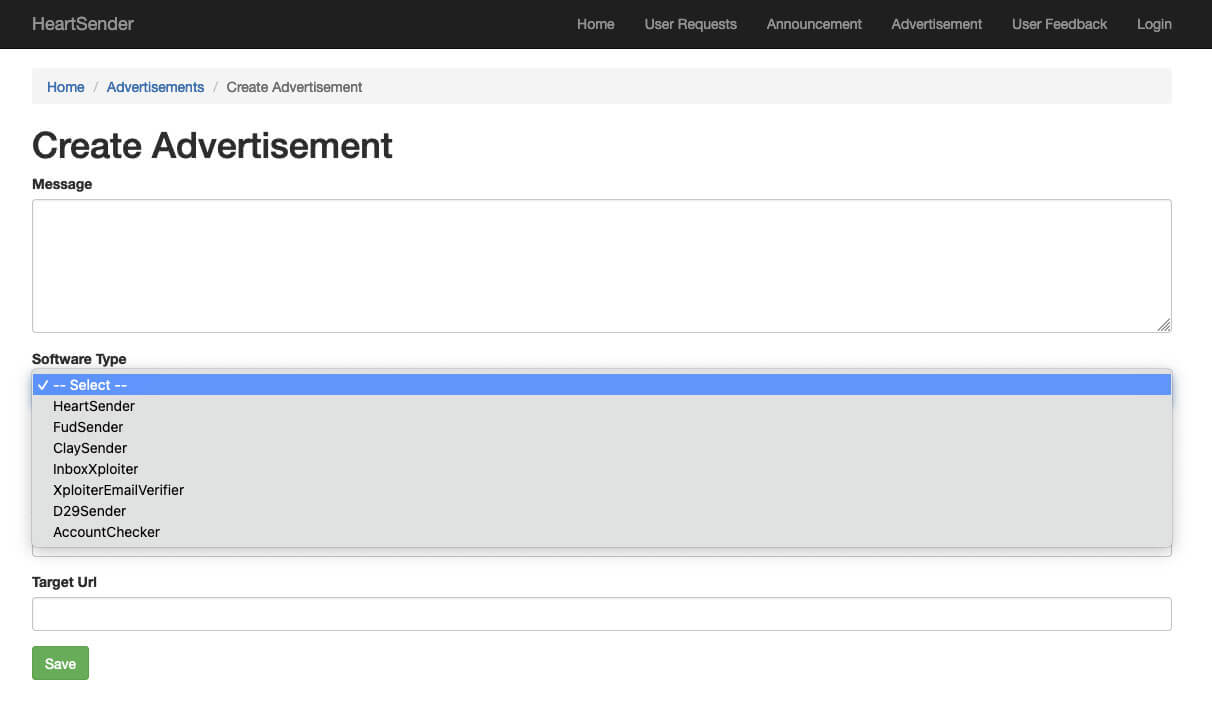
Building a query in DomainTools Iris Investigate for domains containing the product names listed in Figure 6 returns several results, including 117 domains, several hosts, and notable email addresses closely associated with the Manipulaters like saim.raza1338@gmail[.]com (Figure 7). These results offer helpful footholds and pivots to identify additional Manipulaters-controlled domains and infrastructure.
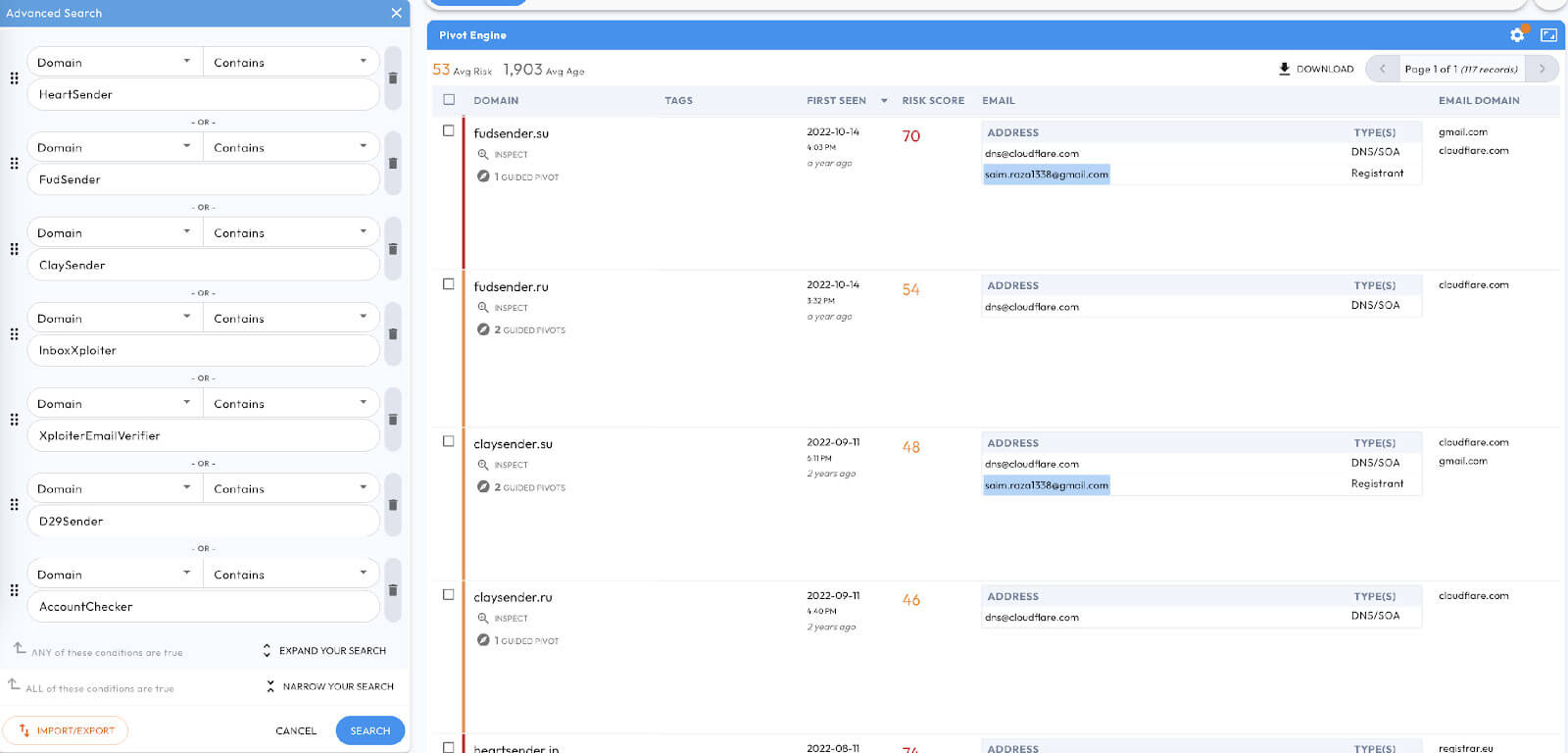
Introducing HeartSender
The heartsender[.]com storefront focuses on email and email-to-SMS spamming services (Figure 8). Customer response in cybercrime communities to HeartSender has been largely positive and represents a meaningful technical advancement for the Manipulaters, especially its improved email-to-SMS spamming capabilities (Figure 9). The latest person to join the Manipulaters could be the reason for the improved capabilities.
A code snippet found on another Manipulaters domain may offer insight into how the Node.js version of HeartSender works (Figure 10).
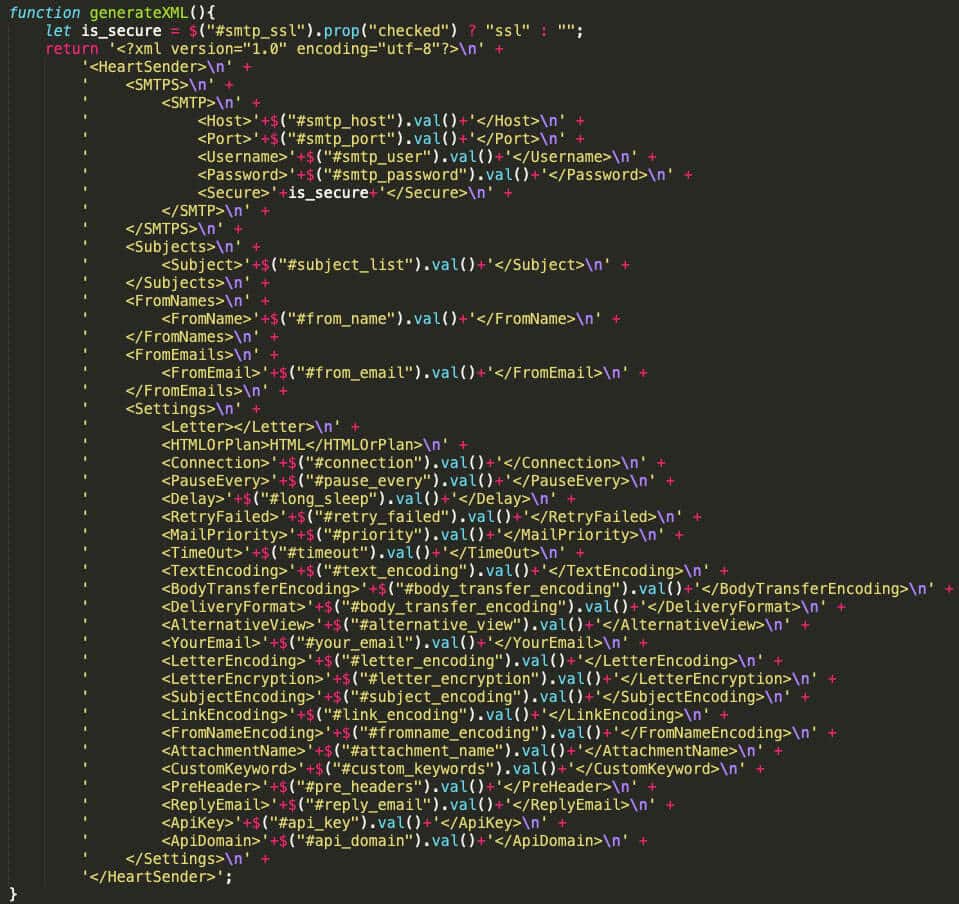
The Javascript function generateXML() dynamically constructs an XML string based on form field values using string concatenation and interpolation. This XML corresponds to a predefined scheme for sending emails using HeartSender. Perhaps the most notable portions of “main.js” are found in the <Settings> element. These elements exist to evade spam filters and detection generally, including <PauseEvery> , <Delay> , <BodyTransferEncoding> , <LetterEncoding> , <LetterEncryption> , and <LinkEncoding> .
The desktop version of HeartSender also deserves particular attention, but for different reasons.
Additional Pivots From the HeartSender Demo and a Pakistan IP Address
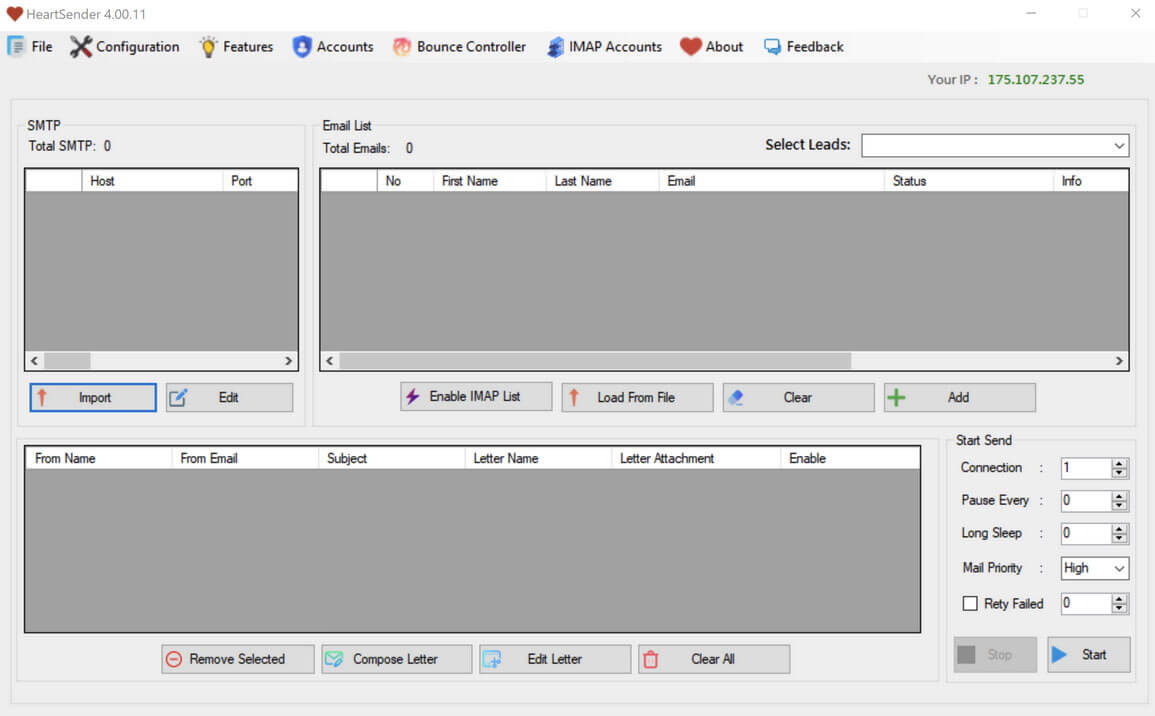
A screenshot of HeartSender 4.00.11’s interface displays the IP address 175.107.237[.]55 (Lahore, Pakistan) (Figure 11). This IP address is associated with several accounts, including the email addresses fudtoolshop@gmail[.]com, bodla057@gmail[.]com, mr6450465@gmail[.]com, and admin@coderteam[.]in. It is also associated with the usernames “saimraza786” and “mrbodla.” These naming conventions and aliases closely match those historically tied to the Manipulaters.
Domain registrations associated with the email address “fudtoolshop@gmail[.]com” return nearly 500 domains, many flagged as high risk in DomainTools Iris Investigate. The email address bodla057@gmail[.]com returns a domain registration for bodla[.]info with registrant “Hamza Bodla” in Fatehpur, Pakistan.
From HeartSender to dozens of Manipulaters-run shops
The host 185.11.145[.]254 has long been associated with Manipulaters activity and revealed dozens of deployed shops.
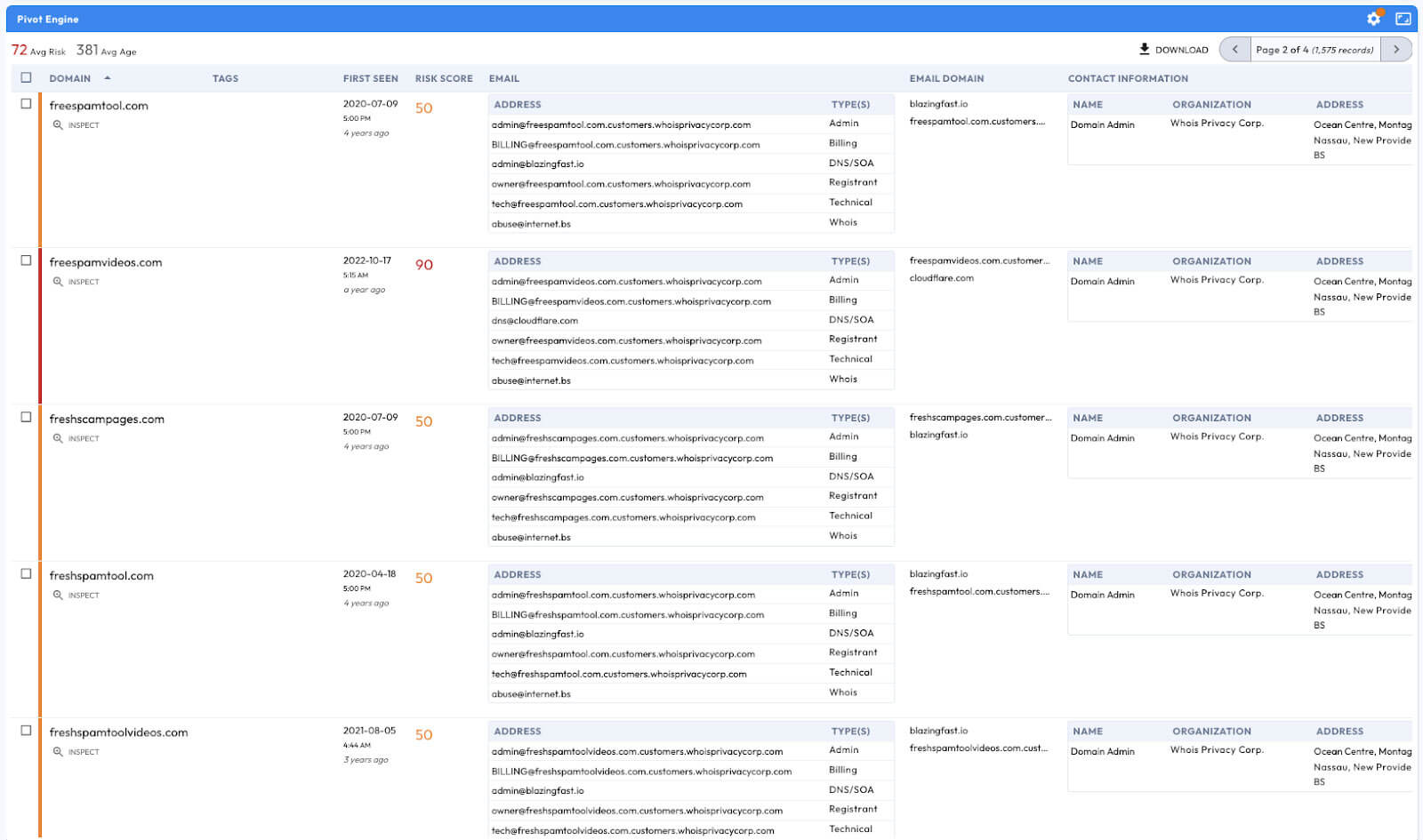
The Manipulaters often pair shop domains with domains containing tutorials and promotional videos for their products, providing a helpful point of reference for mapping the group’s domain footprint. Some of these domains include:
Trouble on the Horizon Targeting USPS-Related Impersonation and Session Cookie Grabbing
The Manipulaters’ newfound interest in email-to-SMS spam could be in response to the massive increase in smishing activity impersonating the USPS . Proofs posted on HeartSender’s Telegram channel contain numerous references to postal service impersonation, including proving delivery of USPS-themed phishing lures and the sale of a USPS phishing kit (Figures 13-14).
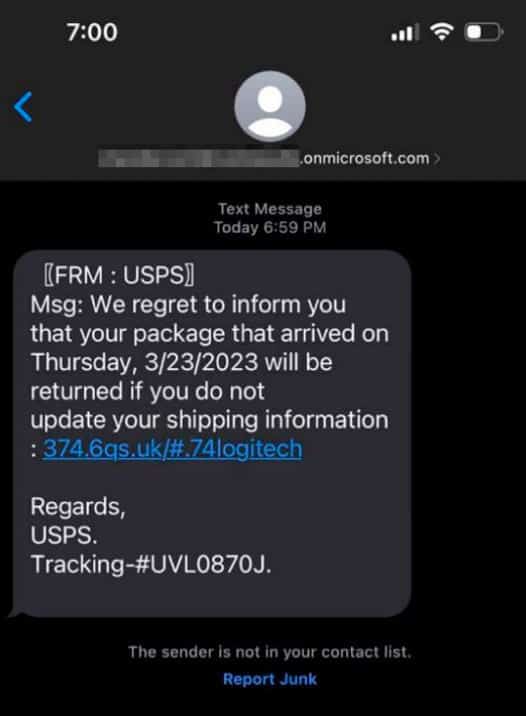
The Manipulaters appear to favor spamming services paired with session cookie grabbers, including operating a cybercrime shop focused almost exclusively on cookie theft and even creating an account named grabber@fudteambilling[.]com (Figure 15). This dangerous combination can make account takeover activity much less detectable than traditional credential phishing.
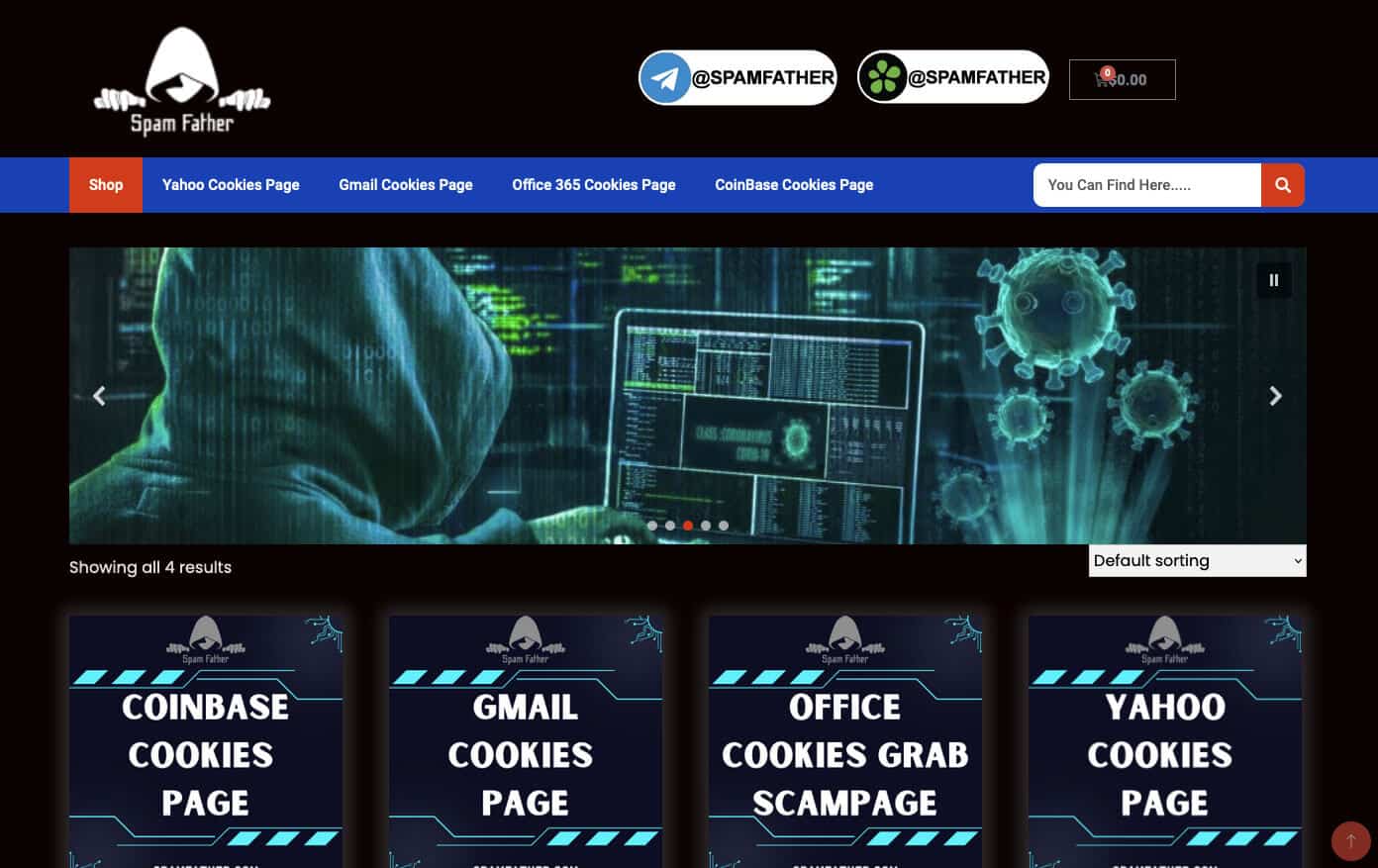
A Case Study in Technical Debt and Sloppy Authentication
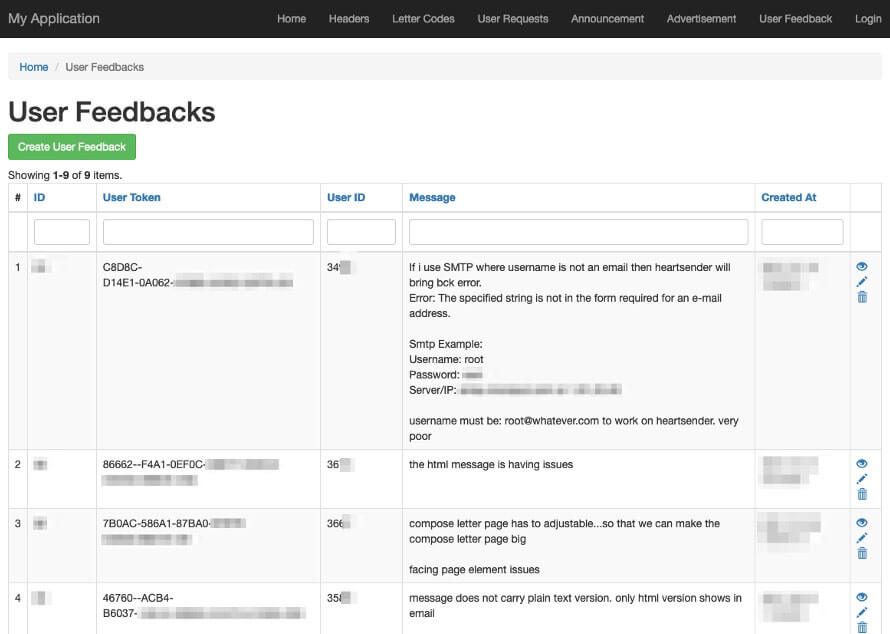
Ironically, the Manipulaters may create more short-term risk to their own customers than law enforcement. The data table “User Feedbacks” (sic) exposes what appear to be customer authentication tokens, user identifiers, and even a customer support request that exposes root-level SMTP credentials–all visible by an unauthenticated user on a Manipulaters-controlled domain. Given the risk of abuse, this domain will not be published.
There is so much more, however. Breach records associated with the unnamed domain and other domains used by the Manipulaters reveal a large online footprint paired with several severe operational security failures.
When It Rains, It Pours
Research suggests that several PCs associated with the Manipulaters have been compromised by stealer malware for a considerable amount of time, exposing vast swaths of account-related data along with an outline of the group’s membership, operations, and position in the broader underground economy. Curiously, the large subset of identified Manipulaters customers appear to be compromised by the same stealer malware. All observed customer malware infections began after the initial compromise of Manipulaters PCs, which raises a number of questions regarding the origin of those infections.
These breach records can be divided into three clusters. Overlap exists between activity clusters likely because several people were working on the same projects.
Cluster “Adnan”
Associated usernames: adnan, grabber, harsh, mrcoder, xleet
Associated email addresses: admin@fudsender[.]club, admin@fudsender[.]com, admin@heartsender[.]com, f.udtoolshop@gmail[.]com, fudscam@fudsender[.]com, fudsender.utube@gmail[.]com, fudspam.toolss@gmail[.]com, fudspam@hotmail[.]com, fudtool786@gmail[.]com, mohsinaseller@gmail[.]com, mr.codertools@gmail[.]com, saim.pays@gmail[.]com, xleet@fudsender[.]com
Associated domains: busypaymant[.]com, fudsell[.]com, fudsender[.]com, fudsender[.]store, fudteambilling[.]com, fudtool[.]su, fudtoolshop[.]com, fudtoolvideos[.]com, mrcodertools[.]com, profud[.]tools, provip[.]tools, saimraza[.]com
Cluster “Imran”
Associated usernames: fudtoolr, imran231, saimraza786, turbopk
Associated email addresses: abdulrehman940@gmail[.]com, admin@buyspamtools[.]com, admin@fudsender[.]com, admin@fudteam[.]com, admin@remitciti[.]com, admin@turbopk[.]net, ikorai99@gmail[.]com, info@shahg[.]co, itmalik91@gmail[.]com, itwebs92@gmail[.]com, saim.raza1338@gmail[.]com, sh4hgh3x0r@gmail[.]com
Associated domains: billing.saimraza[.]info, fudtoolshop[.]com, fudtoolvideos[.]com
Cluster “Bodla”
Associated usernames: live:fudtoolshop, mr6450465, mrbodla, mrbodlah, saimraza007, saimraza123, saimraza786
Associated email addresses: admin@coderteam[.]in, admin@fudteam[.]com, bodla0143@gmail[.]com, bodla057@gmail[.]com, fudtool786@gmail[.]com, fudtoolshop@gmail[.]com, help.alizain@gmail[.]com, henrylukeusa@gmail[.]com, mr6450465@gmail[.]com, osamaevee2000@gmail[.]com, sahrn512@gmail[.]com
Associated domains: bodla[.]info, coderteam[.]in
Conclusion, Where Do We Go From Here?
The Manipulaters offer illustrative examples of how cybercrime vendors integrate into the broader underground economy. In the decade they have been active, the Manipulaters have appeared in and created many different marketplaces selling phishing kits, malware, spamming services and more. Most recently, DomainTools Research has found them moving into email-to-SMS services with HeartSender, as well as pairing spamming services with session cookie grabbers. We have also found some of their infrastructure seems to be accessible by unauthenticated users and that some of their (and their customers’) infrastructure has been compromised by malware.
Given the Manipulaters’ resurgence and improved capabilities, DomainTools Research urges businesses and consumers to remain vigilant against threat actor groups like the Manipulaters and those they enable with their products and services.
Download our Security Bulletin for more additional background details on the Manipulaters and to explore the role of historical Whois and DNS data in mapping a domain-focused threat actor’s footprint.
For free 2024 lists of domains, email addresses, and usernames associated with the Manipulaters and a non-exhaustive collection of domains from 2015 to early 2018, visit our SecuritySnacks GitHub Repo .
Active Shops – 03.25.24:
bulktools[.]su buyfreshtools[.]com buyspampages[.]com buyspamtool[.]com buyspamtool[.]ru claysender[.]com d29sender[.]com freespamtool[.]com freshscampages[.]com freshspamtool[.]com freshtoolshop[.]com fudfreshtools[.]com fudlinkheartsender[.]com fudpage[.]com fudpagetools[.]com fudscampages[.]com fudscams[.]net fudsender[.]com fudsender[.]live fudsender[.]ru fudspam[.]com fudspam[.]su fudtools[.]com gxsender[.]com heartsender[.]com heartsenderscampages[.]com inboxxploiter[.]com newspamtools[.]com nodesender[.]com officesender[.]com scampageshop[.]com smtpshop[.]com spamfather[.]com spamtoolx[.]com stroxshop[.]com toolsplug[.]com xleetshop[.]com
Email addresses:
admin@buyspamtools[.]com admin@claysender[.]com admin@coderteam[.]in admin@fudsender[.]club admin@fudsender[.]com admin@fudsender[.]store admin@fudspam[.]tools admin@fudteam[.]com admin@heartsender[.]com admin@remitciti[.]com admin@turbopk[.]net afaqkhan.khan334@gmail[.]com ahmadbodla@yahoo[.]com aliraza0347601@gmail[.]com askimran.33@gmail[.]com bluebtcus@gmail[.]com bodla_143@yahoo[.]com bodla0143@gmail[.]com bodla057@gmail[.]com burhanahmad107@hotmail[.]com emraanmurtaza9@gmail[.]com f.udtoolshop@gmail[.]com faisal_awan2011@yahoo[.]com freshtoolsshop@gmail[.]com fud.tool.s@gmail[.]com fudpages@gmail[.]com fudpagez@gmail[.]com fudscam@fudsender[.]com fudsender.utube@gmail[.]com fudspam.toolss@gmail[.]com fudspam@hotmail[.]com fudtool786@gmail[.]com fudtoolshop@gmail[.]com grabber@fudteambilling[.]com gxsender@hotmail[.]com hamzaseller@gmail[.]com heartsender123@gmail[.]com heartsenderupdates@gmail[.]com ikorai99@gmail[.]com imranmurtaza03@gmail[.]com imranmurtaza323@gmail[.]com info@shahg[.]co itwebs92@gmail[.]com javidtabiseller@gmail[.]com mohsin@gmail[.]com mohsinaseller@gmail[.]com mr_coder@inbox[.]ru mr.codertools@gmail[.]com mr6450465@gmail[.]com mrbodla@gmail[.]com mrbodla@yahoo[.]com osamaevee2000@gmail[.]com pakfunplus91@gmail[.]com privatetools26@yahoo[.]com rainyeyes143@gmail[.]com saim.pays@gmail[.]com saim.raza1338@gmail[.]com saim.raza933@gmail[.]com saimmalik123@yahoo[.]com saimraza1992@gmail[.]com sanwal_raza66@yahoo[.]com sh4hgh3x0r@gmail[.]com smtpshop.su@yahoo[.]com sunnyseller@gmail[.]com support@mr-coder[.]com talhasheikh918@gmail[.]com xitforum00@gmail[.]com xleet@fudsender[.]com
adminfreshscampages buyfreshtool clay_sender clayadmin d29admin d29sender d29senderupdate freshfud_tools freshscampagesadmin fud spam fud_page fudfreshtool fudpages fudpagesadmin fudsender fudspam_com fudtool fudtoolshop hamzabodla heartsender imran33 krank007 fudtoolshop mr-coder mrbodla mrbodlah mrcoder node_sender nodesenderadmin rainy_eyes rameez786 saadaliadmin saimraza saimraza007 saimraza786 sunny_bodla057

A Look Back on "The Manipulaters"

[Special Report] Father Phishmas, Give Us The Money

Merry Phishmas: Beware US Postal Service Phishing During the Holidays
Sign up for our newsletter, related content.
Enhancing dnsdbq Output With Geolocation Data

We need an American Girl who bolsters cybersecurity

Nowhere Near Extinction: Mastodon One Year Later

- Threat Intelligence
- Phishing and Fraud Prevention
- Threat Hunting
- Brand Protection
- Forensics & Incident Response
- Application Enrichment
- Federal Government
- Financial Services
- Iris Detect
- Iris Enrich
- Iris Investigate
- Farsight DNSDB
- Predictive Risk Scoring
- Hosting IP Risk Feed & Hotlist
- Domain Risk Feed & Hotlist
- Domain Visibility Feed
- Domain Discovery Feed
- Farsight Newly Active Domains
- Farsight Newly Observed Hostnames
- Farsight Newly Observed Domains
- DomainTools Monitors
- Cortex XSOAR
- CrowdStrike
- IBM Resilient
- Splunk SOAR
- TheHive and Cortex
- Reseller Partner
- Technology Partners
- MSSP Partners
- OEM Partners
- Partner Portal
- API Documentation
© 2024 DomainTools
DomainTools® and DomainTools™ are owned by DomainTools, all rights reserved.
Privacy Policy | California Privacy Notice Do Not Sell My Personal Information | Terms of Service | Sitemap

COMMENTS
This paper focuses on the prevailing development of governance policies for cyber space and defies among the agencies and information technology venders. Moreover, the case study of national bank of Pakistan and other cyber crime survey shows that a lot of law making is needed in order to reduce the chances of cyber crime.
BankIslami. In November 2018, Pakistan's banking industry suffered a unique form of cyber attack. Data of almost all Pakistani banks was breached, affecting nearly 20,000 banking customers ...
Cyber Crime WING. Cybercrime Wing (CCW), of Federal Investigation Agency, is guided by laws under prevention of Electronic Crimes ACT (PECA) 2016, which deals with the growing threats of cybercrimes. Inception of this Hi-Tech crime fighting unit transpired in 2007 to identify and curb the phenomenon of technological abuse in society.
significance to understand its contribution at what stage Pakistan is, in case of cyber world. In Pakistan, however, three decades ago commission of cyber-crimes was not significant as most of ... The foremost problem for the cyber crime's study is the absence of proper definition for the term cyber-crime, some jurists tried to define this ...
Conclusion. Pakistan's National Cybersecurity Policy 2021 provides much-needed direction to the overall benefit of society at large, however, policy makers have yet to clarify the following: Operating framework of the CGPC. Reporting structure of the CGPC. Powers granted to the CGPC.
of cyber-threats and crimes amongst young adults in Pakistan, focusing on their mechanisms for protecting themselves, for reporting cyber threats and for managing their digital identi-ties. Relying on data from a qualitative study with 34 partici-pants in combination with a repertory grid analysis with 18
This paper focuses on the prevailing development of governance policies for cyber space and defies among the agencies and information technology venders. Moreover, the case study of national bank of Pakistan and other cyber crime survey shows that a lot of law making is needed in order to reduce the chances of cyber crime.
Pakistan also lacks sufficient legislation for countering cyber threats. In 2016, Pakistan passed a cybercrime law called the Prevention of Electronic Crimes Act, 2016; however, the act does not ...
(Sept. 21, 2016) On August 11, 2016, Pakistan's lower house, the National Assembly, passed a controversial cybercrime law called the Prevention of Electronic Crimes Act, 2016. The Senate had unanimously passed the law, with a number of amendments, in July. (Raza Khan, Cyber Crime Bill Passed by NA: 13 Reasons Pakistanis Should Be Worried, DAWN […]
Read online. "Cyber Crime in Pakistan; Detection and Punishment Mechanism" addresses improvement of public health and safety policies by focusing on enhancing knowledge about cybercrime, women victimization, the pattern of time spent on the internet, sexual harassment and cyberbullying and the effect of sociodemographic factors on cybercrime.
Updated Monday Jan 04 2021. The year 2020 was not only hard for people across the globe because of the pandemic and the economic crisis engendered by it, but extended lockdowns also led to a surge ...
The cases under the Pakistan Electronic Crimes Act (PECA, also referred to as the country's "cyber-crime law") were often compounded with allegations under the penal code, with criminal ...
cybercrime in Pakistan can be gauged from the fact that FIA received 84,764 complaints in 2020, 300 percent more than the complaints received in 2019. FIAthrough it Cyber Crime Wing(CCW) is making consistent efforts to cope with ... University termed the booklet very informative as real world case studies has been included in it. She also ...
The principle aim of this study is to discuss the cybercrimes and examine the cyber laws in Pakistan and talk about the cyber security strategy of Pakistan. Communications have become the most essential and quite an easy as well as fast because of technology advancement. Developing states are also getting the same blessings of computer networks and internet like the developed nations of the world.
The National Response Center for Cyber Crime (NR3C) — a law enforcement agency which combats cyber crimes in Pakistan — lists various cyber-crime prevention tips for the secure use of smart ...
Technical facilitation extended through digital forensic analysis, cyber tracking, digital crime investigation to local law enforcement agencies in cases such as murder, robbery, extortion and many more. -. Technical trainings on cyber crime, digital forensics, information security to law enforcement agencies like IB, ISI, NAB, ANF, Local Police.
The minister informed the participants that Pakistan's first cyber security policy, launched in July 2021, explained the mechanism of staying safe from cyber attacks.
at the FIA Cyber Crime Wing, Lahore under section 20 of the Prevention of Electronic Crimes Act, 2016 ('PECA') against eight persons, including the petitioners and her witnesses; all of whom, we are told, have obtained bail and are facing the ordeal of a criminal trial. And, by such tactics the
Particularly, cybercrimes against children in developing countries are another major concern that requires serious consideration. For example, Federal Intelligence Agency (FIA) Pakistan reported daily 266 cybercrimes against children, mainly including child pornography and harassment, in the country. Still, most cybercrimes against children ...
This study was an effort to identify contextual factors stimulating illegitimate activities in cyber environment and to suggest remedial measures in this regard. Countries across the world are deeply concerned about the cybercrimes. Experts and practitioners always emphasize on collaborative efforts to investigate and control illegal activities in virtual environment. Countries differ ...
CYBER CRIME PREVENTION TIPS. Read More . Help & Feedback Frquently Asked Questions About NR3C Complaints. CONTACT. Address: 2nd Floor, National Police Foundation Building, Mauve Area, Sector G-10/4, Islamabad, Pakistan. Helpline: 1991 Phone: +92 51 9106 384 Email: [email protected]. LEGAL.
National Reponse Centre for Cyber Crime (NR3C), is the latest introduction to mandate of the FIA, primarily to deal with technology based crimes in Pakistan. It is the only unit of its kind in the country and in addition to the directly received complaints also assists other law enforcement agencies in their own cases.
According to official data, 32pc of the complaints in 2021 were reported by students, while 25pc of them pertained to financial crimes. Among the categories of cases, financial fraud and forgery ...
The Pakistan-based "Manipulaters" (their corruption of the word "manipulators") represent a notorious and, in some respects, pioneering cybercrime empire. The Manipulaters have a decade-long history of selling phishing kits, spamming services, and malware. This history spans dozens of cybercrime marketplaces and the malicious domains associated with them are measured in the tens of ...